Powerpoint Templates and Google slides for Cyber Systems
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Physical Systems CPS In Powerpoint And Google Slides
Cyber Physical Systems CPS In Powerpoint And Google SlidesThis complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fifty eight slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.
-
 Computer system security cyber attacks experienced by company in previous financial year
Computer system security cyber attacks experienced by company in previous financial yearThis slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2021. Present the topic in a bit more detail with this Computer System Security Cyber Attacks Experienced By Company In Previous Financial Year. Use it as a tool for discussion and navigation on Cyber Attacks Experienced By Company In Previous Financial Year. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
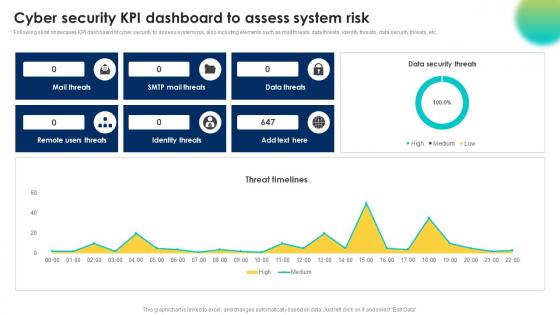 Cyber Security Kpi Dashboard To Assess System Risk
Cyber Security Kpi Dashboard To Assess System RiskFollowing slide showcases KPI dashboard of cyber security to assess system risk, also including elements such as mail threats, data threats, identity threats, data security threats, etc. Presenting our well structured Cyber Security Kpi Dashboard To Assess System Risk. The topics discussed in this slide are Identity Threats, Remote Users Threats, Data Threats. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Computer system security assessment matrix of cyber risks ppt grid
Computer system security assessment matrix of cyber risks ppt gridThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Increase audience engagement and knowledge by dispensing information using Computer System Security Assessment Matrix Of Cyber Risks Ppt Grid. This template helps you present information on one stages. You can also present information on Industrial, Data Center, Multifamily, Retail, Access using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
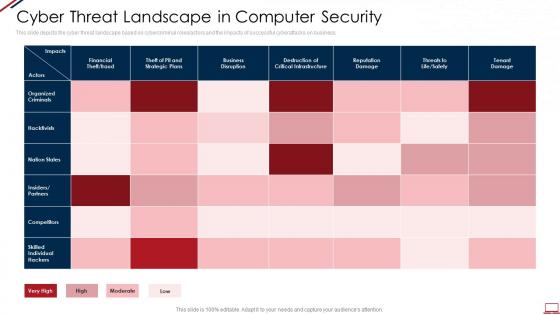 Computer system security cyber threat landscape in computer security
Computer system security cyber threat landscape in computer securityThis slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Present the topic in a bit more detail with this Computer System Security Cyber Threat Landscape In Computer Security. Use it as a tool for discussion and navigation on Financial, Business, Tenant Damage, Organized Criminals, Competitors. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security strategies to manage cyber risks
Computer system security strategies to manage cyber risksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Introducing Computer System Security Strategies To Manage Cyber Risks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Secure, Vigilant, Resilient, Implementation, Awareness, using this template. Grab it now to reap its full benefits.
-
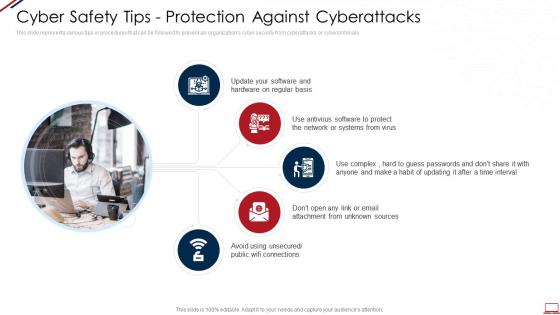 Cyber safety tips protection against cyberattacks computer system security
Cyber safety tips protection against cyberattacks computer system securityThis slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Increase audience engagement and knowledge by dispensing information using Cyber Safety Tips Protection Against Cyberattacks Computer System Security. This template helps you present information on five stages. You can also present information on Cyber Safety Tips Protection Against Cyberattacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Advanced Technologies Various Types Of Cyber Attacks On System
Advanced Technologies Various Types Of Cyber Attacks On SystemThis slide explains Various types of cyber attacks on system on a system such as malware, phishing, man in the middle, distributed denial of service, brute force, SQL injection, and domain name system. Introducing Advanced Technologies Various Types Of Cyber Attacks On System to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Malware, Phishing, Brute Force, using this template. Grab it now to reap its full benefits.
