Powerpoint Templates and Google slides for Cryptography Algorithm
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 About Asymmetric Algorithm Overview And Benefits Cloud Cryptography
About Asymmetric Algorithm Overview And Benefits Cloud CryptographyThis slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc. Present the topic in a bit more detail with this About Asymmetric Algorithm Overview And Benefits Cloud Cryptography. Use it as a tool for discussion and navigation on Overview, Asymmetric, Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 About Symmetric Algorithm Overview And Benefits Cloud Cryptography
About Symmetric Algorithm Overview And Benefits Cloud CryptographyThis slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc. Deliver an outstanding presentation on the topic using this About Symmetric Algorithm Overview And Benefits Cloud Cryptography. Dispense information and present a thorough explanation of Overview, Automatically, Environments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Applications Of Standard For Advanced Encryption Aes Algorithm Cloud Cryptography
Applications Of Standard For Advanced Encryption Aes Algorithm Cloud CryptographyThis slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc. Introducing Applications Of Standard For Advanced Encryption Aes Algorithm Cloud Cryptography to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Wireless Security, General File Encryption, Encrypted Browsing, using this template. Grab it now to reap its full benefits.
-
 Cryptographic Algorithms Used In Data Security Cloud Cryptography
Cryptographic Algorithms Used In Data Security Cloud CryptographyThis slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. Deliver an outstanding presentation on the topic using this Cryptographic Algorithms Used In Data Security Cloud Cryptography. Dispense information and present a thorough explanation of Cryptographic, Algorithms, Data Encryption Standard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Elliptic Curve Cryptography Ecc Asymmetric Algorithm Cloud Cryptography
Elliptic Curve Cryptography Ecc Asymmetric Algorithm Cloud CryptographyThis slide talks about the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different applications of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc. Present the topic in a bit more detail with this Elliptic Curve Cryptography Ecc Asymmetric Algorithm Cloud Cryptography. Use it as a tool for discussion and navigation on Overview, Applications, Cryptocurrency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1636 Working Process Of Asymmetric Cryptographic Algorithm Cloud Cryptography
F1636 Working Process Of Asymmetric Cryptographic Algorithm Cloud CryptographyThis slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc. Present the topic in a bit more detail with this F1636 Working Process Of Asymmetric Cryptographic Algorithm Cloud Cryptography. Use it as a tool for discussion and navigation on Process, Asymmetric, Cryptographic Algorithm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Importance Of Cryptographic Algorithms In Cloud Computing Cloud Cryptography
Importance Of Cryptographic Algorithms In Cloud Computing Cloud CryptographyThis slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc. Introducing Importance Of Cryptographic Algorithms In Cloud Computing Cloud Cryptography to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Strengthens Authentication, Enhances Compliance, Ensures Data Integrity, using this template. Grab it now to reap its full benefits.
-
 Methods Used By Asymmetric Algorithm To Provide Cloud Security Cloud Cryptography
Methods Used By Asymmetric Algorithm To Provide Cloud Security Cloud CryptographyThis slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures. Introducing Methods Used By Asymmetric Algorithm To Provide Cloud Security Cloud Cryptography to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Key Management, Digital Signatures, using this template. Grab it now to reap its full benefits.
-
 Methods Used By Symmetric Algorithm To Provide Cloud Security Cloud Cryptography
Methods Used By Symmetric Algorithm To Provide Cloud Security Cloud CryptographyThis slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc. Increase audience engagement and knowledge by dispensing information using Methods Used By Symmetric Algorithm To Provide Cloud Security Cloud Cryptography. This template helps you present information on four stages. You can also present information on Encryption, Access Control, Key Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Rivest Shamir Adleman Rsa Asymmetric Algorithm Cloud Cryptography
Rivest Shamir Adleman Rsa Asymmetric Algorithm Cloud CryptographyThis slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc. Present the topic in a bit more detail with this Rivest Shamir Adleman Rsa Asymmetric Algorithm Cloud Cryptography. Use it as a tool for discussion and navigation on Asymmetric, Communication, Transactions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Workflow Of Cloud Cryptography Hashing Algorithm Cloud Cryptography
Workflow Of Cloud Cryptography Hashing Algorithm Cloud CryptographyThis slide demonstrates the working structure of hashing technique of cloud cryptography with the help of an illustrative diagram. The key components included are original data, hashing algorithm, one-way hash, digital signature, etc. Present the topic in a bit more detail with this Workflow Of Cloud Cryptography Hashing Algorithm Cloud Cryptography. Use it as a tool for discussion and navigation on Cryptography, Hashing Function, Data Storage . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Of Common Data Encryption Des Algorithm Cloud Cryptography
Working Of Common Data Encryption Des Algorithm Cloud CryptographyThis slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Deliver an outstanding presentation on the topic using this Working Of Common Data Encryption Des Algorithm Cloud Cryptography. Dispense information and present a thorough explanation of Pseudorandom, Initialization, Independent using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Working Of Standard For Advanced Encryption Aes Algorithm Cloud Cryptography
