Powerpoint Templates and Google slides for Cloud Modeling
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Budget To Implement Secure Access Service Edge Cloud Security Model
Budget To Implement Secure Access Service Edge Cloud Security ModelThis slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD WAN, SWG, ZTNA, CASB, and FWaaS. Present the topic in a bit more detail with this Budget To Implement Secure Access Service Edge Cloud Security Model. Use it as a tool for discussion and navigation on Implement, Network, Secure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Business Benefits Of Firewall As A Service Cloud Security Model
Business Benefits Of Firewall As A Service Cloud Security ModelThis slide illustrates the advantages of firewall as a service to businesses. The purpose of this slide is to demonstrate the business benefits of FWaaS, such as easy maintenance, simple infrastructure, better visibility, easy configuration, scalability and protection of remote workers. Deliver an outstanding presentation on the topic using this Business Benefits Of Firewall As A Service Cloud Security Model. Dispense information and present a thorough explanation of Maintain, Visibility, Configuration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Challenges And Solutions For SASE Implementation Cloud Security Model
Challenges And Solutions For SASE Implementation Cloud Security ModelThis slide represents the challenges and solutions for implementing a secure access service edge in an organization. The purpose of this slide is to showcase the different challenges that a business can face while deploying the SASE model into a business. The key challenges include networking and security team misalignment, change management, etc. Present the topic in a bit more detail with this Challenges And Solutions For SASE Implementation Cloud Security Model. Use it as a tool for discussion and navigation on Solutions, Implementation, Challenges. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Challenges With Traditional Network Security Approaches Cloud Security Model
Challenges With Traditional Network Security Approaches Cloud Security ModelThis slide describes the challenges with traditional network security approaches. The purpose of this slide is to demonstrate the various challenges caused by conventional network security methods while backhauling traffic to data centers, including disjoint management, workload, slower cloud adoption, and so on. Deliver an outstanding presentation on the topic using this Challenges With Traditional Network Security Approaches Cloud Security Model. Dispense information and present a thorough explanation of Approaches, Security, Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Implement Secure Access Service Edge Cloud Security Model
Checklist To Implement Secure Access Service Edge Cloud Security ModelPresent the topic in a bit more detail with this Checklist To Implement Secure Access Service Edge Cloud Security Model. Use it as a tool for discussion and navigation on Service, Access, Secure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB Overview Cloud Security Model
Cloud Access Security Broker CASB Overview Cloud Security ModelThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Introducing Cloud Access Security Broker CASB Overview Cloud Security Model to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Visibility, Prevention, Management, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker Implementation Models Cloud Security Model
Cloud Access Security Broker Implementation Models Cloud Security ModelThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out of band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Implementation Models Cloud Security Model. This template helps you present information on three stages. You can also present information on Scanning, Forward, Reverse using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Use Cases Cloud Security Model
Cloud Access Security Broker Use Cases Cloud Security ModelThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker Use Cases Cloud Security Model. Dispense information and present a thorough explanation of Protection, Govern, Secure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Working Process Cloud Security Model
Cloud Access Security Broker Working Process Cloud Security ModelThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Working Process Cloud Security Model. This template helps you present information on three stages. You can also present information on Discovery, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Model Table Of Contents Ppt Demonstration
Cloud Security Model Table Of Contents Ppt DemonstrationIntroducing Cloud Security Model Table Of Contents Ppt Demonstration to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Secure, Architecture, Network, using this template. Grab it now to reap its full benefits.
