Powerpoint Templates and Google slides for Cyber Attack Management
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Attack Incident Tracking Dashboard Implementing Cyber Risk Management Process
Cyber Attack Incident Tracking Dashboard Implementing Cyber Risk Management ProcessThe following slide depicts the number of cyber-attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Present the topic in a bit more detail with this Cyber Attack Incident Tracking Dashboard Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Attack Trends, Attacks Allowed By Policy. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Causes Of Cyber Crimes And Attacks Implementing Cyber Risk Management Process
Major Causes Of Cyber Crimes And Attacks Implementing Cyber Risk Management ProcessThe following slide highlights the key reasons of cyber-attack to analyze and formulate actions. It includes key elements such asphysical theft, human error, insider misuse, old security vulnerabilities etc. Present the topic in a bit more detail with this Major Causes Of Cyber Crimes And Attacks Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Major Reasons. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
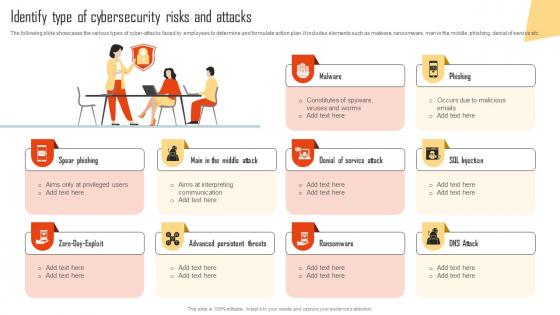 Identify Type Of Cybersecurity Risks And Attacks Improving Cyber Security Risks Management
Identify Type Of Cybersecurity Risks And Attacks Improving Cyber Security Risks ManagementThe following slide showcases the various types of cyber-attacks faced by employees to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service etc. Introducing Identify Type Of Cybersecurity Risks And Attacks Improving Cyber Security Risks Management to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing, Advanced Persistent Threats, Ransomware, Phishing, using this template. Grab it now to reap its full benefits.
-
 Implement Best Practices To Prevent Cyber Attacks Improving Cyber Security Risks Management
Implement Best Practices To Prevent Cyber Attacks Improving Cyber Security Risks ManagementThe following slide illustrates some best practices to execute preventive actions for cyber attacks. It includes elements such as train employees, updating systems and software, developing incident response plan, backing up data, maintaining compliance etc. Increase audience engagement and knowledge by dispensing information using Implement Best Practices To Prevent Cyber Attacks Improving Cyber Security Risks Management. This template helps you present information on six stages. You can also present information on Train Employees, Maintain Compliance, Develop Incident Response Plan using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Analyse Impact Of Cyber Attack On Valuable Assets Implementing Cyber Risk Management Process
Analyse Impact Of Cyber Attack On Valuable Assets Implementing Cyber Risk Management ProcessThe following slide depicts the consequences of data breach threats to prevent information leakage. It mainly includes elements such as impact on revenue, protection cost, liability if lost, weightage criteria, asset importance etc. Present the topic in a bit more detail with this Analyse Impact Of Cyber Attack On Valuable Assets Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Criteria, Impact On Revenue, Protection Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices To Prevent Cyber Attacks Implementing Cyber Risk Management Process
Best Practices To Prevent Cyber Attacks Implementing Cyber Risk Management ProcessThe following slide illustrates some activities to minimize the probability of cybercrimes within the organization. It includes elements such as utilizing anti-virus, preventing to open suspicious emails, keeping systems up-to date etc. Introducing Best Practices To Prevent Cyber Attacks Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Utilize Anti Virus, Prevent Opening Suspicious, Leverage Firewalls, using this template. Grab it now to reap its full benefits.
