Powerpoint Templates and Google slides for Breach Risk
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Computer system security detail impact computer security plan can reduce the risk of data breach in organization
Computer system security detail impact computer security plan can reduce the risk of data breach in organizationThis slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Present the topic in a bit more detail with this Computer System Security Detail Impact Computer Security Plan Can Reduce The Risk Of Data Breach In Organization. Use it as a tool for discussion and navigation on System Misconfiguration, Network Intrusion, Automated Information Exfiltration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Trend Analysis With KPI Dashboard Implementing Cyber Risk Management Process
Data Breach Trend Analysis With KPI Dashboard Implementing Cyber Risk Management ProcessThe following slide depicts the data breach trends to minimize information leakage and patch affected system. It includes elements such as breach risk trend, breach by risk category, current and future goal analysis etc. Deliver an outstanding presentation on the topic using this Data Breach Trend Analysis With KPI Dashboard Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Current And Future Goal Analysis, Breach Risk Trend using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Trend Analysis With KPI Dashboard Cyber Risk Assessment
Data Breach Trend Analysis With KPI Dashboard Cyber Risk AssessmentThe following slide depicts the data breach trends to minimize information leakage and patch affected system. It includes elements such as breach risk trend, breach by risk category, current and future goal analysis etc. Present the topic in a bit more detail with this Data Breach Trend Analysis With KPI Dashboard Cyber Risk Assessment Use it as a tool for discussion and navigation on Breach Risk, Business Unit, Risk Category This template is free to edit as deemed fit for your organization. Therefore download it now.
-
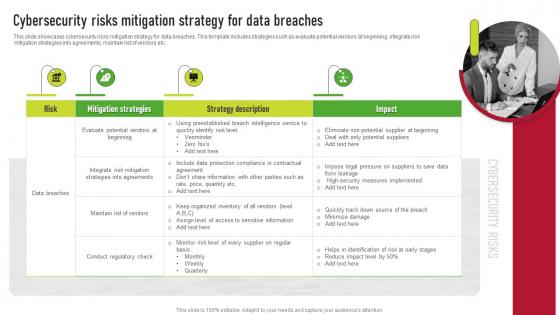 Cybersecurity Risks Mitigation Strategy For Data Breaches Supplier Risk Management
Cybersecurity Risks Mitigation Strategy For Data Breaches Supplier Risk ManagementThis slide showcases cybersecurity risks mitigation strategy for data breaches. This template includes strategies such as evaluate potential vendors at beginning, integrate risk mitigation strategies into agreements, maintain list of vendors etc. Introducing Cybersecurity Risks Mitigation Strategy For Data Breaches Supplier Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Mitigation Strategies, Strategy Description, Risk, using this template. Grab it now to reap its full benefits.
-
 Data Breach Response Plan Assessing Risk And Potential Vulnerabilities In Business Data
Data Breach Response Plan Assessing Risk And Potential Vulnerabilities In Business DataThis slide discusses the risks and vulnerabilities assessment of organizational data. The different risk scenarios can be incompetent and malicious employees, catastrophic data loss, disruption of services, sensitive data exposure, reputation management, etc. Present the topic in a bit more detail with this Data Breach Response Plan Assessing Risk And Potential Vulnerabilities In Business Data. Use it as a tool for discussion and navigation on Incompetent And Malicious Employees, Catastrophic Data Loss, Reputation Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Response Plan Risks And Mitigation Strategies For Data Breach Response Plan
Data Breach Response Plan Risks And Mitigation Strategies For Data Breach Response PlanThe purpose of this slide is to discuss the challenges faced while handling data breaches. The critical components of this slide are the description of the risk, probability of occurrence, impact on system infrastructure, and possible mitigation strategies. Deliver an outstanding presentation on the topic using this Data Breach Response Plan Risks And Mitigation Strategies For Data Breach Response Plan. Dispense information and present a thorough explanation of Inadequate Employee Training, Weak Network Security, Regulatory Non Compliance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Contingency Risk Icon For Data Breaches
Contingency Risk Icon For Data BreachesIntroducing our Contingency Risk Icon For Data Breaches set of slides. The topics discussed in these slides are Contingency Risk Icon For Data Breaches. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Risk Management Case Study Mitigating Data Breach Risks Optimizing Risk Management Practices Risk SS
Risk Management Case Study Mitigating Data Breach Risks Optimizing Risk Management Practices Risk SSThis slide defines a case study on mitigating data breach risks faced by an insurance company, along with details related to the problems faced, solutions taken, and the resulting outcome. Introducing Risk Management Case Study Mitigating Data Breach Risks Optimizing Risk Management Practices Risk SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Risk Management, Mitigating Data Breach Risks, Frameworks And Regulations, using this template. Grab it now to reap its full benefits.
