Powerpoint Templates and Google slides for ChatGPT Information Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Leveraging ChatGPT For Strengthening Information Security AI CD V
Leveraging ChatGPT For Strengthening Information Security AI CD VEnthrall your audience with this Leveraging ChatGPT For Strengthening Information Security AI CD V. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising fifty one slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Security Automation In Information Technology Powerpoint Presentation Slides
Security Automation In Information Technology Powerpoint Presentation SlidesThis complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fourty two slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.
-
 Agenda For Leveraging ChatGPT For Strengthening Information Security AI SS V
Agenda For Leveraging ChatGPT For Strengthening Information Security AI SS VIntroducing Agenda For Leveraging ChatGPT For Strengthening Information Security AI SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Agenda using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Leveraging ChatGPT For Strengthening Information Security AI SS V
Icons Slide For Leveraging ChatGPT For Strengthening Information Security AI SS VIntroducing our well researched set of slides titled Icons Slide For Leveraging ChatGPT For Strengthening Information Security AI SS V It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Leveraging ChatGPT For Strengthening Information Security Table Of Contents AI SS V
Leveraging ChatGPT For Strengthening Information Security Table Of Contents AI SS VDeliver an outstanding presentation on the topic using this Leveraging ChatGPT For Strengthening Information Security Table Of Contents AI SS V Dispense information and present a thorough explanation of Organization Cybersecurity, Importance For Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents Leveraging ChatGPT For Strengthening Information Security AI SS V
Table Of Contents Leveraging ChatGPT For Strengthening Information Security AI SS VIncrease audience engagement and knowledge by dispensing information using Table Of Contents Leveraging ChatGPT For Strengthening Information Security AI SS V This template helps you present information on Five stages. You can also present information on SQL Injection, Phishing, Middle Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 F652 Security Automation In Information Technology Security Automation Dashboard Highlighting Phishing
F652 Security Automation In Information Technology Security Automation Dashboard Highlighting PhishingThis slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Present the topic in a bit more detail with this F652 Security Automation In Information Technology Security Automation Dashboard Highlighting Phishing. Use it as a tool for discussion and navigation on Automation, Dashboard, Phishing Alerts. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Dashboard Highlighting Resolved Events Security Automation In Information Technology
Security Automation Dashboard Highlighting Resolved Events Security Automation In Information TechnologyThis slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions. Deliver an outstanding presentation on the topic using this Security Automation Dashboard Highlighting Resolved Events Security Automation In Information Technology. Dispense information and present a thorough explanation of Automation, Dashboard, Workload using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Automation In Information Technology Time To Fix Security Threat With Manual Testing
Security Automation In Information Technology Time To Fix Security Threat With Manual TestingThis slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Deliver an outstanding presentation on the topic using this Security Automation In Information Technology Time To Fix Security Threat With Manual Testing. Dispense information and present a thorough explanation of Security, Threat, Manual Testing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Automation In Information Technology Current State Of Security Automation With Projected Development
Security Automation In Information Technology Current State Of Security Automation With Projected DevelopmentThis slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. Deliver an outstanding presentation on the topic using this Security Automation In Information Technology Current State Of Security Automation With Projected Development. Dispense information and present a thorough explanation of Projected Development, Security Automation, Organizations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 How is automation used in electronic information security
How is automation used in electronic information securityThis slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Increase audience engagement and knowledge by dispensing information using How Is Automation Used In Electronic Information Security. This template helps you present information on three stages. You can also present information on Threat Detection, Threat Response, Human Augmentation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security How Is Automation Used In Information Security
Information Security How Is Automation Used In Information SecurityThis slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Increase audience engagement and knowledge by dispensing information using Information Security How Is Automation Used In Information Security. This template helps you present information on three stages. You can also present information on Threat Detection, Human Augmentation, Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Program Eliminating Manual Security Processes Through Automation
Information Security Program Eliminating Manual Security Processes Through AutomationMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver an outstanding presentation on the topic using this Information Security Program Eliminating Manual Security Processes Through Automation. Dispense information and present a thorough explanation of Processes, Automation, Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security How Is Automation Used In Information Technology Security
Information Technology Security How Is Automation Used In Information Technology SecurityThis slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Introducing Information Technology Security How Is Automation Used In Information Technology Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Threat Detection, Threat Response, Human Augmentation, using this template. Grab it now to reap its full benefits.
