Powerpoint Templates and Google slides for Confidential Computing
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Confidential Computing V2 Powerpoint Presentation Slides
Confidential Computing V2 Powerpoint Presentation SlidesThis complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of eighty nine slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.
-
 Confidential Computing IT Powerpoint Presentation Slides
Confidential Computing IT Powerpoint Presentation SlidesThis complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of eighty nine slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.
-
 Confidential Computing Consortium Powerpoint Presentation Slides
Confidential Computing Consortium Powerpoint Presentation SlidesDeliver an informational PPT on various topics by using this Confidential Computing Consortium Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with eighty three slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
-
 Confidential Computing Market Powerpoint Presentation Slides
Confidential Computing Market Powerpoint Presentation SlidesThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Confidential Computing Market Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of eighty three slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Confidential Computing Technology Powerpoint Presentation Slides
Confidential Computing Technology Powerpoint Presentation SlidesEnthrall your audience with this Confidential Computing Technology Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising eighty two slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Confidential Cloud Computing Powerpoint Presentation Slides
Confidential Cloud Computing Powerpoint Presentation SlidesEnthrall your audience with this Confidential Cloud Computing Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising eighty three slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Confidential Computing Hardware Powerpoint Presentation Slides
Confidential Computing Hardware Powerpoint Presentation SlidesEnthrall your audience with this Confidential Computing Hardware Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising eighty three slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Confidential Computing Market Confidential Computing Adoption In North America And Apac
Confidential Computing Market Confidential Computing Adoption In North America And ApacThis slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. Present the topic in a bit more detail with this Confidential Computing Market Confidential Computing Adoption In North America And Apac. Use it as a tool for discussion and navigation on Confidential, Computing, Adoption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
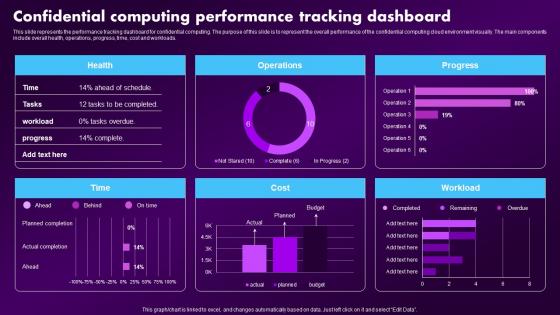 Confidential Computing Market Confidential Computing Performance Tracking Dashboard
Confidential Computing Market Confidential Computing Performance Tracking DashboardThis slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. Present the topic in a bit more detail with this Confidential Computing Market Confidential Computing Performance Tracking Dashboard. Use it as a tool for discussion and navigation on Dashboard, Confidential, Performance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Market Confidential Computing Technology Segment Market Growth
Confidential Computing Market Confidential Computing Technology Segment Market GrowthThis slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. Present the topic in a bit more detail with this Confidential Computing Market Confidential Computing Technology Segment Market Growth. Use it as a tool for discussion and navigation on Technology, Growth, Confidential. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Market Confidential Computing Total Addressable Market Overview
Confidential Computing Market Confidential Computing Total Addressable Market OverviewThis slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026. Deliver an outstanding presentation on the topic using this Confidential Computing Market Confidential Computing Total Addressable Market Overview. Dispense information and present a thorough explanation of Overview, Applications, Inexpensive using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F1599 Confidential Computing Adoption By Regulated Industries Confidential Computing Market
F1599 Confidential Computing Adoption By Regulated Industries Confidential Computing MarketThis slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Present the topic in a bit more detail with this F1599 Confidential Computing Adoption By Regulated Industries Confidential Computing Market. Use it as a tool for discussion and navigation on Businesses, Confidential, Demonstrate. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1604 Confidential Computing Market Driven By Cloud And Security Confidential Computing Market
F1604 Confidential Computing Market Driven By Cloud And Security Confidential Computing MarketThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Present the topic in a bit more detail with this F1604 Confidential Computing Market Driven By Cloud And Security Confidential Computing Market. Use it as a tool for discussion and navigation on Enterprise, Awareness, Confidential. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents Confidential Computing Market
Table Of Contents Confidential Computing MarketPresent the topic in a bit more detail with this Table Of Contents Confidential Computing Market. Use it as a tool for discussion and navigation on Confidential Computing Overview, Importance Of Confidential Computing, Confidential Computing Consortium. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Adoption By Regulated Industries Confidential Computing Hardware