-
 Classify Assets Vulnerable To Cyber Attack Implementing Cyber Risk Management Process
Classify Assets Vulnerable To Cyber Attack Implementing Cyber Risk Management ProcessThe following slide depicts some major assets that are more prone to cyber-attack. It mainly includes elements such as sales record, sales lead record, company internal database, customer and product information etc. Present the topic in a bit more detail with this Classify Assets Vulnerable To Cyber Attack Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Assets, Details, Comments. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identifying Impact Of Cyber Attack On Business Implementing Cyber Risk Management Process
Identifying Impact Of Cyber Attack On Business Implementing Cyber Risk Management ProcessThe following slide depicts the negative impact of cyber-crimes on business to build control actions and strategies. It includes key elements such as rising costs, reputational damage, operational disruption, loss of revenue etc. Increase audience engagement and knowledge by dispensing information using Identifying Impact Of Cyber Attack On Business Implementing Cyber Risk Management Process. This template helps you present information on four stages. You can also present information on Reputational Damage, Rising Cost, Operational Disruption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Reduce Attack Surface With Privilege Access Management Implementing Cyber Risk Management Process
Reduce Attack Surface With Privilege Access Management Implementing Cyber Risk Management ProcessThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Deliver an outstanding presentation on the topic using this Reduce Attack Surface With Privilege Access Management Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Users Access Request, Approval Rules, Session Proxy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Types Of Cyber Attacks Encountered By Employees Implementing Cyber Risk Management Process
Types Of Cyber Attacks Encountered By Employees Implementing Cyber Risk Management ProcessThe following slide showcases the various types of cyber-attacks faced by staff to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service etc. Introducing Types Of Cyber Attacks Encountered By Employees Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Malware, Ransomware, Phishing, using this template. Grab it now to reap its full benefits.
-
 Reduce Attack Surface With Privilege Access Management Cyber Risk Assessment
Reduce Attack Surface With Privilege Access Management Cyber Risk AssessmentThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Deliver an outstanding presentation on the topic using this Reduce Attack Surface With Privilege Access Management Cyber Risk Assessment Dispense information and present a thorough explanation of Users Access Request, Record Sessions, Session Proxy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Reduce Attack Surface With Privilege Access Management Creating Cyber Security Awareness
Reduce Attack Surface With Privilege Access Management Creating Cyber Security AwarenessThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Deliver an outstanding presentation on the topic using this Reduce Attack Surface With Privilege Access Management Creating Cyber Security Awareness Dispense information and present a thorough explanation of Time Consuming Process, Incremental Backup using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access Management
Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access ManagementThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Present the topic in a bit more detail with this Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access Management Use it as a tool for discussion and navigation on Access Request, Approval Rules, Session Proxy This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attack And Readiness Assessment And Management Matrix
Cyber Attack And Readiness Assessment And Management MatrixFollowing slide highlights readiness evaluation to cyber security management for compliance with regulations. It further covers process, technology used, people target and basis such as basic, advanced and extended, etc. Introducing our Cyber Attack And Readiness Assessment And Management Matrix set of slides. The topics discussed in these slides are Process, Technology, People. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Attack Vulnerability Icon For Security Management
Cyber Attack Vulnerability Icon For Security ManagementPresenting our set of slides with Cyber Attack Vulnerability Icon For Security Management This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Attack Vulnerability, Security Management
-
 Setting Goals For Cyber Attack Management Business Recovery Plan To Overcome Cyber Security Threat
Setting Goals For Cyber Attack Management Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about time-based goals set for cyber attack management. It includes goals such as mean time to detect incidents, containment time, resolution time, and recovery time. Introducing Setting Goals For Cyber Attack Management Business Recovery Plan To Overcome Cyber Security Threat to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Mean Time To Contain, Mean Time To Resolve, Mean Time To Recover, using this template. Grab it now to reap its full benefits.
