Powerpoint Templates and Google slides for Computing Architecture
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Grid Computing Architecture Powerpoint Presentation Slides
Grid Computing Architecture Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Grid Computing Architecture Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fifty eight slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Serverless computing framework architecture powerpoint presentation slides
Serverless computing framework architecture powerpoint presentation slidesPresenting our Serverless Computing Framework Architecture Powerpoint Presentation Slides. This is a 100% editable and adaptable PPT slide. You can save it in different formats like PDF, JPG, and PNG. It can be edited with different colors, fonts, font sizes, and font types of the template as per your requirements. This template supports the standard (4:3) and widescreen (16:9) format. It is also compatible with Google slides.
-
 Edge Computing Technology Edge Computing Architecture General Overview AI SS
Edge Computing Technology Edge Computing Architecture General Overview AI SSThis slide showcases general overview of edge computing architecture with cloud, edge and device layer. It provides details about data warehousing, big data processing, virtualization, controllers, sensors, etc. Introducing Edge Computing Technology Edge Computing Architecture General Overview AI SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Virtualization, Control Response, Data Caching And Buffering, Data Processing And Reduction, Local Network, using this template. Grab it now to reap its full benefits.
-
 IoT edge computing architecture applications and role of IOT edge computing IoT SS V
IoT edge computing architecture applications and role of IOT edge computing IoT SS VFollowing slide showcases IoT and edge computing architecture that helps to understand working process. It include layers such as IoT device, edge and cloud layers. Introducing IoT edge computing architecture applications and role of IOT edge computing IoT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Server, Cloud Layers, Edge Layers, using this template. Grab it now to reap its full benefits.
-
 Cloud Layer Architectural Governance Computing Processing Moonrise
Cloud Layer Architectural Governance Computing Processing MoonriseIt covers all the important concepts and has relevant templates which cater to your business needs. This complete deck has PPT slides on Cloud Layer Architectural Governance Computing Processing Moonrise with well suited graphics and subject driven content. This deck consists of total of ten slides. All templates are completely editable for your convenience. You can change the colour, text and font size of these slides. You can add or delete the content as per your requirement. Get access to this professionally designed complete deck presentation by clicking the download button below.
-
 Cloud service models it architecture of cloud computing
Cloud service models it architecture of cloud computingThis slide shows cloud computing architecture, including client infrastructure that falls under the front end and back end elements such as application, service, runtime cloud, management, storage, etc. Deliver an outstanding presentation on the topic using this Cloud Service Models It Architecture Of Cloud Computing. Dispense information and present a thorough explanation of Client Infrastructure, Management, Deployment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Market Ack Tee 2 0 Architecture And Workflow
Confidential Computing Market Ack Tee 2 0 Architecture And WorkflowThis slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Present the topic in a bit more detail with this Confidential Computing Market Ack Tee 2 0 Architecture And Workflow. Use it as a tool for discussion and navigation on Architecture, Workflow, Confidential Computing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Market Budget For Implementing Confidential Computing Architecture
Confidential Computing Market Budget For Implementing Confidential Computing ArchitectureThis slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Deliver an outstanding presentation on the topic using this Confidential Computing Market Budget For Implementing Confidential Computing Architecture. Dispense information and present a thorough explanation of Implementing, Confidential, Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Market Checklist To Implement Confidential Computing Architecture
Confidential Computing Market Checklist To Implement Confidential Computing ArchitectureThis slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person. Deliver an outstanding presentation on the topic using this Confidential Computing Market Checklist To Implement Confidential Computing Architecture. Dispense information and present a thorough explanation of Confidential, Computing, Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Market Components Of Inclavare Containers Architecture
Confidential Computing Market Components Of Inclavare Containers ArchitectureThis slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API. Increase audience engagement and knowledge by dispensing information using Confidential Computing Market Components Of Inclavare Containers Architecture. This template helps you present information on eight stages. You can also present information on Language Runtime, Containerd, Containers Architecture using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Market Confidential Computing Architecture Implementation Timeline