-
 Case Study Of Financial Institution And Cyber Security System
Case Study Of Financial Institution And Cyber Security SystemThis slide represents case study on use of cybersecurity system in financial institution. This further includes about client, challenges, solutions and results after using cyber security system. Presenting our set of slides with Case Study Of Financial Institution And Cyber Security System. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Financial Services, Customer Data, Management.
-
 Cloud Cyber Security System Architecture
Cloud Cyber Security System ArchitectureThis slide showcases cyber security system architecture for business cloud data protection from hacks. This further includes key takeaways such as business having cloud misconfiguration that pose serious hazards. Introducing our Cloud Cyber Security System Architecture set of slides. The topics discussed in these slides are Emulated Components, Cyber Security, System Architecture. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Futuristic Trends In Cyber Security System
Futuristic Trends In Cyber Security SystemThis slide represents cyber security system futuristic trends. This further includes remote work, automate, adopt zero trust principles, improve response capabilities and recognize supply chain risks. Presenting our set of slides with Futuristic Trends In Cyber Security System. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Remote Work, Trust Principles, Response Capabilities.
-
 Global Cyber Security System Market Size Overview
Global Cyber Security System Market Size OverviewThis slide showcases market size overview for global cyber security system. This further includes key takeaways and data projection such as 175 billion dollars to 300 billion dollars by 2027 and about growth rate increase. Introducing our premium set of slides with Global Cyber Security System Market Size Overview. Ellicudate the one stage and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Global Cyber Security System, Market Size Overview. So download instantly and tailor it with your information.
-
 Information System Shield For Cyber Security Icon
Information System Shield For Cyber Security IconIntroducing our premium set of slides with Information System Shield For Cyber Security Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information System, Shield For Cyber Security Icon. So download instantly and tailor it with your information.
-
 IOT Solution Components In Cyber Security System
IOT Solution Components In Cyber Security SystemThis slide highlights cyber security system components for IOT solutions. This includes secure device, secure communication, secured cloud and further includes messaging control and device integrated connections. Presenting our set of slides with IOT Solution Components In Cyber Security System. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secure Device, Secure Communication, Secured Cloud.