-
 Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information Security
Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information SecurityThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type if cyber attacks and formulate strategies to tackle them Present the topic in a bit more detail with this Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Experienced, Organization, Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Faced By Organization In Previous Information Security Risk Management
Cyber Attacks Faced By Organization In Previous Information Security Risk ManagementThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different types of cyber attacks and formulate strategies to tackle them. Deliver an outstanding presentation on the topic using this Cyber Attacks Faced By Organization In Previous Information Security Risk Management. Dispense information and present a thorough explanation of Cyber Attacks Faced, Organization, Previous Financial Year using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
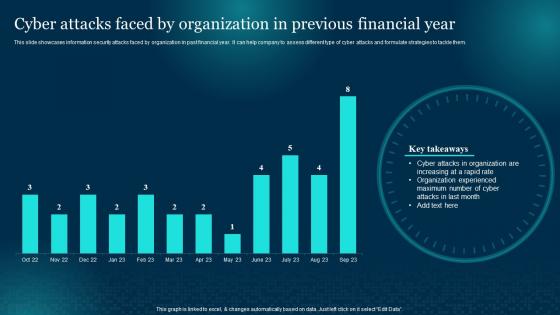 Cyber Attacks Faced By Organization Previous Cybersecurity Risk Analysis And Management Plan
Cyber Attacks Faced By Organization Previous Cybersecurity Risk Analysis And Management PlanThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Deliver an outstanding presentation on the topic using this Cyber Attacks Faced By Organization Previous Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Organization, Financial Year, Experienced using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
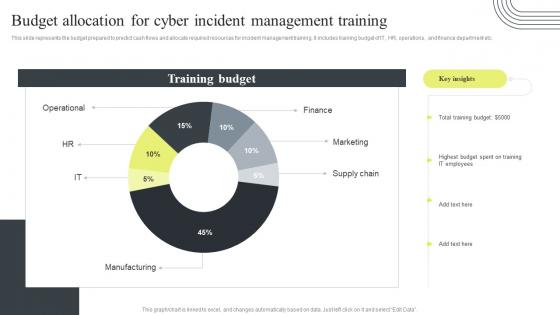 Cyber Security Attacks Response Plan Budget Allocation For Cyber Incident Management Training
Cyber Security Attacks Response Plan Budget Allocation For Cyber Incident Management TrainingThis slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Budget Allocation For Cyber Incident Management Training. Dispense information and present a thorough explanation of Budget Allocation, Cyber Incident Management, Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management Dashboard
Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management DashboardThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management Dashboard. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Cyber Supply Chain Risk Management Dashboard
Cyber Security Attacks Response Plan Cyber Supply Chain Risk Management DashboardThis slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Cyber Supply Chain Risk Management Dashboard. Use it as a tool for discussion and navigation on Cyber Supply Chain, Risk Management, Dashboard, Regulatory Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Enterprise Cyber Risk Management Dashboard
Cyber Security Attacks Response Plan Enterprise Cyber Risk Management DashboardThis slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Enterprise Cyber Risk Management Dashboard. Dispense information and present a thorough explanation of Enterprise Cyber, Risk Management, Dashboard, Action Plan Breakdown using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber threat management workplace determine sequence phases for attack
Cyber threat management workplace determine sequence phases for attackThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Increase audience engagement and knowledge by dispensing information using Cyber Threat Management Workplace Determine Sequence Phases For Attack. This template helps you present information on four stages. You can also present information on Reconnaissance, Weaponization, Delivery, Exploitation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security risk management determine sequence phases for threat attack
Cyber security risk management determine sequence phases for threat attackThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Determine Sequence Phases For Threat Attack. This template helps you present information on four stages. You can also present information on Reconnaissance, Weaponization, Exploitation, Delivery using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine sequence phases for threat attack contd cyber security risk management
Determine sequence phases for threat attack contd cyber security risk managementThis slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Introducing Determine Sequence Phases For Threat Attack Contd Cyber Security Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Installation, Command And Control, Actions And Objectives, Covering Tracks, using this template. Grab it now to reap its full benefits.
