Powerpoint Templates and Google slides for Cyber Attacks Risk Assessment
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Attack Incident Tracking Dashboard Cyber Risk Assessment
Cyber Attack Incident Tracking Dashboard Cyber Risk AssessmentThe following slide depicts the number of cyber-attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Present the topic in a bit more detail with this Cyber Attack Incident Tracking Dashboard Cyber Risk Assessment Use it as a tool for discussion and navigation on Cyber Attack Incident, Tracking Dashboard This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Causes Of Cyber Crimes And Attacks Cyber Risk Assessment
Major Causes Of Cyber Crimes And Attacks Cyber Risk AssessmentThe following slide highlights the key reasons of cyber-attack to analyze and formulate actions. It includes key elements such as physical theft, human error, insider misuse, old security vulnerabilities etc. Present the topic in a bit more detail with this Major Causes Of Cyber Crimes And Attacks Cyber Risk Assessment Use it as a tool for discussion and navigation on Major Reasons, Major Causes, Cyber Crimes And Attacks This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Analyze Impact Of Cyber Attack On Valuable Assets Cyber Risk Assessment
Analyze Impact Of Cyber Attack On Valuable Assets Cyber Risk AssessmentThe following slide depicts the consequences of data breach threats to prevent information leakage. It mainly includes elements such as impact on revenue, protection cost, liability if lost, weightage criteria, asset importance etc. Deliver an outstanding presentation on the topic using this Analyze Impact Of Cyber Attack On Valuable Assets Cyber Risk Assessment Dispense information and present a thorough explanation of Customer Database, Product Database, Sales Lead Database using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Prevent Cyber Attacks Cyber Risk Assessment
Best Practices To Prevent Cyber Attacks Cyber Risk AssessmentThe following slide illustrates some activities to minimize the probability of cybercrimes within the organization. It includes elements such as utilizing anti-virus, preventing to open suspicious emails, keeping systems up-to date etc. Introducing Best Practices To Prevent Cyber Attacks Cyber Risk Assessment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Prevent Opening, Suspicious Emails, Leverage Firewalls using this template. Grab it now to reap its full benefits.
-
 Classify Assets Vulnerable To Cyber Attack Cyber Risk Assessment
Classify Assets Vulnerable To Cyber Attack Cyber Risk AssessmentThe following slide depicts some major assets that are more prone to cyber-attack. It mainly includes elements such as sales record, sales lead record, company internal database, customer and product information etc. Introducing Classify Assets Vulnerable To Cyber Attack Cyber Risk Assessment to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Customer Database, Product Database, Sales Lead Database using this template. Grab it now to reap its full benefits.
-
 Identifying Impact Of Cyber Attack On Business Cyber Risk Assessment
Identifying Impact Of Cyber Attack On Business Cyber Risk AssessmentThe following slide depicts the negative impact of cyber-crimes on business to build control actions and strategies. It includes key elements such as rising costs, reputational damage, operational disruption, loss of revenue etc. Increase audience engagement and knowledge by dispensing information using Identifying Impact Of Cyber Attack On Business Cyber Risk Assessment This template helps you present information on four stages. You can also present information on Rising Cost, Reputational Damage, Operational Disruption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Reduce Attack Surface With Privilege Access Management Cyber Risk Assessment
Reduce Attack Surface With Privilege Access Management Cyber Risk AssessmentThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Deliver an outstanding presentation on the topic using this Reduce Attack Surface With Privilege Access Management Cyber Risk Assessment Dispense information and present a thorough explanation of Users Access Request, Record Sessions, Session Proxy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Types Of Cyber Attacks Encountered By Employees Cyber Risk Assessment
Types Of Cyber Attacks Encountered By Employees Cyber Risk AssessmentThe following slide showcases the various types of cyber-attacks faced by staff to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service etc. Introducing Types Of Cyber Attacks Encountered By Employees Cyber Risk Assessment to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Malware, Phishing, Ransomware, Denial Of Service Attack using this template. Grab it now to reap its full benefits.