-
 Emerging Technologies Various Types Of Cyber Attacks On System
Emerging Technologies Various Types Of Cyber Attacks On SystemThis slide explains Various types of cyber attacks on system on a system such as malware, phishing, man in the middle, distributed denial of service, brute force, SQL injection, and domain name system. Increase audience engagement and knowledge by dispensing information using Emerging Technologies Various Types Of Cyber Attacks On System. This template helps you present information on seven stages. You can also present information on Malware, Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Trending Technologies Various Types Of Cyber Attacks On System
Trending Technologies Various Types Of Cyber Attacks On SystemThis slide explains Various types of cyber attacks on system on a system such as malware, phishing, man in the middle, distributed denial of service, brute force, SQL injection, and domain name system. Increase audience engagement and knowledge by dispensing information using Trending Technologies Various Types Of Cyber Attacks On System. This template helps you present information on eight stages. You can also present information on Malware, Phishing, Brute Force using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various Types Of Cyber Attacks On System Modern Technologies
Various Types Of Cyber Attacks On System Modern TechnologiesThis slide explains Various types of cyber attacks on system on a system such as malware,phishing,man in the middle,distributed denial of service,brute force,SQL injection,and domain name system. Introducing Various Types Of Cyber Attacks On System Modern Technologies to increase your presentation threshold. Encompassed with seven stages,this template is a great option to educate and entice your audience. Dispence information on Information Found,Conceivable Using,Cryptographic Trick,using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Discovery Identifying Potential Vulnerabilities In System BCT SS V
Cyber Threats In Blockchain Discovery Identifying Potential Vulnerabilities In System BCT SS VThe following slide showcases key phases of penetration testing to identify potential flaws and malware. It includes elements of discovery phase such as architecture, compliance readiness, readiness analysis, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Discovery Identifying Potential Vulnerabilities In System BCT SS V This template helps you present information on Three stages. You can also present information on Architecture Of Blockchain, Compliance Readiness, Readiness Analysis using this PPT design. This layout is completely editable so personaize it now
-
 Elements Of Systems Applications And Products Cyber Security
Elements Of Systems Applications And Products Cyber SecurityThis slide depicts the components of SAP cybersecurity. The purpose of this template is to help understand the areas of business networks that can be safeguarded with the help of SAP cybersecurity elements. It includes data base security, infrastructure security, etc. Presenting our set of slides with Elements Of Systems Applications And Products Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Database Security, Operating System Security, Network Security, Infrastructure Security.
-
 Use Cases Of System Application And Product Cyber Security
Use Cases Of System Application And Product Cyber SecurityThis template depicts the applications of SAP cyber security. The purpose of this slide is to help the business leverage SAP cybersecurity to improve its internal network safety. It includes use cases such as ensuring data integrity, identification of unauthorized access, etc. Presenting our well structured Use Cases Of System Application And Product Cyber Security. The topics discussed in this slide are Prevent Exploitation And Fraud, Ensuring Data Integrity, Continuous Results. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Current Trending Technologies Various Types Of Cyber Attacks On System
Current Trending Technologies Various Types Of Cyber Attacks On SystemThis slide explains Various types of cyber attacks on system on a system such as malware, phishing, man in the middle, distributed denial of service, brute force, SQL injection, and domain name system. Introducing Current Trending Technologies Various Types Of Cyber Attacks On System to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Attacks On System, Distributed Denial Of Service, Cryptographic Trick, Cybercriminals Disable Targeted Servers, using this template. Grab it now to reap its full benefits.
-
 New Technologies Various Types Of Cyber Attacks On System
New Technologies Various Types Of Cyber Attacks On SystemThis slide explains Various types of cyber attacks on system on a system such as malware, phishing, man in the middle, distributed denial of service, brute force, SQL injection, and domain name system. Introducing New Technologies Various Types Of Cyber Attacks On System to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Malware, Phishing, Distributed, using this template. Grab it now to reap its full benefits.
-
 Identify Threat And Vulnerabilities Within Information System Cyber Risk Assessment
Identify Threat And Vulnerabilities Within Information System Cyber Risk AssessmentThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Introducing Identify Threat And Vulnerabilities Within Information System Cyber Risk Assessment to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on No Framework, Monitor User Behavior, Vulnerability using this template. Grab it now to reap its full benefits.
-
 Identify Threat And Vulnerabilities Within Information System Creating Cyber Security Awareness
Identify Threat And Vulnerabilities Within Information System Creating Cyber Security AwarenessThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Deliver an outstanding presentation on the topic using this Identify Threat And Vulnerabilities Within Information System Creating Cyber Security Awareness Dispense information and present a thorough explanation of Unclear Storage Mechanism, Monitor User Behaviour, No Appropriate Structure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Industry 4 0 Cyber Physical System And Adoption In Manufacturing Enabling Smart Production DT SS
Industry 4 0 Cyber Physical System And Adoption In Manufacturing Enabling Smart Production DT SSThis slide covers Industry 4.0 generated cyber physical system in manufacturing and production process. It involves key elements such as physical, computational and communication elements such as machines, robots and technological capabilities. Introducing Industry 4 0 Cyber Physical System And Adoption In Manufacturing Enabling Smart Production DT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Physical System, Effective Process Monitoring, Physical Elements using this template. Grab it now to reap its full benefits.