-
 A57 Managing Cyber Terrorism 30 Days Plan Cyber Terrorism Attacks
A57 Managing Cyber Terrorism 30 Days Plan Cyber Terrorism AttacksThis slide demonstrates how the cyber security model would operate in the first 30 days and the duties that the company should concentrate on.Present the topic in a bit more detail with this A57 Managing Cyber Terrorism 30 Days Plan Cyber Terrorism Attacks. Use it as a tool for discussion and navigation on Managing Cyber Terrorism 30 Days Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managing Cyber Terrorism 60 Days Plan Cyber Terrorism Attacks
Managing Cyber Terrorism 60 Days Plan Cyber Terrorism AttacksThis slide depicts the plan for the next 60 days after the firm has implemented the cyber security model to tackle cyber terrorism. Deliver an outstanding presentation on the topic using this Managing Cyber Terrorism 60 Days Plan Cyber Terrorism Attacks. Dispense information and present a thorough explanation of Managing Cyber Terrorism 60 Days Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managing Cyber Terrorism Attacks 90 Days Plan Cyber Terrorism Attacks
Managing Cyber Terrorism Attacks 90 Days Plan Cyber Terrorism AttacksThis slide demonstrates the cyber security models 90 day strategy in an enterprise, as well as training compliance and communication strategies. Deliver an outstanding presentation on the topic using this Managing Cyber Terrorism Attacks 90 Days Plan Cyber Terrorism Attacks. Dispense information and present a thorough explanation of Managing Cyber Terrorism Attacks 90 Days Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
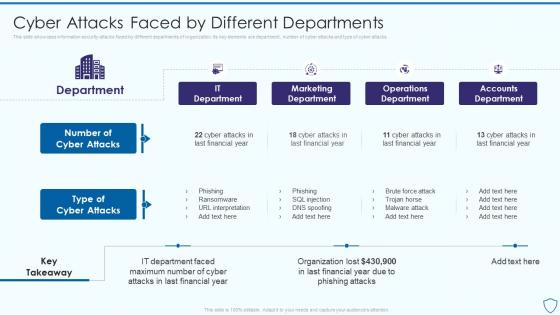 Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By Different
Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By DifferentThis slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks Deliver an outstanding presentation on the topic using this Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By Different. Dispense information and present a thorough explanation of Marketing Department, Operations Department, Accounts Department using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Attacks Faced By Different Departments Information Security Risk Management
Cyber Attacks Faced By Different Departments Information Security Risk ManagementThis slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Introducing Cyber Attacks Faced By Different Departments Information Security Risk Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispense information on Department, Number Of Cyber Attacks, Type Of Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Risk Analysis And Management Plan Cyber Attacks Faced By Different Departments
Cybersecurity Risk Analysis And Management Plan Cyber Attacks Faced By Different DepartmentsThis slide showcases information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks Present the topic in a bit more detail with this Cybersecurity Risk Analysis And Management Plan Cyber Attacks Faced By Different Departments. Use it as a tool for discussion and navigation on Departments, Information, Cyber Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategy To Minimize Cyber Attacks Framework For Cybersecurity Risk Management
Strategy To Minimize Cyber Attacks Framework For Cybersecurity Risk ManagementThis slide indicates the framework for cybersecurity risk management. The major sub components of model are data sources, cyber intelligence and monitoring, threat and vulnerabilities, executive board and IT governance. Present the topic in a bit more detail with this Strategy To Minimize Cyber Attacks Framework For Cybersecurity Risk Management. Use it as a tool for discussion and navigation on Information Sharing, Components Of Framework, Framework For Cybersecurity, Risk Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Leverage Strong And Complex Password Management Cyber Attack Risks Mitigation
Leverage Strong And Complex Password Management Cyber Attack Risks MitigationThe following slide illustrates some practices to ensure strong password management and restrict access to data. It includes activities such as avoiding weak passwords, encryption, multi-factor authentication, conducting test etc. Increase audience engagement and knowledge by dispensing information using Leverage Strong And Complex Password Management Cyber Attack Risks Mitigation. This template helps you present information on four stages. You can also present information on Select Strong Password, Multi Factor Authentication, Conduct Password Test using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Monitor And Assess Vendor Risk Management Cyber Attack Risks Mitigation
Monitor And Assess Vendor Risk Management Cyber Attack Risks MitigationThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Introducing Monitor And Assess Vendor Risk Management Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Web Application Security, Infrastructure Security, Vendor Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Guid Cyber Security Incident Management Checklist During An Incident