Confidential Computing Adoption By Regulated Industries Confidential Computing HardwareThis slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Present the topic in a bit more detail with this Confidential Computing Adoption By Regulated Industries Confidential Computing Hardware. Use it as a tool for discussion and navigation on Confidential Computing Adoption, Demonstrate The Adoption Rate, Public Sector, Retail And CPG. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Adoption In North America Confidential Computing Hardware
Confidential Computing Adoption In North America Confidential Computing HardwareThis slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. Deliver an outstanding presentation on the topic using this Confidential Computing Adoption In North America Confidential Computing Hardware. Dispense information and present a thorough explanation of Adoption Rate, Confidential Computing, Demonstrate, Growth Drivers, Specific Data Privacy Legislation, European Market using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
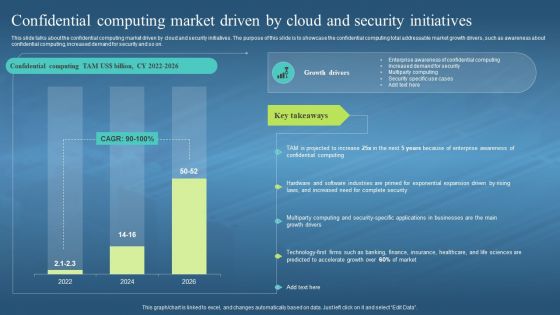 Confidential Computing Market Driven By Cloud And Security Confidential Computing Hardware
Confidential Computing Market Driven By Cloud And Security Confidential Computing HardwareThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Deliver an outstanding presentation on the topic using this Confidential Computing Market Driven By Cloud And Security Confidential Computing Hardware. Dispense information and present a thorough explanation of Confidential Computing, Market Driven By Cloud, Security Initiatives, Awareness About Confidential Computing, Demand For Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Technology Segment Market Confidential Computing Hardware
Confidential Computing Technology Segment Market Confidential Computing HardwareThis slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. Present the topic in a bit more detail with this Confidential Computing Technology Segment Market Confidential Computing Hardware. Use it as a tool for discussion and navigation on Technology Segment, Market Growth, Confidential Computing, Software And Hardware. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Total Addressable Market Confidential Computing Hardware
Confidential Computing Total Addressable Market Confidential Computing HardwareThis slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026. Present the topic in a bit more detail with this Confidential Computing Total Addressable Market Confidential Computing Hardware. Use it as a tool for discussion and navigation on Confidential Computing, Addressable Market, Demonstrate The Best, Cloud Computing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents Confidential Computing Hardware Ppt Icon File Formats
Table Of Contents Confidential Computing Hardware Ppt Icon File FormatsIncrease audience engagement and knowledge by dispensing information using Table Of Contents Confidential Computing Hardware Ppt Icon File Formats. This template helps you present information on six stages. You can also present information on Importance Of Confidential Computing, Confidential Computing Overview, Architecture, Working And Approaches Of Confidential Computing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Consortium Confidential Computing Adoption By Regulated Industries
Confidential Computing Consortium Confidential Computing Adoption By Regulated IndustriesThis slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Deliver an outstanding presentation on the topic using this Confidential Computing Consortium Confidential Computing Adoption By Regulated Industries. Dispense information and present a thorough explanation of Confidential Computing Adoption, Demonstrate The Adoption Rate, Public Sector using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Consortium Confidential Computing Market Driven By Cloud And Security
Confidential Computing Consortium Confidential Computing Market Driven By Cloud And SecurityThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Present the topic in a bit more detail with this Confidential Computing Consortium Confidential Computing Market Driven By Cloud And Security. Use it as a tool for discussion and navigation on Confidential Computing, Market Driven By Cloud, Security Initiatives, Security Specific Use Cases. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Consortium Confidential Computing Performance Tracking Dashboard
Confidential Computing Consortium Confidential Computing Performance Tracking DashboardThis slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. Present the topic in a bit more detail with this Confidential Computing Consortium Confidential Computing Performance Tracking Dashboard. Use it as a tool for discussion and navigation on Confidential Computing Performance, Tracking Dashboard, Cloud Environment Visually. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Consortium Confidential Computing Technology Segment Market Growth
Confidential Computing Consortium Confidential Computing Technology Segment Market GrowthThis slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. Present the topic in a bit more detail with this Confidential Computing Consortium Confidential Computing Technology Segment Market Growth. Use it as a tool for discussion and navigation on Confidential Computing Technology, Segment Market Growth, Technology Segment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Consortium Confidential Computing Total Addressable Market Overview
Confidential Computing Consortium Confidential Computing Total Addressable Market OverviewThis slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026. Deliver an outstanding presentation on the topic using this Confidential Computing Consortium Confidential Computing Total Addressable Market Overview. Dispense information and present a thorough explanation of Confidential Computing, Addressable Market, Median Case Scenario, Worst Case Scenario using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For Confidential Computing Consortium Ppt Ideas Background Designs