-
 Web application firewall waf it implementation decreased risk data breach in web apps
Web application firewall waf it implementation decreased risk data breach in web appsThis slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Deliver an outstanding presentation on the topic using this Web Application Firewall Waf It Implementation Decreased Risk Data Breach In Web Apps. Dispense information and present a thorough explanation of Implementation, Misconfiguration, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Detail Impact Information Security Can Reduce Risk Data Breach Organization
Information Security Detail Impact Information Security Can Reduce Risk Data Breach OrganizationThis slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver an outstanding presentation on the topic using this Information Security Detail Impact Information Security Can Reduce Risk Data Breach Organization. Dispense information and present a thorough explanation of Organization, Information, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Assessing Cost Of Information Breach In Risk Assessment And Management Plan For Information Security
Assessing Cost Of Information Breach In Risk Assessment And Management Plan For Information SecurityPresent the topic in a bit more detail with this Assessing Cost Of Information Breach In Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Information, Sources, Engineering. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Assessing Cost Of Information Breach In Different Countries Information Security Risk Management
Assessing Cost Of Information Breach In Different Countries Information Security Risk ManagementDeliver an outstanding presentation on the topic using this Assessing Cost Of Information Breach In Different Countries Information Security Risk Management. Dispense information and present a thorough explanation of Assessing, Information Breach, Different Countries using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information And Data Breach Impacting Customer Loyalty Information Security Risk Management
Information And Data Breach Impacting Customer Loyalty Information Security Risk ManagementDeliver an outstanding presentation on the topic using this Information And Data Breach Impacting Customer Loyalty Information Security Risk Management. Dispense information and present a thorough explanation of Information, Data Breach Impacting, Customer Loyalty using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Firewall WAF Implementation Decreased the Risk of Data Breach in Web Apps
Application Firewall WAF Implementation Decreased the Risk of Data Breach in Web AppsThis slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Present the topic in a bit more detail with this Application Firewall WAF Implementation Decreased the Risk of Data Breach in Web Apps. Use it as a tool for discussion and navigation on SQL Injection, Ddos Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Average Costing On Risk Management For Data Breach Incident
Average Costing On Risk Management For Data Breach IncidentThis slide covers total cost incurred on response of data breach incident. It includes four categories such as incident detection and escalation, notifications, post breach response, lost business cost ,etc. Presenting our well structured Average Costing On Risk Management For Data Breach Incident. The topics discussed in this slide are Average Costing On Risk, Management, Data Breach Incident. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Breakdown Of Malicious Data Breach Risk Root Cause By Threat
Breakdown Of Malicious Data Breach Risk Root Cause By ThreatThis slide depicts division of data breach with root cause. It includes risk categories such as compromised credentials, cloud misconfiguration, third party software vulnerability, phishing, security compromise, social engineering, business email compromise, etc. Introducing our Breakdown Of Malicious Data Breach Risk Root Cause By Threat set of slides. The topics discussed in these slides are Social Engineering, Business Email Compromise, Malicious Insider. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Breach Risks Stats On Social Media Platforms And Incident Sources
Data Breach Risks Stats On Social Media Platforms And Incident SourcesThis slide covers trends on social media data breach incidents reported. It also includes various sources of data theft such as malicious outsider, accidental loss, malicious insider, hacker, etc. Introducing our Data Breach Risks Stats On Social Media Platforms And Incident Sources set of slides. The topics discussed in these slides are Data Breach Risks, Stats On Social Media, Platforms And Incident Sources. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Theft And Breach Risk Monitoring Dashboard
