Powerpoint Templates and Google slides for Automated Cyber
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Security Automation To Investigate And Remediate Cyberthreats Powerpoint Presentation Slides
Security Automation To Investigate And Remediate Cyberthreats Powerpoint Presentation SlidesThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Security Automation To Investigate And Remediate Cyberthreats Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of fourty three slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Enabling Automation In Cyber Security Operations Powerpoint Presentation Slides
Enabling Automation In Cyber Security Operations Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Enabling Automation In Cyber Security Operations Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fourty two slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Automation Ideas Mechanization Cyber Security Infrastructure Implement Technology Material
Automation Ideas Mechanization Cyber Security Infrastructure Implement Technology MaterialEnhance your audiences knowledge with this well researched complete deck. Showcase all the important features of the deck with perfect visuals. This deck comprises of total of ten slides with each slide explained in detail. Each template comprises of professional diagrams and layouts. Our professional PowerPoint experts have also included icons, graphs and charts for your convenience. All you have to do is DOWNLOAD the deck. Make changes as per the requirement. Yes, these PPT slides are completely customizable. Edit the colour, text and font size. Add or delete the content from the slide. And leave your audience awestruck with the professionally designed Automation Ideas Mechanization Cyber Security Infrastructure Implement Technology Material complete deck.
-
 IT In Manufacturing Industry V2 Role Of Cyber Security In Manufacturing Automation
IT In Manufacturing Industry V2 Role Of Cyber Security In Manufacturing AutomationThis slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Introducing IT In Manufacturing Industry V2 Role Of Cyber Security In Manufacturing Automation to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Network Security Evaluation, Threat And Risk Analysis, Workshops And Trainings, Product Testing And Certification, using this template. Grab it now to reap its full benefits.
-
 Automated Traffic Analytics For Cyber Security
Automated Traffic Analytics For Cyber SecurityThe following slide highlights challenges, essential technologies, and data sources to showcase automated traffic analytics for cybersecurity. It helps organizations enhance threat detection and response by leveraging automated traffic analysis. Introducing our premium set of slides with Automated Traffic Analytics For Cyber Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Learning, Analytics, Research. So download instantly and tailor it with your information.
-
 IoT Cyber Attack Scenario In Self Automated Improving IoT Device Cybersecurity IoT SS
IoT Cyber Attack Scenario In Self Automated Improving IoT Device Cybersecurity IoT SSPresent the topic in a bit more detail with this IoT Cyber Attack Scenario In Self Automated Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Systems, Updates, Connectivity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Role Of Cyber Security In Manufacturing Automation AI In Manufacturing
Role Of Cyber Security In Manufacturing Automation AI In ManufacturingThis slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Deliver an outstanding presentation on the topic using this Role Of Cyber Security In Manufacturing Automation AI In Manufacturing. Dispense information and present a thorough explanation of Unauthorized Access, Operational Disruption, Intellectual Property using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implement Automated Patch Management Solution Implementing Cyber Risk Management Process
Implement Automated Patch Management Solution Implementing Cyber Risk Management ProcessThe following slide showcases the automated patch management process to fix software vulnerabilities and ensure smooth functioning of systems. It includes activities such as scanning of systems, requesting to take back-up etc. Present the topic in a bit more detail with this Implement Automated Patch Management Solution Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Vulnerability Assessment, List Of Servers, Determine Missing Patches. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Essential Steps For Automated Cyber Incident Report Template
Essential Steps For Automated Cyber Incident Report TemplateThis slide highlights steps of cyber incident report template providing necessary information to handle cyber attacks better and efficiently. It includes phases such as record, remediate and report. Presenting our set of slides with Essential Steps For Automated Cyber Incident Report Template. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Record, Remediate, Essential.
