Powerpoint Templates and Google slides for By Security Type
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Total Cryptocurrency Stolen By Victim Type Hands On Blockchain Security Risk BCT SS V
Total Cryptocurrency Stolen By Victim Type Hands On Blockchain Security Risk BCT SS VThe following slide depicts the total amount of cryptocurrencies stolen. It includes elements such as centralized exchange, decentralized finance protocol, etc. Deliver an outstanding presentation on the topic using this Total Cryptocurrency Stolen By Victim Type Hands On Blockchain Security Risk BCT SS V. Dispense information and present a thorough explanation of Total Cryptocurrency, Stolen By Victim Type using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber Attacks
Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber AttacksThis slide represents the different types of cyber-attacks throughout the year, including the percentage of total loss caused by these attacks. Present the topic in a bit more detail with this Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber Attacks. Use it as a tool for discussion and navigation on Cyber Attacks Throughout, Online Or Web Based Attacks, Malware Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
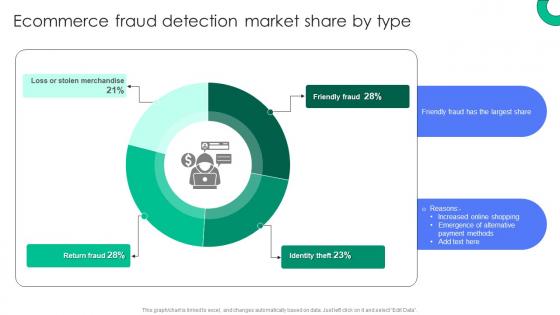 Ecommerce Fraud Detection Market Share By Type Implementing E Commerce Security Measures
Ecommerce Fraud Detection Market Share By Type Implementing E Commerce Security MeasuresPresent the topic in a bit more detail with this Ecommerce Fraud Detection Market Share By Type Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Identity Theft, Friendly Fraud, Return Fraud. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Of Information Most Commonly Types Of Ict Securities Used By Strategy SS V
Implementation Of Information Most Commonly Types Of Ict Securities Used By Strategy SS VThis slide represents various types of information and communication technology ICT securities used by businesses. It covers network security, endpoint security, access security, and data encryption. Introducing Implementation Of Information Most Commonly Types Of Ict Securities Used By Strategy SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, Access Security, using this template. Grab it now to reap its full benefits.
-
 Strategic Plan To Implement Most Commonly Types Of Ict Securities Used By Businesses Strategy SS V
Strategic Plan To Implement Most Commonly Types Of Ict Securities Used By Businesses Strategy SS VThis slide represents various types of information and communication technology ICT securities used by businesses. It covers network security, endpoint security, access security, and data encryption. Introducing Strategic Plan To Implement Most Commonly Types Of Ict Securities Used By Businesses Strategy SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on IT Governance, Visualization, Resource Management using this template. Grab it now to reap its full benefits.
-
 Types Of Cyber Attacks Encountered By Employees Creating Cyber Security Awareness
Types Of Cyber Attacks Encountered By Employees Creating Cyber Security AwarenessThe following slide showcases the various types of cyber-attacks faced by staff to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service tec. Increase audience engagement and knowledge by dispensing information using Types Of Cyber Attacks Encountered By Employees Creating Cyber Security Awareness This template helps you present information on Five stages. You can also present information on Malware, Ransomware, Middle Attack, Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Types Of Security Vulnerability Caused By Oversight
Types Of Security Vulnerability Caused By OversightFollowing slide highlights oversight due to security vulnerabilities type that lead to data breaching. It further covers types such as insider threat, lack of strong encryption, weak credentialing practices, etc. Presenting our set of slides with Types Of Security Vulnerability Caused By Oversight This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Insider Threat, Strong Encryption, Weak Credentialing Practices
-
 Revenue By Customer Type Manpower Security Services Company Profile Ppt Slides Information
Revenue By Customer Type Manpower Security Services Company Profile Ppt Slides InformationThis slide highlights the security company revenue by customer type which includes government, financial institutions, major corporate and industries, retail, transport, leisure and tourism. Present the topic in a bit more detail with this Revenue By Customer Type Manpower Security Services Company Profile Ppt Slides Information. Use it as a tool for discussion and navigation on Revenue, Educational, Institutions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Revenue By Customer Type Security Guard Service Company Profile
Revenue By Customer Type Security Guard Service Company ProfileThis slide highlights the security company revenue by customer type which includes government, financial institutions, major corporate and industries, retail, transport, leisure and tourism. Deliver an outstanding presentation on the topic using this Revenue By Customer Type Security Guard Service Company Profile. Dispense information and present a thorough explanation of Government, Financial Institutions, Schools And Colleges using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Revenue By Customer Type Security Services Business Profile Ppt Slides
Revenue By Customer Type Security Services Business Profile Ppt SlidesThis slide highlights the security company revenue by customer type which includes government, financial institutions, major corporate and industries, retail, transport, leisure and tourism. Deliver an outstanding presentation on the topic using this Revenue By Customer Type Security Services Business Profile Ppt Slides. Dispense information and present a thorough explanation of Revenue, Customer Type using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Revenue By Customer Type Security And Manpower Services Company Profile
Revenue By Customer Type Security And Manpower Services Company ProfileThis slide highlights the security company revenue by customer type which includes government, financial institutions, major corporate and industries, retail, transport, leisure and tourism. Present the topic in a bit more detail with this Revenue By Customer Type Security And Manpower Services Company Profile. Use it as a tool for discussion and navigation on Major Corporates And Industrials, Financial Institutions, Government, Transport And Logistics. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Architecture And Security Review Types Of Services Offered By Consulting Firm
Cloud Architecture And Security Review Types Of Services Offered By Consulting FirmThis slide covers the broader services offered by consulting firm such as managing data centres, multi cloud services, manged security services. Increase audience engagement and knowledge by dispensing information using Cloud Architecture And Security Review Types Of Services Offered By Consulting Firm. This template helps you present information on four stages. You can also present information on Managed Security, Data Centers, Consulting Firm using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Most Commonly Types Of ICT Securities Used By Businesses ICT Strategic Framework Strategy SS V
Most Commonly Types Of ICT Securities Used By Businesses ICT Strategic Framework Strategy SS VThis slide represents various types of information and communication technology ICT securities used by businesses. It covers network security, endpoint security, access security, and data encryption. Introducing Most Commonly Types Of ICT Securities Used By Businesses ICT Strategic Framework Strategy SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, End Point Security, Access Security, Data Encryption, using this template. Grab it now to reap its full benefits.