-
 Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information Security
Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information SecurityThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type if cyber attacks and formulate strategies to tackle them Present the topic in a bit more detail with this Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Experienced, Organization, Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management Dashboard
Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management DashboardThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management Dashboard. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Assessment Program Cyber Attacks Faced By Organization
Cybersecurity Risk Assessment Program Cyber Attacks Faced By OrganizationThis slide provides information regarding the number of cyber attacks faced by the organization and its impact on IT operations and system downtime. It also provides details of percentage rise in such attacks since last month. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Cyber Attacks Faced By Organization. Use it as a tool for discussion and navigation on Cyber Attacks, IT Operations, System Downtime. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels
Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk LevelsThe slide represents the dashboard for tracking cyber attack risk levels. It includes information regarding the multiple threat agents, attack methods, preventive controls along with details of risk score and infected systems. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels. Dispense information and present a thorough explanation of Infrastructure Controls, Preventive Controls, Detective Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Assessment Program Dashboard To Monitor Cyber Attack Incidents
Cybersecurity Risk Assessment Program Dashboard To Monitor Cyber Attack IncidentsThis slide indicates the dashboard to monitor cyber attacks on IT assets of the firm. It includes information regarding the total cyber attack incidents both month and day wise along with the details of threat class, overall risk factor and top vulnerabilities. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Dashboard To Monitor Cyber Attack Incidents. Use it as a tool for discussion and navigation on Dashboard To Monitor, Cyber Attack Incidents, Vulnerabilities, Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Assessment Program Summary Of Key Cyber Attacks Occurred
Cybersecurity Risk Assessment Program Summary Of Key Cyber Attacks OccurredThis slide shows the summary of key of cybers attacks occurred in organization such as phishing, malware attack, denial of service, SQL injections, identity thefts. It also contains details of the cyber attacker origin such as inadvertent actors, malicious insiders. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Summary Of Key Cyber Attacks Occurred. Use it as a tool for discussion and navigation on Cyber Attacks Occurred, Financial Loss, Cyber Attack Origins. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
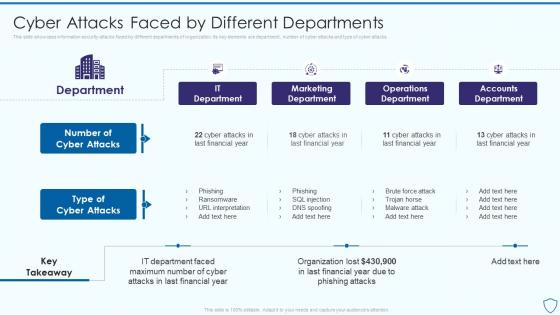 Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By Different
Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By DifferentThis slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks Deliver an outstanding presentation on the topic using this Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By Different. Dispense information and present a thorough explanation of Marketing Department, Operations Department, Accounts Department using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategy To Minimize Cyber Attacks Multistep Approach To Conduct Cybersecurity Risk Assessment
Strategy To Minimize Cyber Attacks Multistep Approach To Conduct Cybersecurity Risk AssessmentThis slide indicates the multistep approach to conduct cybersecurity risk assessment in business organization. The major steps of process are risk identification, quantification, evaluation, mitigation and monitoring. Introducing Strategy To Minimize Cyber Attacks Multistep Approach To Conduct Cybersecurity Risk Assessment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Risk Identification, Risk Mapping, Risk Evaluation, Risk Mitigation And Monitoring, using this template. Grab it now to reap its full benefits.