Data Theft And Breach Risk Monitoring DashboardThis slide covers dashboard to monitor top data breaches and loss of confidential data in organization. It includes KPIs such percentage of data risks detected, number of data risks, data risk analysis, response progress for data risks, data risk ratings. Presenting our well structured Data Theft And Breach Risk Monitoring Dashboard. The topics discussed in this slide are Data Theft And Breach, Risk Monitoring, Dashboard. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Information System Security And Risk Administration Information And Data Breach Impacting Customer Loyalty
Information System Security And Risk Administration Information And Data Breach Impacting Customer LoyaltyDeliver an outstanding presentation on the topic using this Information System Security And Risk Administration Information And Data Breach Impacting Customer Loyalty. Dispense information and present a thorough explanation of Business, Financial Data, Data Breach using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Assessing Cost Of Information Breach In Different Information System Security And Risk Administration Plan
Assessing Cost Of Information Breach In Different Information System Security And Risk Administration PlanPresent the topic in a bit more detail with this Assessing Cost Of Information Breach In Different Information System Security And Risk Administration Plan. Use it as a tool for discussion and navigation on Past Decade, Social Engineering, Advanced Persistent Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
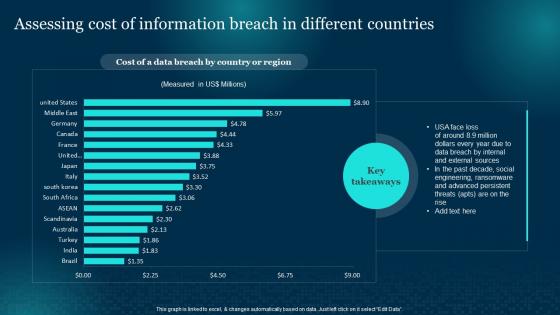 Assessing Cost Of Information Breach In Cybersecurity Risk Analysis And Management Plan
Assessing Cost Of Information Breach In Cybersecurity Risk Analysis And Management PlanPresent the topic in a bit more detail with this Assessing Cost Of Information Breach In Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Information, Ransomware, Sources. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
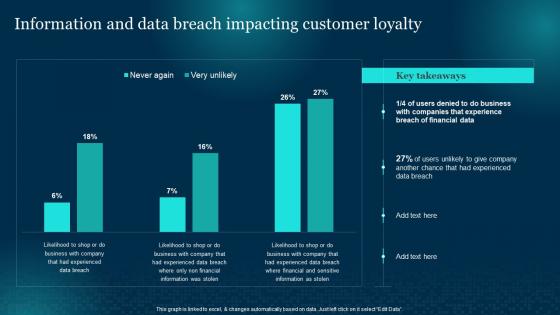 Cybersecurity Risk Analysis And Management Plan Information And Data Breach Impacting
Cybersecurity Risk Analysis And Management Plan Information And Data Breach ImpactingPresent the topic in a bit more detail with this Cybersecurity Risk Analysis And Management Plan Information And Data Breach Impacting. Use it as a tool for discussion and navigation on Information, Customer Loyalty, Financial Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Action plan in case of breaches managing cyber risk in a digital age
Action plan in case of breaches managing cyber risk in a digital ageMentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time. Present the topic in a bit more detail with this Action Plan In Case Of Breaches Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Action Plan In Case Of Breaches. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Communication plan for cyber breaches managing cyber risk in a digital age
Communication plan for cyber breaches managing cyber risk in a digital ageMentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Deliver an outstanding presentation on the topic using this Communication Plan For Cyber Breaches Managing Cyber Risk In A Digital Age. Dispense information and present a thorough explanation of Communication Plan For Cyber Breaches using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Action Plan In Case Of Breaches Risk Based Methodology To Cyber
Action Plan In Case Of Breaches Risk Based Methodology To CyberMentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time.Present the topic in a bit more detail with this Action Plan In Case Of Breaches Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Security Breach, Confidential Information, Resources Required This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Action Plan In Case Of Breaches Introducing A Risk Based Approach To Cyber Security
Action Plan In Case Of Breaches Introducing A Risk Based Approach To Cyber SecurityMentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time.Present the topic in a bit more detail with this Action Plan In Case Of Breaches Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Expected Resolution Time, Responsible Person, Communication Mode This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Communication Plan For Cyber Breaches Introducing A Risk Based Approach To Cyber Security
Communication Plan For Cyber Breaches Introducing A Risk Based Approach To Cyber SecurityMentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible.Present the topic in a bit more detail with this Communication Plan For Cyber Breaches Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Evaluate Sprint Status, Quality Standards, Project Coordinator This template is free to edit as deemed fit for your organization. Therefore download it now.