Confidential Computing Market Confidential Computing Architecture Implementation TimelineThis slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Introducing Confidential Computing Market Confidential Computing Architecture Implementation Timeline to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Architecture, Implementation, Timeline, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Market Inclavare Confidential Containers Architecture In Tee
Confidential Computing Market Inclavare Confidential Containers Architecture In TeeThis slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. Present the topic in a bit more detail with this Confidential Computing Market Inclavare Confidential Containers Architecture In Tee. Use it as a tool for discussion and navigation on Confidential, Containers, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Market Multiparty Privacy Preserving Computation Architecture Design
Confidential Computing Market Multiparty Privacy Preserving Computation Architecture DesignThis slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on Deliver an outstanding presentation on the topic using this Confidential Computing Market Multiparty Privacy Preserving Computation Architecture Design. Dispense information and present a thorough explanation of Computation, Architecture, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Market Occlum System Architecture And Features
Confidential Computing Market Occlum System Architecture And FeaturesThis slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on. Deliver an outstanding presentation on the topic using this Confidential Computing Market Occlum System Architecture And Features. Dispense information and present a thorough explanation of Architecture, Environment, Multi Process Support using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F1600 Confidential Computing Architecture And Realms Working Confidential Computing Market
F1600 Confidential Computing Architecture And Realms Working Confidential Computing MarketThis slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on. Deliver an outstanding presentation on the topic using this F1600 Confidential Computing Architecture And Realms Working Confidential Computing Market. Dispense information and present a thorough explanation of Confidential, Computing, Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F1601 Confidential Computing Architecture Based On Azure Services Confidential Computing Market
F1601 Confidential Computing Architecture Based On Azure Services Confidential Computing MarketThis slide represents the architecture of confidential computing based on Azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. Present the topic in a bit more detail with this F1601 Confidential Computing Architecture Based On Azure Services Confidential Computing Market. Use it as a tool for discussion and navigation on Components, Sensitive Application Logs, Executing Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
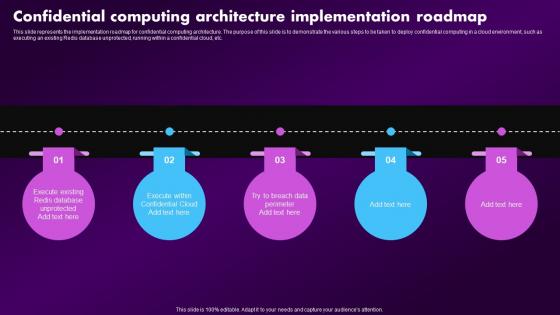 F1602 Confidential Computing Architecture Implementation Roadmap Confidential Computing Market
F1602 Confidential Computing Architecture Implementation Roadmap Confidential Computing MarketThis slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Increase audience engagement and knowledge by dispensing information using F1602 Confidential Computing Architecture Implementation Roadmap Confidential Computing Market. This template helps you present information on five stages. You can also present information on Architecture, Implementation, Roadmap using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Cloud Computing Confidential Computing Architecture Implementation Roadmap
Confidential Cloud Computing Confidential Computing Architecture Implementation RoadmapThis slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Increase audience engagement and knowledge by dispensing information using Confidential Cloud Computing Confidential Computing Architecture Implementation Roadmap. This template helps you present information on five stages. You can also present information on Architecture, Implementation, Roadmap using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Architecture And Realms Working Confidential Computing Hardware
Confidential Computing Architecture And Realms Working Confidential Computing HardwareThis slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on. Present the topic in a bit more detail with this Confidential Computing Architecture And Realms Working Confidential Computing Hardware. Use it as a tool for discussion and navigation on Architecture Of Confidential Computing, Working Of Realms, Demonstrate, Operating System, Realm Manager, Hypervisor. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Architecture Based On Azure Services Confidential Computing Hardware
Confidential Computing Architecture Based On Azure Services Confidential Computing HardwareThis slide represents the architecture of confidential computing based on Azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. Present the topic in a bit more detail with this Confidential Computing Architecture Based On Azure Services Confidential Computing Hardware. Use it as a tool for discussion and navigation on Architecture Of Confidential Computing, Azure Confidential Computing Services, Typical Approaches, Sensitive Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Architecture Implementation Roadmap Confidential Computing Hardware
