Powerpoint Templates and Google slides for Cyber Security Systems
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Computer system security cyber attacks experienced by company in previous financial year
Computer system security cyber attacks experienced by company in previous financial yearThis slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2021. Present the topic in a bit more detail with this Computer System Security Cyber Attacks Experienced By Company In Previous Financial Year. Use it as a tool for discussion and navigation on Cyber Attacks Experienced By Company In Previous Financial Year. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
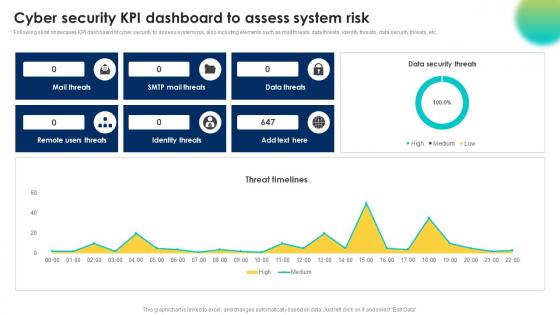 Cyber Security Kpi Dashboard To Assess System Risk
Cyber Security Kpi Dashboard To Assess System RiskFollowing slide showcases KPI dashboard of cyber security to assess system risk, also including elements such as mail threats, data threats, identity threats, data security threats, etc. Presenting our well structured Cyber Security Kpi Dashboard To Assess System Risk. The topics discussed in this slide are Identity Threats, Remote Users Threats, Data Threats. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Computer system security assessment matrix of cyber risks ppt grid
Computer system security assessment matrix of cyber risks ppt gridThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Increase audience engagement and knowledge by dispensing information using Computer System Security Assessment Matrix Of Cyber Risks Ppt Grid. This template helps you present information on one stages. You can also present information on Industrial, Data Center, Multifamily, Retail, Access using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
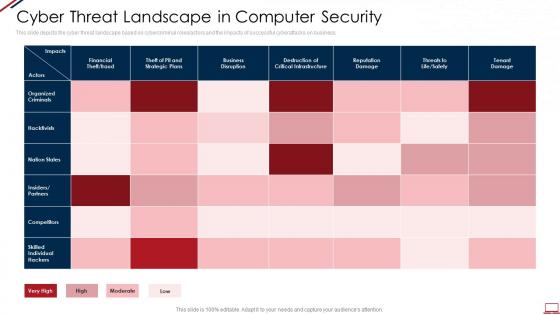 Computer system security cyber threat landscape in computer security
Computer system security cyber threat landscape in computer securityThis slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Present the topic in a bit more detail with this Computer System Security Cyber Threat Landscape In Computer Security. Use it as a tool for discussion and navigation on Financial, Business, Tenant Damage, Organized Criminals, Competitors. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security strategies to manage cyber risks
Computer system security strategies to manage cyber risksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Introducing Computer System Security Strategies To Manage Cyber Risks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Secure, Vigilant, Resilient, Implementation, Awareness, using this template. Grab it now to reap its full benefits.
-
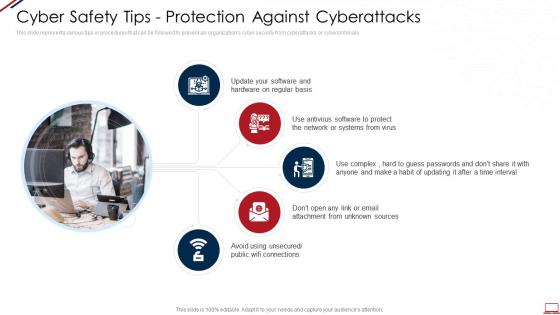 Cyber safety tips protection against cyberattacks computer system security
Cyber safety tips protection against cyberattacks computer system securityThis slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Increase audience engagement and knowledge by dispensing information using Cyber Safety Tips Protection Against Cyberattacks Computer System Security. This template helps you present information on five stages. You can also present information on Cyber Safety Tips Protection Against Cyberattacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Case Study Of Financial Institution And Cyber Security System
Case Study Of Financial Institution And Cyber Security SystemThis slide represents case study on use of cybersecurity system in financial institution. This further includes about client, challenges, solutions and results after using cyber security system. Presenting our set of slides with Case Study Of Financial Institution And Cyber Security System. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Financial Services, Customer Data, Management.