-
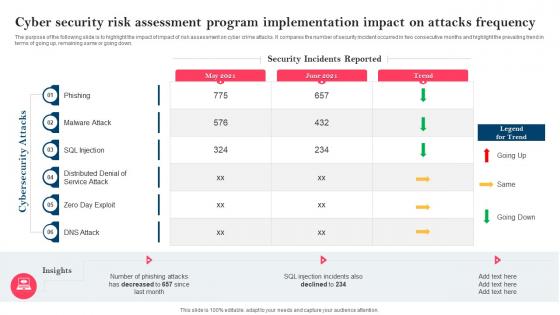 Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program Implementation
Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program ImplementationThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Present the topic in a bit more detail with this Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program Implementation. Use it as a tool for discussion and navigation on Cyber Security, Risk Assessment, Program Implementation, Impact On Attacks Frequency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Monitor And Assess Vendor Risk Management Cyber Attack Risks Mitigation
Monitor And Assess Vendor Risk Management Cyber Attack Risks MitigationThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Introducing Monitor And Assess Vendor Risk Management Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Web Application Security, Infrastructure Security, Vendor Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response Plan
Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response PlanThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response Plan. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Assessment Program Key Approaches To Minimize Cyber Attacks Risks
Cybersecurity Risk Assessment Program Key Approaches To Minimize Cyber Attacks RisksThis slide indicates the key approaches to minimize the risk associated with cyber attacks. The approaches discussed are update and upgrade outdated software, control accounts access, introduce signed software execution policies, regularly track network intrusions and use multifactor authentication. Increase audience engagement and knowledge by dispensing information using Cybersecurity Risk Assessment Program Key Approaches To Minimize Cyber Attacks Risks. This template helps you present information on five stages. You can also present information on Control Accounts Access, Multifactor Authentication, Track Network Intrusions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Risk Assessment Program Major Cyber Attacks Faced By Organization
Cybersecurity Risk Assessment Program Major Cyber Attacks Faced By OrganizationThis purpose of this slide is to showcase the major cyber attacks faced by business organization. The key attacks listed are phishing, malware attack, denial of service attacks, SQL injections, and ransomware. It also provides details regarding the major IT assets impacted and primary objective of each of the attacks. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Major Cyber Attacks Faced By Organization. Use it as a tool for discussion and navigation on Phishing, Malware Attack, Denial Of Service Attack, Ransomware. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Assessment Program Mapping Of Multiple Cyber Attacks Using Risk Heat Map
Cybersecurity Risk Assessment Program Mapping Of Multiple Cyber Attacks Using Risk Heat MapThis slide shows the mapping of cyber attacks based on the likelihood of risk occurrence and its impact. It also contains details of attacks segmentation and the control actions that must be taken such as track, monitor and mitigate against such cyber attacks. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Assessment Program Mapping Of Multiple Cyber Attacks Using Risk Heat Map. Dispense information and present a thorough explanation of Cyber Attacks, Risk Heat Map, Cyber Attacks Segmentation, Mitigate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Assessment Program Risk Register To Measure Cyber Attacks Vulnerabilities
Cybersecurity Risk Assessment Program Risk Register To Measure Cyber Attacks VulnerabilitiesThis slide indicates the risk register to measure the cyber attack risk vulnerabilities faced by an organization. It includes information regarding the multiple risks in terms of vulnerability exploited, impact level, likelihood of occurrence and control recommended. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Risk Register To Measure Cyber Attacks Vulnerabilities. Use it as a tool for discussion and navigation on Cyber Attacks, Vulnerabilities, Cloud Network Compromised, Outdated Antivirus. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Assessment Program Strategic Plan To Mitigate Cyber Attacks
Cybersecurity Risk Assessment Program Strategic Plan To Mitigate Cyber AttacksThe slide indicates the risk mitigation plan for the multiple cyber attacks. It also includes details of cost involved and implementation time required for each mitigation approach. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Assessment Program Strategic Plan To Mitigate Cyber Attacks. Dispense information and present a thorough explanation of Strategic Plan, Mitigate Cyber Attacks, Malware Attack, Recommended Mitigation Strategy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.



