Powerpoint Templates and Google slides for Cloud Computing And Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 F1604 Confidential Computing Market Driven By Cloud And Security Confidential Computing Market
F1604 Confidential Computing Market Driven By Cloud And Security Confidential Computing MarketThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Present the topic in a bit more detail with this F1604 Confidential Computing Market Driven By Cloud And Security Confidential Computing Market. Use it as a tool for discussion and navigation on Enterprise, Awareness, Confidential. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Market Driven By Cloud And Security Confidential Computing Hardware
Confidential Computing Market Driven By Cloud And Security Confidential Computing HardwareThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Deliver an outstanding presentation on the topic using this Confidential Computing Market Driven By Cloud And Security Confidential Computing Hardware. Dispense information and present a thorough explanation of Confidential Computing, Market Driven By Cloud, Security Initiatives, Awareness About Confidential Computing, Demand For Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Consortium Confidential Computing Market Driven By Cloud And Security
Confidential Computing Consortium Confidential Computing Market Driven By Cloud And SecurityThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Present the topic in a bit more detail with this Confidential Computing Consortium Confidential Computing Market Driven By Cloud And Security. Use it as a tool for discussion and navigation on Confidential Computing, Market Driven By Cloud, Security Initiatives, Security Specific Use Cases. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Driven By Cloud And Security Initiatives Confidential Computing System Technology
Confidential Driven By Cloud And Security Initiatives Confidential Computing System TechnologyThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Deliver an outstanding presentation on the topic using this Confidential Driven By Cloud And Security Initiatives Confidential Computing System Technology. Dispense information and present a thorough explanation of Confidential, Enterprise, Awareness using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing V2 Market Driven By Cloud And Security Initiatives
Confidential Computing V2 Market Driven By Cloud And Security InitiativesThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Deliver an outstanding presentation on the topic using this Confidential Computing V2 Market Driven By Cloud And Security Initiatives. Dispense information and present a thorough explanation of Confidential Computing Market, Cloud And Security Initiatives, Total Addressable Market using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Adopting Homomorphic Encryption To Secure Cloud Computing Implementing Digital Transformation And Ai DT SS
Adopting Homomorphic Encryption To Secure Cloud Computing Implementing Digital Transformation And Ai DT SSThis slide provides glimpse about utilizing homomorphic encryption approach that can help businesses in privacy preservation. It includes stages such as encryption, computation, decryption, etc. Increase audience engagement and knowledge by dispensing information using Adopting Homomorphic Encryption To Secure Cloud Computing Implementing Digital Transformation And Ai DT SS. This template helps you present information on three stages. You can also present information on Privacy Preservation, Secure Cloud Computing, Model Owner using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
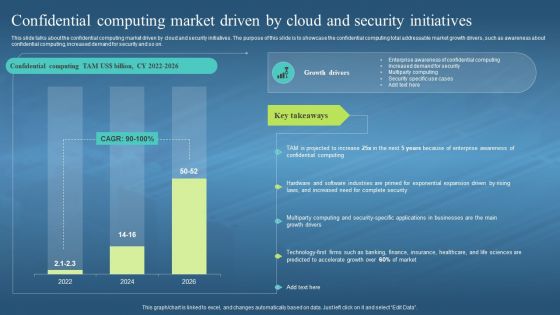
 Confidential Computing Market Driven By Cloud And Security Initiatives Ppt Slides Summary
Confidential Computing Market Driven By Cloud And Security Initiatives Ppt Slides SummaryThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Deliver an outstanding presentation on the topic using this Confidential Computing Market Driven By Cloud And Security Initiatives Ppt Slides Summary. Dispense information and present a thorough explanation of Confidential Computing TAM, Growth Drivers, Key Takeaways using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Computing Security Difference Between Cloud Security Solutions And Traditional IT Solutions
Cloud Computing Security Difference Between Cloud Security Solutions And Traditional IT SolutionsThis slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security Difference Between Cloud Security Solutions And Traditional IT Solutions. This template helps you present information on two stages. You can also present information on Cloud Security, Traditional It Security, Low Efficiency using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Computing Security How Does Cloud Security Work Data Retention And Business
Cloud Computing Security How Does Cloud Security Work Data Retention And BusinessThis slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security How Does Cloud Security Work Data Retention And Business. This template helps you present information on four stages. You can also present information on Impact Analysis, Recovery Strategies, Testing And Maintenance, Plan Development using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Computing Security How Does Cloud Security Work Identity And Access Management
Cloud Computing Security How Does Cloud Security Work Identity And Access ManagementThis slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Introducing Cloud Computing Security How Does Cloud Security Work Identity And Access Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Authorization, Access Management, Central User Repository, using this template. Grab it now to reap its full benefits.
