Powerpoint Templates and Google slides for Cloud Access Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cloud Access Security Broker CASB V2 Powerpoint Presentation Slides
Cloud Access Security Broker CASB V2 Powerpoint Presentation SlidesEnthrall your audience with this Cloud Access Security Broker CASB V2 Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising eighty seven slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Cloud Access Security Broker CASB Powerpoint Presentation Slides
Cloud Access Security Broker CASB Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Cloud Access Security Broker CASB Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the eighty seven slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Cloud Access Security Brokers As An Element Of Network Security Training Ppt
Cloud Access Security Brokers As An Element Of Network Security Training PptPresenting Cloud Access Security Brokers as an Element of Network Security. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Cloud Security Icon Security Computing Data Protection Digital Access
Cloud Security Icon Security Computing Data Protection Digital AccessKeep your audience glued to their seats with professionally designed PPT slides. This deck comprises of total of twelve slides. It has PPT templates with creative visuals and well researched content. Not just this, our PowerPoint professionals have crafted this deck with appropriate diagrams, layouts, icons, graphs, charts and more. This content ready presentation deck is fully editable. Just click the DOWNLOAD button below. Change the colour, text and font size. You can also modify the content as per your need. Get access to this well crafted complete deck presentation and leave your audience stunned.
-
 Cloud Access Security Broker CASB V2 CASB Performance Tracking Dashboard
Cloud Access Security Broker CASB V2 CASB Performance Tracking DashboardThis slide outlines the performance tracking dashboard for CASB deployment. The purpose of this slide is to showcase the status of various applications, IP addresses, users, machines, and web traffic. It also includes cloud discovery open alerts, risk levels, and top entities. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 CASB Performance Tracking Dashboard. Dispense information and present a thorough explanation of Performance Tracking Dashboard, Machines And Web Traffic, Cloud Discover Open Alerts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Use Cases Ppt Ideas Graphics Download
Cloud Access Security Broker CASB V2 Use Cases Ppt Ideas Graphics DownloadThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Use Cases Ppt Ideas Graphics Download. Dispense information and present a thorough explanation of Protection Against Threats, Secure Data, Upload Prevention And Encryption, Cloud Solutions With Transparency using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For Cloud Access Security Broker CASB V2 Ppt Ideas Design Inspiration
Table Of Contents For Cloud Access Security Broker CASB V2 Ppt Ideas Design InspirationIntroducing Table Of Contents For Cloud Access Security Broker CASB V2 Ppt Ideas Design Inspiration to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Shadow IT Management Lifecycle, Threat Protection, Data Security, Emerging Cloud Security Risks And Threats, using this template. Grab it now to reap its full benefits.
-
 Global Market Of Secure Access Service Edge Cloud Security Model
Global Market Of Secure Access Service Edge Cloud Security ModelThis slide depicts the global market size of the SASE market by components such as platforms and services. The purpose of this slide is to showcase the compound annual growth rate for the SASE model, including its growth drivers, such as cloud adoption, work from anywhere culture, and so on. Deliver an outstanding presentation on the topic using this Global Market Of Secure Access Service Edge Cloud Security Model. Dispense information and present a thorough explanation of Global, Market, Secure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Access Service Edge Performance Tracking Dashboard Cloud Security Model
Secure Access Service Edge Performance Tracking Dashboard Cloud Security ModelThis slide demonstrates the performance tracking dashboard for secure access service edge. The purpose of this slide is to showcase the overall performance of the SASE model, including connections, critical network alarms, critical security alerts, application volume, risky applications, and unblocked security threats. Deliver an outstanding presentation on the topic using this Secure Access Service Edge Performance Tracking Dashboard Cloud Security Model. Dispense information and present a thorough explanation of Service, Secure, Performance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Use Cases Next Generation CASB
Cloud Access Security Broker Use Cases Next Generation CASBThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker Use Cases Next Generation CASB Dispense information and present a thorough explanation of Protection Against Threats, Govern Usage, Secure Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Use Cases CASB Cloud Security
Cloud Access Security Broker Use Cases CASB Cloud SecurityThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Present the topic in a bit more detail with this Cloud Access Security Broker Use Cases CASB Cloud Security. Use it as a tool for discussion and navigation on Protection Against Threats, Compliance Policies, Cloud Access Security Broker. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agenda For Cloud Access Security Broker CASB V2 Ppt Ideas Introduction
Agenda For Cloud Access Security Broker CASB V2 Ppt Ideas IntroductionIntroducing Agenda For Cloud Access Security Broker CASB V2 Ppt Ideas Introduction to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Broker Technology, Architecture, Technologies, using this template. Grab it now to reap its full benefits.