-
 Cloud Cyber Security System Architecture
Cloud Cyber Security System ArchitectureThis slide showcases cyber security system architecture for business cloud data protection from hacks. This further includes key takeaways such as business having cloud misconfiguration that pose serious hazards. Introducing our Cloud Cyber Security System Architecture set of slides. The topics discussed in these slides are Emulated Components, Cyber Security, System Architecture. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Futuristic Trends In Cyber Security System
Futuristic Trends In Cyber Security SystemThis slide represents cyber security system futuristic trends. This further includes remote work, automate, adopt zero trust principles, improve response capabilities and recognize supply chain risks. Presenting our set of slides with Futuristic Trends In Cyber Security System. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Remote Work, Trust Principles, Response Capabilities.
-
 Global Cyber Security System Market Size Overview
Global Cyber Security System Market Size OverviewThis slide showcases market size overview for global cyber security system. This further includes key takeaways and data projection such as 175 billion dollars to 300 billion dollars by 2027 and about growth rate increase. Introducing our premium set of slides with Global Cyber Security System Market Size Overview. Ellicudate the one stage and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Global Cyber Security System, Market Size Overview. So download instantly and tailor it with your information.
-
 Information System Shield For Cyber Security Icon
Information System Shield For Cyber Security IconIntroducing our premium set of slides with Information System Shield For Cyber Security Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information System, Shield For Cyber Security Icon. So download instantly and tailor it with your information.
-
 IOT Solution Components In Cyber Security System
IOT Solution Components In Cyber Security SystemThis slide highlights cyber security system components for IOT solutions. This includes secure device, secure communication, secured cloud and further includes messaging control and device integrated connections. Presenting our set of slides with IOT Solution Components In Cyber Security System. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secure Device, Secure Communication, Secured Cloud.
-
 Elements Of Systems Applications And Products Cyber Security
Elements Of Systems Applications And Products Cyber SecurityThis slide depicts the components of SAP cybersecurity. The purpose of this template is to help understand the areas of business networks that can be safeguarded with the help of SAP cybersecurity elements. It includes data base security, infrastructure security, etc. Presenting our set of slides with Elements Of Systems Applications And Products Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Database Security, Operating System Security, Network Security, Infrastructure Security.
-
 Use Cases Of System Application And Product Cyber Security
Use Cases Of System Application And Product Cyber SecurityThis template depicts the applications of SAP cyber security. The purpose of this slide is to help the business leverage SAP cybersecurity to improve its internal network safety. It includes use cases such as ensuring data integrity, identification of unauthorized access, etc. Presenting our well structured Use Cases Of System Application And Product Cyber Security. The topics discussed in this slide are Prevent Exploitation And Fraud, Ensuring Data Integrity, Continuous Results. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Identify Threat And Vulnerabilities Within Information System Creating Cyber Security Awareness
Identify Threat And Vulnerabilities Within Information System Creating Cyber Security AwarenessThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Deliver an outstanding presentation on the topic using this Identify Threat And Vulnerabilities Within Information System Creating Cyber Security Awareness Dispense information and present a thorough explanation of Unclear Storage Mechanism, Monitor User Behaviour, No Appropriate Structure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Organizational Csirt Cyber Security System
Organizational Csirt Cyber Security SystemThis slide showcases framework of CSIRT cyber security. The main purpose of this template is conflicting management and collective learning. This includes technology, CSIRT processes, CSIRT level situation, etc. Introducing our Organizational Csirt Cyber Security System set of slides. The topics discussed in these slides are Event Management, Conflict Management, Collective Learning. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Triage Cyber Security For System Protection Icon
Triage Cyber Security For System Protection IconPresenting our set of slides with name Triage Cyber Security For System Protection Icon This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Triage Cyber Security, System Protection Icon
-
 Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber Security
Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber SecurityThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Deliver an outstanding presentation on the topic using this Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber Security Dispense information and present a thorough explanation of Vulnerability, Threat, Threat Source using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Infrastructure Cyber Security System Icon
Infrastructure Cyber Security System IconIntroducing our premium set of slides with Infrastructure Cyber Security System Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Infrastructure, Cyber, Security. So download instantly and tailor it with your information.