-
 Comparative Analysis For Corporate Network Efficacy Cloud Security Model
Comparative Analysis For Corporate Network Efficacy Cloud Security ModelThis slide depicts the comparison between SASE and other approaches for corporate network efficacy. The purpose of this slide is to demonstrate the various network security approaches and their comparison based on latency, management, app prioritization, and unified provisioning. Increase audience engagement and knowledge by dispensing information using Comparative Analysis For Corporate Network Efficacy Cloud Security Model. This template helps you present information on five stages. You can also present information on Security, Backhauls, Web using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comparison Between Secure Access Service Edge And SD WAN Cloud Security Model
Comparison Between Secure Access Service Edge And SD WAN Cloud Security ModelThis slide compares secure access service edge and software defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access. Present the topic in a bit more detail with this Comparison Between Secure Access Service Edge And SD WAN Cloud Security Model. Use it as a tool for discussion and navigation on Deployment, Architecture, Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall As A Service FWaaS Overview And Importance Cloud Security Model
Firewall As A Service FWaaS Overview And Importance Cloud Security ModelThis slide represents the overview and importance of firewall as a service. The purpose of this slide is to demonstrate the overview of cloud firewall, including its importance, services offered and top vendors such as Fortinet, Zscaler, Cisco, CheckPoint and so on. Increase audience engagement and knowledge by dispensing information using Firewall As A Service FWaaS Overview And Importance Cloud Security Model. This template helps you present information on two stages. You can also present information on Businesses, Providers, Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall As A Service FWaaS Working And Security Features Cloud Security Model
Firewall As A Service FWaaS Working And Security Features Cloud Security ModelThis slide describes the working and security features of the firewall as a service. The purpose of this slide is to demonstrate the working of the firewall as a service, including its security features such as packet filtering, network monitoring, IPsec, SSL VPN support, DPI, and IP mapping. Introducing Firewall As A Service FWaaS Working And Security Features Cloud Security Model to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Packet, Internet, Network, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Cloud Security Model Ppt Background
Icons Slide For Cloud Security Model Ppt BackgroundIntroducing our well researched set of slides titled Icons Slide For Cloud Security Model Ppt Background. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Importance Of Software Defined Wide Area Network Cloud Security Model
Importance Of Software Defined Wide Area Network Cloud Security ModelThis slide talks about the need for SD WAN by comparing traditional WAN with SD WAN. The purpose of this slide is to demonstrate IT problems experienced with traditional wide area network and how SD WAN can address those problems. Present the topic in a bit more detail with this Importance Of Software Defined Wide Area Network Cloud Security Model. Use it as a tool for discussion and navigation on Problems, Solutions, Complexity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Introduction To Secure Access Service Edge SASE Cloud Security Model
Introduction To Secure Access Service Edge SASE Cloud Security ModelThis slide represents the introduction of SASE cloud security technology. The purpose of this slide is to demonstrate the core capabilities, benefits and key components of SASE. The key components include SD WAN, FWaaS, ZTNA, CASB, SWG, and unified management. Introducing Introduction To Secure Access Service Edge SASE Cloud Security Model to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Secure, Access, Service, using this template. Grab it now to reap its full benefits.
-
 Key Drivers For SASE Adoption Cloud Security Model
Key Drivers For SASE Adoption Cloud Security ModelThis slide outlines the critical drivers for secure access service edge adoption. This slide aims to demonstrate the key drivers that boost SASE adoption among different organizations, including cloud adoption, increased flexibility and agility, cost effective network traffic management, etc. Increase audience engagement and knowledge by dispensing information using Key Drivers For SASE Adoption Cloud Security Model. This template helps you present information on five stages. You can also present information on Adoption, Flexibility, Growth using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Pillars Of Cloud Access Security Broker Cloud Security Model
Pillars Of Cloud Access Security Broker Cloud Security ModelThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Introducing Pillars Of Cloud Access Security Broker Cloud Security Model to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Compliance, Visibility, Security, using this template. Grab it now to reap its full benefits.