-
 Benefits Of Cloud Access Security Broker 2 0 Cloud Access Security Broker CASB V2
Benefits Of Cloud Access Security Broker 2 0 Cloud Access Security Broker CASB V2This slide represents the advantages of cloud access security broker version 2.0. The purpose of this slide is to highlight the main benefits of CASB 2.0, including comprehensive coverage, cost-effectiveness, enhanced security efficacy, improved visibility, app database, and so on. Increase audience engagement and knowledge by dispensing information using Benefits Of Cloud Access Security Broker 2 0 Cloud Access Security Broker CASB V2. This template helps you present information on five stages. You can also present information on Cloud Access Security Broker, Comprehensive Coverage, Enhanced Security Efficacy, Cost Effectiveness using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 CASB Vs CSPM Vs CWPP Cloud Access Security Broker CASB V2 Ppt Ideas Samples
CASB Vs CSPM Vs CWPP Cloud Access Security Broker CASB V2 Ppt Ideas SamplesThis slide describes the difference between Cloud Access Security Broker CASB, cloud security posture management CSPM, and cloud workload protection platforms CWPP. The purpose of this slide is to highlight the key differences between the three technologies based on features such as focus, use cases, deployment model, etc. Present the topic in a bit more detail with this CASB Vs CSPM Vs CWPP Cloud Access Security Broker CASB V2 Ppt Ideas Samples. Use it as a tool for discussion and navigation on Cloud Workload Protection, Threat Detection And Response, Vulnerability Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 30 60 90 Days Plan To Deploy CASB Model
Cloud Access Security Broker CASB V2 30 60 90 Days Plan To Deploy CASB ModelThis slide represents the 30-0-90 days plan to implement the Cloud Access Security Broker model in an organization. The purpose of this slide is to showcase the various steps to be taken to deploy CASB at the interval every 30 days. Introducing Cloud Access Security Broker CASB V2 30 60 90 Days Plan To Deploy CASB Model to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Scope, Current Security Architecture, Security Operations Center Functions, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Advantages And Disadvantages Of Proxy Based Deployment
Cloud Access Security Broker CASB V2 Advantages And Disadvantages Of Proxy Based DeploymentThis slide represents the benefits and drawbacks of proxy-based CASB deployment. The purpose of this slide is to showcase the various pros and cons of proxy-based cloud access security brokers and the advantages cover flexibility, secure SaaS applications, and so on. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Advantages And Disadvantages Of Proxy Based Deployment. This template helps you present information on two stages. You can also present information on Cloud Access Security Brokers, Cover Flexibility, Secure SaaS Applications, Enforcement Of Security Policies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 And Encryption Ppt Gallery Design Templates
Cloud Access Security Broker CASB V2 And Encryption Ppt Gallery Design TemplatesThis slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of Cloud Access Security Broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 And Encryption Ppt Gallery Design Templates. Dispense information and present a thorough explanation of Detecting Sensitive Information, Personally Identifiable Information, Personal Health Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 And Secure Web Gateway Ppt Gallery Shapes
Cloud Access Security Broker CASB V2 And Secure Web Gateway Ppt Gallery ShapesThis slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 And Secure Web Gateway Ppt Gallery Shapes. Use it as a tool for discussion and navigation on Simplifying Deployment, Cloud Access Security Broker, Secure Web Gateway, Standardizing Authentication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 API Based Use Cases Of CASB Deployment
Cloud Access Security Broker CASB V2 API Based Use Cases Of CASB DeploymentThis slide outlines the use cases of API-based CASB deployment. This slide highlights the main use cases of API-based deployment of CASB deployment, including identifying malware in cloud services, implementing data transfer policies across different cloud services, auditing user access provisioning and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 API Based Use Cases Of CASB Deployment. Dispense information and present a thorough explanation of Malware In Cloud Services, Data Transfer Policies, Cloud Services, Auditing User Access Provisioning using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 API Scanning CASB Deployment Model