-
 ATP Cyber Security System Process
ATP Cyber Security System ProcessThis slide showcases the ATP cyber security process. Its aim is to help define the target and identify the anomalies. This slide includes researching target, acquiring tools, detection of virus, strengthening the system, remove virus, etc. Presenting our set of slides with name ATP Cyber Security System Process. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Plan, Intrusion, Getting Out, Sub Zero.
-
 ATP Cyber Security Threat Detection System
ATP Cyber Security Threat Detection SystemThis slide depicts the ATP cyber security detection system. Its aim is to use various approach to kill off any threats during cyber attack. This slide includes multilayer approach, behavioural analysis, machine learning, sand boxing, threat intelligence, etc. Presenting our set of slides with name ATP Cyber Security Threat Detection System. This exhibits information on Nine stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Multilayered Approach, Behavioural Analysis, Machine Learning, Threat Intelligence, Endpoint Detection.
-
 Network Intrusion Prevention Cyber Security System
Network Intrusion Prevention Cyber Security SystemThis slide highlights the network intrusion prevention system cybersecurity. The purpose of this slide is to help ensure that suitable processes are undertaken during security incidents. It includes elements such as network perimeters, internet, LAN, etc. Introducing our Network Intrusion Prevention Cyber Security System set of slides. The topics discussed in these slides are Internet, Network Perimeter, Prevention Systems This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Importance Of Cyber Security In Automotive Systems
Importance Of Cyber Security In Automotive SystemsThis slide highlights relevance of cyber security in vehicles. The purpose of this slide is to aid professionals in ensuring safety, privacy and functionality of automobiles against potential cyber threats and attacks. It includes elements such as safety, data protection, etc. Presenting our set of slides with Importance Of Cyber Security In Automotive Systems This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Protection, Vehicle Integrity, Financial Implications.
-
 Use Case Of Cyber Security In Automotive Systems
Use Case Of Cyber Security In Automotive SystemsThis slide highlights application of cyber security to automotive components. The purpose of this slide is to assist businesses in protecting vehicles from system manipulation in interconnected environment. It includes elements such as access control, data encryption, etc. Introducing our premium set of slides with Use Case Of Cyber Security In Automotive Systems Ellicudate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Control, Data Encryption, Firmware Updates So download instantly and tailor it with your information.
-
 Advantages Of Hids Based Cyber Security Systems
Advantages Of Hids Based Cyber Security SystemsThis slide represents advantages of HIDS based cyber security which assists organizations to monitor process and applications running on devices. It includes advantages such as monitor system activities, detects attacks, etc Presenting our set of slides with Advantages Of Hids Based Cyber Security Systems. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Monitors System Activities, Lowers Entry Cost, Verifies Success Or Failures Of Attacks.
