Powerpoint Templates and Google slides for Cybers Attacks
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Understanding Types of Cyber Attacks Training Ppt
Understanding Types of Cyber Attacks Training PptPresenting Training Deck on Understanding Types of Cyber Attacks. This deck comprises of 116 slides. Each slide is well crafted and designed by our PowerPoint experts. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed business presentation, add your content, and present it with confidence.
-
 Prevention of Cyber Attacks Training Ppt
Prevention of Cyber Attacks Training PptPresenting Training Deck on Prevention of Cyber Attacks. This deck comprises of 88 slides. Each slide is well crafted and designed by our PowerPoint experts. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed business presentation, add your content, and present it with confidence.
-
 Business Impact of Cyber Attacks Training Ppt
Business Impact of Cyber Attacks Training PptPresenting Training Deck on Business Impact of Cyber Attacks. This deck comprises of 39 slides. Each slide is well crafted and designed by our PowerPoint experts. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed business presentation, add your content, and present it with confidence.
-
 Implementing Security Awareness Training To Prevent Cyber Attacks Powerpoint Presentation Slides
Implementing Security Awareness Training To Prevent Cyber Attacks Powerpoint Presentation SlidesEnthrall your audience with this Implementing Security Awareness Training To Prevent Cyber Attacks Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising senenty five slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Cyber Terrorism Attacks Powerpoint Presentation Slides
Cyber Terrorism Attacks Powerpoint Presentation SlidesEnthrall your audience with this Cyber Terrorism Attacks Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising seventy one slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Cyber Security Attacks Response Plan Powerpoint Presentation Slides V
Cyber Security Attacks Response Plan Powerpoint Presentation Slides VEnthrall your audience with this Cyber Security Attacks Response Plan Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising sixty eight slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Generating Security Awareness Among Employees To Reduce Cyber Attacks Complete Deck
Generating Security Awareness Among Employees To Reduce Cyber Attacks Complete DeckDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Generating Security Awareness Among Employees To Reduce Cyber Attacks Complete Deck is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the sixty five slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Cyber Attacks On Ukraine Powerpoint Presentation Slides
Cyber Attacks On Ukraine Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Cyber Attacks On Ukraine Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the sixty one slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 String Of Cyber Attacks Against Ukraine 2022 Powerpoint Presentation Slides
String Of Cyber Attacks Against Ukraine 2022 Powerpoint Presentation SlidesThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes String Of Cyber Attacks Against Ukraine 2022 Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of sixty one slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Security Plan To Prevent Cyber Attacks Powerpoint Presentation Slides
Security Plan To Prevent Cyber Attacks Powerpoint Presentation SlidesDeliver an informational PPT on various topics by using this Security Plan To Prevent Cyber Attacks Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with forty slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
-
 DoS and DDoS Attacks In Cyber Security Training Ppt
DoS and DDoS Attacks In Cyber Security Training PptPresenting DoS and DDoS Attacks in Cyber Security. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Strategy To Minimize Cyber Attacks Risks Powerpoint Presentation Slides
Strategy To Minimize Cyber Attacks Risks Powerpoint Presentation SlidesThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Strategy To Minimize Cyber Attacks Risks Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of thirty eight slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Password Attack Types In Cyber Security Training Ppt
Password Attack Types In Cyber Security Training PptPresenting Password Attack Types in Cyber Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed business presentation, add your content and present it with confidence.