-
 Implement Automated Patch Management Solution Cyber Risk Assessment
Implement Automated Patch Management Solution Cyber Risk AssessmentThe following slide showcases the automated patch management process to fix software vulnerabilities and ensure smooth functioning of systems. It includes activities such as scanning of systems, requesting to take back up etc. Present the topic in a bit more detail with this Implement Automated Patch Management Solution Cyber Risk Assessment Use it as a tool for discussion and navigation on Vulnerability Assessment, Asset Inventory, List Of Servers This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implement Automated Patch Management Solution Creating Cyber Security Awareness
Implement Automated Patch Management Solution Creating Cyber Security AwarenessThe following slide showcases the automated patch management process to fix software vulnerabilities and ensure smooth functioning of systems. It includes activities such as scanning of systems, requesting to take back-up etc. Present the topic in a bit more detail with this Implement Automated Patch Management Solution Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Cyber Attack Type, Ransomware Attacks This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Automated Traffic Analytics For Cyber Protection
Automated Traffic Analytics For Cyber ProtectionThe following slide highlights challenges, essential technologies, and data sources to showcase automated traffic analytics for cybersecurity. It helps organizations enhance threat detection and response by leveraging automated traffic analysis. Introducing our Automated Traffic Analytics For Cyber Protection set of slides. The topics discussed in these slides are Detection Of Breaches, Malware Evaluation, Challenges. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Implement Automated Patch Management Solution Implementing Strategies To Mitigate Cyber Security Threats
Implement Automated Patch Management Solution Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the automated patch management process to fix software vulnerabilities and ensure smooth functioning of systems. It includes activities such as scanning of systems, requesting to take back up etc. Present the topic in a bit more detail with this Implement Automated Patch Management Solution Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Vulnerability Assessment, Request Cancelled, Asset Inventory This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Smart Automation Robotics Cybersecurity Measures And Techniques Ensuring Safety RB SS
Smart Automation Robotics Cybersecurity Measures And Techniques Ensuring Safety RB SSThis slide present various cybersecurity measures techniques for ensuring to ensure the safety of technologies involved in the robotic deployment. It includes network segmentation, access control, and regular software updates. Introducing Smart Automation Robotics Cybersecurity Measures And Techniques Ensuring Safety RB SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Network Segmentation, Access Control, Regular Software Updates using this template. Grab it now to reap its full benefits.
-
 Impact Of ATP Cyber Security Automation
Impact Of ATP Cyber Security AutomationThis slide depicts the ATP cyber security automation to detect virus. Its aim is to help prevent the virus in the system. This slide includes prevention, detection and mitigate. Presenting our set of slides with name Impact Of ATP Cyber Security Automation. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Prevent, Detec, Mitigate.
-
 Stages Of Cyber Security And Compliance Automation
Stages Of Cyber Security And Compliance AutomationThis slide represents stages of cyber security and compliance automation which assists in cyber risk and policy adherence. It includes stages of cyber security and compliance automation such as initial, developing, define, etc. Presenting our set of slides with name Stages Of Cyber Security And Compliance Automation. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Stages Of Cyber Security, Compliance Automation, Developing, Risk And Policy Adherence.
-
 Cybersecurity Automation Tools To Enhance Data Protection
Cybersecurity Automation Tools To Enhance Data ProtectionThis slide represents various cybersecurity automation tools that help companies to enhance data protection from threats and vulnerabilities. It includes various tools such as sprint, quals, splunk, logpoint, etc. Introducing our premium set of slides with Cybersecurity Automation Tools To Enhance Data Protection Ellicudate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Features, Cybersecurity Automation, Data Protection So download instantly and tailor it with your information.
-
 Endpoint Cyber Security Automated Workflow
Endpoint Cyber Security Automated WorkflowThis slide lays out framework for automated workflow for endpoint cyber security process. The purpose of this slide is to secure organization network and assets against cyber threats. It covers processes such as collecting data, selecting security tools and deploying tools. Introducing our premium set of slides with Endpoint Cyber Security Automated Workflow Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Collect Data, Select Security Tools, Deploy Tools So download instantly and tailor it with your information.