-
 Roadmap To Implement Secure Access Service Edge Cloud Security Model
Roadmap To Implement Secure Access Service Edge Cloud Security ModelThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Increase audience engagement and knowledge by dispensing information using Roadmap To Implement Secure Access Service Edge Cloud Security Model. This template helps you present information on seven stages. You can also present information on Objectives, Discover, Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
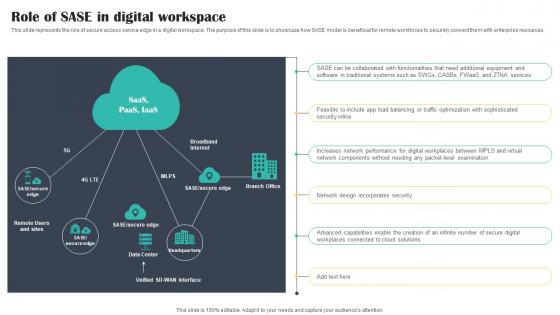 Role Of SASE In Digital Workspace Cloud Security Model
Role Of SASE In Digital Workspace Cloud Security ModelThis slide represents the role of secure access service edge in a digital workspace. The purpose of this slide is to showcase how SASE model is beneficial for remote workforces to securely connect them with enterprise resources. Introducing Role Of SASE In Digital Workspace Cloud Security Model to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Software, Optimization, Examination, using this template. Grab it now to reap its full benefits.
-
 SASE Identity Centric Architecture Overview Cloud Security Model
SASE Identity Centric Architecture Overview Cloud Security ModelThis slide outlines the overview of the centric architecture of the secure access service edge. The purpose of this slide is to demonstrate the various services executed by SASE architecture and components involved in this, such as enterprise data center, internet, internet edge, distributed edge, etc. Deliver an outstanding presentation on the topic using this SASE Identity Centric Architecture Overview Cloud Security Model. Dispense information and present a thorough explanation of Identity, Architecture, Overview using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE Vs SD WAN Vs SWGs Vs UTM Cloud Security Model
SASE Vs SD WAN Vs SWGs Vs UTM Cloud Security ModelThis slide demonstrates the difference between secure access service edge, software defined wide area network, secure web gateways, and unified threat management. The comparison is based on global connectivity, simplified management, optimized cloud access, multi layered protection, etc. Present the topic in a bit more detail with this SASE Vs SD WAN Vs SWGs Vs UTM Cloud Security Model. Use it as a tool for discussion and navigation on Management, Protection, Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Access Service Edge Architecture Characteristics Cloud Security Model
Secure Access Service Edge Architecture Characteristics Cloud Security ModelThis slide represents the architectural characteristics of a secure access service edge. The purpose of this slide is to showcase the features of SASE architecture that include identity driven, cloud native, support for all edges, and global distribution. Increase audience engagement and knowledge by dispensing information using Secure Access Service Edge Architecture Characteristics Cloud Security Model. This template helps you present information on four stages. You can also present information on Identity, Native, Support using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Access Service Edge Implementation Steps Cloud Security Model
Secure Access Service Edge Implementation Steps Cloud Security ModelThis slide outlines the steps to implement a secure service edge in a business. The purpose of this slide is to demonstrate the various guidelines to consider while implementing the SASE model in an organization. The main steps include defining SASE goals and requirements, selecting the SD WAN backbone, incorporating zero trust solutions, etc. Introducing Secure Access Service Edge Implementation Steps Cloud Security Model to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Requirements, Solutions, Optimize, using this template. Grab it now to reap its full benefits.
