Powerpoint Templates and Google slides for Cyber Operations
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Enabling Automation In Cyber Security Operations Powerpoint Presentation Slides
Enabling Automation In Cyber Security Operations Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Enabling Automation In Cyber Security Operations Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fourty two slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
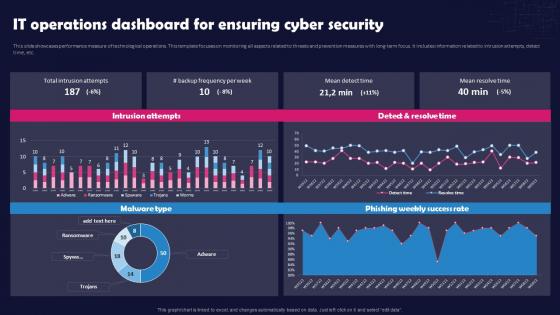 Unlocking The Impact Of Technology It Operations Dashboard For Ensuring Cyber Security
Unlocking The Impact Of Technology It Operations Dashboard For Ensuring Cyber SecurityThis slide showcases performance measure of technological operations. This template focuses on monitoring all aspects related to threats and prevention measures with long-term focus. It includes information related to intrusion attempts, detect time, etc. Present the topic in a bit more detail with this Unlocking The Impact Of Technology It Operations Dashboard For Ensuring Cyber Security. Use it as a tool for discussion and navigation on IT Operations Dashboard, Ensuring Cyber Security, Threats And Prevention, Technological Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Key KPMG Cyber Security KPMG Operational And Marketing Strategy SS V
Overview Of Key KPMG Cyber Security KPMG Operational And Marketing Strategy SS VThis slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights Increase audience engagement and knowledge by dispensing information using Overview Of Key KPMG Cyber Security KPMG Operational And Marketing Strategy SS V. This template helps you present information on five stages. You can also present information on Digital, Security, Automation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Case Study 2 Setting Up Cyber Security Infrastructure Strategic Improvement In Banking Operations
Case Study 2 Setting Up Cyber Security Infrastructure Strategic Improvement In Banking OperationsThe purpose of the mentioned slide is to showcase various measures initiated for cyber security protection in banking operations. This slide depicts various challenges faced by the bank along with desired solutions and impact Introducing Case Study 2 Setting Up Cyber Security Infrastructure Strategic Improvement In Banking Operations to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Infrastructure, Desired Solutions, Environment, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Analytics Solution Operating Model
Cyber Security Analytics Solution Operating ModelThe following slide highlights key points like threat intelligence, security information and event management, and analysis of user behavior to illustrate the cyber security analytics solution operating model. It helps organizations to proactively identify and respond to security threats, improving overall cybersecurity posture. Introducing our Cyber Security Analytics Solution Operating Model set of slides. The topics discussed in these slides are Intelligence, Data, Measures. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Protection for Financial Operations AI Image PowerPoint Presentation PPT ECS
Cyber Protection for Financial Operations AI Image PowerPoint Presentation PPT ECSIntroducing a Visual PPT on Cyber Protection for Financial Operations. Our design team have meticulously designed every PowerPoint Slide. Tailor the PPT content effortlessly. Additionally, the PPT Template is compatible with all monitor sizes and as well as Google Slides. Download the PPT, make the needed adjustments, and showcase with conviction.
-
 Cyber Strategies For KPMG For Client KPMG Operational And Marketing Strategy SS V
Cyber Strategies For KPMG For Client KPMG Operational And Marketing Strategy SS VThis slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company. It includes strategies such as people, process, data and technology and regulatory. Present the topic in a bit more detail with this Cyber Strategies For KPMG For Client KPMG Operational And Marketing Strategy SS V. Use it as a tool for discussion and navigation on Strategies, Protection, Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Other Cyber Strategies Of KPMG For Client KPMG Operational And Marketing Strategy SS V
Other Cyber Strategies Of KPMG For Client KPMG Operational And Marketing Strategy SS VThis slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc. Increase audience engagement and knowledge by dispensing information using Other Cyber Strategies Of KPMG For Client KPMG Operational And Marketing Strategy SS V. This template helps you present information on five stages. You can also present information on Developing, Implementing, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Operation Center Use Cases
Cyber Security Operation Center Use CasesThis slide showcases cyber security operation center use cases that helps to detect security events in real-time and mitigate actions to reduce risk. It includes elements such as technical level, business logic level and user behavior level. Presenting our set of slides with Cyber Security Operation Center Use Cases. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Technical Level Use Cases, User Behavior Level Use Cases, Business Logic Level Use Cases.