-
 Cyber Deception Use Case In Automated Moving Target Defense
Cyber Deception Use Case In Automated Moving Target DefenseThe purpose of this slide is to illustrate a cyber deception use case in automated moving target defense, demonstrating its effectiveness in cloud security, hardware protection, etc. Presenting our set of slides with Cyber Deception Use Case In Automated Moving Target Defense. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Security, Hardware Protection, Host Endpoint Security.
-
 Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security Threat
Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about system patch management to determine vulnerabilities after cyber attack. It includes key process of automated patch management and best practices such as schedule patching, prioritization, and patch testing. Deliver an outstanding presentation on the topic using this Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Management, Process, Vulnerability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Automated Cyber Threat Hunting Overview
Automated Cyber Threat Hunting OverviewThis slide gives an overview of an automated cyber threat-hunting process that uses artificial intelligence and machine learning algorithms for threat detection. Increase audience engagement and knowledge by dispensing information using Automated Cyber Threat Hunting Overview. This template helps you present information on four stages. You can also present information on Automated Cyber, Threat Hunting Overview, Machine Learning Algorithms, Threat Detection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 AI Supply Chain Automation Icon To Prevent Cybersecurity Attacks
AI Supply Chain Automation Icon To Prevent Cybersecurity AttacksPresenting our well structured AI Supply Chain Automation Icon To Prevent Cybersecurity Attacks. The topics discussed in this slide are AI Supply Chain Automation Icon, Prevent Cybersecurity Attacks. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Current State Of Security Automation With Projected Development Enabling Automation In Cyber Security
Current State Of Security Automation With Projected Development Enabling Automation In Cyber SecurityThis slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. Deliver an outstanding presentation on the topic using this Current State Of Security Automation With Projected Development Enabling Automation In Cyber Security. Dispense information and present a thorough explanation of Automation, Development, Organizations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enabling Automation In Cyber Security Operations Time To Fix Security Threat With Manual Testing
Enabling Automation In Cyber Security Operations Time To Fix Security Threat With Manual TestingThis slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Present the topic in a bit more detail with this Enabling Automation In Cyber Security Operations Time To Fix Security Threat With Manual Testing. Use it as a tool for discussion and navigation on Manual, Testing, Security Threat. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Dashboard Highlighting Resolved Events And Workload Enabling Automation In Cyber Security
Security Automation Dashboard Highlighting Resolved Events And Workload Enabling Automation In Cyber SecurityThis slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions. Deliver an outstanding presentation on the topic using this Security Automation Dashboard Highlighting Resolved Events And Workload Enabling Automation In Cyber Security. Dispense information and present a thorough explanation of Dashboard, Security Automation, Workload using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Automation Dashboard Highlighting Network Enabling Automation In Cyber Security Operations
Security Automation Dashboard Highlighting Network Enabling Automation In Cyber Security OperationsThis slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Present the topic in a bit more detail with this Security Automation Dashboard Highlighting Network Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Automation, Dashboard, Highlighting. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Current State Of Security Automation Projected Security Automation To Investigate And Remediate Cyberthreats
Current State Of Security Automation Projected Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. Deliver an outstanding presentation on the topic using this Current State Of Security Automation Projected Security Automation To Investigate And Remediate Cyberthreats. Dispense information and present a thorough explanation of Automation, Development, Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Automation Dashboard Highlighting Resolved Security Automation To Investigate And Remediate Cyberthreats
