Powerpoint Templates and Google slides for Attack Works
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Working Of Denial Of Service Or Dos Attacks Training Ppt
Working Of Denial Of Service Or Dos Attacks Training PptPresenting Working of Denial of Service or DoS Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
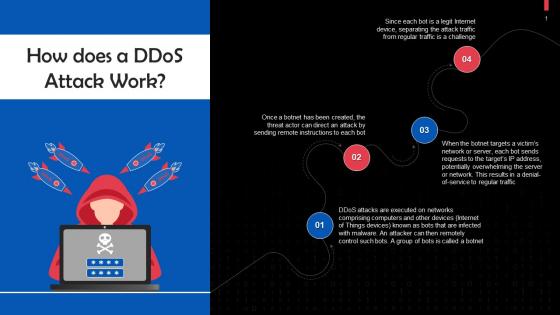 Working Of Distributed Denial Of Service Or DDoS Attacks Training Ppt
Working Of Distributed Denial Of Service Or DDoS Attacks Training PptPresenting Working of Distributed Denial of Service or DDoS Attacks . This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Working Of Man In The Middle Attacks Training Ppt
Working Of Man In The Middle Attacks Training PptPresenting Working of Man in the Middle Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
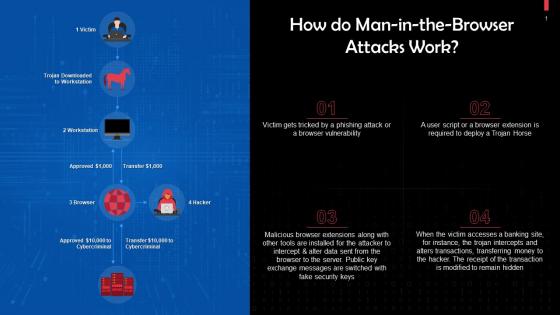 Working Of Man In The Browser Attacks Training Ppt
Working Of Man In The Browser Attacks Training PptPresenting Working of Man in the Browser Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Overview Of Working Of Ransomware Attacks Training Ppt
Overview Of Working Of Ransomware Attacks Training PptPresenting Overview of Working of Ransomware Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Working Of Spam And Phishing Attacks Training Ppt
Working Of Spam And Phishing Attacks Training PptPresenting Working of Spam and Phishing Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 How Blockchain DDoS Attacks Work Training Ppt
How Blockchain DDoS Attacks Work Training PptPresenting How Blockchain DDoS Attacks Work. Our PowerPoint experts have included all the necessary templates, designs, icons, graphs, and other essential material. This deck is well crafted by extensive research. Slides consist of amazing visuals and appropriate content. These PPT slides can be instantly downloaded with just a click. Compatible with all screen types and monitors. Supports Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Data Breach Prevention Working Steps Of Data Breach Attack Cycle
Data Breach Prevention Working Steps Of Data Breach Attack CycleThis slide explains the phases of the data breach attack cycle to gain unauthorized access to sensitive information. The steps involved are reconnaissance, intrusion and presence, lateral migration, using data for personal benefits, demanding a ransom, etc. Introducing Data Breach Prevention Working Steps Of Data Breach Attack Cycle to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reconnaissance, Intrusion And Presence, Lateral Migration, Exfiltration , using this template. Grab it now to reap its full benefits.
-
 Types Of Attacks On Proof Of Work System Complete Guide On How Blockchain BCT SS
Types Of Attacks On Proof Of Work System Complete Guide On How Blockchain BCT SSThis slide mentions the various types of attacks that can be encountered on proof of work system used for blockchain mining and their corresponding description and solutions. Attacks mentioned include Sybil attacks and Denial of Service attacks. Present the topic in a bit more detail with this Types Of Attacks On Proof Of Work System Complete Guide On How Blockchain BCT SS. Use it as a tool for discussion and navigation on Description, Solutions, Denial Of Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 K107 Working Process Of Cyber Phishing Attacks Phishing Attacks And Strategies To Mitigate Them V2
K107 Working Process Of Cyber Phishing Attacks Phishing Attacks And Strategies To Mitigate Them V2This slide talks about the implementation and working of phishing attacks. The purpose of this slide is to explain how are cyber phishing scams conducted. The components include hacker, phishing mail, target, phishing website and original website. Introducing K107 Working Process Of Cyber Phishing Attacks Phishing Attacks And Strategies To Mitigate Them V2 to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Working Process, Cyber Phishing Attacks, Phishing Website, Cyber Phishing Scams Conducted, using this template. Grab it now to reap its full benefits.