-
 Secure Access Service Edge Importance Cloud Security Model
Secure Access Service Edge Importance Cloud Security ModelThis slide represents the importance of secure access service edge. This slides purpose is to demonstrate why businesses need the SASE model. The main reasons include scaling with business needs, encouraging work from anywhere environment, standing up for cyber threats, and offering a base for IoT adoption. Increase audience engagement and knowledge by dispensing information using Secure Access Service Edge Importance Cloud Security Model. This template helps you present information on four stages. You can also present information on Scales, Encourage, Evolution using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Access Service Edge SASE Architecture Cloud Security Model
Secure Access Service Edge SASE Architecture Cloud Security ModelThis slide represents the SASE architecture overview and its goals. The purpose of this slide is to demonstrate the secure access service edge architecture and its goals. The building blocks of SASE architecture include SWG, CASB, ZTNA, FWaaS, SD WAN, Thin Edge, and so on. Present the topic in a bit more detail with this Secure Access Service Edge SASE Architecture Cloud Security Model. Use it as a tool for discussion and navigation on Service, Secure, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Access Service Edge Training Program Cloud Security Model
Secure Access Service Edge Training Program Cloud Security ModelThis slide represents the training program for the secure access service edge model. The purpose of this slide is to demonstrate the teams eligible for training, the modules to be covered during the training, the schedule and venue of the training. Deliver an outstanding presentation on the topic using this Secure Access Service Edge Training Program Cloud Security Model. Dispense information and present a thorough explanation of Access, Service, Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Access Service Edge Use Cases Cloud Security Model
Secure Access Service Edge Use Cases Cloud Security ModelThis slide represents the use cases of secure access service edge within an organization. The purpose of this slide is to demonstrate the various use cases of the SASE model, including rapid response to network demand, support for IoT and edge computing, VPN replacement, performance assurance and so on. Increase audience engagement and knowledge by dispensing information using Secure Access Service Edge Use Cases Cloud Security Model. This template helps you present information on six stages. You can also present information on Demand, Computing, Replacement using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Web Gateway SWG Functional Components Cloud Security Model
Secure Web Gateway SWG Functional Components Cloud Security ModelThis slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. Present the topic in a bit more detail with this Secure Web Gateway SWG Functional Components Cloud Security Model. Use it as a tool for discussion and navigation on Components, Prevention, Inspection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Web Gateway SWG Importance For Businesses Cloud Security Model
Secure Web Gateway SWG Importance For Businesses Cloud Security ModelThis slide outlines the importance of secure web gateways to businesses. The purpose of this slide is to demonstrate the need for SWGs for companies to protect their critical data and applications from malicious activities and actors. Increase audience engagement and knowledge by dispensing information using Secure Web Gateway SWG Importance For Businesses Cloud Security Model. This template helps you present information on six stages. You can also present information on Protecting, Corporations, Technologies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Web Gateway SWG Introduction And Features Cloud Security Model
Secure Web Gateway SWG Introduction And Features Cloud Security ModelThis slide describes the overview and features of the secure gateway. The purpose of this slide is to demonstrate the SWG and its benefits to businesses. The features include URL filtering, application control, data loss prevention, antivirus, and HTTPS inspection. Introducing Secure Web Gateway SWG Introduction And Features Cloud Security Model to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Problematic, Security, Protect, using this template. Grab it now to reap its full benefits.
-
 Secure Web Gateways SWG Setup And Working Cloud Security Model
Secure Web Gateways SWG Setup And Working Cloud Security ModelThis slide depicts the methods to setup the secure web gateways and their working. The purpose of this slide is to demonstrate the various ways in which organizations can install the SWGs. It also caters to the working and functions performed by SWGs to protect data and safe browsing on the internet. Increase audience engagement and knowledge by dispensing information using Secure Web Gateways SWG Setup And Working Cloud Security Model. This template helps you present information on eight stages. You can also present information on Implemented, Classifications, Programs using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Software Defined Wide Area Network SD WAN Introduction Cloud Security Model
Software Defined Wide Area Network SD WAN Introduction Cloud Security ModelThis slide represents the overview of SD WAN components of secure access service access. The purpose of this slide is to showcase the introduction and service components of SD WAN, including edge, orchestrator, and controller. Introducing Software Defined Wide Area Network SD WAN Introduction Cloud Security Model to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Network, Platform, Supervises, using this template. Grab it now to reap its full benefits.
-
 Timeline To Implement Cloud Access Security Broker Cloud Security Model
Timeline To Implement Cloud Access Security Broker Cloud Security ModelThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing Timeline To Implement Cloud Access Security Broker Cloud Security Model to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Activity, Identify, Removal, using this template. Grab it now to reap its full benefits.