Cyber Security Attacks Response Guid Cyber Security Incident Management Checklist During An IncidentThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management during the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using Cyber Security Attacks Response Guid Cyber Security Incident Management Checklist During An Incident. This template helps you present information on one stages. You can also present information on Cyber Security, Incident Management, Checklist During An Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Attacks Response Cyber Security Incident Management Team Roles And Responsibilities
Cyber Security Attacks Response Cyber Security Incident Management Team Roles And ResponsibilitiesPresent the topic in a bit more detail with this Cyber Security Attacks Response Cyber Security Incident Management Team Roles And Responsibilities. Use it as a tool for discussion and navigation on Cyber Security Incident, Management Team, Roles And Responsibilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Impact Of Implementing Cyber Security Incident Management
Cyber Security Attacks Response Impact Of Implementing Cyber Security Incident ManagementThis slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Impact Of Implementing Cyber Security Incident Management. Dispense information and present a thorough explanation of Cyber Security Incident, Management On Organization, Software Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Best Practices For Cybersecurity Incident Management
Cyber Security Attacks Response Plan Best Practices For Cybersecurity Incident ManagementThis slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Introducing Cyber Security Attacks Response Plan Best Practices For Cybersecurity Incident Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Incident Management Process, Incident Management Plan, Responsibilities, Team Members, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Plan Cyber Security Crisis Management Action Plan Timeline
Cyber Security Attacks Response Plan Cyber Security Crisis Management Action Plan TimelineThis slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Cyber Security Crisis Management Action Plan Timeline. Use it as a tool for discussion and navigation on Incident Response, Business Continuity, Review And Recovery, Management Action, Plan Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Five Phases Of Cybersecurity Incident Management
Cyber Security Attacks Response Plan Five Phases Of Cybersecurity Incident ManagementThis slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Introducing Cyber Security Attacks Response Plan Five Phases Of Cybersecurity Incident Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Plan And Prepare, Post Incident Activity, Assess And Design, Incident Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Management Checklist After An Incident Cyber Security Attacks Response
Cyber Security Incident Management Checklist After An Incident Cyber Security Attacks ResponseThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Checklist After An Incident Cyber Security Attacks Response. This template helps you present information on one stages. You can also present information on Cyber Security, Incident Management, Checklist After An Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Management Team Structure Cyber Security Attacks Response Plan
Cyber Security Incident Management Team Structure Cyber Security Attacks Response PlanThis slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team. Deliver an outstanding presentation on the topic using this Cyber Security Incident Management Team Structure Cyber Security Attacks Response Plan. Dispense information and present a thorough explanation of Cyber Security, Incident Management, Team Structure, Human Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response Plan
Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response PlanThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response Plan. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 K55 Cyber Security Attacks Response Cyber Security Incident Management Checklist Before
K55 Cyber Security Attacks Response Cyber Security Incident Management Checklist BeforeThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management before the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using K55 Cyber Security Attacks Response Cyber Security Incident Management Checklist Before. This template helps you present information on one stages. You can also present information on Cyber Security, Incident Management, Checklist Before An Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Crisis management plan cyber attacks ppt powerpoint presentation show demonstration cpb
Crisis management plan cyber attacks ppt powerpoint presentation show demonstration cpbPresenting this set of slides with name Crisis Management Plan Cyber Attacks Ppt Powerpoint Presentation Show Demonstration Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Crisis Management Plan Cyber Attacks to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.