-
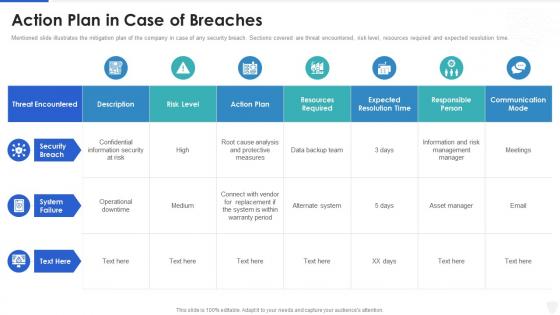 Cybersecurity and digital business risk management action plan in case of breaches
Cybersecurity and digital business risk management action plan in case of breachesMentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time. Present the topic in a bit more detail with this Cybersecurity And Digital Business Risk Management Action Plan In Case Of Breaches. Use it as a tool for discussion and navigation on Measures, Replacement, Resources. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity and digital business risk management communication plan for cyber breaches
Cybersecurity and digital business risk management communication plan for cyber breachesMentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Deliver an outstanding presentation on the topic using this Cybersecurity And Digital Business Risk Management Communication Plan For Cyber Breaches. Dispense information and present a thorough explanation of Communication, Product, Development using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Risk Management Financial Burden To Company From IT Security Breaches
Enterprise Risk Management Financial Burden To Company From IT Security BreachesThis slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Deliver an outstanding presentation on the topic using this Enterprise Risk Management Financial Burden To Company From IT Security Breaches. Dispense information and present a thorough explanation of Professional Services, Lost Business Opportunities, Total Damage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Analyzing The Impact On Assets Due To Information Breach Information Security Risk Management
Analyzing The Impact On Assets Due To Information Breach Information Security Risk ManagementThis slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets. Present the topic in a bit more detail with this Analyzing The Impact On Assets Due To Information Breach Information Security Risk Management. Use it as a tool for discussion and navigation on Impact On Revenue, Analyzing, Information Breach. This template is free to edit as deemed fit for your organization. Therefore download it now
-
 Mitigation Strategies To Avoid Information Breach Information Security Risk Management
Mitigation Strategies To Avoid Information Breach Information Security Risk ManagementThis slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Introducing Mitigation Strategies To Avoid Information Breach Information Security Risk Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Implement Antivirus Software, Monitor Network Traffic, Incident Response Plan, using this template. Grab it now to reap its full benefits.
-
 Financial Burden To Company From It Security Breaches Risk Assessment Of It Systems
Financial Burden To Company From It Security Breaches Risk Assessment Of It SystemsThis slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Deliver an outstanding presentation on the topic using this Financial Burden To Company From It Security Breaches Risk Assessment Of It Systems. Dispense information and present a thorough explanation of Professional Services, Lost Business Opportunities, Financial using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Risk Process Flow Model
Data Breach Risk Process Flow ModelThis slide covers process of data breach in an organisation. It includes steps such as researching weak points, staging attack and exfiltration of data resulting it to data breach in an organisation. Presenting our well structured Data Breach Risk Process Flow Model. The topics discussed in this slide are Social Engineering, Infrastructure Weakness, Risk Process Flow. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Four Steps Of Cyber Security Data Breach Risk Process
Four Steps Of Cyber Security Data Breach Risk ProcessThis slide covers steps utilised to breach data. It includes stages such as probing, performing initial attack, expansion of attacks and data lifting. Introducing our premium set of slides with name Four Steps Of Cyber Security Data Breach Risk Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Initial Attack, Expanded Attack, Breach Risk Process. So download instantly and tailor it with your information.