-
 Cloud Computing Security Measures And Controls In Cloud Security
Cloud Computing Security Measures And Controls In Cloud SecurityThis slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls. Introducing Cloud Computing Security Measures And Controls In Cloud Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Preventive Control, Corrective Control, Detective Control, Deterrent Control, Cloud Security, using this template. Grab it now to reap its full benefits.
-
 Cloud Computing Security Phase1 Understand Cloud Utilization And Risk
Cloud Computing Security Phase1 Understand Cloud Utilization And RiskThis slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of. Present the topic in a bit more detail with this Cloud Computing Security Phase1 Understand Cloud Utilization And Risk. Use it as a tool for discussion and navigation on Recognize Critical Data, User Activities, Risk Assessment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Security Checklist Backup And Data Recovery Cloud Computing Security
Cloud Security Checklist Backup And Data Recovery Cloud Computing SecurityThis slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them. Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Backup And Data Recovery Cloud Computing Security. This template helps you present information on three stages. You can also present information on Cyber Attacks, Physical Location, Backup And Recovery Plans using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Checklist Logging And Monitoring Cloud Computing Security
Cloud Security Checklist Logging And Monitoring Cloud Computing SecurityThis slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Logging And Monitoring Cloud Computing Security. This template helps you present information on five stages. You can also present information on Future Evaluation, Organization, Policy Change Activities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Checklist Policies And Procedures Cloud Computing Security
Cloud Security Checklist Policies And Procedures Cloud Computing SecurityThis slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization. Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Policies And Procedures Cloud Computing Security. This template helps you present information on five stages. You can also present information on Organization, Cloud Security, Security Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Checklist Security Patches And Updates Cloud Computing Security
Cloud Security Checklist Security Patches And Updates Cloud Computing SecurityThis slide depicts the importance of security patches and timely updates of security technologies. It also shows how it is crucial to scan systems, servers, and frameworks regularly. Introducing Cloud Security Checklist Security Patches And Updates Cloud Computing Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Organization, Advanced Security Tools, Security Measures, using this template. Grab it now to reap its full benefits.
-
 Pillars Of Cloud Security Visibility And Consistency Cloud Computing Security
Pillars Of Cloud Security Visibility And Consistency Cloud Computing SecurityThis slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security. Introducing Pillars Of Cloud Security Visibility And Consistency Cloud Computing Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Asset Inventory, Cloud Framework, Data Security, using this template. Grab it now to reap its full benefits.
-
 Cloud Computing Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Computing Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Cloud computing security colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Cloud Computing Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Computing Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Cloud computing security monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
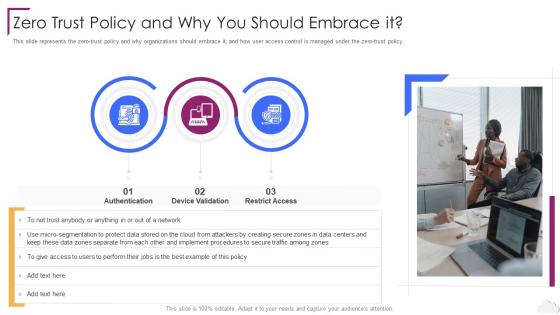 Cloud Computing Security Zero Trust Policy And Why You Should Embrace It
Cloud Computing Security Zero Trust Policy And Why You Should Embrace ItThis slide represents the zero trust policy and why organizations should embrace it, and how user access control is managed under the zero trust policy. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security Zero Trust Policy And Why You Should Embrace It. This template helps you present information on three stages. You can also present information on Authentication, Device Validation, Restrict Access using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Computing Security And Privacy Icon
Cloud Computing Security And Privacy IconPresenting our set of slides with name Cloud Computing Security And Privacy Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Computing, Security And Privacy Icon.