Table Of Contents For Confidential Computing Consortium Ppt Ideas Background DesignsIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Confidential Computing Consortium Ppt Ideas Background Designs. This template helps you present information on six stages. You can also present information on Confidential Computing Overview, Confidential Computing Consortium, Technologies Overview using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 K86 Confidential Computing Adoption In North America And APAC Confidential Computing Consortium
K86 Confidential Computing Adoption In North America And APAC Confidential Computing ConsortiumThis slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. Present the topic in a bit more detail with this K86 Confidential Computing Adoption In North America And APAC Confidential Computing Consortium. Use it as a tool for discussion and navigation on Adoption Rate, Confidential Computing, Demonstrate, Data Privacy Legislation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Hardware Confidential Computing Performance Tracking Dashboard
Confidential Computing Hardware Confidential Computing Performance Tracking DashboardThis slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Confidential Computing Performance Tracking Dashboard. Dispense information and present a thorough explanation of Performance Tracking Dashboard, Confidential Computing, Cloud Environment Visually, Cost And Workloads using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Adoption By Regulated Industries Confidential Computing System Technology
Confidential Adoption By Regulated Industries Confidential Computing System TechnologyThis slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Present the topic in a bit more detail with this Confidential Adoption By Regulated Industries Confidential Computing System Technology. Use it as a tool for discussion and navigation on Businesses, Manufacturers, Confidential. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Driven By Cloud And Security Initiatives Confidential Computing System Technology
Confidential Driven By Cloud And Security Initiatives Confidential Computing System TechnologyThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Deliver an outstanding presentation on the topic using this Confidential Driven By Cloud And Security Initiatives Confidential Computing System Technology. Dispense information and present a thorough explanation of Confidential, Enterprise, Awareness using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Technology Segment Market Growth Confidential Computing System Technology
Confidential Technology Segment Market Growth Confidential Computing System TechnologyThis slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. Present the topic in a bit more detail with this Confidential Technology Segment Market Growth Confidential Computing System Technology. Use it as a tool for discussion and navigation on Growth, Technology, Confidential. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Total Addressable Market Overview Confidential Computing System Technology
Confidential Total Addressable Market Overview Confidential Computing System TechnologyThis slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026. Deliver an outstanding presentation on the topic using this Confidential Total Addressable Market Overview Confidential Computing System Technology. Dispense information and present a thorough explanation of Overview, Confidential, Computing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For Confidential Computing System Technology
Table Of Contents For Confidential Computing System TechnologyIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Confidential Computing System Technology. This template helps you present information on six stages. You can also present information on Confidential Computing Overview, Importance Of Confidential Computing, Confidential Computing Consortium using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing System Technology Performance Tracking Dashboard
Confidential Computing System Technology Performance Tracking DashboardThis slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. Deliver an outstanding presentation on the topic using this Confidential Computing System Technology Performance Tracking Dashboard. Dispense information and present a thorough explanation of Performance, Dashboard, Confidential using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing V2 Adoption By Regulated Industries Ppt Inspiration Show
Confidential Computing V2 Adoption By Regulated Industries Ppt Inspiration ShowThis slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Present the topic in a bit more detail with this Confidential Computing V2 Adoption By Regulated Industries Ppt Inspiration Show. Use it as a tool for discussion and navigation on Confidential Computing Adoption, Confidential Computing, Edge Computing, Data And Analytics Based Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing V2 Adoption In North America And Apac
Confidential Computing V2 Adoption In North America And ApacThis slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. Deliver an outstanding presentation on the topic using this Confidential Computing V2 Adoption In North America And Apac. Dispense information and present a thorough explanation of Adoption Rate, Confidential Computing, Confidential Computing, Country Specific Data, Privacy Legislation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing V2 Market Driven By Cloud And Security Initiatives
