Powerpoint Templates and Google slides for Cyber Attacks Identification
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
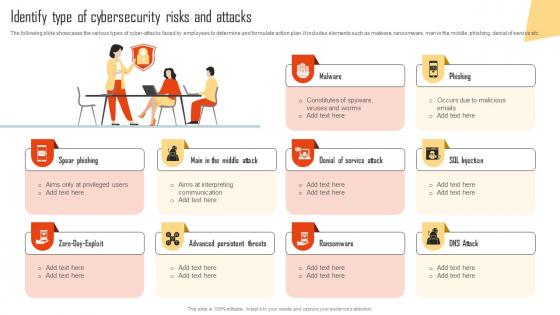 Identify Type Of Cybersecurity Risks And Attacks Improving Cyber Security Risks Management
Identify Type Of Cybersecurity Risks And Attacks Improving Cyber Security Risks ManagementThe following slide showcases the various types of cyber-attacks faced by employees to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service etc. Introducing Identify Type Of Cybersecurity Risks And Attacks Improving Cyber Security Risks Management to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing, Advanced Persistent Threats, Ransomware, Phishing, using this template. Grab it now to reap its full benefits.
-
 Identifying Impact Of Cyber Attack On Business Implementing Cyber Risk Management Process
Identifying Impact Of Cyber Attack On Business Implementing Cyber Risk Management ProcessThe following slide depicts the negative impact of cyber-crimes on business to build control actions and strategies. It includes key elements such as rising costs, reputational damage, operational disruption, loss of revenue etc. Increase audience engagement and knowledge by dispensing information using Identifying Impact Of Cyber Attack On Business Implementing Cyber Risk Management Process. This template helps you present information on four stages. You can also present information on Reputational Damage, Rising Cost, Operational Disruption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Identifying Impact Of Cyber Attack On Business Cyber Risk Assessment
Identifying Impact Of Cyber Attack On Business Cyber Risk AssessmentThe following slide depicts the negative impact of cyber-crimes on business to build control actions and strategies. It includes key elements such as rising costs, reputational damage, operational disruption, loss of revenue etc. Increase audience engagement and knowledge by dispensing information using Identifying Impact Of Cyber Attack On Business Cyber Risk Assessment This template helps you present information on four stages. You can also present information on Rising Cost, Reputational Damage, Operational Disruption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Identifying Impact Of Cyber Attack On Business Creating Cyber Security Awareness
Identifying Impact Of Cyber Attack On Business Creating Cyber Security AwarenessThe following slide depicts the negative impact of cyber-crimes on business to build control actions and strategies. It includes key elements such as rising costs, reputational damage, operational disruption, loss of revenue etc. Increase audience engagement and knowledge by dispensing information using Identifying Impact Of Cyber Attack On Business Creating Cyber Security Awareness This template helps you present information on Four stages. You can also present information on Small Size, Ransomware Attack, Cyber Attacks, Security Precautionary Measures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security Threats
Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the negative impact of cyber crimes on business to build control actions and strategies. It includes key elements such as rising costs, reputational damage, operational disruption, loss of revenue etc. Introducing Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Rising Cost, Reputational Damage, Operational Disruption using this template. Grab it now to reap its full benefits.
-
 Strategies To Identify Smishing Cyber Scams Phishing Attacks And Strategies
Strategies To Identify Smishing Cyber Scams Phishing Attacks And StrategiesThis slide talks about the various methods of identifying smishing cyber attacks. The purpose of this slide is to help users identify smishing scams. These include suspicious texts from unknown numbers, unrequested links and files, money transfer requests, etc.Present the topic in a bit more detail with this Strategies To Identify Smishing Cyber Scams Phishing Attacks And Strategies. Use it as a tool for discussion and navigation on Requests Asking, Transfer Requests, Notifications Stating. This template is free to edit as deemed fit for your organization. Therefore download it now.