-
 Timeline To Implement Secure Access Service Edge Cloud Security Model
Timeline To Implement Secure Access Service Edge Cloud Security ModelThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Increase audience engagement and knowledge by dispensing information using Timeline To Implement Secure Access Service Edge Cloud Security Model. This template helps you present information on seven stages. You can also present information on Objectives, Solutions, Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Traditional Networking Security Problems And SASE Solutions Cloud Security Model
Traditional Networking Security Problems And SASE Solutions Cloud Security ModelThis slide describes the traditional networking security problems and how SASE model can overcome those problems. The main problems include, remote access to on-premises resources, access to cloud resources, network access controls etc. Deliver an outstanding presentation on the topic using this Traditional Networking Security Problems And SASE Solutions Cloud Security Model. Dispense information and present a thorough explanation of Networking, Model, Solutions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Types Of Zero Trust Network Access ZTNA Models Cloud Security Model
Types Of Zero Trust Network Access ZTNA Models Cloud Security ModelThis slide describes the various types of zero trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Increase audience engagement and knowledge by dispensing information using Types Of Zero Trust Network Access ZTNA Models Cloud Security Model. This template helps you present information on three stages. You can also present information on Change, Technologies, Knowledge using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Working Of Secure Access Service Edge Cloud Security Model
Working Of Secure Access Service Edge Cloud Security ModelThis slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. Present the topic in a bit more detail with this Working Of Secure Access Service Edge Cloud Security Model. Use it as a tool for discussion and navigation on Network, Security, Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Of Zero Trust Network Access Cloud Security Model
Working Of Zero Trust Network Access Cloud Security ModelThis slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Deliver an outstanding presentation on the topic using this Working Of Zero Trust Network Access Cloud Security Model. Dispense information and present a thorough explanation of Working, Network, Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Zero Trust Network Access Vs Virtual Private Network Cloud Security Model
Zero Trust Network Access Vs Virtual Private Network Cloud Security ModelThis slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application level access. Present the topic in a bit more detail with this Zero Trust Network Access Vs Virtual Private Network Cloud Security Model. Use it as a tool for discussion and navigation on Workforce, Network, Private. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Zero Trust Network Access ZTNA Introduction Cloud Security Model
Zero Trust Network Access ZTNA Introduction Cloud Security ModelThis slide represents the overview of zero trust network access, including its architecture. The purpose of this slide is to demonstrate the overview and use cases of ZTNA. The primary use cases include authentication and access control and holistic control and visibility. Deliver an outstanding presentation on the topic using this Zero Trust Network Access ZTNA Introduction Cloud Security Model. Dispense information and present a thorough explanation of Network, Access, Introduction using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 ZTNA 1 0 Vs ZTNA 2 0 Cloud Security Model Ppt Pictures
ZTNA 1 0 Vs ZTNA 2 0 Cloud Security Model Ppt PicturesThis slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero trust network access. Present the topic in a bit more detail with this ZTNA 1 0 Vs ZTNA 2 0 Cloud Security Model Ppt Pictures. Use it as a tool for discussion and navigation on Remote, Secures, Regulations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Aws Amplify Web Services Pricing Model Comprehensive Guide To Mobile Cloud Computing
Aws Amplify Web Services Pricing Model Comprehensive Guide To Mobile Cloud ComputingThe purpose of the mentioned slide is to showcase Amazon web services pricing models. It includes Free Tier, Pay-as-you-go, resource-based pricing, amplify console pricing, and additional services Increase audience engagement and knowledge by dispensing information using Aws Amplify Web Services Pricing Model Comprehensive Guide To Mobile Cloud Computing. This template helps you present information on five stages. You can also present information on Resource Based Pricing, Amplify Console Pricing, Additional Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mobile Cloud As Service Model Vendors Comprehensive Guide To Mobile Cloud Computing