Confidential Computing Architecture Implementation Roadmap Confidential Computing HardwareThis slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Introducing Confidential Computing Architecture Implementation Roadmap Confidential Computing Hardware to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Roadmap, Confidential Computing Architecture, Demonstrate, Deploy Confidential Computing, Cloud Environment, Existing Redis Database Unprotected, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware Ack Tee 2 0 Architecture And Workflow
Confidential Computing Hardware Ack Tee 2 0 Architecture And WorkflowThis slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Ack Tee 2 0 Architecture And Workflow. Dispense information and present a thorough explanation of Architecture Of Container Service, Kubernetes Trusted, Execution Environment Version, Data Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Hardware Inclavare Confidential Containers Architecture In Tee
Confidential Computing Hardware Inclavare Confidential Containers Architecture In TeeThis slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. Introducing Confidential Computing Hardware Inclavare Confidential Containers Architecture In Tee to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Architecture Of Inclavare, Confidential Containers, Tee Environment, Kubernetes Ecosystem, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware Multiparty Privacy Preserving Computation Architecture
Confidential Computing Hardware Multiparty Privacy Preserving Computation ArchitectureThis slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on. Introducing Confidential Computing Hardware Multiparty Privacy Preserving Computation Architecture to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Architecture Design, Multiparty Computing, Confidential Computing, Blockchain With Azure Virtual Machine, Blockchain As A Service, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware Occlum System Architecture And Features
Confidential Computing Hardware Occlum System Architecture And FeaturesThis slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on. Introducing Confidential Computing Hardware Occlum System Architecture And Features to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Trusted Environment, Efficient Multi Process Support, Memory Security Guarantee, using this template. Grab it now to reap its full benefits.
-
 IoT Edge Computing Architecture Layers Comprehensive Guide For IoT Edge IOT SS
IoT Edge Computing Architecture Layers Comprehensive Guide For IoT Edge IOT SSFollowing slide showcases IoT and edge computing architecture that helps to understand working process. It include layers such as IoT device, edge and cloud layers.Deliver an outstanding presentation on the topic using this IoT Edge Computing Architecture Layers Comprehensive Guide For IoT Edge IOT SS. Dispense information and present a thorough explanation of Data Processing, Data Caching Buffering, Sensors Controllers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Consortium Components Of Inclavare Containers Architecture
Confidential Computing Consortium Components Of Inclavare Containers ArchitectureThis slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API. Increase audience engagement and knowledge by dispensing information using Confidential Computing Consortium Components Of Inclavare Containers Architecture. This template helps you present information on eight stages. You can also present information on Inclavare Containers Architecture, Shim Rune, Demonstrate, Handles Container Lifecycle using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Consortium Confidential Computing Architecture And Realms Working
Confidential Computing Consortium Confidential Computing Architecture And Realms WorkingThis slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on. Present the topic in a bit more detail with this Confidential Computing Consortium Confidential Computing Architecture And Realms Working. Use it as a tool for discussion and navigation on Hardware Manufacturers, Simultaneously Running Software On System, Confidential Computing Architecture, Realms Working. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Consortium Inclavare Confidential Containers Architecture In TEE
Confidential Computing Consortium Inclavare Confidential Containers Architecture In TEEThis slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. Present the topic in a bit more detail with this Confidential Computing Consortium Inclavare Confidential Containers Architecture In TEE. Use it as a tool for discussion and navigation on Container Ecosystem, Container Initiative, Enclave Container Architecture, Kubernetes Ecosystem. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Consortium Multiparty Privacy Preserving Computation Architecture Design
Confidential Computing Consortium Multiparty Privacy Preserving Computation Architecture DesignThis slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on. Introducing Confidential Computing Consortium Multiparty Privacy Preserving Computation Architecture Design to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Azure Kubernetes Service, Virtual Machines, Confidential Computing, Hyperledger Fabric, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Consortium Occlum System Architecture And Features
Confidential Computing Consortium Occlum System Architecture And FeaturesThis slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on. Introducing Confidential Computing Consortium Occlum System Architecture And Features to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Trusted Environment, Powerful File Systems, Memory Security Guarantee, Efficient Multi Process Support, using this template. Grab it now to reap its full benefits.
