Powerpoint Templates and Google slides for Cyber Threat Assessment
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Threats In Blockchain Conducting Vulnerability Assessment To Respond And Recover BCT SS V
Cyber Threats In Blockchain Conducting Vulnerability Assessment To Respond And Recover BCT SS VThe following slide showcases blockchain cybersecurity vulnerability assessment framework to optimize resilience and transparency. It includes key elements such as identify, protect, respond, recover, etc. Present the topic in a bit more detail with this Cyber Threats In Blockchain Conducting Vulnerability Assessment To Respond And Recover BCT SS V Use it as a tool for discussion and navigation on Identity, Protect, Detect This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threats In Blockchain Performing Threat Assessment For Cause Identification BCT SS V
Cyber Threats In Blockchain Performing Threat Assessment For Cause Identification BCT SS VThe following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Major Cybersecurity Challenges In Blockchain Technology BCT SS V Dispense information and present a thorough explanation of Double Spending, Mining Threats, Wallet Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Analyze And Rank Impact Of Cyber Threat Cyber Risk Assessment
Analyze And Rank Impact Of Cyber Threat Cyber Risk AssessmentThe following slide highlights the prioritization of cyber security threats to minimize possibility of likelihood and severity. It mainly includes elements such as vulnerability, threat, source, likelihood, impact and ranking etc. Present the topic in a bit more detail with this Analyze And Rank Impact Of Cyber Threat Cyber Risk Assessment Use it as a tool for discussion and navigation on Framework, Appropriate Structure, Internet Access This template is free to edit as deemed fit for your organization. Therefore download it now.
-
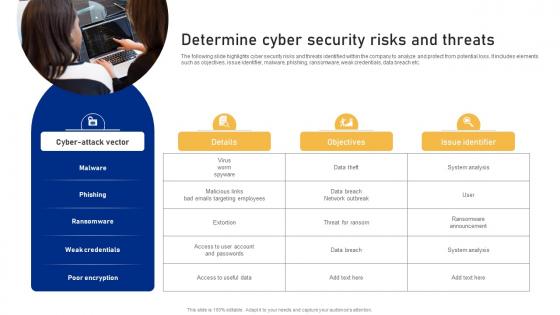 Determine Cyber Security Risks And Threats Cyber Risk Assessment
Determine Cyber Security Risks And Threats Cyber Risk AssessmentThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Increase audience engagement and knowledge by dispensing information using Determine Cyber Security Risks And Threats Cyber Risk Assessment This template helps you present information on three stages. You can also present information on Malware, Phishing, Ransomware, Weak Credentials using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Identify Threat And Vulnerabilities Within Information System Cyber Risk Assessment
Identify Threat And Vulnerabilities Within Information System Cyber Risk AssessmentThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Introducing Identify Threat And Vulnerabilities Within Information System Cyber Risk Assessment to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on No Framework, Monitor User Behavior, Vulnerability using this template. Grab it now to reap its full benefits.
-
 Cyber Propaganda And Ethical Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V
Cyber Propaganda And Ethical Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS VThis slide showcases various negative implications of leveraging ChatGPT for committing cybercrimes. Its key components are spreading propaganda, human bias and privacy plus security concerns. Introducing Cyber Propaganda And Ethical Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Spreading Propaganda, Privacy And Security Concerns, Propaganda, using this template. Grab it now to reap its full benefits.
