Powerpoint Templates and Google slides for Automation In Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Unified Platform Integration For Security Automation Enabling Automation In Cyber Security Operations
Unified Platform Integration For Security Automation Enabling Automation In Cyber Security OperationsThis slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. Present the topic in a bit more detail with this Unified Platform Integration For Security Automation Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Automation, Access Management, Platform Integration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Why To Automate The It Security Process Enabling Automation In Cyber Security Operations
Why To Automate The It Security Process Enabling Automation In Cyber Security OperationsThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Increase audience engagement and knowledge by dispensing information using Why To Automate The It Security Process Enabling Automation In Cyber Security Operations. This template helps you present information on five stages. You can also present information on Better Threat Detection, Faster Containment, Improve Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 F651 Security Automation In Information Technology Security Automation Architecture With Key Elements
F651 Security Automation In Information Technology Security Automation Architecture With Key ElementsThis slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Present the topic in a bit more detail with this F651 Security Automation In Information Technology Security Automation Architecture With Key Elements. Use it as a tool for discussion and navigation on Security, Automation, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F653 Security Automation In Information Technology Security Automation Stages With Maturity Level
F653 Security Automation In Information Technology Security Automation Stages With Maturity LevelThis slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Present the topic in a bit more detail with this F653 Security Automation In Information Technology Security Automation Stages With Maturity Level. Use it as a tool for discussion and navigation on Systematic Stage, Institutionalized Stage, Opportunistic Stage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Architecture With Key Elements Enabling Automation In Cyber Security Operations
Security Automation Architecture With Key Elements Enabling Automation In Cyber Security OperationsThis slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Deliver an outstanding presentation on the topic using this Security Automation Architecture With Key Elements Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Automation, Architecture, Sources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Automation In Information Technology Domain Security Controls That Can Be Automated
Security Automation In Information Technology Domain Security Controls That Can Be AutomatedThis slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Present the topic in a bit more detail with this Security Automation In Information Technology Domain Security Controls That Can Be Automated. Use it as a tool for discussion and navigation on Information Security, Organization, Operations Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
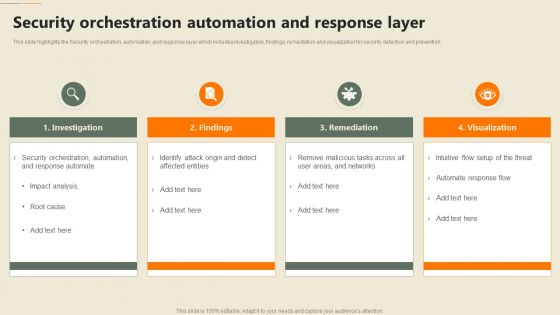 Security Automation In Information Technology Security Orchestration Automation And Response Layer
Security Automation In Information Technology Security Orchestration Automation And Response LayerThis slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention Increase audience engagement and knowledge by dispensing information using Security Automation In Information Technology Security Orchestration Automation And Response Layer. This template helps you present information on four stages. You can also present information on Investigation, Remediation, Visualization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Right Time To Add Automation In Security Security Automation To Investigate And Remediate Cyberthreats
Right Time To Add Automation In Security Security Automation To Investigate And Remediate CyberthreatsThis slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. Present the topic in a bit more detail with this Right Time To Add Automation In Security Security Automation To Investigate And Remediate Cyberthreats. Use it as a tool for discussion and navigation on Individual Insights, Automation, Security Personnels. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agenda For Security Automation In Information Technology
Agenda For Security Automation In Information TechnologyIncrease audience engagement and knowledge by dispensing information using Agenda For Security Automation In Information Technology. This template helps you present information on six stages. You can also present information on Business, Process, Importance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine Ideal Tasks For Security Automation Security Automation In Information Technology