-
 Storage Area Network San Internet Small Computer System Interface Iscsi Architecture And Working
Storage Area Network San Internet Small Computer System Interface Iscsi Architecture And WorkingThis Slide Represents The Architecture And Working Of The Internet Small Computer System Interface Iscsi. The Purpose Of This Slide Is To Showcase The Architecture Of Iscsialong With Its Working. The Architecture Components Include The OSI Model, Iscsiinitiator, And Iscsitarget. Present The Topic In A Bit More Detail With This Storage Area Network San Internet Small Computer System Interface Iscsi Architecture And Working. Use It As A Tool For Discussion And Navigation On Architecture, Information, Virtualization. This Template Is Free To Edit As Deemed Fit For Your Organization. Therefore Download It Now.
-
 Confidential Computing Consortium Ack Tee 2 0 Architecture And Workflow
Confidential Computing Consortium Ack Tee 2 0 Architecture And WorkflowThis slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Present the topic in a bit more detail with this Confidential Computing Consortium Ack Tee 2 0 Architecture And Workflow. Use it as a tool for discussion and navigation on Container Service For Kubernetes, Execution Environment, Demonstrate, Launch And Target Users. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Consortium Budget For Implementing Confidential Computing Architecture
Confidential Computing Consortium Budget For Implementing Confidential Computing ArchitectureThis slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Deliver an outstanding presentation on the topic using this Confidential Computing Consortium Budget For Implementing Confidential Computing Architecture. Dispense information and present a thorough explanation of Budget For Implementing Confidential, Computing Architecture, Hardware And Software Costs using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Consortium Checklist To Implement Confidential Computing Architecture
Confidential Computing Consortium Checklist To Implement Confidential Computing ArchitectureThis slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person. Deliver an outstanding presentation on the topic using this Confidential Computing Consortium Checklist To Implement Confidential Computing Architecture. Dispense information and present a thorough explanation of Cloud Environment, Confidential Computing, Execute Within Confidential Cloud, Redis Database Unprotected using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 K87 Confidential Computing Architecture Based On Azure Services Confidential Computing Consortium
K87 Confidential Computing Architecture Based On Azure Services Confidential Computing ConsortiumThis slide represents the architecture of confidential computing based on Azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. Deliver an outstanding presentation on the topic using this K87 Confidential Computing Architecture Based On Azure Services Confidential Computing Consortium. Dispense information and present a thorough explanation of Sensitive Data Encryption Keys, Sensitive Application Logic, Sensitive Application Logs, Sensitive Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 K88 Confidential Computing Architecture Implementation Roadmap Confidential Computing Consortium
K88 Confidential Computing Architecture Implementation Roadmap Confidential Computing ConsortiumThis slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Introducing K88 Confidential Computing Architecture Implementation Roadmap Confidential Computing Consortium to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Execute Within Confidential Cloud, Execute Existing Redis, Database Unprotected, Breach Data Perimeter, using this template. Grab it now to reap its full benefits.