-
 Types Of Cyber Attacks Faced By Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V
Types Of Cyber Attacks Faced By Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS VThis slide showcases various types of cyber attacks that significantly damage the organization resources and reputation. Different types of attacks faced are Malware, Phishing, Man in middle attack, SQL injection etc. Increase audience engagement and knowledge by dispensing information using Types Of Cyber Attacks Faced By Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V. This template helps you present information on five stages. You can also present information on Phishing, SQL Injection, Organization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security Threats
Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates checklist to evaluate third party risk assessment to eliminate unnecessary threats. It includes elements such as cyber security policies, patch management process, physical security guidelines, information safety etc. Deliver an outstanding presentation on the topic using this Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Parameters, Response, Status using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security Threat
Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the cyber security attack risk assessment matrix which can be leveraged to determine the severity of cyber threats, the likelihood of occurrence, and future action plan. Present the topic in a bit more detail with this Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Assessment Matrix, Occurrence, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber threat management workplace comparative assessment various threat
Cyber threat management workplace comparative assessment various threatThis slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Present the topic in a bit more detail with this Cyber Threat Management Workplace Comparative Assessment Various Threat. Use it as a tool for discussion and navigation on Insider Threat, Social Engineering, Insider Normal Operations And Maintenance Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber threat management workplace technological assessment firm current
Cyber threat management workplace technological assessment firm currentThis slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Present the topic in a bit more detail with this Cyber Threat Management Workplace Technological Assessment Firm Current. Use it as a tool for discussion and navigation on Parameters, Industry Standard, Firms Standard, Service Delay Rate. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it assessment matrix of cyber terrorism ppt slides picture
Cyberterrorism it assessment matrix of cyber terrorism ppt slides pictureThis slide demonstrate cyber terrorism in terms of cybercriminal actors, as well as the financial impact of successful cyber terrorists attacks. Present the topic in a bit more detail with this Cyberterrorism IT Assessment Matrix Of Cyber Terrorism Ppt Slides Picture. Use it as a tool for discussion and navigation on Organized Criminals, Financial Theft Froud, Business Destruction. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management comparative assessment various threat agents
Cyber security risk management comparative assessment various threat agentsThis slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an outstanding presentation on the topic using this Cyber Security Risk Management Comparative Assessment Various Threat Agents. Dispense information and present a thorough explanation of Insider Threat, Social Engineering, Threat Agents, Cyber Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Terrorism Attacks Assessment Matrix Of Cyber Terrorism
Cyber Terrorism Attacks Assessment Matrix Of Cyber TerrorismThis slide demonstrates the cyber terrorism attacks in terms of cybercriminal actors, as well as the financial impact of successful cyber terrorists attacks. Deliver an outstanding presentation on the topic using this Cyber Terrorism Attacks Assessment Matrix Of Cyber Terrorism. Dispense information and present a thorough explanation of Assessment Matrix Of Cyber Terrorism using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Terrorism Threats And Safeguard Assessment Matrix
Cyber Terrorism Threats And Safeguard Assessment MatrixThis slide represents the assessment matrix for cyber terrorism threats and its functions and safeguards. It includes functions such as identify, protect, detect, respond and recover and threats such as phishing, ransomware, web app attacks and vendor and partner data loss. Presenting our well structured Cyber Terrorism Threats And Safeguard Assessment Matrix. The topics discussed in this slide are Phishing, Ransomware, Deception Technology. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Threat Assessment Checklist With Solution
Cyber Security Threat Assessment Checklist With SolutionThe following slide highlights the cyber security threat assessment checklist with solution to assist management in decision making, id depicts threat, vulnerability, asset, consequences, risks and solution to control the risk. Introducing our Cyber Security Threat Assessment Checklist With Solution set of slides. The topics discussed in these slides are System Threat, Data Threat, Cloud Security Threat. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Prioritized Cyber Security Threats With Risk Mitigation Plan Risk Assessment Of It Systems
Prioritized Cyber Security Threats With Risk Mitigation Plan Risk Assessment Of It SystemsThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Prioritized Cyber Security Threats With Risk Mitigation Plan Risk Assessment Of It Systems. Use it as a tool for discussion and navigation on Mitigation Plan, Prioritized, Security Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of Various Cyber Threats Management To Enable Digital Assets Security
Comparative Assessment Of Various Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an outstanding presentation on the topic using this Comparative Assessment Of Various Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Comparative, Assessment, Parameters using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Analysis Of Cyber Security Threat Assessment Tools
Comparative Analysis Of Cyber Security Threat Assessment ToolsThis slide provides a comparative analysis of various tools to detect and assess cyber security threats in the industry to gain insights about which tool to implement. The major tools are Nessus home, GFI Languard, QualysGuard and n Circle IP 360 Presenting our well structured Comparative Analysis Of Cyber Security Threat Assessment Tools. The topics discussed in this slide are Nessus Home, Compatible Mechanisms. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber threat assessment template ppt powerpoint presentation styles structure cpb
Cyber threat assessment template ppt powerpoint presentation styles structure cpbPresenting this set of slides with name Cyber Threat Assessment Template Ppt Powerpoint Presentation Styles Structure Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Cyber Threat Assessment Template to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.