-
 Key Challenges To Hids Cyber Security System
Key Challenges To Hids Cyber Security SystemThis slide represents key challenges to HIDS cyber security system which hinders effective deployment of system and reduces detection rate. It includes key challenges to HIDS cyber security system, such as ensuring effective deployment, etc Presenting our well structured Key Challenges To Hids Cyber Security System. The topics discussed in this slide are Knowledge, Deployment, Investigate. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cost Breakdown Points Incurred On Cyber Security System Failures
Cost Breakdown Points Incurred On Cyber Security System FailuresThis slide depicts different points leading to failures to set up an effective security system. It includes the cost borne by company due to failures in log management, communication over unauthorized ports, asset inventory, failures of anti-malware software, etc. Introducing our Cost Breakdown Points Incurred On Cyber Security System Failures set of slides. The topics discussed in these slides are Cost Breakdown Points, Cyber Security, System Failures. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Attacks Faced By Organization Previous Financial Year Information System Security And Risk Administration
Cyber Attacks Faced By Organization Previous Financial Year Information System Security And Risk AdministrationThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Deliver an outstanding presentation on the topic using this Cyber Attacks Faced By Organization Previous Financial Year Information System Security And Risk Administration. Dispense information and present a thorough explanation of Organization Experienced, Increasing A Rapid Rate, Financial Year using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Systems Monitoring Report Ppt Powerpoint Presentation Show Background Images
Cyber Security Systems Monitoring Report Ppt Powerpoint Presentation Show Background ImagesThis slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Deliver an outstanding presentation on the topic using this Cyber Security Systems Monitoring Report Ppt Powerpoint Presentation Show Background Images. Dispense information and present a thorough explanation of Cyber Security, Intrusion Attempts, Monitoring Report using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Systems Monitoring Report Incident Response Strategies Deployment
Cyber Security Systems Monitoring Report Incident Response Strategies DeploymentThis slide represents the report to effectively monitor the networks and systems of the organization. It includes kpis such as total intrusion attempts, mean detect team, mean resolve time etc. Present the topic in a bit more detail with this Cyber Security Systems Monitoring Report Incident Response Strategies Deployment. Use it as a tool for discussion and navigation on Success, Resolve, Intrusion. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
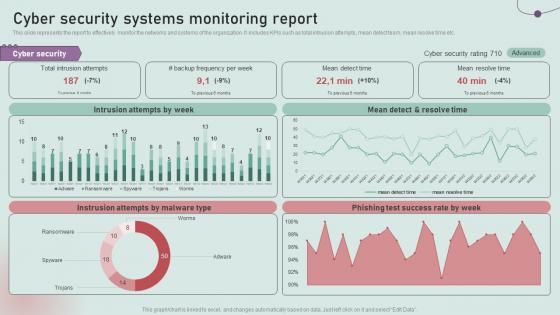 Cyber Security Systems Monitoring Report Development And Implementation Of Security Incident Management
Cyber Security Systems Monitoring Report Development And Implementation Of Security Incident ManagementThis slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Deliver an outstanding presentation on the topic using this Cyber Security Systems Monitoring Report Development And Implementation Of Security Incident Management. Dispense information and present a thorough explanation of Intrusion Attempts, Mean Detect, Resolve Time using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Cyber Security Systems Monitoring Report
Cyber Security Attacks Response Plan Cyber Security Systems Monitoring ReportThis slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Cyber Security Systems Monitoring Report. Use it as a tool for discussion and navigation on Cyber Security Systems, Monitoring Report, Mean Detect And Resolve Time. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
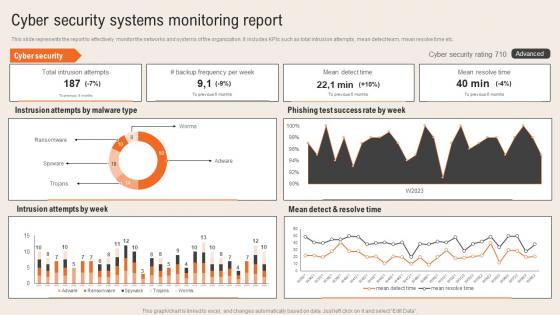 Cyber Security Systems Monitoring Report Deploying Computer Security Incident Management
Cyber Security Systems Monitoring Report Deploying Computer Security Incident ManagementThis slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc.Present the topic in a bit more detail with this Cyber Security Systems Monitoring Report Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Intrusion Attempts, Ransomware, Phishing Test Success. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security threat management system