Working Of Standard For Advanced Encryption Aes Algorithm Cloud CryptographyThis slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc. Present the topic in a bit more detail with this Working Of Standard For Advanced Encryption Aes Algorithm Cloud Cryptography. Use it as a tool for discussion and navigation on Demonstrates, Encryption, Algorithm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Process Of Symmetric Cryptographic Algorithm Cloud Cryptography
Working Process Of Symmetric Cryptographic Algorithm Cloud CryptographyThis slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc. Deliver an outstanding presentation on the topic using this Working Process Of Symmetric Cryptographic Algorithm Cloud Cryptography. Dispense information and present a thorough explanation of Process, Symmetric, Cryptographic using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
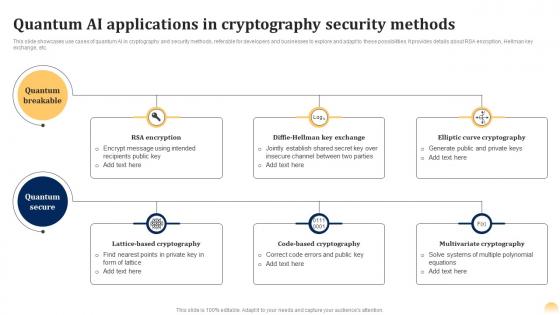 Quantum Cryptography Security Quantum Ai Fusing Quantum Computing With Intelligent Algorithms AI SS
Quantum Cryptography Security Quantum Ai Fusing Quantum Computing With Intelligent Algorithms AI SSThis slide showcases use cases of quantum AI in cryptography and security methods, referable for developers and businesses to explore and adapt to these possibilities. It provides details about RSA encryption, Hellman key exchange, etc. Present the topic in a bit more detail with this Quantum Cryptography Security Quantum Ai Fusing Quantum Computing With Intelligent Algorithms AI SS. Use it as a tool for discussion and navigation on Elliptic Curve Cryptography, Code Based Cryptography, Multivariate Cryptography. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Algorithms Based On Elliptic Curve Cryptography Encryption For Data Privacy In Digital Age It
Algorithms Based On Elliptic Curve Cryptography Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the applications of elliptic curve cryptography ECC in digital signatures, encryption, and key agreement. The algorithms discussed are ECDSA Elliptic Curve Digital Signature Algorithm, ECDH Elliptic Curve Diffie-Hellman, etc. Introducing Algorithms Based On Elliptic Curve Cryptography Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Digital Signatures, Minimal Computational Power, Fast Key Generation, using this template. Grab it now to reap its full benefits.
-
 Applications Of Elliptic Curve Cryptography Algorithm Encryption For Data Privacy In Digital Age It
Applications Of Elliptic Curve Cryptography Algorithm Encryption For Data Privacy In Digital Age ItThis slide outlines the various fields which employ Elliptic Curve Cryptography algorithm to provide security. The applications of ECC discussed in this slide are Tor, National Security Agency NSA, blockchain, iMessage and Secure Sockets Layer SSL. Introducing Applications Of Elliptic Curve Cryptography Algorithm Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Blockchain, Cryptography Algorithm, Applications, using this template. Grab it now to reap its full benefits.
-
 Asymmetric Cryptography Using Digital Signature Algorithm Encryption For Data Privacy In Digital Age It
Asymmetric Cryptography Using Digital Signature Algorithm Encryption For Data Privacy In Digital Age ItThis slide demonstrates the working of Digital Signature Algorithm. The purpose of this slide is to outline the benefits of DSA asymmetric cryptography. The advantages of DSA are message authentication, identity verification and non-repudiation. Present the topic in a bit more detail with this Asymmetric Cryptography Using Digital Signature Algorithm Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Message Authentication, Integrity Verification, Non Repudiation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Benefits Of Elliptic Curve Cryptography Algorithm Encryption For Data Privacy In Digital Age It
Benefits Of Elliptic Curve Cryptography Algorithm Encryption For Data Privacy In Digital Age ItThis slide represents the advantages of Elliptic Curve Cryptography algorithm ECC. The benefits discussed in this slide are shorter key lengths, minimal computational power, faster key generation and incredibly fast generation of digital signatures. Increase audience engagement and knowledge by dispensing information using Benefits Of Elliptic Curve Cryptography Algorithm Encryption For Data Privacy In Digital Age It. This template helps you present information on four stages. You can also present information on Shorter Key Lengths, Minimal Computational Power, Fast Key Generation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Disadvantages Of Elliptic Curve Cryptography Algorithm Encryption For Data Privacy In Digital Age It
Disadvantages Of Elliptic Curve Cryptography Algorithm Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to outline the drawbacks of using Elliptic Curve Cryptography ECC algorithm. The disadvantages of ECC algorithm are complicated implementation, random number generator, patents, signature verification, etc. Deliver an outstanding presentation on the topic using this Disadvantages Of Elliptic Curve Cryptography Algorithm Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Cryptography, Algorithm, Disadvantages using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Elliptic Curve Cryptography Ecc Asymmetric Algorithm Encryption For Data Privacy In Digital Age It
Elliptic Curve Cryptography Ecc Asymmetric Algorithm Encryption For Data Privacy In Digital Age ItThis slide discusses the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different uses of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc. Present the topic in a bit more detail with this Elliptic Curve Cryptography Ecc Asymmetric Algorithm Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Algorithms, Asymmetric, Cryptography. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Algorithms Of Cryptography In Cybersecurity
Encryption Algorithms Of Cryptography In CybersecurityThis slide elaborates on encrypt algorithms in cyber security and provides details about how to secure servers from hackers in organization. It includes elements such as blowfish, twofish, etc. Presenting our set of slides with Encryption Algorithms Of Cryptography In Cybersecurity. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Triple Data Encryption Standard, Advanced Encryption Standard, Blowfish.