Security Automation Dashboard Highlighting Resolved Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions. Present the topic in a bit more detail with this Security Automation Dashboard Highlighting Resolved Security Automation To Investigate And Remediate Cyberthreats. Use it as a tool for discussion and navigation on Automation, Dashboard, Workload. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation To Investigate And Remediate Cyberthreats Security Automation Dashboard Highlighting Network
Security Automation To Investigate And Remediate Cyberthreats Security Automation Dashboard Highlighting NetworkThis slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Present the topic in a bit more detail with this Security Automation To Investigate And Remediate Cyberthreats Security Automation Dashboard Highlighting Network. Use it as a tool for discussion and navigation on Automation, Dashboard, Incident Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Time To Fix Security Threat With Manual Testing Security Automation To Investigate And Remediate Cyberthreats
Time To Fix Security Threat With Manual Testing Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Deliver an outstanding presentation on the topic using this Time To Fix Security Threat With Manual Testing Security Automation To Investigate And Remediate Cyberthreats. Dispense information and present a thorough explanation of Security, Threat, Manual Testing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ai based automation of cyber threat security controls
Ai based automation of cyber threat security controlsThe following slide highlights the threat security controls which are integrated with artificial intelligence which includes RPA and ML. Introducing our AI Based Automation Of Cyber Threat Security Controls set of slides. The topics discussed in these slides are Cyber Threat Security, Automated Control Management, Control And Vulnerability Reporting. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Eliminating Manual Security Processes Through Automation Risk Based Methodology To Cyber
Eliminating Manual Security Processes Through Automation Risk Based Methodology To CyberMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools.Present the topic in a bit more detail with this Eliminating Manual Security Processes Through Automation Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Manual Vulnerability, Scanning And Resolution, Vulnerability Scanning This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 About Us Security Automation To Investigate And Remediate Cyberthreats
About Us Security Automation To Investigate And Remediate CyberthreatsIntroducing About Us Security Automation To Investigate And Remediate Cyberthreats to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on About Us, using this template. Grab it now to reap its full benefits.
-
 Financial Security Automation To Investigate And Remediate Cyberthreats
Financial Security Automation To Investigate And Remediate CyberthreatsIncrease audience engagement and knowledge by dispensing information using Financial Security Automation To Investigate And Remediate Cyberthreats. This template helps you present information on three stages. You can also present information on Financial using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Our Mission Security Automation To Investigate And Remediate Cyberthreats
Our Mission Security Automation To Investigate And Remediate CyberthreatsIntroducing Our Mission Security Automation To Investigate And Remediate Cyberthreats to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Our Mission, using this template. Grab it now to reap its full benefits.
-
 Quotes Security Automation To Investigate And Remediate Cyberthreats
Quotes Security Automation To Investigate And Remediate CyberthreatsIncrease audience engagement and knowledge by dispensing information using Quotes Security Automation To Investigate And Remediate Cyberthreats. This template helps you present information on one stages. You can also present information on Quotes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Thanks For Watching Security Automation To Investigate And Remediate Cyberthreats
Thanks For Watching Security Automation To Investigate And Remediate CyberthreatsIntroducing Thanks For Watching Security Automation To Investigate And Remediate Cyberthreats to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Thanks For Watching, using this template. Grab it now to reap its full benefits.
-
 Agenda Enabling Automation In Cyber Security Operations Ppt Slides Background Images
Agenda Enabling Automation In Cyber Security Operations Ppt Slides Background ImagesIntroducing Agenda Enabling Automation In Cyber Security Operations Ppt Slides Background Images to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Environment, Business, Process, using this template. Grab it now to reap its full benefits.