Cyber security threat management systemThe following slide illustrates the cyber security threat management system which includes threat containment, logging and traceability management. Introducing our Cyber Security Threat Management System set of slides. The topics discussed in these slides are Threat Containment And Remediation, Identify Management, Application Visibility And Control. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 CPS Security And Privacy Life Cycle Cyber Physical Systems Ppt Powerpoint Presentation File Layouts
CPS Security And Privacy Life Cycle Cyber Physical Systems Ppt Powerpoint Presentation File LayoutsThis slide depicts the cyber physical systems security and privacy life cycle, including its phases from 1 to 6, along with the tasks performed in each phase. Present the topic in a bit more detail with this CPS Security And Privacy Life Cycle Cyber Physical Systems Ppt Powerpoint Presentation File Layouts. Use it as a tool for discussion and navigation on Applications Services, Communication Networks, Physical Infrastructures. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
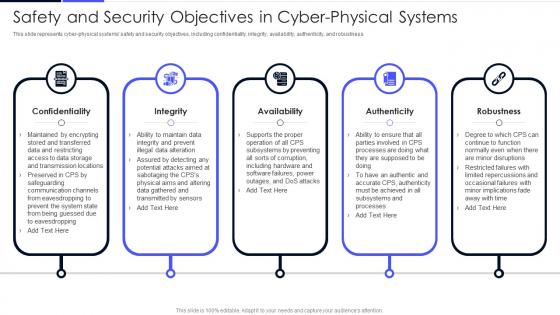 Safety And Security Objectives In Cyber Physical Systems Ppt Powerpoint Presentation File Graphics
Safety And Security Objectives In Cyber Physical Systems Ppt Powerpoint Presentation File GraphicsThis slide represents cyber physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. Introducing Safety And Security Objectives In Cyber Physical Systems Ppt Powerpoint Presentation File Graphics to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Availability, Authenticity, using this template. Grab it now to reap its full benefits.
-
 Security Strategic Planning Process For CPS Cyber Physical Systems In Powerpoint And Google Slides
Security Strategic Planning Process For CPS Cyber Physical Systems In Powerpoint And Google SlidesThis slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Deliver an outstanding presentation on the topic using this Security Strategic Planning Process For CPS Cyber Physical Systems In Powerpoint And Google Slides. Dispense information and present a thorough explanation of Gap Analysis, Prioritization, Environmental Trends using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps For CPS Security Strategy Plan Cyber Physical Systems In Powerpoint And Google Slides
Steps For CPS Security Strategy Plan Cyber Physical Systems In Powerpoint And Google SlidesThis slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Present the topic in a bit more detail with this Steps For CPS Security Strategy Plan Cyber Physical Systems In Powerpoint And Google Slides. Use it as a tool for discussion and navigation on Continuous Monitoring, Gap Analysis, Communicate Risk. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
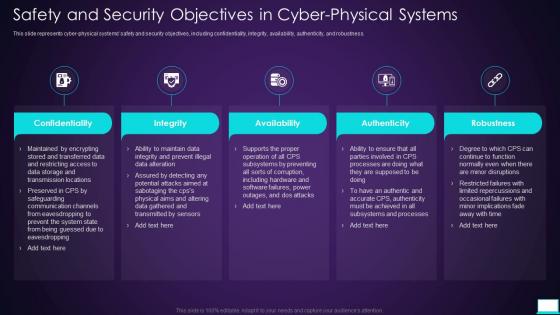 Safety And Security Objectives In Cyber Physical Systems Intelligent System
Safety And Security Objectives In Cyber Physical Systems Intelligent SystemThis slide represents cyber-physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. Present the topic in a bit more detail with this Safety And Security Objectives In Cyber Physical Systems Intelligent System. Use it as a tool for discussion and navigation on Confidentiality, Availability, Authenticity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology Systems
Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology SystemsThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology Systems. Use it as a tool for discussion and navigation on Threat Risk, Risk Mitigation Plan, Risk Owner. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Evaluating It System Security Using Swot Analysis Developing Cyber Security Awareness Training Program
Evaluating It System Security Using Swot Analysis Developing Cyber Security Awareness Training ProgramThe purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Introducing Evaluating It System Security Using Swot Analysis Developing Cyber Security Awareness Training Program to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strengths, Weaknesses, Opportunities, Threats, using this template. Grab it now to reap its full benefits.