-
 K89 Confidential Computing Architecture Implementation Timeline Confidential Computing Consortium
K89 Confidential Computing Architecture Implementation Timeline Confidential Computing ConsortiumThis slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Increase audience engagement and knowledge by dispensing information using K89 Confidential Computing Architecture Implementation Timeline Confidential Computing Consortium. This template helps you present information on six stages. You can also present information on Confidential Computing, Architecture Implementation Timeline, Redis Database Unprotected using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Components Of Inclavare Containers Architecture
Confidential Computing Hardware Components Of Inclavare Containers ArchitectureThis slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Components Of Inclavare Containers Architecture. This template helps you present information on eight stages. You can also present information on Inclavare Containers Architecture, Demonstrate, Language Runtime, Handle Container Lifecycle using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Confidential Computing Architecture Implementation Timeline
Confidential Computing Hardware Confidential Computing Architecture Implementation TimelineThis slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Confidential Computing Architecture Implementation Timeline. This template helps you present information on six stages. You can also present information on Implementation Timeline, Confidential Computing Architecture, Deploy Confidential Computing, Cloud Environment, Existing Redis Database Unprotected using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda For Grid Computing Architecture Ppt Icon Example Introduction
Agenda For Grid Computing Architecture Ppt Icon Example IntroductionIntroducing Agenda For Grid Computing Architecture Ppt Icon Example Introduction to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Grid Computing Architecture, Security Model, Grid User Roles, Four Layered Architecture, using this template. Grab it now to reap its full benefits.
-
 Architecture Of Grid Computing Technology Grid Computing Architecture
Architecture Of Grid Computing Technology Grid Computing ArchitectureThis slide represents the architecture of grid computing technology that is used collaborative sharing of resources. It also includes various layers such as application, collective, resource, connectivity, and fabric. Present the topic in a bit more detail with this Architecture Of Grid Computing Technology Grid Computing Architecture. Use it as a tool for discussion and navigation on Protected Network Transactions, Grid Security Infrastructure, General Purpose Components, Generic Architecture For Advanced Reservation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Grid Computing Architecture Application Of Grid Computing In Life Science
Grid Computing Architecture Application Of Grid Computing In Life ScienceThis slide represents the application of grid computing in life science for efficient access, collection, and critical information mining. Grid computing is adopted by various life science disciplines such as computational biology, bioinformatics, genomics, neurology, and so on. Increase audience engagement and knowledge by dispensing information using Grid Computing Architecture Application Of Grid Computing In Life Science. This template helps you present information on six stages. You can also present information on Application Of Grid Computing, Life Science For Efficient Access, Collection And Critical Information Mining, Grid Computing Is Adopted, Computational Biology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Grid Computing Architecture Benefits Of Grid Computing Network
Grid Computing Architecture Benefits Of Grid Computing NetworkThis slide represents the benefits of grid computing, and it includes utilizing underutilized resources, parallel CPU capacity, reliability, management, availability of additional resources, and resource allocation. Introducing Grid Computing Architecture Benefits Of Grid Computing Network to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Reliability, Resource Allocation, Additional Resources, Management, Grid Computing Network, using this template. Grab it now to reap its full benefits.
-
 Grid Computing Architecture Challenges In Grid Computing Technology
Grid Computing Architecture Challenges In Grid Computing TechnologyThis slide represents the challenges in grid computing technology, including scalability, message communication latencies, network communication capacities, input and output bandwidth to storage and other devices, and synchronization protocol. Increase audience engagement and knowledge by dispensing information using Grid Computing Architecture Challenges In Grid Computing Technology. This template helps you present information on five stages. You can also present information on Network Communication Capacities, Message Communication Latencies, Scalability, Synchronization Protocol using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Grid Computing Architecture Characteristics Of Grid Computing Technology
Grid Computing Architecture Characteristics Of Grid Computing TechnologyThis slide depicts the characteristics of grid computing technology, and it includes geographical distribution, heterogeneity and loosely connected, resource sharing, multiple administrations, large scale, resource coordination, and quality of service. Introducing Grid Computing Architecture Characteristics Of Grid Computing Technology to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Multiple Administrations, Geographical Distribution, Resource Sharing, Resource Coordination, Heterogeneity And Loosely Coupled, using this template. Grab it now to reap its full benefits.