-
 Criteria To Automate Security Analysis And Response Enabling Automation In Cyber Security Operations
Criteria To Automate Security Analysis And Response Enabling Automation In Cyber Security OperationsThis slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Present the topic in a bit more detail with this Criteria To Automate Security Analysis And Response Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Intervention, Malware Analysis, Automate. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Security Automation Tools With Pros And Cons Enabling Automation In Cyber Security Operations
Different Security Automation Tools With Pros And Cons Enabling Automation In Cyber Security OperationsThis slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Present the topic in a bit more detail with this Different Security Automation Tools With Pros And Cons Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Information, Management, Automation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enabling Automation In Cyber Security Operations Determine Ideal Tasks For Security Automation
Enabling Automation In Cyber Security Operations Determine Ideal Tasks For Security AutomationThis slide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Deliver an outstanding presentation on the topic using this Enabling Automation In Cyber Security Operations Determine Ideal Tasks For Security Automation. Dispense information and present a thorough explanation of Automation, Individual, Takeaways Section using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enabling Automation In Cyber Security Operations Domain Security Controls That Can Be Automated
Enabling Automation In Cyber Security Operations Domain Security Controls That Can Be AutomatedThis slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Present the topic in a bit more detail with this Enabling Automation In Cyber Security Operations Domain Security Controls That Can Be Automated. Use it as a tool for discussion and navigation on Communication, Management, Human Resources. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enabling Automation In Cyber Security Operations Table Of Contents Ppt Slides Infographic Template
Enabling Automation In Cyber Security Operations Table Of Contents Ppt Slides Infographic TemplateDeliver an outstanding presentation on the topic using this Enabling Automation In Cyber Security Operations Table Of Contents Ppt Slides Infographic Template. Dispense information and present a thorough explanation of Protection Platform, Security Automation, Processes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Network It Security Automation Enabling Automation In Cyber Security Operations
Enterprise Network It Security Automation Enabling Automation In Cyber Security OperationsThis slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Deliver an outstanding presentation on the topic using this Enterprise Network It Security Automation Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Orchestrating Network Security, Troubleshooting, Integrating Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Extended Detection And Response For Endpoint Security Enabling Automation In Cyber Security Operations
Extended Detection And Response For Endpoint Security Enabling Automation In Cyber Security OperationsThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deceptio Increase audience engagement and knowledge by dispensing information using Extended Detection And Response For Endpoint Security Enabling Automation In Cyber Security Operations. This template helps you present information on four stages. You can also present information on Endpoint Protection, Network Protection, User Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Enabling Automation In Cyber Security Operations Ppt Slides Background Designs
Icons Slide For Enabling Automation In Cyber Security Operations Ppt Slides Background DesignsDeliver an outstanding presentation on the topic using this Icons Slide For Enabling Automation In Cyber Security Operations Ppt Slides Background Designs. Dispense information and present a thorough explanation of Icons using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security Operations
Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security OperationsThis slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Increase audience engagement and knowledge by dispensing information using Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security Operations. This template helps you present information on four stages. You can also present information on Ineffective, Information, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Managed Detection And Response Layer For Expert Monitoring Enabling Automation In Cyber Security Operations
Managed Detection And Response Layer For Expert Monitoring Enabling Automation In Cyber Security OperationsThis slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. Introducing Managed Detection And Response Layer For Expert Monitoring Enabling Automation In Cyber Security Operations to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Alert Monitoring, Attack Investigation, Threat Hunting, using this template. Grab it now to reap its full benefits.