-
 Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations
Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security OperationsThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Present the topic in a bit more detail with this Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Automation, Integrates, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritized Cyber Security Threats With Risk Mitigation Plan Risk Assessment Of It Systems
Prioritized Cyber Security Threats With Risk Mitigation Plan Risk Assessment Of It SystemsThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Prioritized Cyber Security Threats With Risk Mitigation Plan Risk Assessment Of It Systems. Use it as a tool for discussion and navigation on Mitigation Plan, Prioritized, Security Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
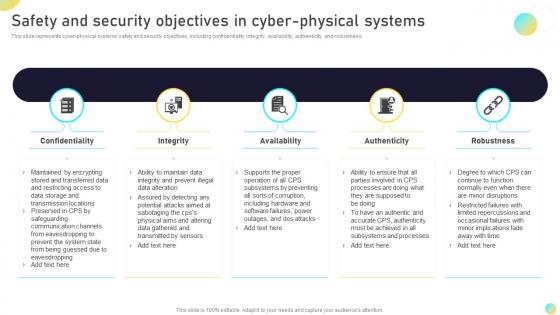 Safety And Security Objectives In Cyber Physical Systems Next Generation Computing Systems
Safety And Security Objectives In Cyber Physical Systems Next Generation Computing SystemsThis slide represents cyber-physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. Present the topic in a bit more detail with this Safety And Security Objectives In Cyber Physical Systems Next Generation Computing Systems. Use it as a tool for discussion and navigation on Confidentiality, Availability, Authenticity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Faced By Different Departments Information System Security And Risk Administration Plan
Cyber Attacks Faced By Different Departments Information System Security And Risk Administration PlanThis slide showcases information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Present the topic in a bit more detail with this Cyber Attacks Faced By Different Departments Information System Security And Risk Administration Plan. Use it as a tool for discussion and navigation on It Department, Marketing Department, Operations Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
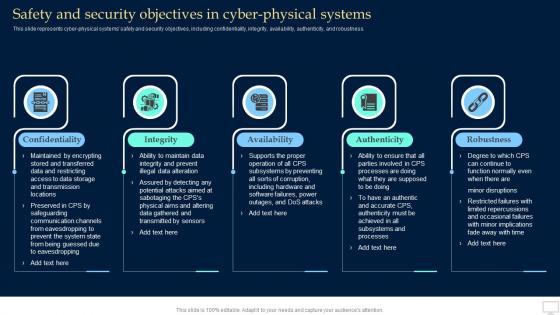 Safety And Security Objectives In Cyber Physical Systems Collective Intelligence Systems
Safety And Security Objectives In Cyber Physical Systems Collective Intelligence SystemsThis slide represents cyber-physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. Introducing Safety And Security Objectives In Cyber Physical Systems Collective Intelligence Systems to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Integrity, Availability, Authenticity, Robustness, using this template. Grab it now to reap its full benefits.
-
 Cyber E Security System Types For Data Protection
Cyber E Security System Types For Data ProtectionThis slide mentions types of cyber e security systems used in organizations for data protection. It includes critical infrastructure security, application security, network security, cloud security and IoT security. Presenting our set of slides with name Cyber E Security System Types For Data Protection. This exhibits information on five stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Critical Infrastructure Security, Application Security, Network Security.