-
 K108 Working Process Of Evil Twin Phishing Attack Phishing Attacks And Strategies To Mitigate Them V2
K108 Working Process Of Evil Twin Phishing Attack Phishing Attacks And Strategies To Mitigate Them V2This slide represents the working of evil twin phishing attacks. The key points include set up evil twin fake access point, set up a fake captive portal, push users to sign into evil twin wi-fi and steal victims personal information and login credentials. Increase audience engagement and knowledge by dispensing information using K108 Working Process Of Evil Twin Phishing Attack Phishing Attacks And Strategies To Mitigate Them V2. This template helps you present information on four stages. You can also present information on Steal Victims Personal Information, Twin Fake Access Point, Fake Captive Portal using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Angler Phishing Working And Example
Phishing Attacks And Strategies To Mitigate Them V2 About Angler Phishing Working And ExampleThis slide talks about the angler phishing attacks conducted on internet using social media platforms. The purpose of this slide is to illustrate how fraudulent tweets or texts containing malicious links and misleading information, can be used by scammers to trick individuals. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 About Angler Phishing Working And Example. Use it as a tool for discussion and navigation on Angler Phishing Attacks, Social Media Platforms, Fraudulent Tweets, Texts Containing Malicious, Misleading Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Smishing Attacks Working And Example
Phishing Attacks And Strategies To Mitigate Them V2 About Smishing Attacks Working And ExampleThis slide talks about the smishing cyber attacks conducted by sending text messages to the targets. The purpose of this slide is to illustrate how fraudulent texts are sent to the users which contains malicious links and other mis-leading information. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 About Smishing Attacks Working And Example. This template helps you present information on three stages. You can also present information on Personal Information, Contains Malicious Link, Fraudulent Activities, Smishing Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 How Does A Phishing Attack Work
Phishing Attacks And Strategies To Mitigate Them V2 How Does A Phishing Attack WorkThis slide demonstrates the working flow of a phishing attack. The purpose of this slide is to outline the various phases of phishing scams such as campaign crafted, payloads, impersonation, execution, ransomware and encrypts on target. Introducing Phishing Attacks And Strategies To Mitigate Them V2 How Does A Phishing Attack Work to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Campaign Crafted, Payloads, Impersonation, Execution, Encrypts On Target, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 How Does Vishing Attack Works
Phishing Attacks And Strategies To Mitigate Them V2 How Does Vishing Attack WorksThis slide illustrates the working procedure of a vishing attack. The purpose of this slide is to explain the working flow of vishing cyber attack. The key components include attacker, target, spoofed caller ID, SMS to victim, file execution confirmation, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 How Does Vishing Attack Works. Use it as a tool for discussion and navigation on Execution Confirmation, Sending Confirmation, Vishing Attack Works. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Working Of Phishing Training Programs
Phishing Attacks And Strategies To Mitigate Them V2 Working Of Phishing Training ProgramsIntroducing Phishing Attacks And Strategies To Mitigate Them V2 Working Of Phishing Training Programs to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Start With Employee Training, Make Fictitious Phishing Campaigns, Track Progress And Upgrade, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Working Of Watering Hole Phishing Attack
Phishing Attacks And Strategies To Mitigate Them V2 Working Of Watering Hole Phishing AttackThis slide represents the working process of watering hole phishing attacks. The purpose of this slide is to illustrate the flow diagram of watering hole phishing scams. The key points include research and identification, analysis, preparation and execution. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Working Of Watering Hole Phishing Attack. This template helps you present information on four stages. You can also present information on Analysis, Research And Identification, Preparation, Execution, Phishing Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Working Procedure Of Spear Phishing Attack
Phishing Attacks And Strategies To Mitigate Them V2 Working Procedure Of Spear Phishing AttackThis slide illustrates the structure of spear phishing attack. The purpose of this slide is to explain the working flow of spear phishing attack. The key components include attacker, phishing email, targeted users, exploited system, internal network, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Working Procedure Of Spear Phishing Attack to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Email, Targeted Users, Exploited System, Internal Network, Attacker, using this template. Grab it now to reap its full benefits.
-
 How Does Dos Attack Work Improving IoT Device Cybersecurity IoT SS
How Does Dos Attack Work Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase working of Denial of Service DoS attack working. It covers information about target identification, exploiting weaknesses, target flooding, exhausting system capabilities Introducing How Does Dos Attack Work Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Target, Exploiting, Flooding, using this template. Grab it now to reap its full benefits.