-
 Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security Operations
Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security OperationsThis slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Increase audience engagement and knowledge by dispensing information using Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security Operations. This template helps you present information on four stages. You can also present information on Ineffective, Information, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 F651 Security Automation In Information Technology Security Automation Architecture With Key Elements
F651 Security Automation In Information Technology Security Automation Architecture With Key ElementsThis slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Present the topic in a bit more detail with this F651 Security Automation In Information Technology Security Automation Architecture With Key Elements. Use it as a tool for discussion and navigation on Security, Automation, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F653 Security Automation In Information Technology Security Automation Stages With Maturity Level
F653 Security Automation In Information Technology Security Automation Stages With Maturity LevelThis slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Present the topic in a bit more detail with this F653 Security Automation In Information Technology Security Automation Stages With Maturity Level. Use it as a tool for discussion and navigation on Systematic Stage, Institutionalized Stage, Opportunistic Stage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation In Information Technology Domain Security Controls That Can Be Automated
Security Automation In Information Technology Domain Security Controls That Can Be AutomatedThis slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Present the topic in a bit more detail with this Security Automation In Information Technology Domain Security Controls That Can Be Automated. Use it as a tool for discussion and navigation on Information Security, Organization, Operations Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
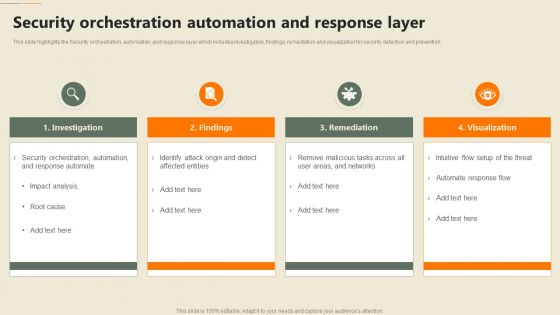 Security Automation In Information Technology Security Orchestration Automation And Response Layer
Security Automation In Information Technology Security Orchestration Automation And Response LayerThis slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention Increase audience engagement and knowledge by dispensing information using Security Automation In Information Technology Security Orchestration Automation And Response Layer. This template helps you present information on four stages. You can also present information on Investigation, Remediation, Visualization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Impacts Of Ineffective Information Technology Security Automation To Investigate And Remediate Cyberthreats
Impacts Of Ineffective Information Technology Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Increase audience engagement and knowledge by dispensing information using Impacts Of Ineffective Information Technology Security Automation To Investigate And Remediate Cyberthreats. This template helps you present information on five stages. You can also present information on Ineffective, Information, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda For Security Automation In Information Technology
Agenda For Security Automation In Information TechnologyIncrease audience engagement and knowledge by dispensing information using Agenda For Security Automation In Information Technology. This template helps you present information on six stages. You can also present information on Business, Process, Importance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine Ideal Tasks For Security Automation Security Automation In Information Technology
Determine Ideal Tasks For Security Automation Security Automation In Information Technologyslide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Present the topic in a bit more detail with this Determine Ideal Tasks For Security Automation Security Automation In Information Technology. Use it as a tool for discussion and navigation on Security Automation, Determine, Sensitive Tasks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Security Automation Tools With Pros And Cons Security Automation In Information Technology
Different Security Automation Tools With Pros And Cons Security Automation In Information TechnologyThis slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM Deliver an outstanding presentation on the topic using this Different Security Automation Tools With Pros And Cons Security Automation In Information Technology. Dispense information and present a thorough explanation of Automation, Security Orchestration, Process Automation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Network It Security Automation Security Automation In Information Technology
Enterprise Network It Security Automation Security Automation In Information TechnologyThis slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Increase audience engagement and knowledge by dispensing information using Enterprise Network It Security Automation Security Automation In Information Technology. This template helps you present information on six stages. You can also present information on Orchestrating Network Security, Security Policy Automation, Infrastructure using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
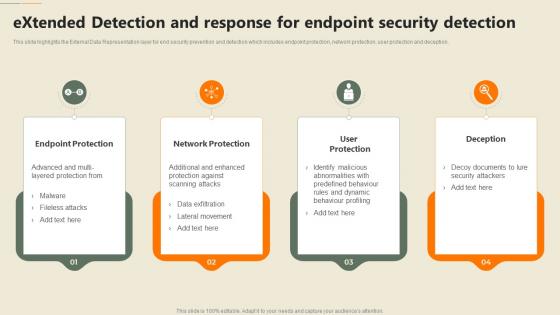 Extended Detection And Response For Endpoint Security Detection Security Automation In Information Technology
Extended Detection And Response For Endpoint Security Detection Security Automation In Information TechnologyThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Increase audience engagement and knowledge by dispensing information using Extended Detection And Response For Endpoint Security Detection Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Endpoint Protection, Network Protection, Deception using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide Security Automation In Information Technology
Icons Slide Security Automation In Information TechnologyPresent the topic in a bit more detail with this Icons Slide Security Automation In Information Technology. Use it as a tool for discussion and navigation on Icons. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
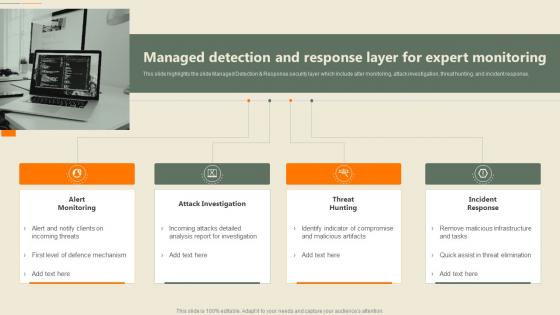 Managed Detection And Response Layer For Expert Monitoring Security Automation In Information Technology