-
 Grid Computing Architecture Comparison Between Grid Computing And Cluster Computing
Grid Computing Architecture Comparison Between Grid Computing And Cluster ComputingThis slide outlines the comparison between grid computing and cluster computing based on the type of system, number of tasks, computer location, internet connection, connectivity, scheduling, and resource manager. Deliver an outstanding presentation on the topic using this Grid Computing Architecture Comparison Between Grid Computing And Cluster Computing. Dispense information and present a thorough explanation of Grid Computing, Cluster Computing, Number Of Tasks, Computer Location, Internet Connection, Connectivity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Grid Computing Architecture Difference Between Cloud Computing And Grid Computing
Grid Computing Architecture Difference Between Cloud Computing And Grid ComputingThis slide represents the difference between cloud computing and grid computing based on factors such as architecture design, administrative system, use of resources, flexibility, scalability, and payment options. Increase audience engagement and knowledge by dispensing information using Grid Computing Architecture Difference Between Cloud Computing And Grid Computing. This template helps you present information on one stages. You can also present information on Administrative System, Flexibility, Decentralized Administrative System, Cloud Computing, Grid Computing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Grid Computing Architecture Difference Between Grid Computing And Utility Computing
Grid Computing Architecture Difference Between Grid Computing And Utility ComputingThis slide represents the difference between grid computing and utility computing based on factors such as architecture, working, tasks performed, focus, types of both, and their real-world applications. Present the topic in a bit more detail with this Grid Computing Architecture Difference Between Grid Computing And Utility Computing. Use it as a tool for discussion and navigation on Internal And External Utility, Marketing Research, Services For Computing, Storage And Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Grid Computing Architecture For Table Of Contents Ppt Icon Example Topics
Grid Computing Architecture For Table Of Contents Ppt Icon Example TopicsDeliver an outstanding presentation on the topic using this Grid Computing Architecture For Table Of Contents Ppt Icon Example Topics. Dispense information and present a thorough explanation of Overview Of Grid Computing, Resources In Grid Computing Network, Machines In Grid Computing Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Grid Computing Architecture Grid Computing Four Layered Architecture
Grid Computing Architecture Grid Computing Four Layered ArchitectureThis slide represents the four-layered architecture of grid computing, and four layers include the application layer, grid system software layer, node system software layer, and node and interconnection layer. It also covers the functions of these layers. Present the topic in a bit more detail with this Grid Computing Architecture Grid Computing Four Layered Architecture. Use it as a tool for discussion and navigation on Node System Software Layer, Grid System Software Layer, Application Layer, Grid Service Gateway. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Grid Computing Architecture Grid Computing In Commercial Applications
Grid Computing Architecture Grid Computing In Commercial ApplicationsThis slide outlines the use of grid computing in commercial applications such as online gaming and entertainment. Grid computing allows collaborative play and lowers the overhead investment of hardware and software. Introducing Grid Computing Architecture Grid Computing In Commercial Applications to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Grid Computing, Commercial Applications, Investment Of Hardware And Software, Online Gaming And Entertainment, using this template. Grab it now to reap its full benefits.
-
 Grid Computing Architecture Grid Computing In Data Oriented Applications
Grid Computing Architecture Grid Computing In Data Oriented ApplicationsThis slide depicts the use of grid computing in data-oriented applications, and it is used to collect, store, analyze data and make patterns from that information. DAME is an operational data-oriented program that manages a large amount of in-flight information. Increase audience engagement and knowledge by dispensing information using Grid Computing Architecture Grid Computing In Data Oriented Applications. This template helps you present information on seven stages. You can also present information on Grid Computing, Data Oriented Applications, Operational Data Oriented Program, Analyze Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Grid Computing Architecture Grid Computing In Engineering Oriented Applications
Grid Computing Architecture Grid Computing In Engineering Oriented ApplicationsThis slide talks about using grid computing in engineering-oriented applications, and it drastically reduces the resource-intensive engineering applications cost. NASAs information power grid also implements it. Introducing Grid Computing Architecture Grid Computing In Engineering Oriented Applications to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Grid Computing, Engineering Oriented Applications, Resource Intensive, Engineering Applications Cost, using this template. Grab it now to reap its full benefits.