-
 Cyber Protection Analytics Solution Operating Model
Cyber Protection Analytics Solution Operating ModelThe following slide highlights key points like threat intelligence, security information and event management, and analysis of user behavior to illustrate the cyber security analytics solution operating model. It helps organizations to proactively identify and respond to security threats, improving overall cybersecurity posture Presenting our well structured Cyber Protection Analytics Solution Operating Model. The topics discussed in this slide are Risk Intelligence, Key Insights, Analysis User Behavior. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Utilization Of Triage By Cyber Security Operations Teams
Utilization Of Triage By Cyber Security Operations TeamsThis slide represents utilization of triage by cyber security operations teams which assists to assess, prioritize and respond to cybersecurity incidents. It includes key components such as retrieval results, trace, etc Introducing our Utilization Of Triage By Cyber Security Operations Teams set of slides. The topics discussed in these slides are Triage Cyber Security, Network Traffic, Security Incidents. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Saas Cyber Security Icon To Improve Operational Efficiency
Saas Cyber Security Icon To Improve Operational EfficiencyPresenting our set of slides with Saas Cyber Security Icon To Improve Operational Efficiency This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Saas Cyber Security, Icon To Improve Operational Efficiency
-
 Characteristics Of Operational Cyber Threat Intelligence
Characteristics Of Operational Cyber Threat IntelligenceThis slide outlines the features of second type of cyber threat intelligence, which is, operation cyber threat intelligence. Increase audience engagement and knowledge by dispensing information using Characteristics Of Operational Cyber Threat Intelligence. This template helps you present information on five stages. You can also present information on Operational Intel Analysis, Generated By Humans, Cyber Pros Analyze Adversaries, Context Reveals Adversary Tactics using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Threat Intelligence Operationalize Framework
Cyber Threat Intelligence Operationalize FrameworkThis slide represents cyber threat intelligence operationalize framework with factors such as alerts for monitoring, threat intelligence, etc. Present the topic in a bit more detail with this Cyber Threat Intelligence Operationalize Framework. Use it as a tool for discussion and navigation on Situational Awareness, Threat Intelligence, Alerts For Monitoring, Strategic Reports. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Cyber Attacks On Organizational Operations IT Security Awareness Training Cybersecurity SS
Impact Of Cyber Attacks On Organizational Operations IT Security Awareness Training Cybersecurity SSThis slide represents impact of attacks that are attempted to steal sensitive information in the form of user names, credit card numbers etc. on organizational operations. Increase audience engagement and knowledge by dispensing information using Impact Of Cyber Attacks On Organizational Operations IT Security Awareness Training Cybersecurity SS. This template helps you present information on four stages. You can also present information on Reputational Damage, Stolen Intellectual Property, Operational Disruption, Increased Costs using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Offensive Cyber Operations And Deterrence Strategic Guide To Implement Strategy SS
Offensive Cyber Operations And Deterrence Strategic Guide To Implement Strategy SSThis slide showcases the Offensive Cyber Operations and Deterrence. It includes elements such as definition, objective and examples.Present the topic in a bit more detail with this Offensive Cyber Operations And Deterrence Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Define, Objective, Examples, Deterrence Cyber Operations, Offensive Cyber Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attack Icon To Affect Supply Chain Operations
Cyber Attack Icon To Affect Supply Chain OperationsPresenting our set of slides with name Cyber Attack Icon To Affect Supply Chain Operations. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Attack Icon, Affect Supply Chain Operations.