-
 Organizational Csirt Cyber Security System
Organizational Csirt Cyber Security SystemThis slide showcases framework of CSIRT cyber security. The main purpose of this template is conflicting management and collective learning. This includes technology, CSIRT processes, CSIRT level situation, etc. Introducing our Organizational Csirt Cyber Security System set of slides. The topics discussed in these slides are Event Management, Conflict Management, Collective Learning. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Triage Cyber Security For System Protection Icon
Triage Cyber Security For System Protection IconPresenting our set of slides with name Triage Cyber Security For System Protection Icon This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Triage Cyber Security, System Protection Icon
-
 Industry 4 0 Cyber Physical System And Adoption Ensuring Quality Products By Leveraging DT SS V
Industry 4 0 Cyber Physical System And Adoption Ensuring Quality Products By Leveraging DT SS VThis slide covers Industry 4.0 generated cyber physical system in manufacturing and production process. It involves key elements such as physical, computational and communication elements such as machines, robots and technological capabilities. Deliver an outstanding presentation on the topic using this Industry 4 0 Cyber Physical System And Adoption Ensuring Quality Products By Leveraging DT SS V Dispense information and present a thorough explanation of Physical Elements, Computational Elements, Communication Elements using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber Security
Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber SecurityThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Deliver an outstanding presentation on the topic using this Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber Security Dispense information and present a thorough explanation of Vulnerability, Threat, Threat Source using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Infrastructure Cyber Security System Icon
Infrastructure Cyber Security System IconIntroducing our premium set of slides with Infrastructure Cyber Security System Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Infrastructure, Cyber, Security. So download instantly and tailor it with your information.
-
 ATP Cyber Security System Process
ATP Cyber Security System ProcessThis slide showcases the ATP cyber security process. Its aim is to help define the target and identify the anomalies. This slide includes researching target, acquiring tools, detection of virus, strengthening the system, remove virus, etc. Presenting our set of slides with name ATP Cyber Security System Process. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Plan, Intrusion, Getting Out, Sub Zero.
-
 ATP Cyber Security Threat Detection System
ATP Cyber Security Threat Detection SystemThis slide depicts the ATP cyber security detection system. Its aim is to use various approach to kill off any threats during cyber attack. This slide includes multilayer approach, behavioural analysis, machine learning, sand boxing, threat intelligence, etc. Presenting our set of slides with name ATP Cyber Security Threat Detection System. This exhibits information on Nine stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Multilayered Approach, Behavioural Analysis, Machine Learning, Threat Intelligence, Endpoint Detection.
-
 Network Intrusion Prevention Cyber Security System
Network Intrusion Prevention Cyber Security SystemThis slide highlights the network intrusion prevention system cybersecurity. The purpose of this slide is to help ensure that suitable processes are undertaken during security incidents. It includes elements such as network perimeters, internet, LAN, etc. Introducing our Network Intrusion Prevention Cyber Security System set of slides. The topics discussed in these slides are Internet, Network Perimeter, Prevention Systems This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Importance Of Cyber Security In Automotive Systems
Importance Of Cyber Security In Automotive SystemsThis slide highlights relevance of cyber security in vehicles. The purpose of this slide is to aid professionals in ensuring safety, privacy and functionality of automobiles against potential cyber threats and attacks. It includes elements such as safety, data protection, etc. Presenting our set of slides with Importance Of Cyber Security In Automotive Systems This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Protection, Vehicle Integrity, Financial Implications.