Cloud Access Security Broker CASB V2 API Scanning CASB Deployment ModelThis slide outlines the overview of the API scanning model of CASB deployment. The purpose of this slide is to showcase its features and introduce APIs and how this deployment works. It also represents the architecture of the API scanning model and its components include mobile and corporate devices and APIs. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 API Scanning CASB Deployment Model. Use it as a tool for discussion and navigation on Corporate Devices, Facilitate Communication, Real Time Protection, Non Intrusive Security Technique. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Architectural Components Ppt Gallery Microsoft
Cloud Access Security Broker CASB V2 Architectural Components Ppt Gallery MicrosoftThis slide outlines the main components of Cloud Access Security Broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Architectural Components Ppt Gallery Microsoft. Dispense information and present a thorough explanation of Cloud Access Security, Broker Architectural, Connectivity Gateway, Software As A Service using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Benefits Of Cloud Access Security Broker
Cloud Access Security Broker CASB V2 Benefits Of Cloud Access Security BrokerThis slide outlines the different advantages of Cloud Access Security Broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Benefits Of Cloud Access Security Broker. Use it as a tool for discussion and navigation on Cyber Threat Prevention, Granular Cloud Usage Control, Data Loss Prevention, Controlled External File Sharing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Best Practices To Implement Cloud Access Security Broker
Cloud Access Security Broker CASB V2 Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a Cloud Access Security Broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Best Practices To Implement Cloud Access Security Broker. Dispense information and present a thorough explanation of Cloud Access Security Broker, Business Operations, Building Visibility, Forecasting Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 CASB Application In Accounting And Finance Sector
Cloud Access Security Broker CASB V2 CASB Application In Accounting And Finance SectorThis slide outlines the application of the CASB model in the accounting and banking sectors. The purpose of this slide is to give an overview and represent the challenges that occur due to cloud data exchange and how CASB can overcome those challenges. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 CASB Application In Accounting And Finance Sector. This template helps you present information on three stages. You can also present information on Accounting And Banking Sectors, Cloud Data Exchange, Finance Organization, Data Drives Banking Business using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 CASB Application In Learning And Education Sector
Cloud Access Security Broker CASB V2 CASB Application In Learning And Education SectorThis slide represents the application of a Cloud Access Security Broker in the learning and education department. The purpose of this slide is to highlight the overview, challenges caused by the transition in education, and CASB solutions. Introducing Cloud Access Security Broker CASB V2 CASB Application In Learning And Education Sector to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Learning And Education Department, Transition In Education, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 CASB As A Streamline Endpoint Protection Solution
Cloud Access Security Broker CASB V2 CASB As A Streamline Endpoint Protection SolutionThis slide outlines how Cloud Access Security Broker 2.0 streamlines endpoint protection. The purpose of this slide is to showcase how CASB 2.0 improves endpoint security for streamlined deployment. It also includes the features of CASB 2.0 and endpoint security integration. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 CASB As A Streamline Endpoint Protection Solution. Use it as a tool for discussion and navigation on Cloud Access Security Broker, Streamlines Endpoint Protection, Streamlined Deployment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 CASB Deployment With Optional Components Pricing
Cloud Access Security Broker CASB V2 CASB Deployment With Optional Components PricingThis slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 CASB Deployment With Optional Components Pricing. Dispense information and present a thorough explanation of Data Security Subscription, Threat Protection Subscription, Data Retention, Customer Relationship Admins using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 CASB Deployment With Standard Components Pricing