-
 Survey Insights On Data Breach Risk Incidents Icon
Survey Insights On Data Breach Risk Incidents IconPresenting our set of slides with name Survey Insights On Data Breach Risk Incidents Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Survey Insights, Data Breach, Risk Incidents Icon.
-
 Survey Insights On Risk Of Data Breach With Employees BYOD Policy
Survey Insights On Risk Of Data Breach With Employees BYOD PolicyThis slide covers insights on data breach incidents pertaining to companys BYOD policy. It includes stats on balancing employee freedom, company app functionality and data theft incidents by employees. Introducing our premium set of slides with name Survey Insights On Risk Of Data Breach With Employees BYOD Policy. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Survey Insights On Risk, Data Breach With Employees, BYOD Policy. So download instantly and tailor it with your information.
-
 Analysing The Impact On Assets Information Breach Information System Security And Risk Administration
Analysing The Impact On Assets Information Breach Information System Security And Risk AdministrationThis slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets. Deliver an outstanding presentation on the topic using this Analysing The Impact On Assets Information Breach Information System Security And Risk Administration. Dispense information and present a thorough explanation of Cost To Protect, Sales Records, Products Database using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mitigation Strategies To Avoid Information Breach Information System Security And Risk Administration Plan
Mitigation Strategies To Avoid Information Breach Information System Security And Risk Administration PlanThis slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Increase audience engagement and knowledge by dispensing information using Mitigation Strategies To Avoid Information Breach Information System Security And Risk Administration Plan. This template helps you present information on five stages. You can also present information on Incident Response Plan, Monitor Network Traffic, Patch Management Schedule using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 F857 Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Analysis And Management Plan
F857 Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Analysis And Management PlanThis slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls Increase audience engagement and knowledge by dispensing information using F857 Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Analysis And Management Plan. This template helps you present information on five stages. You can also present information on Mitigation, Strategies, Information Breach using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Risk Management Icon To Avoid Data Breaches
Cyber Risk Management Icon To Avoid Data BreachesPresenting our set of slides with name Cyber Risk Management Icon To Avoid Data Breaches. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Management, Cyber Risk, Data Breaches.
-
 Breach risk incident response plan ppt powerpoint presentation design cpb
Breach risk incident response plan ppt powerpoint presentation design cpbPresenting this set of slides with name Breach Risk Incident Response Plan Ppt Powerpoint Presentation Design Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Breach Risk Incident Response Plan to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Risk management worksheet security breach ppt powerpoint outline
Risk management worksheet security breach ppt powerpoint outlineThe risk management worksheet will help in keeping the track of various issues concerns that are existing in the firm by looking at the initial level of risk associated with them and the residual risk that is the amount of risk which remains after the inherited risk which the firm has tried to reduce through risk control measures. Presenting this set of slides with name Risk Management Worksheet Security Breach Ppt Powerpoint Outline. The topics discussed in these slides are Risk Management, Worksheet Security, Breach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Security breach risk management model
Security breach risk management modelThis slide exhibits data breach risk management model. It includes major evaluation criteria such as- does the management has two unique credentials to perform administer activities, does the multifactor authentication is enabled for administrative access etc. Introducing our Security Breach Risk Management Model set of slides. The topics discussed in these slides are Asset, Control Topic, Evaluation Questions, Response, Threat. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber security it detail impact cyber security plan can reduce the risk of data breach in organization
Cyber security it detail impact cyber security plan can reduce the risk of data breach in organizationThis slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver an outstanding presentation on the topic using this Cyber Security IT Detail Impact Cyber Security Plan Can Reduce The Risk Of Data Breach In Organization. Dispense information and present a thorough explanation of Detail Impact It Security It Plan Can Reduce The Risk Of Data Breach In Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Detail impact security awareness training can reduce the risk of a data breach misconfiguration ppt icons
Detail impact security awareness training can reduce the risk of a data breach misconfiguration ppt iconsThis slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen lost devices or records and inadvertent disclosure. Present the topic in a bit more detail with this Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Misconfiguration Ppt Icons. Use it as a tool for discussion and navigation on System Misconfiguration, Stolen Lost Device Or Records, Inadvertent Disclosure. This template is free to edit as deemed fit for your organization. Therefore download it now.