Confidential Computing V2 Market Driven By Cloud And Security InitiativesThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Deliver an outstanding presentation on the topic using this Confidential Computing V2 Market Driven By Cloud And Security Initiatives. Dispense information and present a thorough explanation of Confidential Computing Market, Cloud And Security Initiatives, Total Addressable Market using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing V2 Performance Tracking Dashboard Ppt Inspiration Aids
Confidential Computing V2 Performance Tracking Dashboard Ppt Inspiration AidsThis slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. Deliver an outstanding presentation on the topic using this Confidential Computing V2 Performance Tracking Dashboard Ppt Inspiration Aids. Dispense information and present a thorough explanation of Confidential Computing Performance, Tracking Dashboard, Cost And Workloads, Cloud Environment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing V2 Technology Segment Market Growth
Confidential Computing V2 Technology Segment Market GrowthThis slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. Deliver an outstanding presentation on the topic using this Confidential Computing V2 Technology Segment Market Growth. Dispense information and present a thorough explanation of Confidential Computing Technology, Segment Market Growth, Technology Segment Market Growth using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing V2 Total Addressable Market Overview Ppt Inspiration Topics
Confidential Computing V2 Total Addressable Market Overview Ppt Inspiration TopicsThis slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026. Present the topic in a bit more detail with this Confidential Computing V2 Total Addressable Market Overview Ppt Inspiration Topics. Use it as a tool for discussion and navigation on Confidential Computing, Addressable Market Overview, Worst Case Scenarios. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents For Confidential Computing V2 Ppt Infographics Demonstration
Table Of Contents For Confidential Computing V2 Ppt Infographics DemonstrationIntroducing Table Of Contents For Confidential Computing V2 Ppt Infographics Demonstration to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Confidential Computing Overview, Confidential Computing Hardware, Technologies Overview, Confidential Computing Consortium, using this template. Grab it now to reap its full benefits.
-
 Agenda For Confidential Computing Market
Agenda For Confidential Computing MarketIntroducing Agenda For Confidential Computing Market to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Confidential, Architecture, Computing Environment, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Market Ack Tee 2 0 Architecture And Workflow
Confidential Computing Market Ack Tee 2 0 Architecture And WorkflowThis slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Present the topic in a bit more detail with this Confidential Computing Market Ack Tee 2 0 Architecture And Workflow. Use it as a tool for discussion and navigation on Architecture, Workflow, Confidential Computing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Market Ack Tee Introduction And Version 1 0
Confidential Computing Market Ack Tee Introduction And Version 1 0This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. Deliver an outstanding presentation on the topic using this Confidential Computing Market Ack Tee Introduction And Version 1 0. Dispense information and present a thorough explanation of Introduction, Operations, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Market Benefits Of Confidential Computing For Businesses
Confidential Computing Market Benefits Of Confidential Computing For BusinessesThis slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on. Present the topic in a bit more detail with this Confidential Computing Market Benefits Of Confidential Computing For Businesses. Use it as a tool for discussion and navigation on Businesses, Solutions, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Market Budget For Implementing Confidential Computing Architecture
Confidential Computing Market Budget For Implementing Confidential Computing ArchitectureThis slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Deliver an outstanding presentation on the topic using this Confidential Computing Market Budget For Implementing Confidential Computing Architecture. Dispense information and present a thorough explanation of Implementing, Confidential, Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Market Business Scenarios Of Confidential Computing Platform
Confidential Computing Market Business Scenarios Of Confidential Computing PlatformThis slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. Increase audience engagement and knowledge by dispensing information using Confidential Computing Market Business Scenarios Of Confidential Computing Platform. This template helps you present information on seven stages. You can also present information on Blockchain, Finance, Edge Computing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Market Case Study Irene Energy
Confidential Computing Market Case Study Irene EnergyThis slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact. Present the topic in a bit more detail with this Confidential Computing Market Case Study Irene Energy. Use it as a tool for discussion and navigation on Financial, Manufacturers, Distributors. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Market Checklist To Implement Confidential Computing Architecture