-
 Cloud Architecture And Security Multi Cloud Computing Stack For Applications Need A Highly Scalable
Cloud Architecture And Security Multi Cloud Computing Stack For Applications Need A Highly ScalableThis slide covers the reasons to choose SaaS infrastructure when business grows as all applications would need a highly scalable platform. Present the topic in a bit more detail with this Cloud Architecture And Security Multi Cloud Computing Stack For Applications Need A Highly Scalable. Use it as a tool for discussion and navigation on Multi Cloud, Computing Stack, Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1541 Confidential Computing Market Driven By Cloud And Security Initiatives Confidential Cloud Computing
F1541 Confidential Computing Market Driven By Cloud And Security Initiatives Confidential Cloud ComputingThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Deliver an outstanding presentation on the topic using this F1541 Confidential Computing Market Driven By Cloud And Security Initiatives Confidential Cloud Computing. Dispense information and present a thorough explanation of Initiatives, Confidential, Computing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Computing Security Architecture And Boundaries
Cloud Computing Security Architecture And BoundariesThe slide presents an architecture describing technologies and hardware to protect data and systems within cloud platforms . The slide includes security boundaries and key takeaways. Introducing our Cloud Computing Security Architecture And Boundaries set of slides. The topics discussed in these slides are Presentation Mobility, Presentation Platform, Boundaries This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Computing Security Threats And Solutions
Cloud Computing Security Threats And SolutionsThe slide showcases threats occurred due to data flowing between cloud service providers and organizations with their solutions. It includes lack of cloud security architecture and tactics, account hijacking , weak control plane , inadequate of identity, credentials, etc. Presenting our well structured Cloud Computing Security Threats And Solutions. The topics discussed in this slide are Account Hijacking, Weak Control Plane, Threats This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cloud Computing Security Tools And Package
Cloud Computing Security Tools And PackageThe slide represents tools encapsulated in cloud computing security software. The elements include computing tools, software such as SaaS, PaaS, IaaS and pricing package. Introducing our Cloud Computing Security Tools And Package set of slides. The topics discussed in these slides are Cloud, Computing, Tools This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Analysis Of Cybersecurity And Cloud Computing Security
Comparative Analysis Of Cybersecurity And Cloud Computing SecurityThe purpose of the slide is to showcase the significant differences between cyber security and cloud security. It provides a comparative matrix with differentiating aspects like definition, maintenance of personal information security, liability of security breach, access to data and security threat detection. Presenting our well structured Comparative Analysis Of Cybersecurity And Cloud Computing Security. The topics discussed in this slide are Aspects, Cloud Security, Cyber Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security And Cloud Computing Icon
Cyber Security And Cloud Computing IconPresenting our set of slides with Cyber Security And Cloud Computing Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security, Cloud Computing, Icon.
-
 Ways Cloud Computing Strengthening Industrial Cyber Security And Productivity
Ways Cloud Computing Strengthening Industrial Cyber Security And ProductivityThe slide showcases the benefits associated with cloud computing at global industrial level. it shows how cloud computing is enhancing global industries productivity and cyber security and dealing with financial barriers. Introducing our premium set of slides with Ways Cloud Computing Strengthening Industrial Cyber Security And Productivity. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cloud Computing, Booting Industrial Production, Cloud Computing Industrial, Cyber Security. So download instantly and tailor it with your information.
-
 Cloud computing security dimensions and categories
Cloud computing security dimensions and categoriesPresenting this set of slides with name Cloud Computing Security Dimensions And Categories. This is a three stage process. The stages in this process are Security Domains, Security Risks, Security Threats. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Secure cloud interfaces and apis cloud computing standard architecture patterns ppt presentation diagram
Secure cloud interfaces and apis cloud computing standard architecture patterns ppt presentation diagramHere is a slide titled Secure Cloud Interfaces And APIs Cloud Computing Standard Architecture Patterns Ppt Presentation Diagram. Describe cloud computing patterns and their applications using this contemporary presentation template available in standard and widescreen sizes. Topics such as Relying Parties, Attackers, Authentication Gateway Service can be discussed with the help of this PowerPoint theme. Hit the download button and instantly elevate your presentation with our customizable PPT template.