Managed Detection And Response Layer For Expert Monitoring Security Automation In Information TechnologyThis slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response Increase audience engagement and knowledge by dispensing information using Managed Detection And Response Layer For Expert Monitoring Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Attack Investigation, Incident Response, Threat Hunting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Measure Security Automation Metrics For Operations Efficiency Security Automation In Information Technology
Measure Security Automation Metrics For Operations Efficiency Security Automation In Information TechnologyThis slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Present the topic in a bit more detail with this Measure Security Automation Metrics For Operations Efficiency Security Automation In Information Technology. Use it as a tool for discussion and navigation on Automation, Operations Efficiency, Performance Improvements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Right Time To Add Automation In Security Security Automation In Information Technology
Right Time To Add Automation In Security Security Automation In Information TechnologyThis slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. Deliver an outstanding presentation on the topic using this Right Time To Add Automation In Security Security Automation In Information Technology. Dispense information and present a thorough explanation of Individual, Insights, Automation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
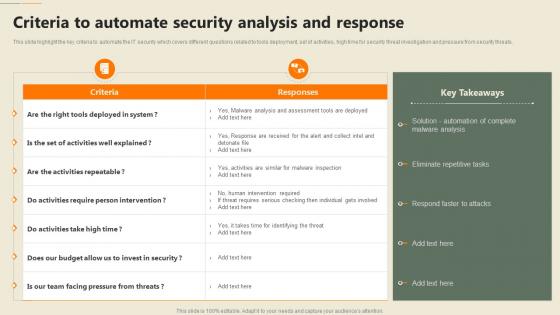 Security Automation In Information Technology Criteria To Automate Security Analysis And Response
Security Automation In Information Technology Criteria To Automate Security Analysis And ResponseThis slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Present the topic in a bit more detail with this Security Automation In Information Technology Criteria To Automate Security Analysis And Response. Use it as a tool for discussion and navigation on Analysis, Eliminate Repetitive Tasks, Respond Faster To Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation In Information Technology Impacts Of Ineffective Information Technology Security
Security Automation In Information Technology Impacts Of Ineffective Information Technology SecurityThis slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Increase audience engagement and knowledge by dispensing information using Security Automation In Information Technology Impacts Of Ineffective Information Technology Security. This template helps you present information on five stages. You can also present information on Information, Technology, Automation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Security Automation In Information Technology Table Of Contents
Security Automation In Information Technology Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Security Automation In Information Technology Table Of Contents. This template helps you present information on one stages. You can also present information on Security Automation, Processes, Security Detection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Security Automation Integrates Tools Systems And Processes Security Automation In Information Technology
Security Automation Integrates Tools Systems And Processes Security Automation In Information TechnologyThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Increase audience engagement and knowledge by dispensing information using Security Automation Integrates Tools Systems And Processes Security Automation In Information Technology. This template helps you present information on eight stages. You can also present information on Automation, Integrates, Processes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Security Processes That Cant Be Automated Security Automation In Information Technology
Security Processes That Cant Be Automated Security Automation In Information TechnologyThe following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Increase audience engagement and knowledge by dispensing information using Security Processes That Cant Be Automated Security Automation In Information Technology. This template helps you present information on three stages. You can also present information on Threat Modeling, Penetration Testing, Bug Bounty using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents Security Automation In Information Technology
Table Of Contents Security Automation In Information TechnologyPresent the topic in a bit more detail with this Table Of Contents Security Automation In Information Technology. Use it as a tool for discussion and navigation on Security Automation, Architecture And Importance, Automation Dashboards. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Unified Platform Integration For Security Automation Security Automation In Information Technology
Unified Platform Integration For Security Automation Security Automation In Information TechnologyThis slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. Increase audience engagement and knowledge by dispensing information using Unified Platform Integration For Security Automation Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Access Management, Security Automation, Firewalls using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Why To Automate The It Security Process Security Automation In Information Technology
Why To Automate The It Security Process Security Automation In Information TechnologyThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Increase audience engagement and knowledge by dispensing information using Why To Automate The It Security Process Security Automation In Information Technology. This template helps you present information on five stages. You can also present information on Better Threat Detection, Faster Containment, Improve Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Impacts Of Ineffective Information Technology Security Security Orchestration Automation
Impacts Of Ineffective Information Technology Security Security Orchestration AutomationThis slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Introducing Impacts Of Ineffective Information Technology Security Security Orchestration Automation to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Impacts Of Ineffective, Information Technology, Security, using this template. Grab it now to reap its full benefits.