-
 Man In The Middle Attack In Cyber Security Training Ppt
Man In The Middle Attack In Cyber Security Training PptPresenting Man in the Browser Attack in Cyber Security. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Malware Attack In Cyber Security Training Ppt
Malware Attack In Cyber Security Training PptPresenting Malware Attack in Cyber Security. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Adware Attack In Cyber Security Training Ppt
Adware Attack In Cyber Security Training PptPresenting Adware Attack in Cyber Security. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Ransomware Attacks In Cyber Security Training Ppt
Ransomware Attacks In Cyber Security Training PptPresenting Ransomware Attacks in Cyber Security. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Man In The Browser Attack In Cyber Security Training Ppt
Man In The Browser Attack In Cyber Security Training PptPresenting Man in the Browser Attack in Cyber Security. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Cryptojacking Attack In Cyber Security Training Ppt
Cryptojacking Attack In Cyber Security Training PptPresenting Cryptojacking Attack in Cyber Security. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Phishing Attack Types In Cyber Attack Training Ppt
Phishing Attack Types In Cyber Attack Training PptPresenting Phishing Attack Types in Cyber Attack. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Cyber Attacks Trends To Watchout Training Ppt
Cyber Attacks Trends To Watchout Training PptPresenting Cyber Attacks Trends to Watchout. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Mobile Adware Attack In Cyber Security Training Ppt
Mobile Adware Attack In Cyber Security Training PptPresenting Mobile Adware Attack in Cyber Security. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Case Study On Cyber Attack Training Ppt
Case Study On Cyber Attack Training PptPresenting Case Study on Cyber Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Cyber Attack Risks Mitigation Strategies Powerpoint Ppt Template Bundles DK MD
Cyber Attack Risks Mitigation Strategies Powerpoint Ppt Template Bundles DK MDIf you require a professional template with great design, then this Cyber Attack Risks Mitigation Strategies Powerpoint Ppt Template Bundles DK MD is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using eighteen slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Distributed Denial Of Service Attack In Cyber Security Training Ppt
Distributed Denial Of Service Attack In Cyber Security Training PptPresenting Distributed Denial of Service Attack in Cyber Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Spyware Cyber Attack In Cybersecurity Training Ppt
Spyware Cyber Attack In Cybersecurity Training PptPresenting Spyware Cyber Attack in Cybersecurity. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Malvertising Cyber Attacks In Cybersecurity Training Ppt
Malvertising Cyber Attacks In Cybersecurity Training PptPresenting Malvertising Cyber Attacks in Cybersecurity. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Protection Against Cyber Threats And Attacks Training Ppt
Protection Against Cyber Threats And Attacks Training PptPresenting Protection Against Cyber Threats and Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Cyber Attack In Cybersecurity Training Ppt
Cyber Attack In Cybersecurity Training PptPresenting Cyber Attack in Cybersecurity. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Different Reasons Behind Cyber Attacks Training Ppt
Different Reasons Behind Cyber Attacks Training PptPresenting Different Reasons Behind Cyber Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Individuals And Organizations Behind Cyber Attacks Training Ppt
Individuals And Organizations Behind Cyber Attacks Training PptPresenting Individuals and Organizations Behind Cyber Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 List Of Motivations Behind Cyber Attacks Training Ppt
List Of Motivations Behind Cyber Attacks Training PptPresenting List of Motivations behind Cyber Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
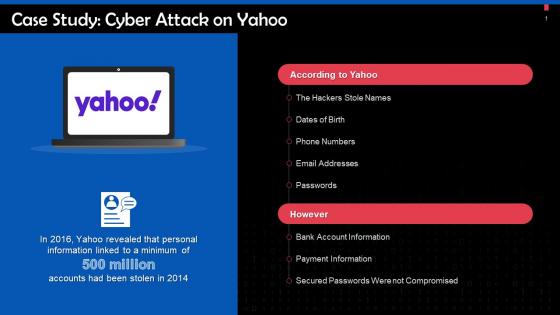
 Cyber Attack On Yahoo Case Study Training Ppt
Cyber Attack On Yahoo Case Study Training PptPresenting Cyber Attack on Yahoo Case Study. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Password Attacks In Cyber Security Training Ppt
Password Attacks In Cyber Security Training PptPresenting Password Attacks in Cyber Security. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Types Of Phishing Password Attacks In Cyber Security Training Ppt
Types Of Phishing Password Attacks In Cyber Security Training PptPresenting Types of Phishing Password Attacks in Cyber Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Cyber Attack Powerpoint Ppt Template Bundles
Cyber Attack Powerpoint Ppt Template BundlesIf you require a professional template with great design, then this Cyber Attack Powerpoint Ppt Template Bundles is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using fourteen slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Cyber Phishing Attacks Tracking Dashboard