Determine Ideal Tasks For Security Automation Security Automation In Information Technologyslide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Present the topic in a bit more detail with this Determine Ideal Tasks For Security Automation Security Automation In Information Technology. Use it as a tool for discussion and navigation on Security Automation, Determine, Sensitive Tasks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Security Automation Tools With Pros And Cons Security Automation In Information Technology
Different Security Automation Tools With Pros And Cons Security Automation In Information TechnologyThis slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM Deliver an outstanding presentation on the topic using this Different Security Automation Tools With Pros And Cons Security Automation In Information Technology. Dispense information and present a thorough explanation of Automation, Security Orchestration, Process Automation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Network It Security Automation Security Automation In Information Technology
Enterprise Network It Security Automation Security Automation In Information TechnologyThis slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Increase audience engagement and knowledge by dispensing information using Enterprise Network It Security Automation Security Automation In Information Technology. This template helps you present information on six stages. You can also present information on Orchestrating Network Security, Security Policy Automation, Infrastructure using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
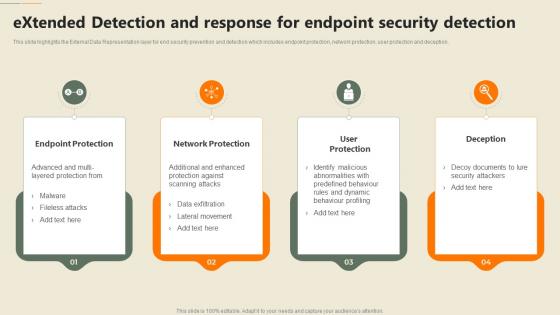 Extended Detection And Response For Endpoint Security Detection Security Automation In Information Technology
Extended Detection And Response For Endpoint Security Detection Security Automation In Information TechnologyThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Increase audience engagement and knowledge by dispensing information using Extended Detection And Response For Endpoint Security Detection Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Endpoint Protection, Network Protection, Deception using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide Security Automation In Information Technology
Icons Slide Security Automation In Information TechnologyPresent the topic in a bit more detail with this Icons Slide Security Automation In Information Technology. Use it as a tool for discussion and navigation on Icons. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
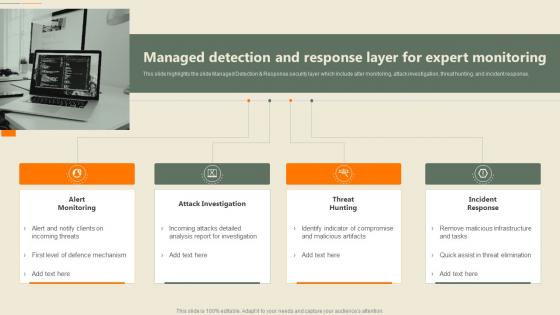 Managed Detection And Response Layer For Expert Monitoring Security Automation In Information Technology
Managed Detection And Response Layer For Expert Monitoring Security Automation In Information TechnologyThis slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response Increase audience engagement and knowledge by dispensing information using Managed Detection And Response Layer For Expert Monitoring Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Attack Investigation, Incident Response, Threat Hunting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Measure Security Automation Metrics For Operations Efficiency Security Automation In Information Technology
Measure Security Automation Metrics For Operations Efficiency Security Automation In Information TechnologyThis slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Present the topic in a bit more detail with this Measure Security Automation Metrics For Operations Efficiency Security Automation In Information Technology. Use it as a tool for discussion and navigation on Automation, Operations Efficiency, Performance Improvements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Right Time To Add Automation In Security Security Automation In Information Technology
Right Time To Add Automation In Security Security Automation In Information TechnologyThis slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. Deliver an outstanding presentation on the topic using this Right Time To Add Automation In Security Security Automation In Information Technology. Dispense information and present a thorough explanation of Individual, Insights, Automation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
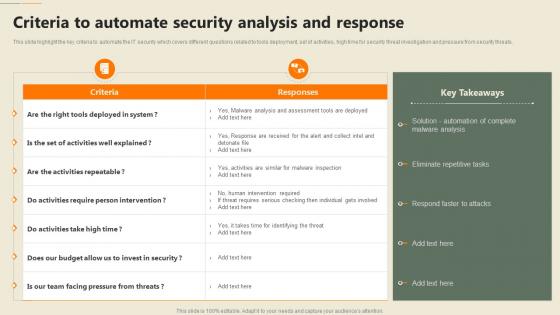 Security Automation In Information Technology Criteria To Automate Security Analysis And Response
Security Automation In Information Technology Criteria To Automate Security Analysis And ResponseThis slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Present the topic in a bit more detail with this Security Automation In Information Technology Criteria To Automate Security Analysis And Response. Use it as a tool for discussion and navigation on Analysis, Eliminate Repetitive Tasks, Respond Faster To Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation In Information Technology Impacts Of Ineffective Information Technology Security
Security Automation In Information Technology Impacts Of Ineffective Information Technology SecurityThis slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Increase audience engagement and knowledge by dispensing information using Security Automation In Information Technology Impacts Of Ineffective Information Technology Security. This template helps you present information on five stages. You can also present information on Information, Technology, Automation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Security Automation In Information Technology Table Of Contents