-
 Operational Outlook Of Security Awareness Training Software Developing Cyber Security Awareness Training
Operational Outlook Of Security Awareness Training Software Developing Cyber Security Awareness TrainingThe purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Deliver an outstanding presentation on the topic using this Operational Outlook Of Security Awareness Training Software Developing Cyber Security Awareness Training. Dispense information and present a thorough explanation of Operational Outlook, Security Awareness, Training Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enabling Automation In Cyber Security Operations Time To Fix Security Threat With Manual Testing
Enabling Automation In Cyber Security Operations Time To Fix Security Threat With Manual TestingThis slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Present the topic in a bit more detail with this Enabling Automation In Cyber Security Operations Time To Fix Security Threat With Manual Testing. Use it as a tool for discussion and navigation on Manual, Testing, Security Threat. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Dashboard Highlighting Network Enabling Automation In Cyber Security Operations
Security Automation Dashboard Highlighting Network Enabling Automation In Cyber Security OperationsThis slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Present the topic in a bit more detail with this Security Automation Dashboard Highlighting Network Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Automation, Dashboard, Highlighting. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise Cyber Risk Management Operational Risk Management Strategic
Enterprise Cyber Risk Management Operational Risk Management StrategicThis slide represents dashboard representing details related to management of strategic risks in the organization. It includes details related to risk rating breakdown, risk heat map, top 5 vulnerabilities etc. Present the topic in a bit more detail with this Enterprise Cyber Risk Management Operational Risk Management Strategic. Use it as a tool for discussion and navigation on Risk Rating Breakdown, Risk Heat Map, Action Plan Breakdown. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ukraine and russia cyber warfare it russian cyber operations against ukraine timeline
Ukraine and russia cyber warfare it russian cyber operations against ukraine timelineThis slide represents the timeline of Russian cyber operations against Ukraine by listing all the cyber attacks held from 14 February to 27 February 2022. Introducing Ukraine And Russia Cyber Warfare It Russian Cyber Operations Against Ukraine Timeline to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Deployment, Sandworm, Ransomware, using this template. Grab it now to reap its full benefits.
-
 Cyber Attacks On Ukraine Russian Cyber Operations Against Ukraine Timeline
Cyber Attacks On Ukraine Russian Cyber Operations Against Ukraine TimelineThis slide represents the timeline of Russian cyber operations against Ukraine by listing all the cyber attacks held from 14 February to 27 February 2022. Increase audience engagement and knowledge by dispensing information using Cyber Attacks On Ukraine Russian Cyber Operations Against Ukraine Timeline. This template helps you present information on ten stages. You can also present information on Russian Cyber Operations Against Ukraine Timeline using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Wiper Malware Attack Russian Cyber Operations Against Ukraine Timeline
Wiper Malware Attack Russian Cyber Operations Against Ukraine TimelineThis slide represents the timeline of Russian cyber operations against Ukraine by listing all the cyber attacks held from 14 February to 27 February 2022. Increase audience engagement and knowledge by dispensing information using Wiper Malware Attack Russian Cyber Operations Against Ukraine Timeline. This template helps you present information on ten stages. You can also present information on Russian Cyber Operations Against Ukraine Timeline using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Four Stages Of Protecting Operational Technology From Cyber Attacks
Four Stages Of Protecting Operational Technology From Cyber AttacksMentioned slide showcase four interlinked stages of operational technology OT security aware, enact, vigilant and resilient. Business organization can overcome top cyber attacks and protect sensitive data by following these stages. Increase audience engagement and knowledge by dispensing information using four Stages Of Protecting Operational Technology From Cyber Attacks. This template helps you present information on four stages. You can also present information on Aware, Enact, Vigilant, Resilient using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Launch Of Cyber IT OT Strategy Digital Transformation Of Operational Industries
Launch Of Cyber IT OT Strategy Digital Transformation Of Operational IndustriesThis slide covers IT or OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT teams etc.Increase audience engagement and knowledge by dispensing information using Launch Of Cyber IT OT Strategy Digital Transformation Of Operational Industries. This template helps you present information on one stage. You can also present information on Business Planning, Operations Management, Process Control using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Project Estimation Plan To Safeguard Business Operation
Cyber Security Project Estimation Plan To Safeguard Business OperationThis slide signifies the cyber security project evaluation plan for safeguarding organisation operations. It covers information regarding to the stages like initiation, planning, execution, implement and monitor. Introducing our premium set of slides with Cyber Security Project Estimation Plan To Safeguard Business Operation. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Initiation, Planning, Execution. So download instantly and tailor it with your information.