-
 Measure Security Automation Metrics For Operations Efficiency Enabling Automation In Cyber Security Operations
Measure Security Automation Metrics For Operations Efficiency Enabling Automation In Cyber Security OperationsThis slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Present the topic in a bit more detail with this Measure Security Automation Metrics For Operations Efficiency Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Automation, Operations, Efficiency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Right Time To Add Automation In Security Enabling Automation In Cyber Security Operations
Right Time To Add Automation In Security Enabling Automation In Cyber Security OperationsThis slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. Present the topic in a bit more detail with this Right Time To Add Automation In Security Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Resolution, Automation, Human Insights. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations
Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security OperationsThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Present the topic in a bit more detail with this Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Automation, Integrates, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Stages With Maturity Level Enabling Automation In Cyber Security Operations
Security Automation Stages With Maturity Level Enabling Automation In Cyber Security OperationsThis slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Deliver an outstanding presentation on the topic using this Security Automation Stages With Maturity Level Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Security Automation, Services, Programmatic Workflow using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
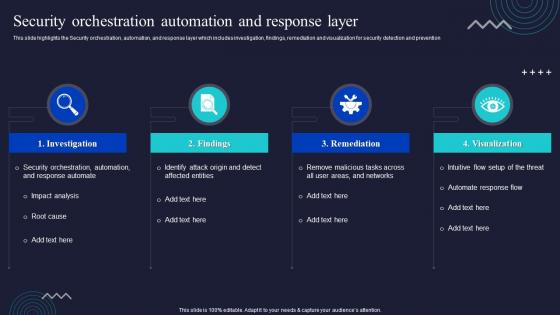 Security Orchestration Automation And Response Layer Enabling Automation In Cyber Security Operations
Security Orchestration Automation And Response Layer Enabling Automation In Cyber Security OperationsThis slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention Deliver an outstanding presentation on the topic using this Security Orchestration Automation And Response Layer Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Investigation, Remediation, Visualization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Processes That Cant Be Automated Enabling Automation In Cyber Security Operations
Security Processes That Cant Be Automated Enabling Automation In Cyber Security OperationsThe following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Increase audience engagement and knowledge by dispensing information using Security Processes That Cant Be Automated Enabling Automation In Cyber Security Operations. This template helps you present information on three stages. You can also present information on Threat Modeling, Penetration Testing, Bug Bounty using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents Enabling Automation In Cyber Security Operations Ppt Slides Background Image
Table Of Contents Enabling Automation In Cyber Security Operations Ppt Slides Background ImageIntroducing Table Of Contents Enabling Automation In Cyber Security Operations Ppt Slides Background Image to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Security Automation, Architecture And Importance, Security Automation Dashboards, using this template. Grab it now to reap its full benefits.
-
 Unified Platform Integration For Security Automation Enabling Automation In Cyber Security Operations
Unified Platform Integration For Security Automation Enabling Automation In Cyber Security OperationsThis slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. Present the topic in a bit more detail with this Unified Platform Integration For Security Automation Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Automation, Access Management, Platform Integration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Why To Automate The It Security Process Enabling Automation In Cyber Security Operations
Why To Automate The It Security Process Enabling Automation In Cyber Security OperationsThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Increase audience engagement and knowledge by dispensing information using Why To Automate The It Security Process Enabling Automation In Cyber Security Operations. This template helps you present information on five stages. You can also present information on Better Threat Detection, Faster Containment, Improve Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Automation Architecture With Key Elements Enabling Automation In Cyber Security Operations
Security Automation Architecture With Key Elements Enabling Automation In Cyber Security OperationsThis slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Deliver an outstanding presentation on the topic using this Security Automation Architecture With Key Elements Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Automation, Architecture, Sources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Different Security Automation Tools With Pros Security Automation To Investigate And Remediate Cyberthreats
Different Security Automation Tools With Pros Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Present the topic in a bit more detail with this Different Security Automation Tools With Pros Security Automation To Investigate And Remediate Cyberthreats. Use it as a tool for discussion and navigation on Automation, Security Orchestration, Response. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
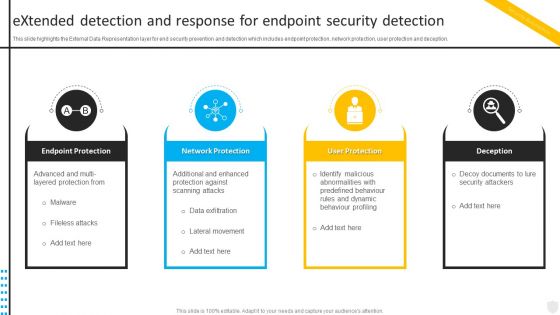 Extended Detection And Response For Endpoint Security Automation To Investigate And Remediate Cyberthreats
Extended Detection And Response For Endpoint Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Introducing Extended Detection And Response For Endpoint Security Automation To Investigate And Remediate Cyberthreats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Endpoint Protection, Network Protection, User Protection, using this template. Grab it now to reap its full benefits.