Cloud Access Security Broker CASB V2 CASB Deployment With Standard Components PricingThis slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 CASB Deployment With Standard Components Pricing. Use it as a tool for discussion and navigation on Pricing Of Classic Elements, Components Include Visibility, Threat Protection, Data Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 CASB Forward Proxy Deployment Use Cases
Cloud Access Security Broker CASB V2 CASB Forward Proxy Deployment Use CasesThis slide highlights the main use cases of forward proxy server CASB deployment. The main purpose of this slide is to showcase the primary use cases of the forward proxy, including implementing granular access and activity controls and detecting show IT in the network. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 CASB Forward Proxy Deployment Use Cases. This template helps you present information on two stages. You can also present information on Deploying Granular Access, Activity Controls, Detecting Shadow, IT In The Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 CASB Reverse Proxy Deployment Use Cases
Cloud Access Security Broker CASB V2 CASB Reverse Proxy Deployment Use CasesThis slide illustrates the use cases of reverse proxy server deployment of the Cloud Access Security Broker model. The purpose of this slide is to highlight the main use cases of reverse proxy deployment, including using user behavior to enforce access constraints, keeping data from certain programs from being lost, and so on. Introducing Proxy to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Reverse Proxy Server Deployment, Cloud Access Security Broker, Reverse Proxy Deployment, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Checklist To Adopt A Cloud Access Security Broker
Cloud Access Security Broker CASB V2 Checklist To Adopt A Cloud Access Security BrokerThis slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Checklist To Adopt A Cloud Access Security Broker. Use it as a tool for discussion and navigation on Cloud Access Security Broker, Cloud Requirements, Conduct Regular Audits. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Cloud Access Security Broker And User Authentication
Cloud Access Security Broker CASB V2 Cloud Access Security Broker And User AuthenticationThis slide represents the improved user authentication method in Cloud Access Security Broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Cloud Access Security Broker And User Authentication. Dispense information and present a thorough explanation of Authentication Solutions, Creating Adaptive Authentication, Businesses To Dynamically using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Cloud Security Standards And Control Frameworks
Cloud Access Security Broker CASB V2 Cloud Security Standards And Control FrameworksThis slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Cloud Security Standards And Control Frameworks. Use it as a tool for discussion and navigation on Payment Card Industry, Data Security Standard, System And Organization Controls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Comparison Between CASB And Data Loss Prevention DLP
Cloud Access Security Broker CASB V2 Comparison Between CASB And Data Loss Prevention DLPThis slide describes the difference between Cloud Access Security Broker and data loss prevention. This slide highlights the main comparisons between CASB and DLP systems based on their purpose, focus area, use cases, key features, implementation and relationship. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Comparison Between CASB And Data Loss Prevention DLP. Dispense information and present a thorough explanation of Content Inspection, Data Classification, Encryption, Access Control using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Comparison Between Reverse Proxy And Load Balancer
Cloud Access Security Broker CASB V2 Comparison Between Reverse Proxy And Load BalancerThis slide represents the difference between reverse proxy and load balancer. The purpose of this slide is to highlight the main differences between reverse proxy server and load balancer based on how they respond to client request, number of servers required, and so on. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Comparison Between Reverse Proxy And Load Balancer. This template helps you present information on one stages. You can also present information on Reverse Proxy And Load Balancer, Reverse Proxy, Site Requires Several Servers, Scalability And Flexibility using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Conventional CASB Vs Next Generation CASB