-
 Cyber Security Elements IT Operational Security Element Of Cyber Security Ppt Introduction
Cyber Security Elements IT Operational Security Element Of Cyber Security Ppt IntroductionThis slide defines the operational security element of cyber security. It also shows the best practices for operational security, such as changing management processes, deploying automation, planning for disasters, restricting device access, and implementing dual control. Increase audience engagement and knowledge by dispensing information using Cyber Security Elements IT Operational Security Element Of Cyber Security Ppt Introduction. This template helps you present information on five stages. You can also present information on Deploy Automation, Restrict Device Access, Change Management Processes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda Enabling Automation In Cyber Security Operations Ppt Slides Background Images
Agenda Enabling Automation In Cyber Security Operations Ppt Slides Background ImagesIntroducing Agenda Enabling Automation In Cyber Security Operations Ppt Slides Background Images to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Environment, Business, Process, using this template. Grab it now to reap its full benefits.
-
 Criteria To Automate Security Analysis And Response Enabling Automation In Cyber Security Operations
Criteria To Automate Security Analysis And Response Enabling Automation In Cyber Security OperationsThis slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Present the topic in a bit more detail with this Criteria To Automate Security Analysis And Response Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Intervention, Malware Analysis, Automate. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Security Automation Tools With Pros And Cons Enabling Automation In Cyber Security Operations
Different Security Automation Tools With Pros And Cons Enabling Automation In Cyber Security OperationsThis slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Present the topic in a bit more detail with this Different Security Automation Tools With Pros And Cons Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Information, Management, Automation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enabling Automation In Cyber Security Operations Determine Ideal Tasks For Security Automation
Enabling Automation In Cyber Security Operations Determine Ideal Tasks For Security AutomationThis slide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Deliver an outstanding presentation on the topic using this Enabling Automation In Cyber Security Operations Determine Ideal Tasks For Security Automation. Dispense information and present a thorough explanation of Automation, Individual, Takeaways Section using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enabling Automation In Cyber Security Operations Domain Security Controls That Can Be Automated
Enabling Automation In Cyber Security Operations Domain Security Controls That Can Be AutomatedThis slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Present the topic in a bit more detail with this Enabling Automation In Cyber Security Operations Domain Security Controls That Can Be Automated. Use it as a tool for discussion and navigation on Communication, Management, Human Resources. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enabling Automation In Cyber Security Operations Table Of Contents Ppt Slides Infographic Template
Enabling Automation In Cyber Security Operations Table Of Contents Ppt Slides Infographic TemplateDeliver an outstanding presentation on the topic using this Enabling Automation In Cyber Security Operations Table Of Contents Ppt Slides Infographic Template. Dispense information and present a thorough explanation of Protection Platform, Security Automation, Processes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Network It Security Automation Enabling Automation In Cyber Security Operations
Enterprise Network It Security Automation Enabling Automation In Cyber Security OperationsThis slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Deliver an outstanding presentation on the topic using this Enterprise Network It Security Automation Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Orchestrating Network Security, Troubleshooting, Integrating Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Extended Detection And Response For Endpoint Security Enabling Automation In Cyber Security Operations
Extended Detection And Response For Endpoint Security Enabling Automation In Cyber Security OperationsThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deceptio Increase audience engagement and knowledge by dispensing information using Extended Detection And Response For Endpoint Security Enabling Automation In Cyber Security Operations. This template helps you present information on four stages. You can also present information on Endpoint Protection, Network Protection, User Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Enabling Automation In Cyber Security Operations Ppt Slides Background Designs
Icons Slide For Enabling Automation In Cyber Security Operations Ppt Slides Background DesignsDeliver an outstanding presentation on the topic using this Icons Slide For Enabling Automation In Cyber Security Operations Ppt Slides Background Designs. Dispense information and present a thorough explanation of Icons using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security Operations
Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security OperationsThis slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Increase audience engagement and knowledge by dispensing information using Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security Operations. This template helps you present information on four stages. You can also present information on Ineffective, Information, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Managed Detection And Response Layer For Expert Monitoring Enabling Automation In Cyber Security Operations
Managed Detection And Response Layer For Expert Monitoring Enabling Automation In Cyber Security OperationsThis slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. Introducing Managed Detection And Response Layer For Expert Monitoring Enabling Automation In Cyber Security Operations to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Alert Monitoring, Attack Investigation, Threat Hunting, using this template. Grab it now to reap its full benefits.