Mobile Cloud As Service Model Vendors Comprehensive Guide To Mobile Cloud ComputingThe purpose of the mentioned slide is to showcase various vendors outsourcing mobile PaaS services. It includes Appcelerator Axway, QuickBase, Kinvey Progress, Kony AppPlatform, etc. Increase audience engagement and knowledge by dispensing information using Mobile Cloud As Service Model Vendors Comprehensive Guide To Mobile Cloud Computing. This template helps you present information on five stages. You can also present information on Appcelerator, Service, Development using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mobile Service Models Comprehensive Guide To Mobile Cloud Computing
Mobile Service Models Comprehensive Guide To Mobile Cloud ComputingThe purpose of the mentioned slide is to showcase the various service models of cloud computing that enhance and streamlines the whole process. It includes IaaS, PaaS, and SaaS Increase audience engagement and knowledge by dispensing information using Mobile Service Models Comprehensive Guide To Mobile Cloud Computing. This template helps you present information on three stages. You can also present information on Infrastructure As Service, Platform As Service, Software As Service using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mobile Working Architecture Model Comprehensive Guide To Mobile Cloud Computing
Mobile Working Architecture Model Comprehensive Guide To Mobile Cloud ComputingThe given slide outlines the various components of cloud computing architecture that enforce the seamless working of the whole process. It includes Mobile network and B, mobile devices, and cloud and B. Deliver an outstanding presentation on the topic using this Mobile Working Architecture Model Comprehensive Guide To Mobile Cloud Computing. Dispense information and present a thorough explanation of Architecture, Environment, Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Platform As Service Paas Model Overview Comprehensive Guide To Mobile Cloud Computing
Platform As Service Paas Model Overview Comprehensive Guide To Mobile Cloud ComputingThis slide represents the platform as service that provides runtime environment to developers, and cloud service providers manage the back-end environment. It also includes key takeaways for PaaS model Present the topic in a bit more detail with this Platform As Service Paas Model Overview Comprehensive Guide To Mobile Cloud Computing. Use it as a tool for discussion and navigation on Overview, Environment, Infrastructure Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
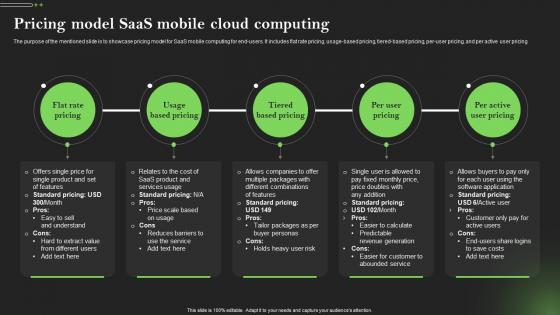 Pricing Model Saas Mobile Cloud Computing Comprehensive Guide To Mobile Cloud Computing
Pricing Model Saas Mobile Cloud Computing Comprehensive Guide To Mobile Cloud ComputingThe purpose of the mentioned slide is to showcase pricing model for SaaS mobile computing for end-users. It includes flat rate pricing, usage-based pricing, tiered-based pricing, per-user pricing, and per active user pricing Introducing Pricing Model Saas Mobile Cloud Computing Comprehensive Guide To Mobile Cloud Computing to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Flat Rate Pricing, Usage Based Pricing, Tiered Based Pricing, using this template. Grab it now to reap its full benefits.
-
 Various Types Of Paas Model In Mobile Computing Comprehensive Guide To Mobile Cloud Computing
Various Types Of Paas Model In Mobile Computing Comprehensive Guide To Mobile Cloud ComputingThis slide shows the various types of PaaS models in mobile cloud computing. It includes public PaaS, private PaaS, hybrid PaaS, communication PaaS, mobile PaaS, and OpenPaaS. Increase audience engagement and knowledge by dispensing information using Various Types Of Paas Model In Mobile Computing Comprehensive Guide To Mobile Cloud Computing. This template helps you present information on six stages. You can also present information on Communications Paas, Infrastructure, Organizations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Business Model Cloud Platform Investment Ask Pitch Deck
Business Model Cloud Platform Investment Ask Pitch DeckFollowing slide covers operational business model of company cloud based software. It include models such as software as a service and marketplace model. Introducing Business Model Cloud Platform Investment Ask Pitch Deck to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Business Model, using this template. Grab it now to reap its full benefits.