Security Automation In Information Technology Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Security Automation In Information Technology Table Of Contents. This template helps you present information on one stages. You can also present information on Security Automation, Processes, Security Detection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Security Automation Integrates Tools Systems And Processes Security Automation In Information Technology
Security Automation Integrates Tools Systems And Processes Security Automation In Information TechnologyThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Increase audience engagement and knowledge by dispensing information using Security Automation Integrates Tools Systems And Processes Security Automation In Information Technology. This template helps you present information on eight stages. You can also present information on Automation, Integrates, Processes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Security Processes That Cant Be Automated Security Automation In Information Technology
Security Processes That Cant Be Automated Security Automation In Information TechnologyThe following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Increase audience engagement and knowledge by dispensing information using Security Processes That Cant Be Automated Security Automation In Information Technology. This template helps you present information on three stages. You can also present information on Threat Modeling, Penetration Testing, Bug Bounty using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents Security Automation In Information Technology
Table Of Contents Security Automation In Information TechnologyPresent the topic in a bit more detail with this Table Of Contents Security Automation In Information Technology. Use it as a tool for discussion and navigation on Security Automation, Architecture And Importance, Automation Dashboards. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Unified Platform Integration For Security Automation Security Automation In Information Technology
Unified Platform Integration For Security Automation Security Automation In Information TechnologyThis slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. Increase audience engagement and knowledge by dispensing information using Unified Platform Integration For Security Automation Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Access Management, Security Automation, Firewalls using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Why To Automate The It Security Process Security Automation In Information Technology
Why To Automate The It Security Process Security Automation In Information TechnologyThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Increase audience engagement and knowledge by dispensing information using Why To Automate The It Security Process Security Automation In Information Technology. This template helps you present information on five stages. You can also present information on Better Threat Detection, Faster Containment, Improve Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 AI Security Concerns In Powerpoint And Google Slides Cpb
AI Security Concerns In Powerpoint And Google Slides CpbPresenting AI Security Concerns In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like AI Security Concerns. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
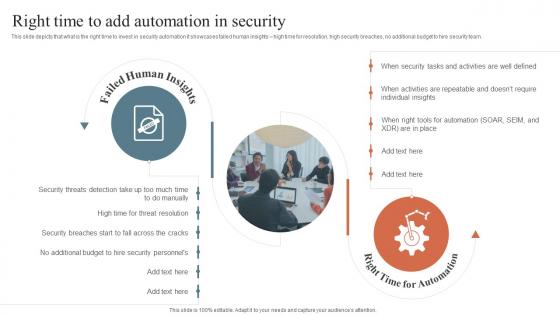 Right Time To Add Automation In Security Security Orchestration Automation And Response Guide
Right Time To Add Automation In Security Security Orchestration Automation And Response GuideThis slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. Introducing Right Time To Add Automation In Security Security Orchestration Automation And Response Guide to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Failed Human Insights, Right Time For Automation, Automation In Security, using this template. Grab it now to reap its full benefits.
-
 Inclusion Of Automation In Enterprise Security Operations
Inclusion Of Automation In Enterprise Security OperationsThis slide covers inclusion of automation in enterprise security operations. It involves key roles such as automation, security analysts, incident responder, threat hunter and security operation manager. Presenting our well structured Inclusion Of Automation In Enterprise Security Operations. The topics discussed in this slide are Security Analyst, Incident Responder, Security Operation Manager. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Role Of Automation In Improving Enterprise Security Operation
Role Of Automation In Improving Enterprise Security OperationThis slide covers role of automation in improving enterprise security operation. It involves AI powered threat detection, integrated threat intelligence and alert validation and noise reduction. Presenting our set of slides with Role Of Automation In Improving Enterprise Security Operation. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on AI Powered Threat Detection, Integrated Threat Intelligence, Alert Validation And Noise Reduction.