-
 Cyber Security Policy Information System Change Management Policy
Cyber Security Policy Information System Change Management PolicyThis slide depicts the change management policy that includes SDLC, hardware, software, database, and application changes to system settings such as moves, adds, and deletes. Increase audience engagement and knowledge by dispensing information using Cyber Security Policy Information System Change Management Policy. This template helps you present information on seven stages. You can also present information on Information, Management, Documentation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Virus alert on cyber security computer system
Virus alert on cyber security computer systemPresenting this set of slides with name Virus Alert On Cyber Security Computer System. The topics discussed in these slides is Virus Alert On Cyber Security Computer System. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Cyber monitoring of system using biometric security identification icon
Cyber monitoring of system using biometric security identification iconPresenting this set of slides with name Cyber Monitoring Of System Using Biometric Security Identification Icon. This is a three stage process. The stages in this process are Cyber Monitoring Of System Using Biometric Security Identification Icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Icon of individual writing code to hack cyber security system
Icon of individual writing code to hack cyber security systemPresenting this set of slides with name Icon Of Individual Writing Code To Hack Cyber Security System. The topics discussed in these slides is Icon Of Individual Writing Code To Hack Cyber Security System. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Cyber security market overview system protection ppt powerpoint presentation templates
Cyber security market overview system protection ppt powerpoint presentation templatesThis slide shows a brief overview of the entire Cyber security Industry. Presenting this set of slides with name Cyber Security Market Overview System Protection Ppt Powerpoint Presentation Templates. The topics discussed in these slides are Cyber Security, Market Overview, System Protection. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Control system cyber security ppt powerpoint presentation portfolio example cpb
Control system cyber security ppt powerpoint presentation portfolio example cpbPresenting this set of slides with name Control System Cyber Security Ppt Powerpoint Presentation Portfolio Example Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Control System Cyber Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Mobile security system to prevent cyber crime
Mobile security system to prevent cyber crimePresenting this set of slides with name Mobile Security System To Prevent Cyber Crime. This is a one stage process. The stages in this process are Mobile Security System To Prevent Cyber Crime. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Security systems deployed to countermeasure cyber attacks launched by hackers
Security systems deployed to countermeasure cyber attacks launched by hackersIntroducing our premium set of slides with Web Portal Requires Username And Password For Login. Ellicudate the one stage and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Web Portal Requires Username And Password For Login. So download instantly and tailor it with your information.
-
 Security access protection system for cyber threat
Security access protection system for cyber threatIntroducing our premium set of slides with Security Access Protection System For Cyber Threat. Ellicudate the one stage and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Access Protection System For Cyber Threat. So download instantly and tailor it with your information.
-
 Cyber security econometric system process ppt powerpoint presentation deck cpb
Cyber security econometric system process ppt powerpoint presentation deck cpbPresenting this set of slides with name Cyber Security Econometric System Process Ppt Powerpoint Presentation Deck Cpb. This is an editable Powerpoint ten stages graphic that deals with topics like Cyber Security Econometric System Process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Firewall Implementation For Cyber Security Problems With Current Network Security System
Firewall Implementation For Cyber Security Problems With Current Network Security SystemThis slide highlights the loss experienced by the organization due to the existing security system. The purpose of this slide is to showcase the various cyber attack incidents and losses caused by them to the organization, such as malware infections, unauthorized access, phishing, etc. Present the topic in a bit more detail with this Firewall Implementation For Cyber Security Problems With Current Network Security System. Use it as a tool for discussion and navigation on Existing Security System, Cyber Attack Incidents, Malware Infections, Unauthorized Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Implementation For Cyber Security Threat Tracking Dashboard For Firewall System
Firewall Implementation For Cyber Security Threat Tracking Dashboard For Firewall SystemThis slide represents the dashboard for threat tracking in a firewall-protected network. The purpose of this slide is to showcase the various threats based on categories such as threats by owners, risk by threats, threat report, monthly threat status, current risk status, and threats based on user role. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Threat Tracking Dashboard For Firewall System. Dispense information and present a thorough explanation of Threat Tracking Dashboard, Firewall System, Current Risk Status, Firewall Protected Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Implementation For Cyber Security Impact Of Poor Network Security System On Business
Firewall Implementation For Cyber Security Impact Of Poor Network Security System On BusinessThis slide outlines the impact of the existing network security system on the company. The purpose of this slide is to showcase the incidents that happen because of poor network security and the total losses caused by those incidents, such as data breaches and loss, downtime, and so on. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Impact Of Poor Network Security System On Business. Dispense information and present a thorough explanation of Downtime And Productivity Loss, Intellectual Property Theft, Legal And Regulatory Consequences using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.