-
 Use Case Of Cyber Security In Automotive Systems
Use Case Of Cyber Security In Automotive SystemsThis slide highlights application of cyber security to automotive components. The purpose of this slide is to assist businesses in protecting vehicles from system manipulation in interconnected environment. It includes elements such as access control, data encryption, etc. Introducing our premium set of slides with Use Case Of Cyber Security In Automotive Systems Ellicudate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Control, Data Encryption, Firmware Updates So download instantly and tailor it with your information.
-
 Advantages Of Hids Based Cyber Security Systems
Advantages Of Hids Based Cyber Security SystemsThis slide represents advantages of HIDS based cyber security which assists organizations to monitor process and applications running on devices. It includes advantages such as monitor system activities, detects attacks, etc Presenting our set of slides with Advantages Of Hids Based Cyber Security Systems. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Monitors System Activities, Lowers Entry Cost, Verifies Success Or Failures Of Attacks.
-
 Key Challenges To Hids Cyber Security System
Key Challenges To Hids Cyber Security SystemThis slide represents key challenges to HIDS cyber security system which hinders effective deployment of system and reduces detection rate. It includes key challenges to HIDS cyber security system, such as ensuring effective deployment, etc Presenting our well structured Key Challenges To Hids Cyber Security System. The topics discussed in this slide are Knowledge, Deployment, Investigate. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Attacks Detection In Iot Systems Strategic Guide To Implement Strategy SS
Cyber Attacks Detection In Iot Systems Strategic Guide To Implement Strategy SSPresent the topic in a bit more detail with this Cyber Attacks Detection In Iot Systems Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Social Media, Gamepad, Firewall, Storage, Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing advanced system workplace addressing cyber risk management dashboard
Implementing advanced system workplace addressing cyber risk management dashboardThis slide portrays information regarding the dashboard that firm will use to manage cyber risks. The dashboard will provide clear picture of risk prevailing and how they are treated to technical engineers and board level executives.Present the topic in a bit more detail with this Implementing Advanced System Workplace Addressing Cyber Risk Management Dashboard. Use it as a tool for discussion and navigation on Management, Dashboard, Cyber. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cost Breakdown Points Incurred On Cyber Security System Failures
Cost Breakdown Points Incurred On Cyber Security System FailuresThis slide depicts different points leading to failures to set up an effective security system. It includes the cost borne by company due to failures in log management, communication over unauthorized ports, asset inventory, failures of anti-malware software, etc. Introducing our Cost Breakdown Points Incurred On Cyber Security System Failures set of slides. The topics discussed in these slides are Cost Breakdown Points, Cyber Security, System Failures. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Global Cyber Physical Systems Market Share Ppt Powerpoint Presentation File Guide
Global Cyber Physical Systems Market Share Ppt Powerpoint Presentation File GuideThis slide shows the global cyber physical systems market share, including North America, Europe, Asia Pacific, South America, and the Middle East and Africa. Deliver an outstanding presentation on the topic using this Global Cyber Physical Systems Market Share Ppt Powerpoint Presentation File Guide. Dispense information and present a thorough explanation of Cyber Physical Systems, Market Share using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Intelligent System Global Cyber Physical Systems Market Share
Intelligent System Global Cyber Physical Systems Market ShareThis slide shows the global cyber-physical systems market share, including North America, Europe, Asia Pacific, South America, and the Middle East and Africa. Deliver an outstanding presentation on the topic using this Intelligent System Global Cyber Physical Systems Market Share. Dispense information and present a thorough explanation of Physical, Systems, Market Share using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Global Cyber Physical Systems Market Share Next Generation Computing Systems