-
 IT In Manufacturing Industry Role Of Cyber Security In Manufacturing Automation
IT In Manufacturing Industry Role Of Cyber Security In Manufacturing AutomationThis slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Present the topic in a bit more detail with this IT In Manufacturing Industry Role Of Cyber Security In Manufacturing Automation. Use it as a tool for discussion and navigation on Threat And Risk Analysis, Network Security Evaluation, Workshops And Trainings. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 AI Security Risks In Powerpoint And Google Slides Cpb
AI Security Risks In Powerpoint And Google Slides CpbPresenting our AI Security Risks In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on AI Security Risks. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Smart Manufacturing Role Of Cyber Security In Manufacturing Automation
Smart Manufacturing Role Of Cyber Security In Manufacturing AutomationThis slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Present the topic in a bit more detail with this Smart Manufacturing Role Of Cyber Security In Manufacturing Automation. Use it as a tool for discussion and navigation on Manufacturing, Automation, Measures. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managing Cyber Security In Manufacturing 30 Days Plan Automation In Manufacturing IT
Managing Cyber Security In Manufacturing 30 Days Plan Automation In Manufacturing ITThis slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time and teams who are responsible and details. Present the topic in a bit more detail with this Managing Cyber Security In Manufacturing 30 Days Plan Automation In Manufacturing IT. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing Reporting, Phishing Repeat Offenders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managing Cyber Security In Manufacturing 60 Days Plan Automation In Manufacturing IT
Managing Cyber Security In Manufacturing 60 Days Plan Automation In Manufacturing ITThis slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Deliver an outstanding presentation on the topic using this Managing Cyber Security In Manufacturing 60 Days Plan Automation In Manufacturing IT. Dispense information and present a thorough explanation of Policy Violations, Data Loss Incidents, Infected Computers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managing Cyber Security In Manufacturing 90 Days Plan Automation In Manufacturing IT
Managing Cyber Security In Manufacturing 90 Days Plan Automation In Manufacturing ITThis slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Present the topic in a bit more detail with this Managing Cyber Security In Manufacturing 90 Days Plan Automation In Manufacturing IT. Use it as a tool for discussion and navigation on Training Completion, Communication Methods, Policy Sign Off. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Role Of Cyber Security In Manufacturing Automation Automation In Manufacturing IT
Role Of Cyber Security In Manufacturing Automation Automation In Manufacturing ITThis slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Present the topic in a bit more detail with this Role Of Cyber Security In Manufacturing Automation Automation In Manufacturing IT. Use it as a tool for discussion and navigation on Unauthorized Access, Operational Disruption, Intellectual Property Theft. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Use Of AI In Banking Industry To Improve Security
Use Of AI In Banking Industry To Improve SecurityThis slide signifies the use of artificial intelligence in banking sector to improve security. It covers information about enhancing customer interaction, improve efficiency and increase security and risk control. Presenting our well structured Use Of AI In Banking Industry To Improve Security. The topics discussed in this slide are Potential Areas, Opportunities In Banking, Enhance Customer Interaction. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Steps To Implement Cyber Security Automation In Secops
Steps To Implement Cyber Security Automation In SecopsThis slide outline the security operations automation process that enables to ease of the burden of cybersecurity organizations by automating repetitive tasks. It includes determine standard operating procedures SOPs , analyse tools, verify existing API connectors, etc. Presenting our set of slides with Steps To Implement Cyber Security Automation In Secops. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Analyse Tools, Progressive Automation, Enhance Processes.
-
 Role Of Cyber Security In Manufacturing Automation 3d Printing In Manufacturing
Role Of Cyber Security In Manufacturing Automation 3d Printing In ManufacturingThis slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Deliver an outstanding presentation on the topic using this Role Of Cyber Security In Manufacturing Automation 3d Printing In Manufacturing. Dispense information and present a thorough explanation of Unauthorized Access, Operational Disruption, Intellectual Property Theft using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Automation Home Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Automation Home Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon is perfect for Smart Home presentations. It features a modern, sleek design with a vibrant blue and white colour scheme. It will help to bring your slides to life and make your presentation stand out. It is easy to use and will help to make your presentation look professional.
-
 Automation Home Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Automation Home Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is perfect for presentations on smart home technology. It is a simple, modern design that is easy to incorporate into any presentation. It is a great visual aid to help explain the concept of a smart home and its various features.
-
 IoT In Manufacturing IT Role Of Cyber Security In Manufacturing Automation
IoT In Manufacturing IT Role Of Cyber Security In Manufacturing AutomationThis slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Deliver an outstanding presentation on the topic using this IoT In Manufacturing IT Role Of Cyber Security In Manufacturing Automation. Dispense information and present a thorough explanation of Security, Manufacturing, Automation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 RPA Uses In Oil And Energy Industry To Automate Security Checks
RPA Uses In Oil And Energy Industry To Automate Security ChecksThis slide presents robotic process automation in the oil, gas, and energy industry to improve reporting for trading and safety. It includes environmental safety reporting, drilling site reporting, and data processing, etc. Introducing our premium set of slides with RPA Uses In Oil And Energy Industry To Automate Security Checks Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Environment Health, Safety Reporting, Drilling, Site Reporting So download instantly and tailor it with your information.
-
 Home Security Home Automation System In Powerpoint And Google Slides Cpb
Home Security Home Automation System In Powerpoint And Google Slides CpbPresenting Home Security Home Automation System In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Home Security Home Automation System. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber security it how is automation used in cybersecurity ppt powerpoint clipart images
Cyber security it how is automation used in cybersecurity ppt powerpoint clipart imagesThis slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Introducing Cyber Security IT How Is Automation Used In Cybersecurity Ppt Powerpoint Clipart Images to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Threat Detection, Threat Response, Human Augmentation, using this template. Grab it now to reap its full benefits.