Cloud Access Security Broker CASB V2 Conventional CASB Vs Next Generation CASBThis slide outlines the comparison between Cloud Access Security Broker and next-generation CASB. This slide highlights the main differences between conventional and next-generation CASB based on features such as focus, deployment model, integration approach, security capabilities, scalability, etc. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Conventional CASB Vs Next Generation CASB. Use it as a tool for discussion and navigation on Integration Approach, Security Capabilities, Deployment Flexibility, Management Complexity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Emerging Cloud Security Risks And Threats
Cloud Access Security Broker CASB V2 Emerging Cloud Security Risks And ThreatsThis slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Emerging Cloud Security Risks And Threats. Dispense information and present a thorough explanation of System Misconfigurations, Continuous Integration And Development, Supply Chain Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 For Table Of Contents Ppt Ideas Designs Download
Cloud Access Security Broker CASB V2 For Table Of Contents Ppt Ideas Designs DownloadIntroducing Cloud Access Security Broker CASB V2 For Table Of Contents Ppt Ideas Designs Download to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Shadow IT Management Lifecycle, Cloud Security Standards, Control Frameworks, Requirements, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Forward Proxy Deployment Overview And Working
Cloud Access Security Broker CASB V2 Forward Proxy Deployment Overview And WorkingThis slide describes the overview of the forward proxy deployment mode of the CASB model, including its working. The purpose of this slide is to showcase the working of proxy-based CASB deployment and the main components include user or clients, forward proxy, internet and origin server. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Forward Proxy Deployment Overview And Working. Use it as a tool for discussion and navigation on Deployment Overview And Working, Web Servers They Visit, Forward Proxy Method Is A Configuration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Future Of Cloud Access Security Broker CASB 2 0
Cloud Access Security Broker CASB V2 Future Of Cloud Access Security Broker CASB 2 0This slide outlines the overview of Cloud Access Security Broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Future Of Cloud Access Security Broker CASB 2 0. This template helps you present information on seven stages. You can also present information on Data Loss Prevention, Advanced Malware Protection, Managed Security Service, Endpoint Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Future Use Of Emerging Technologies In CASB Model
Cloud Access Security Broker CASB V2 Future Use Of Emerging Technologies In CASB ModelThis slide gives an overview of the technologies that can be used in the Cloud Access Security Broker model in the future. The purpose of this slide is to showcase the various emerging technologies that can help CASB to grow in the future. The technologies include AI, ML, CSPM, data privacy and protection, etc. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Future Use Of Emerging Technologies In CASB Model. Dispense information and present a thorough explanation of Cloud Security Posture Management, Data Privacy And Protection, Zero Trust Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
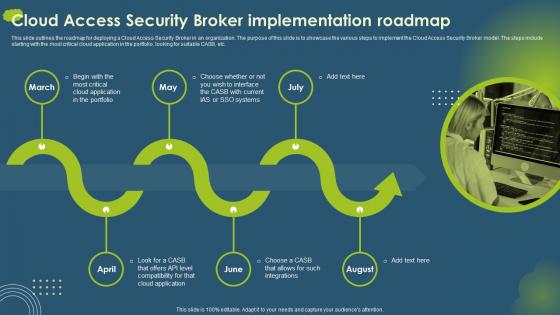 Cloud Access Security Broker CASB V2 Implementation Roadmap Ppt Gallery Portrait
Cloud Access Security Broker CASB V2 Implementation Roadmap Ppt Gallery PortraitThis slide outlines the roadmap for deploying a Cloud Access Security Broker in an organization. The purpose of this slide is to showcase the various steps to implement the Cloud Access Security Broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Introducing Cloud Access Security Broker CASB V2 Implementation Roadmap Ppt Gallery Portrait to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Critical Cloud Application, Compatibility, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Introduction Ppt Infographic Template Deck
Cloud Access Security Broker CASB V2 Introduction Ppt Infographic Template DeckThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the overview, benefits, and pillars of CASB, such as compliance, visibility, threat protection, and data security. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Introduction Ppt Infographic Template Deck. Use it as a tool for discussion and navigation on Risk Visibility, Threat Prevention, Granular Cloud Usage Control, Data Security . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Leading Cloud Access Security Broker Platforms