-
 Measure Security Automation Metrics For Operations Efficiency Enabling Automation In Cyber Security Operations
Measure Security Automation Metrics For Operations Efficiency Enabling Automation In Cyber Security OperationsThis slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Present the topic in a bit more detail with this Measure Security Automation Metrics For Operations Efficiency Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Automation, Operations, Efficiency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Right Time To Add Automation In Security Enabling Automation In Cyber Security Operations
Right Time To Add Automation In Security Enabling Automation In Cyber Security OperationsThis slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. Present the topic in a bit more detail with this Right Time To Add Automation In Security Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Resolution, Automation, Human Insights. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations
Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security OperationsThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Present the topic in a bit more detail with this Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Automation, Integrates, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Stages With Maturity Level Enabling Automation In Cyber Security Operations
Security Automation Stages With Maturity Level Enabling Automation In Cyber Security OperationsThis slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Deliver an outstanding presentation on the topic using this Security Automation Stages With Maturity Level Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Security Automation, Services, Programmatic Workflow using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
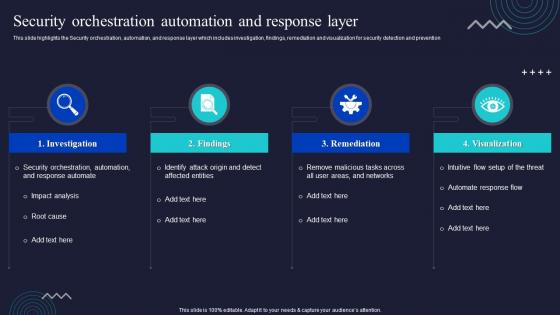 Security Orchestration Automation And Response Layer Enabling Automation In Cyber Security Operations
Security Orchestration Automation And Response Layer Enabling Automation In Cyber Security OperationsThis slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention Deliver an outstanding presentation on the topic using this Security Orchestration Automation And Response Layer Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Investigation, Remediation, Visualization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Processes That Cant Be Automated Enabling Automation In Cyber Security Operations
Security Processes That Cant Be Automated Enabling Automation In Cyber Security OperationsThe following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Increase audience engagement and knowledge by dispensing information using Security Processes That Cant Be Automated Enabling Automation In Cyber Security Operations. This template helps you present information on three stages. You can also present information on Threat Modeling, Penetration Testing, Bug Bounty using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents Enabling Automation In Cyber Security Operations Ppt Slides Background Image
Table Of Contents Enabling Automation In Cyber Security Operations Ppt Slides Background ImageIntroducing Table Of Contents Enabling Automation In Cyber Security Operations Ppt Slides Background Image to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Security Automation, Architecture And Importance, Security Automation Dashboards, using this template. Grab it now to reap its full benefits.
-
 Unified Platform Integration For Security Automation Enabling Automation In Cyber Security Operations
Unified Platform Integration For Security Automation Enabling Automation In Cyber Security OperationsThis slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. Present the topic in a bit more detail with this Unified Platform Integration For Security Automation Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Automation, Access Management, Platform Integration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Why To Automate The It Security Process Enabling Automation In Cyber Security Operations
Why To Automate The It Security Process Enabling Automation In Cyber Security OperationsThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Increase audience engagement and knowledge by dispensing information using Why To Automate The It Security Process Enabling Automation In Cyber Security Operations. This template helps you present information on five stages. You can also present information on Better Threat Detection, Faster Containment, Improve Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Automation Architecture With Key Elements Enabling Automation In Cyber Security Operations
Security Automation Architecture With Key Elements Enabling Automation In Cyber Security OperationsThis slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Deliver an outstanding presentation on the topic using this Security Automation Architecture With Key Elements Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Automation, Architecture, Sources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Tactical Operational Cyber Threat Intelligence
Strategic Tactical Operational Cyber Threat IntelligenceThis slide exhibits strategic tactical and operational levels of cyber threat intelligence to ensure data and software protection from threats. It includes identify reason, assist extent of breach, alert and identify prevention system and ensure safety in advance. Presenting our set of slides with Strategic Tactical Operational Cyber Threat Intelligence. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Strategic Cyber, Threat Intelligence, Tactical Cyber.
-
 Enterprise Cyber Security Operation Icon
Enterprise Cyber Security Operation IconIntroducing our premium set of slides with Enterprise Cyber Security Operation Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Enterprise Cyber Security, Operation Icon. So download instantly and tailor it with your information.