Phishing Attacks And Strategies To Mitigate Them V2 Cyber Phishing Attacks Tracking DashboardThis slide represents the dashboard to track cyber phishing attacks. The purpose of this slide is to provide a graphical representation of cyber attacks occurred in a specific time span. It also depicts the organizations health risk. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Cyber Phishing Attacks Tracking Dashboard. Dispense information and present a thorough explanation of Dashboard To Track, Cyber Phishing Attacks, Graphical Representation, Specific Time Span, Organizations Health Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data security it cyber attacks experienced by company in previous financial year
Data security it cyber attacks experienced by company in previous financial yearThis slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2021. Deliver an outstanding presentation on the topic using this Data Security IT Cyber Attacks Experienced By Company In Previous Financial Year. Dispense information and present a thorough explanation of Cyber Attacks Experienced, FY2022, Comparatively using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Computer system security cyber attacks experienced by company in previous financial year
Computer system security cyber attacks experienced by company in previous financial yearThis slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2021. Present the topic in a bit more detail with this Computer System Security Cyber Attacks Experienced By Company In Previous Financial Year. Use it as a tool for discussion and navigation on Cyber Attacks Experienced By Company In Previous Financial Year. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Faced By Organization Security Plan To Prevent Cyber
Cyber Attacks Faced By Organization Security Plan To Prevent CyberThis slide provides information regarding the number of cyber attacks faced by the organization and its impact on IT operations and system downtime. It also provides details of percentage rise in such attacks since last month. Present the topic in a bit more detail with this Cyber Attacks Faced By Organization Security Plan To Prevent Cyber. Use it as a tool for discussion and navigation on Cyber Attacks, IT Operations, System Downtime. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Plan To Prevent Cyber Dashboard For Tracking Cyber Attack Risk Levels
Security Plan To Prevent Cyber Dashboard For Tracking Cyber Attack Risk LevelsThe slide represents the dashboard for tracking cyber attack risk levels. It includes information regarding the multiple threat agents, attack methods, preventive controls along with details of risk score and infected systems. Present the topic in a bit more detail with this Security Plan To Prevent Cyber Dashboard For Tracking Cyber Attack Risk Levels. Use it as a tool for discussion and navigation on Infrastructure Controls, Preventive Controls, Detective Controls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Plan To Prevent Cyber Dashboard To Monitor Cyber Attack Incidents
Security Plan To Prevent Cyber Dashboard To Monitor Cyber Attack IncidentsThis slide indicates the dashboard to monitor cyber attacks on IT assets of the firm. It includes information regarding the total cyber attack incidents both month and day wise along with the details of threat class, overall risk factor and top vulnerabilities. Deliver an outstanding presentation on the topic using this Security Plan To Prevent Cyber Dashboard To Monitor Cyber Attack Incidents. Dispense information and present a thorough explanation of Dashboard To Monitor, Cyber Attacks, IT Assets Of The Firm, Risk Factor And Top Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Plan To Prevent Cyber Summary Of Key Cyber Attacks Occurred
Security Plan To Prevent Cyber Summary Of Key Cyber Attacks OccurredThis slide shows the summary of key of cybers attacks occurred in organization such as phishing, malware attack, denial of service, SQL injections, identity thefts. It also contains details of the cyber attacker origin such as inadvertent actors, malicious insiders. Present the topic in a bit more detail with this Security Plan To Prevent Cyber Summary Of Key Cyber Attacks Occurred. Use it as a tool for discussion and navigation on Cybers Attacks, Phishing, Malware Attack, Denial Of Service, SQL Injections, Malicious Insiders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
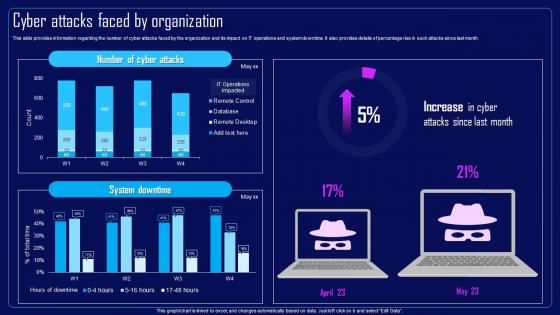 Action Plan To Combat Cyber Crimes Cyber Attacks Faced By Organization
Action Plan To Combat Cyber Crimes Cyber Attacks Faced By OrganizationThis slide provides information regarding the number of cyber attacks faced by the organization and its impact on IT operations and system downtime. It also provides details of percentage rise in such attacks since last month. Deliver an outstanding presentation on the topic using this Action Plan To Combat Cyber Crimes Cyber Attacks Faced By Organization. Dispense information and present a thorough explanation of Cyber Attacks Faced By Organization, IT Operations And System Downtime, Remote Desktop using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