Cloud Access Security Broker CASB V2 Leading Cloud Access Security Broker PlatformsThis slide outlines the Leading Cloud Access Security Broker platforms. The purpose of this slide is to highlight the leading CASB platforms, including G-suite, office 365, and Amazon Web Services, and it also represents the benefits and features of these cloud platforms. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Leading Cloud Access Security Broker Platforms. This template helps you present information on three stages. You can also present information on Cloud Access Security, Broker Platforms, Amazon Web Services, Cloud Platforms using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Life Cycle Protection Ppt Gallery Layout Ideas
Cloud Access Security Broker CASB V2 Life Cycle Protection Ppt Gallery Layout IdeasIntroducing Cloud Access Security Broker CASB V2 Life Cycle Protection Ppt Gallery Layout Ideas to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Continuous Visibility And Assessment Systems, System Activity Payload Network, Contain Or Mitigate Risk, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Overview Of CASB Deployment Models
Cloud Access Security Broker CASB V2 Overview Of CASB Deployment ModelsThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Overview Of CASB Deployment Models. This template helps you present information on four stages. You can also present information on Cloud Access Security Broker, Unmanaged Gadgets, Inline Deployment, Scalable And Strong Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Overview Of Cloud Access Security Broker Architecture
Cloud Access Security Broker CASB V2 Overview Of Cloud Access Security Broker ArchitectureThis slide gives an overview of Cloud Access Security Broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Overview Of Cloud Access Security Broker Architecture. Dispense information and present a thorough explanation of Visibility, Compliance, Threat Protection, Enterprise Integration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Pillar Compliance Ppt Icon Background Images
Cloud Access Security Broker CASB V2 Pillar Compliance Ppt Icon Background ImagesThis slide gives an overview of the compliance pillar of cloud access security broker. The purpose of this slide is to showcase how compliance is a vital factor for an organization migrating its data and systems to the cloud. Compliance can help industries such as healthcare, retail, and financial services. Introducing Cloud Access Security Broker CASB V2 Pillar Compliance Ppt Icon Background Images to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Compliance Pillar, Cloud Access Security Broker, Financial Services, Compliance Risk Domains, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Pillar Data Security Ppt Icon Backgrounds
Cloud Access Security Broker CASB V2 Pillar Data Security Ppt Icon BackgroundsThis slide talks about the data security pillar of the Cloud Access Security Broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Pillar Data Security Ppt Icon Backgrounds. This template helps you present information on four stages. You can also present information on Document Fingerprinting, Data Security Pillar, Cloud Access Security Broker Pillar using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Pillar Overview Ppt Icon Background Designs
Cloud Access Security Broker CASB V2 Pillar Overview Ppt Icon Background DesignsThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Introducing Cloud Access Security Broker CASB V2 Pillar Overview Ppt Icon Background Designs to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Threat Protection, Data Security, Compliance, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Pillar Threat Protection Ppt Icon Introduction
Cloud Access Security Broker CASB V2 Pillar Threat Protection Ppt Icon IntroductionThis slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Pillar Threat Protection Ppt Icon Introduction. This template helps you present information on four stages. You can also present information on Threat Protection Pillar, Cloud Access Security Broker, Machine Learning Algorithms using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Pillar Visibility Ppt Icon Background Image
Cloud Access Security Broker CASB V2 Pillar Visibility Ppt Icon Background ImageThis slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Pillar Visibility Ppt Icon Background Image. Dispense information and present a thorough explanation of Cloud Access Security Broker Pillar, Visibility, Cloud Discovery Analysis, Device And Location Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Popular Cloud Access Security Broker Vendors
Cloud Access Security Broker CASB V2 Popular Cloud Access Security Broker VendorsThis slide outlines the popular Cloud Access Security Broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Popular Cloud Access Security Broker Vendors. Use it as a tool for discussion and navigation on Cloud Access Security Broker, Mid To Large Enterprises, Robust Integration, Cisco Systems. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Primary Types Of Reverse Proxy Server Deployment