Global Cyber Physical Systems Market Share Next Generation Computing SystemsThis slide shows the global cyber-physical systems market share, including North America, Europe, Asia Pacific, South America, and the Middle East and Africa. Present the topic in a bit more detail with this Global Cyber Physical Systems Market Share Next Generation Computing Systems. Use it as a tool for discussion and navigation on Global Cyber, Physical Systems. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Faced By Organization Previous Financial Year Information System Security And Risk Administration
Cyber Attacks Faced By Organization Previous Financial Year Information System Security And Risk AdministrationThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Deliver an outstanding presentation on the topic using this Cyber Attacks Faced By Organization Previous Financial Year Information System Security And Risk Administration. Dispense information and present a thorough explanation of Organization Experienced, Increasing A Rapid Rate, Financial Year using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Systems Monitoring Report Ppt Powerpoint Presentation Show Background Images
Cyber Security Systems Monitoring Report Ppt Powerpoint Presentation Show Background ImagesThis slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Deliver an outstanding presentation on the topic using this Cyber Security Systems Monitoring Report Ppt Powerpoint Presentation Show Background Images. Dispense information and present a thorough explanation of Cyber Security, Intrusion Attempts, Monitoring Report using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Systems Monitoring Report Incident Response Strategies Deployment
Cyber Security Systems Monitoring Report Incident Response Strategies DeploymentThis slide represents the report to effectively monitor the networks and systems of the organization. It includes kpis such as total intrusion attempts, mean detect team, mean resolve time etc. Present the topic in a bit more detail with this Cyber Security Systems Monitoring Report Incident Response Strategies Deployment. Use it as a tool for discussion and navigation on Success, Resolve, Intrusion. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
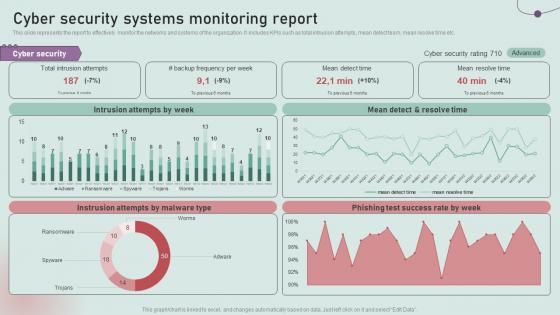 Cyber Security Systems Monitoring Report Development And Implementation Of Security Incident Management
Cyber Security Systems Monitoring Report Development And Implementation Of Security Incident ManagementThis slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Deliver an outstanding presentation on the topic using this Cyber Security Systems Monitoring Report Development And Implementation Of Security Incident Management. Dispense information and present a thorough explanation of Intrusion Attempts, Mean Detect, Resolve Time using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Cyber Security Systems Monitoring Report
Cyber Security Attacks Response Plan Cyber Security Systems Monitoring ReportThis slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Cyber Security Systems Monitoring Report. Use it as a tool for discussion and navigation on Cyber Security Systems, Monitoring Report, Mean Detect And Resolve Time. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
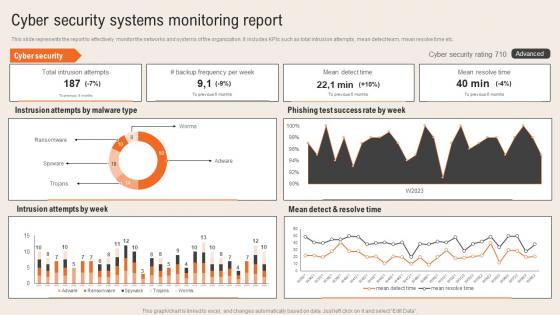 Cyber Security Systems Monitoring Report Deploying Computer Security Incident Management
Cyber Security Systems Monitoring Report Deploying Computer Security Incident ManagementThis slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc.Present the topic in a bit more detail with this Cyber Security Systems Monitoring Report Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Intrusion Attempts, Ransomware, Phishing Test Success. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security threat management system
Cyber security threat management systemThe following slide illustrates the cyber security threat management system which includes threat containment, logging and traceability management. Introducing our Cyber Security Threat Management System set of slides. The topics discussed in these slides are Threat Containment And Remediation, Identify Management, Application Visibility And Control. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber threat report with risk indicator and affected systems
Cyber threat report with risk indicator and affected systemsPresenting our well structured Cyber Threat Report With Risk Indicator And Affected Systems. The topics discussed in this slide are Risk Level, Risk Indication, Potential Affected Systems. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyberterrorism it scada system misused for cyber terrorism