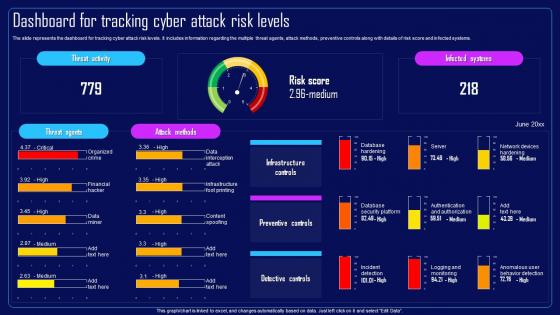 Action Plan To Combat Cyber Crimes Dashboard For Tracking Cyber Attack Risk Levels
Action Plan To Combat Cyber Crimes Dashboard For Tracking Cyber Attack Risk LevelsThe slide represents the dashboard for tracking cyber attack risk levels. It includes information regarding the multiple threat agents, attack methods, preventive controls along with details of risk score and infected systems. Deliver an outstanding presentation on the topic using this Action Plan To Combat Cyber Crimes Dashboard For Tracking Cyber Attack Risk Levels. Dispense information and present a thorough explanation of Dashboard For Tracking, Cyber Attack Risk Levels, Risk Score And Infected Systems, Preventive Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
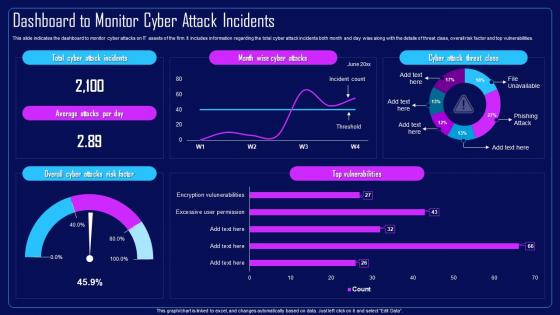 Action Plan To Combat Cyber Crimes Dashboard To Monitor Cyber Attack Incidents
Action Plan To Combat Cyber Crimes Dashboard To Monitor Cyber Attack IncidentsThis slide indicates the dashboard to monitor cyber attacks on IT assets of the firm. It includes information regarding the total cyber attack incidents both month and day wise along with the details of threat class, overall risk factor and top vulnerabilities. Present the topic in a bit more detail with this Action Plan To Combat Cyber Crimes Dashboard To Monitor Cyber Attack Incidents. Use it as a tool for discussion and navigation on Dashboard To Monitor, Cyber Attacks, IT Assets Of The Firm, Risk Factor And Top Vulnerabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
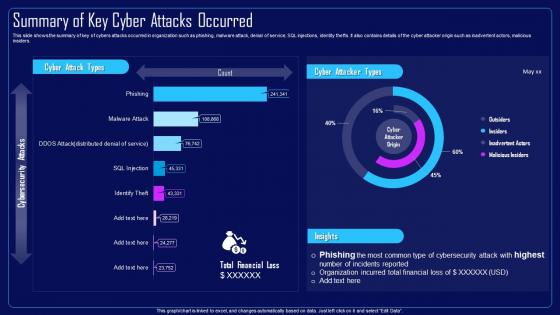 Action Plan To Combat Cyber Crimes Summary Of Key Cyber Attacks Occurred
Action Plan To Combat Cyber Crimes Summary Of Key Cyber Attacks OccurredThis slide shows the summary of key of cybers attacks occurred in organization such as phishing, malware attack, denial of service, SQL injections, identity thefts. It also contains details of the cyber attacker origin such as inadvertent actors, malicious insiders. Present the topic in a bit more detail with this Action Plan To Combat Cyber Crimes Summary Of Key Cyber Attacks Occurred. Use it as a tool for discussion and navigation on Cybers Attacks Occurred In Organization, Malware Attack, Denial Of Service, SQL Injections, Inadvertent Actors, Malicious Insiders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Compressive Planning Guide Cyber Attacks Faced By Organization
Compressive Planning Guide Cyber Attacks Faced By OrganizationThis slide provides information regarding the number of cyber attacks faced by the organization and its impact on IT operations and system downtime. It also provides details of percentage rise in such attacks since last month. Deliver an outstanding presentation on the topic using this Compressive Planning Guide Cyber Attacks Faced By Organization. Dispense information and present a thorough explanation of Cyber Attacks, IT Operations, System Downtime using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Compressive Planning Guide Dashboard For Tracking Cyber Attack Risk Levels
Compressive Planning Guide Dashboard For Tracking Cyber Attack Risk LevelsThe slide represents the dashboard for tracking cyber attack risk levels. It includes information regarding the multiple threat agents, attack methods, preventive controls along with details of risk score and infected systems. Deliver an outstanding presentation on the topic using this Compressive Planning Guide Dashboard For Tracking Cyber Attack Risk Levels. Dispense information and present a thorough explanation of Dashboard For Tracking, Cyber Attack Risk Levels, Preventive Controls, Risk Score And Infected Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Compressive Planning Guide Dashboard To Monitor Cyber Attack Incidents
Compressive Planning Guide Dashboard To Monitor Cyber Attack IncidentsThis slide indicates the dashboard to monitor cyber attacks on IT assets of the firm. It includes information regarding the total cyber attack incidents both month and day wise along with the details of threat class, overall risk factor and top vulnerabilities. Present the topic in a bit more detail with this Compressive Planning Guide Dashboard To Monitor Cyber Attack Incidents. Use it as a tool for discussion and navigation on Dashboard To Monitor, Cyber Attacks On IT Assets, Top Vulnerabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Compressive Planning Guide Summary Of Key Cyber Attacks Occurred