-
 Grid Computing Architecture Grid Computing In Scientific Research Collaboration
Grid Computing Architecture Grid Computing In Scientific Research CollaborationThis slide represents the application of grid computing in scientific research collaboration, which requires enormous storage space as they generate massive amounts of data regularly. Grid computing enables resource sharing by joining a single virtual organization. Increase audience engagement and knowledge by dispensing information using Grid Computing Architecture Grid Computing In Scientific Research Collaboration. This template helps you present information on six stages. You can also present information on Petabytes Of Data Regularly, Grid Computing, Scientific Research Collaboration, Computer Resources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Grid Computing Architecture Grid Computing Types Collaborative Grid Computing
Grid Computing Architecture Grid Computing Types Collaborative Grid ComputingThis slide represents the collaborative grid computing type that solves the problems through seamless cooperation. It uses numerous technologies to help users collaborate to remove regional barriers and improve the work experience. Introducing Grid Computing Architecture Grid Computing Types Collaborative Grid Computing to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Grid Computing Types, Collaborative Grid Computing, Barriers And Work Experience, Numerous Technologies, using this template. Grab it now to reap its full benefits.
-
 Grid Computing Architecture Grid Computing Types Computational Grid Computing
Grid Computing Architecture Grid Computing Types Computational Grid ComputingThis slide represents the computational type of grid computing that divides the primary task into sub-tasks and merge the outcome of subtasks. It helps organizations to generate business reports faster compared to conventional systems. Deliver an outstanding presentation on the topic using this Grid Computing Architecture Grid Computing Types Computational Grid Computing. Dispense information and present a thorough explanation of Computational Grid Computing, Conventional Systems, Generate Business Reports Faster, Merge The Outcome Of Subtasks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Grid Computing Architecture Grid Computing Types Data Grid Computing
Grid Computing Architecture Grid Computing Types Data Grid ComputingThis slide talks about data grid computing, a kind of grid computing used to share information among multiple computers or nodes. Its benefits include a huge information storage system to store website data, a synchronized approach for data sharing, and so on. Increase audience engagement and knowledge by dispensing information using Grid Computing Architecture Grid Computing Types Data Grid Computing. This template helps you present information on two stages. You can also present information on Transmit Dispersed Data Concurrently, Grids Partition Operations, Numerous Systems, Data Grid Computing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Grid Computing Architecture Grid Computing Types Manuscript Grid Computing
Grid Computing Architecture Grid Computing Types Manuscript Grid ComputingThis slide depicts the manuscript grid computing that is used to handle massive amounts of images, text, and documents concurrently. It enables the regular piling of pictures and text blocks and performing operations on previous block batches. Introducing Grid Computing Architecture Grid Computing Types Manuscript Grid Computing to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Photos Simultaneously, Basic System For Processing Massive, Manuscript Grid Computing, using this template. Grab it now to reap its full benefits.
-
 Grid Computing Architecture Grid Computing Types Modular Grid Computing
Grid Computing Architecture Grid Computing Types Modular Grid ComputingThis slide represents the modular grid computing that separates the computing resources in a system. The computing resources include memory, GPU, networking, and storage, which are then integrated with required assets by IT teams. Increase audience engagement and knowledge by dispensing information using Grid Computing Architecture Grid Computing Types Modular Grid Computing. This template helps you present information on six stages. You can also present information on Central Processing Unit, Modular Grid Computing, Merges A Set Of Resources, Memory And Networking using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.