Cyberterrorism it scada system misused for cyber terrorismThis slide describes the SCADA system as a tool misused for cyberterrorism and any damage to the SCADA can cause a major physical damage. Introducing Cyberterrorism IT SCADA System Misused For Cyber Terrorism to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on SCADA Operator Terminal, Alarm Monitor, Radio Cellular Telemetry, Control System Adjustments, Instrumentation Inputs, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it techniques to protect scada systems from cyber attacks
Cyberterrorism it techniques to protect scada systems from cyber attacksThis slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls. Deliver an outstanding presentation on the topic using this Cyberterrorism IT Techniques To Protect SCADA Systems From Cyber Attacks. Dispense information and present a thorough explanation of Security Training, Employee, Access Controls, Strict Firewalls, Network Security Procedures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SCADA System Misused For Cyber Terrorism Cyber Terrorism Attacks
SCADA System Misused For Cyber Terrorism Cyber Terrorism AttacksThis slide describes the SCADA system as a tool misused for cyberterrorism and any damage to the SCADA can cause a major physical damage.. Present the topic in a bit more detail with this SCADA System Misused For Cyber Terrorism Cyber Terrorism Attacks. Use it as a tool for discussion and navigation on Scada System Misused For Cyber Terrorism. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Techniques To Protect SCADA Systems From Cyber Terrorism Attacks
Techniques To Protect SCADA Systems From Cyber Terrorism AttacksThis slide depicts the techniques to protect SCADA from cyber attacks which include security training of employees, strict firewalls. Increase audience engagement and knowledge by dispensing information using Techniques To Protect SCADA Systems From Cyber Terrorism Attacks. This template helps you present information on six stages. You can also present information on Security Training, Access Controls, Strict Firewalls, Security Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 System Cyber Risk Colored Icon In Powerpoint Pptx Png And Editable Eps Format
System Cyber Risk Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable System cyber risk colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 System Cyber Risk Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
System Cyber Risk Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable System cyber risk monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Table Of Contents Cyber Physical Systems CPS Ppt Powerpoint Presentation File Layout
Table Of Contents Cyber Physical Systems CPS Ppt Powerpoint Presentation File LayoutIncrease audience engagement and knowledge by dispensing information using Table Of Contents Cyber Physical Systems CPS Ppt Powerpoint Presentation File Layout. This template helps you present information on eleven stages. You can also present information on Cyber Physical Systems, Roadmap, Concept Map using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 5C Architecture Of Cyber Physical Systems Ppt Powerpoint Presentation File Files
5C Architecture Of Cyber Physical Systems Ppt Powerpoint Presentation File FilesThis slide represents the 5C architecture of cyber physical systems, including connection, conversion, cyber, cognition, and configuration. Introducing 5C Architecture Of Cyber Physical Systems Ppt Powerpoint Presentation File Files to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Performance Forecasting, Data Correlation, Decision Making, using this template. Grab it now to reap its full benefits.
-
 30 60 90 Days Plan For CPS Development Cyber Physical Systems Ppt Powerpoint Presentation File
30 60 90 Days Plan For CPS Development Cyber Physical Systems Ppt Powerpoint Presentation FileThis slide represents the 30 60 90 days plan for cyber physical systems development, including the tasks performed at monthly intervals such as requirement gathering, planning and so on. Increase audience engagement and knowledge by dispensing information using 30 60 90 Days Plan For CPS Development Cyber Physical Systems Ppt Powerpoint Presentation File. This template helps you present information on three stages. You can also present information on Cyber Physical Systems, Employees And Users, Business Operations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.