Compressive Planning Guide Summary Of Key Cyber Attacks OccurredThis slide shows the summary of key of cybers attacks occurred in organization such as phishing, malware attack, denial of service, SQL injections, identity thefts. It also contains details of the cyber attacker origin such as inadvertent actors, malicious insiders. Present the topic in a bit more detail with this Compressive Planning Guide Summary Of Key Cyber Attacks Occurred. Use it as a tool for discussion and navigation on Cybers Attacks Occurred, Malware Attack, Denial Of Service, Inadvertent Actors, Malicious Insiders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Targeted Industries Of Cyber Phishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Targeted Industries Of Cyber Phishing AttacksThis slide represents the statistics of most targeted industries of phishing scams. The purpose of this slide is to outline the various sectors which are more prone to phishing attacks. These industries are retail, manufacturing, food and beverage, tech, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Targeted Industries Of Cyber Phishing Attacks. Dispense information and present a thorough explanation of Phishing Scams, Phishing Attacks, Manufacturing, Food And Beverage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Vishing Cyber Scams In Different Businesses
Phishing Attacks And Strategies To Mitigate Them V2 Vishing Cyber Scams In Different BusinessesThis slide demonstrates the various types of vishing scams. The purpose of this slide is to illustrate the ways in which attackers conduct scams in different businesses using vishing technique. These are banking vishing and internal revenue service vishing. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Vishing Cyber Scams In Different Businesses. Use it as a tool for discussion and navigation on Attackers Conduct Scams, Vishing Technique, Internal Revenue Service Vishing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Cyber Attacks Impact On Organization In Previous Financial Year
Encryption Implementation Strategies Cyber Attacks Impact On Organization In Previous Financial YearThis slide depicts the financial loss experienced by the company in the last year due to different types of data privacy concerns. The purpose of this slide is to illustrate how increasing cyber scams have impacted the organization from april 2022 to april 2023. Present the topic in a bit more detail with this Encryption Implementation Strategies Cyber Attacks Impact On Organization In Previous Financial Year. Use it as a tool for discussion and navigation on Cyber Attacks, Financial Loss, Organization Experienced Loss, Data Privacy Concerns. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS V
Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS V This template helps you present information on Three stages. You can also present information on Spear Phishing, Whaling Phishing, Clone Phishing using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Attack Incident Tracking Dashboard Implementing Cyber Risk Management Process
Cyber Attack Incident Tracking Dashboard Implementing Cyber Risk Management ProcessThe following slide depicts the number of cyber-attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Present the topic in a bit more detail with this Cyber Attack Incident Tracking Dashboard Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Attack Trends, Attacks Allowed By Policy. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Causes Of Cyber Crimes And Attacks Implementing Cyber Risk Management Process
Major Causes Of Cyber Crimes And Attacks Implementing Cyber Risk Management ProcessThe following slide highlights the key reasons of cyber-attack to analyze and formulate actions. It includes key elements such asphysical theft, human error, insider misuse, old security vulnerabilities etc. Present the topic in a bit more detail with this Major Causes Of Cyber Crimes And Attacks Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Major Reasons. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber Attacks
Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber AttacksThis slide represents the different types of cyber-attacks throughout the year, including the percentage of total loss caused by these attacks. Present the topic in a bit more detail with this Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber Attacks. Use it as a tool for discussion and navigation on Cyber Attacks Throughout, Online Or Web Based Attacks, Malware Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attack Incident Tracking Dashboard Cyber Risk Assessment
Cyber Attack Incident Tracking Dashboard Cyber Risk AssessmentThe following slide depicts the number of cyber-attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Present the topic in a bit more detail with this Cyber Attack Incident Tracking Dashboard Cyber Risk Assessment Use it as a tool for discussion and navigation on Cyber Attack Incident, Tracking Dashboard This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Causes Of Cyber Crimes And Attacks Cyber Risk Assessment
Major Causes Of Cyber Crimes And Attacks Cyber Risk AssessmentThe following slide highlights the key reasons of cyber-attack to analyze and formulate actions. It includes key elements such as physical theft, human error, insider misuse, old security vulnerabilities etc. Present the topic in a bit more detail with this Major Causes Of Cyber Crimes And Attacks Cyber Risk Assessment Use it as a tool for discussion and navigation on Major Reasons, Major Causes, Cyber Crimes And Attacks This template is free to edit as deemed fit for your organization. Therefore download it now.