Cloud Access Security Broker CASB V2 Primary Types Of Reverse Proxy Server DeploymentThis slide outlines the main types of reverse proxy server deployment, covering regular reverse proxies and load balancers. The purpose of this slide is to showcase how both methods work to manage traffic and offer security features to organizations. Introducing Cloud Access Security Broker CASB V2 Primary Types Of Reverse Proxy Server Deployment to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Regular Reverse Proxies, Load Balancers, Proxy Server Deployment, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Pros And Cons Of API Scanning CASB Deployment
Cloud Access Security Broker CASB V2 Pros And Cons Of API Scanning CASB DeploymentThis slide outlines the advantages and disadvantages of the API scanning Cloud Access Security Broker deployment model. This slide aims to highlight the pros and cons of the API scanning deployment model and the benefits include no impact on user experience, taking only a few hours to configure, etc. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Pros And Cons Of API Scanning CASB Deployment. This template helps you present information on one stages. You can also present information on Cloud Access Security, Broker Deployment Model, Scanning Deployment Model, Security Policy Modifications using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Proxy Based CASB Deployment Model
Cloud Access Security Broker CASB V2 Proxy Based CASB Deployment ModelThis slide outlines the overview of proxy-based CASB deployment. The purpose of this slide is to highlight the proxy-based implementation of the CASB model and it also includes the fundamental modes of proxy deployment, including forward proxy and reverse proxy. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Proxy Based CASB Deployment Model. Dispense information and present a thorough explanation of Proxy Based Implementation, Proxy Deployment, Proxy And Reverse Proxy, Operation Of Several using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Proxy Based Vs API Based Deployment Of CASB
Cloud Access Security Broker CASB V2 Proxy Based Vs API Based Deployment Of CASBThis slide represents the comparison between proxy-based and API-based deployment of the CASB model. The purpose of this slide is to highlight the key differences between proxy-based and API-based deployment of cloud access security broker. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Proxy Based Vs API Based Deployment Of CASB. Use it as a tool for discussion and navigation on Performance And Security, Proxy Based Deployment, Standalone Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Requirements For Appropriate Cloud Security Model
Cloud Access Security Broker CASB V2 Requirements For Appropriate Cloud Security ModelThis slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Introducing Cloud Access Security Broker CASB V2 Requirements For Appropriate Cloud Security Model to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Visibility And Threat Detection, Continuous Compliance, Data Encryption, Strong Authentication, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Reverse Proxy CASB Deployment Model
Cloud Access Security Broker CASB V2 Reverse Proxy CASB Deployment ModelThis slide outlines the overview of the reverse proxy cloud access security model broker. The purpose of this slide is to showcase overview of working and various types of reverse proxy CASB. The main types include regular reverse proxies and load balancers. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Reverse Proxy CASB Deployment Model. This template helps you present information on five stages. You can also present information on Reverse Proxy, Cloud Access Security Model Broker, Web Server Anonymity, Websites With High Traffic using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Reverse Proxy Vs Forward Proxy
Cloud Access Security Broker CASB V2 Reverse Proxy Vs Forward ProxyThis slide outlines the comparison between reverse proxy and forward proxy based on features. The purpose of this slide is to highlight the key differences between reverse proxy and forward proxy based on the features such as function, position, IP address, purpose, caching, SSL or TLS termination, performance, and implementation. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Reverse Proxy Vs Forward Proxy. Dispense information and present a thorough explanation of Reverse Proxy, Forward Proxy, Performance And Implementation, Load Balancing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.