-
 Enterprise Cyber security Operation Monitoring Framework
Enterprise Cyber security Operation Monitoring FrameworkThis slide covers enterprise cyber security operation monitoring framework. It involves five functions such as identify, protect, detect, respond and recover. Presenting our well structured Enterprise Cybersecurity Operation Monitoring Framework. The topics discussed in this slide are Cybersecurity Outcomes, Service Areas, Identify. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Russian Cyber Operations Against Ukraine Timeline String Of Cyber Attacks Against Ukraine 2022
Russian Cyber Operations Against Ukraine Timeline String Of Cyber Attacks Against Ukraine 2022This slide represents the timeline of russian cyber operations against ukraine by listing all the cyber attacks held from 14 february to 27 february 2022. Increase audience engagement and knowledge by dispensing information using Russian Cyber Operations Against Ukraine Timeline String Of Cyber Attacks Against Ukraine 2022. This template helps you present information on ten stages. You can also present information on Website Defacements, Deployment Of Whispergate, Government using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Operational Technology Cyber Security In Powerpoint And Google Slides Cpb
Operational Technology Cyber Security In Powerpoint And Google Slides CpbPresenting our Operational Technology Cyber Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Operational Technology Cyber Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber Security Risk Governance Operating Model
Cyber Security Risk Governance Operating ModelThe slide showcases an operating model of cyber security risk governance to address business threats. It includes key elements like governance, risk management and compliance. Introducing our Cyber Security Risk Governance Operating Model set of slides. The topics discussed in these slides are Governance, Risk, Compliance. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Five years cyber security roadmap to assess and manage operational risk
Five years cyber security roadmap to assess and manage operational riskPresenting Five Years Cyber Security Roadmap To Assess And Manage Operational Risk PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
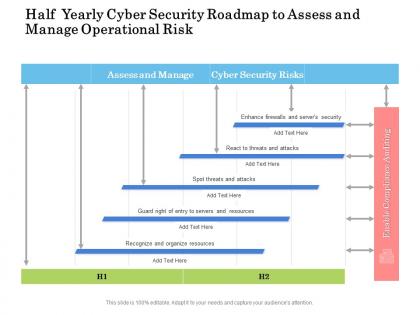 Half yearly cyber security roadmap to assess and manage operational risk
Half yearly cyber security roadmap to assess and manage operational riskPresenting Half Yearly Cyber Security Roadmap To Assess And Manage Operational Risk PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
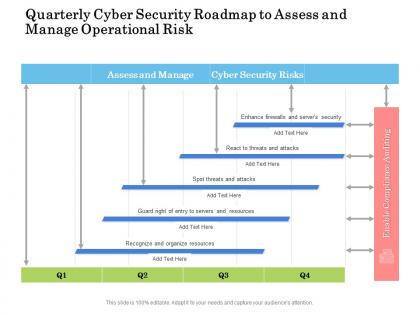 Quarterly cyber security roadmap to assess and manage operational risk
Quarterly cyber security roadmap to assess and manage operational riskPresenting Quarterly Cyber Security Roadmap To Assess And Manage Operational Risk PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
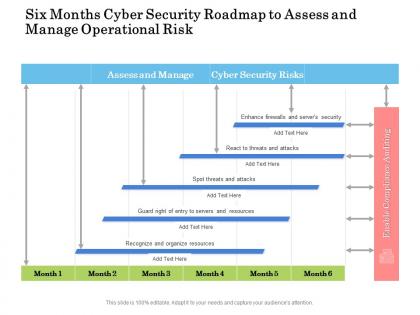 Six months cyber security roadmap to assess and manage operational risk
Six months cyber security roadmap to assess and manage operational riskPresenting Six Months Cyber Security Roadmap To Assess And Manage Operational Risk PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
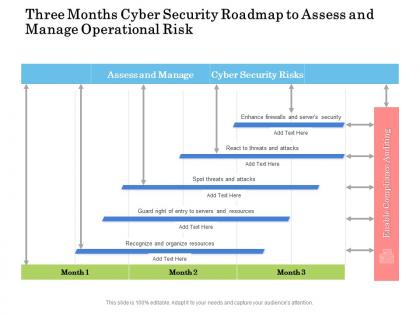 Three months cyber security roadmap to assess and manage operational risk
Three months cyber security roadmap to assess and manage operational riskPresenting Three Months Cyber Security Roadmap To Assess And Manage Operational Risk PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.