-
 Sase Security Cloud Security Broker Implementation Models Ppt Show Graphics Tutorials
Sase Security Cloud Security Broker Implementation Models Ppt Show Graphics TutorialsThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Present the topic in a bit more detail with this Sase Security Cloud Security Broker Implementation Models Ppt Show Graphics Tutorials. Use it as a tool for discussion and navigation on Implementation, Technique, Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Security Broker Implementation Models Secure Access Service Edge Sase
Cloud Security Broker Implementation Models Secure Access Service Edge SaseThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using Cloud Security Broker Implementation Models Secure Access Service Edge Sase. This template helps you present information on three stages. You can also present information on Implementation, Applications, Inline Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Dropbox Platform Support Model Dropbox Saas Cloud Platform CL SS
Dropbox Platform Support Model Dropbox Saas Cloud Platform CL SSThis slide showcases platform support model of dropbox. This further includes dropbox transfer, capture, replay, passwords, shop and backup. Increase audience engagement and knowledge by dispensing information using Dropbox Platform Support Model Dropbox Saas Cloud Platform CL SS. This template helps you present information on three stages. You can also present information on Live Chat, Email, Community, Dropbox Platform using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Implementation Models SASE Network Security
Cloud Access Security Broker Implementation Models SASE Network SecurityThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out of band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing Cloud Access Security Broker Implementation Models SASE Network Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Scanning, Forward, Reverse, using this template. Grab it now to reap its full benefits.
-
 Amazon Web Services Cloud Transformation Maturity Model
Amazon Web Services Cloud Transformation Maturity ModelThis slide shows AWS cloud transformation maturity model that can be adapted for any cloud. The purpose of this slide is to assess cloud adoption maturity through four execution stages such as project, structuring, migration and efficiency. Introducing our Amazon Web Services Cloud Transformation Maturity Model set of slides. The topics discussed in these slides are Project, Structuring, Migration . This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Digital Transformation Using SaaS And Cloud Computing Models
Digital Transformation Using SaaS And Cloud Computing ModelsThis slide shows acceleration of digital transformation process using SaaS and cloud computing models. The purpose of this slide is to help businesses to lower data storage costs and streamlining cloud based SaaS application operations. It covers various reasons of using SaaS and cloud computing together such as easy accessibility, improved data security, efficient workflow, etc. Presenting our set of slides with Digital Transformation Using SaaS And Cloud Computing Models. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Security, Accessibility, Cost Optimization.
-
 Virtual Infrastructure Management Model In Hybrid And Private Clouds
Virtual Infrastructure Management Model In Hybrid And Private CloudsThis slide represents model for virtual infrastructure in hybrid and private cloud ecosystem development to enhance business control over virtualized resources. It includes various components such as cloud interface, VM manager, PaaS, etc. Presenting our well structured Virtual Infrastructure Management Model In Hybrid And Private Clouds. The topics discussed in this slide are Individual Users, Eucalyptus, Globus Nimbus. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Infrastructure As Code Iac Main Cloud Governance Models And Standards
Infrastructure As Code Iac Main Cloud Governance Models And StandardsThis slide represents the cloud governance models and standards of Infrastructure as Code. The purpose of this slide is to highlight the models such as COBIT, itilinformation technology Infrastructure library, ISO or IEC, etc. Introducing Infrastructure As Code Iac Main Cloud Governance Models And Standards to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Technology Infrastructure Library, Cloud Governance Models, Technological Projects, using this template. Grab it now to reap its full benefits.
-
 K122 Cloud Computing Models That Can Incorporate Serverless Computing V2 Multi Cloud
K122 Cloud Computing Models That Can Incorporate Serverless Computing V2 Multi CloudThis slide discusses the integration of serverless computing technology with multi-cloud computing model. The purpose of this slide is to represent the K122 cloud computing model which can incorporate serverless computing in their system architecture. Increase audience engagement and knowledge by dispensing information using Cloud Computing Models That Can Incorporate Serverless Computing V2 Multi Cloud. This template helps you present information on three stages. You can also present information on Independent Workloads, Cloud Computing Models, Incorporate Serverless Computing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