Confidential Computing Market Checklist To Implement Confidential Computing ArchitectureThis slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person. Deliver an outstanding presentation on the topic using this Confidential Computing Market Checklist To Implement Confidential Computing Architecture. Dispense information and present a thorough explanation of Confidential, Computing, Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Market Client Signature And Server Signature In Inclavare Containers
Confidential Computing Market Client Signature And Server Signature In Inclavare ContainersThis slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature. Present the topic in a bit more detail with this Confidential Computing Market Client Signature And Server Signature In Inclavare Containers. Use it as a tool for discussion and navigation on Business, Certifications, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Market Companies Paving The Path For Confidential Computing
Confidential Computing Market Companies Paving The Path For Confidential ComputingThis slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. Introducing Confidential Computing Market Companies Paving The Path For Confidential Computing to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Hub Security, Microsoft Azure, Google Cloud, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Market Components Of Inclavare Containers Architecture
Confidential Computing Market Components Of Inclavare Containers ArchitectureThis slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API. Increase audience engagement and knowledge by dispensing information using Confidential Computing Market Components Of Inclavare Containers Architecture. This template helps you present information on eight stages. You can also present information on Language Runtime, Containerd, Containers Architecture using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Market Confidential Computing Applications In Different Sectors
Confidential Computing Market Confidential Computing Applications In Different SectorsThis slide represents the applications of confidential computing in different sectors. This slide aims to demonstrate the confidential computing applications in healthcare and research, finance, engineering and manufacturing, and automobile sectors. Deliver an outstanding presentation on the topic using this Confidential Computing Market Confidential Computing Applications In Different Sectors. Dispense information and present a thorough explanation of Confidential, Computing, Applications using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Market Confidential Computing Architecture Implementation Timeline
Confidential Computing Market Confidential Computing Architecture Implementation TimelineThis slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Introducing Confidential Computing Market Confidential Computing Architecture Implementation Timeline to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Architecture, Implementation, Timeline, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Market Confidential Computing Consortium Overview And Benefits
Confidential Computing Market Confidential Computing Consortium Overview And BenefitsThis slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. Present the topic in a bit more detail with this Confidential Computing Market Confidential Computing Consortium Overview And Benefits. Use it as a tool for discussion and navigation on Confidential, Consortium, Overview. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Market Confidential Computing Executive Summary Of Key Findings
Confidential Computing Market Confidential Computing Executive Summary Of Key FindingsThis slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on. Deliver an outstanding presentation on the topic using this CConfidential Computing Market Confidential Computing Executive Summary Of Key Findings. Dispense information and present a thorough explanation of Implementation, Confidential, Expansion using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Market Confidential Computing For Total Privacy Assurance
Confidential Computing Market Confidential Computing For Total Privacy AssuranceThis slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Present the topic in a bit more detail with this Confidential Computing Market Confidential Computing For Total Privacy Assurance. Use it as a tool for discussion and navigation on Confidential, Servers, Microservices. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Market Confidential Computing Market Segments Overview
Confidential Computing Market Confidential Computing Market Segments OverviewThis slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description. Deliver an outstanding presentation on the topic using this Confidential Computing Market Confidential Computing Market Segments Overview. Dispense information and present a thorough explanation of Overview, Confidential, Computing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Market Confidential Computing Platform For Healthcare Industry
Confidential Computing Market Confidential Computing Platform For Healthcare IndustryThis slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation. Deliver an outstanding presentation on the topic using this Confidential Computing Market Confidential Computing Platform For Healthcare Industry. Dispense information and present a thorough explanation of Authenticity, Confidential, Computing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Market Confidential Computing Use Cases And Ecosystem
Confidential Computing Market Confidential Computing Use Cases And EcosystemThis slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Present the topic in a bit more detail with this Confidential Computing Market Confidential Computing Use Cases And Ecosystem. Use it as a tool for discussion and navigation on Key Management Systems, Secure Cloud Migration, Database Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.