-
 How Does IoT Botnet Attack Work Improving IoT Device Cybersecurity IoT SS
How Does IoT Botnet Attack Work Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase working of Internet of Things IoT botnet attack. The botnet attack begins with scanning vulnerable IoT devices, gaining access to IoT devices, malware installation, botnet expansion, and conducting malicious activities. Increase audience engagement and knowledge by dispensing information using How Does IoT Botnet Attack Work Improving IoT Device Cybersecurity IoT SS. This template helps you present information on five stages. You can also present information on Devices, Gaining, Installation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Does IoT Password Attack Work Improving IoT Device Cybersecurity IoT SS
How Does IoT Password Attack Work Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase working of Internet of Things IoT password attack. It covers information about gaining control of IoT device, records conversation, collects private video recordings, sends sensitive data to malicious user, etc. Present the topic in a bit more detail with this How Does IoT Password Attack Work Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Cybercriminal, Server, Default. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 How Does Ransomware Attack Work Improving IoT Device Cybersecurity IoT SS
How Does Ransomware Attack Work Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase the working of ransomware attack. The attack begins with installing malware in IoT devices, identifying files stored on local devices, establishing key exchange with control server, covering instruction files, etc. Increase audience engagement and knowledge by dispensing information using How Does Ransomware Attack Work Improving IoT Device Cybersecurity IoT SS. This template helps you present information on seven stages. You can also present information on Devices, Exchange, Covers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Does Phishing Attack Works On Blockchain Network Hands On Blockchain Security Risk BCT SS V
How Does Phishing Attack Works On Blockchain Network Hands On Blockchain Security Risk BCT SS VThe following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Present the topic in a bit more detail with this How Does Phishing Attack Works On Blockchain Network Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Attacker, Phishing Email, Internet Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview And Workflow Process Of Eclipse Attack Hands On Blockchain Security Risk BCT SS V
Overview And Workflow Process Of Eclipse Attack Hands On Blockchain Security Risk BCT SS VThe following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer-to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. Introducing Overview And Workflow Process Of Eclipse Attack Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Enabled Attack, Achieve Control, Incoming And Outgoing, using this template. Grab it now to reap its full benefits.
-
 Overview And Working Process Of Ddos Attack Hands On Blockchain Security Risk BCT SS V
Overview And Working Process Of Ddos Attack Hands On Blockchain Security Risk BCT SS VThe following slide illustrates brief introduction of distributed denial of service DDOS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc. Increase audience engagement and knowledge by dispensing information using Overview And Working Process Of Ddos Attack Hands On Blockchain Security Risk BCT SS V. This template helps you present information on four stages. You can also present information on Website Hostage, Close The Attack, Inability To Resolve using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview Of Blockchain 51 Percent Attack With Workflow Hands On Blockchain Security Risk BCT SS V
Overview Of Blockchain 51 Percent Attack With Workflow Hands On Blockchain Security Risk BCT SS VThe following slide showcases brief introduction of 51percentage attack to analyze hashing power of cryptocurrency users. It includes elements such at mining faster rate, malicious user, along with its workflow, etc. Introducing Overview Of Blockchain 51 Percent Attack With Workflow Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Blockchain Network, Public Network, using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity How Does Phishing Attack Works On Blockchain Network BCT SS V
Blockchain And Cybersecurity How Does Phishing Attack Works On Blockchain Network BCT SS VThe following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity How Does Phishing Attack Works On Blockchain Network BCT SS V This template helps you present information on Seven stages. You can also present information on Phishing Email, Internet Network, Dispense Email using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity Overview And Workflow Process Of Eclipse Attack BCT SS V
Blockchain And Cybersecurity Overview And Workflow Process Of Eclipse Attack BCT SS VThe following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer-to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. Present the topic in a bit more detail with this Blockchain And Cybersecurity Overview And Workflow Process Of Eclipse Attack BCT SS V Use it as a tool for discussion and navigation on Blockchain And Cybersecurity Overview And Workflow Process Of Eclipse Attack BCT SS V This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain And Cybersecurity Overview And Working Process Of Ddos Attack BCT SS V
Blockchain And Cybersecurity Overview And Working Process Of Ddos Attack BCT SS VThe following slide illustrates brief introduction of distributed denial of service DDoS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Overview And Working Process Of Ddos Attack BCT SS V This template helps you present information on Four stages. You can also present information on Attacker Controls Website Hostage, Perform Operations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity Overview Of Blockchain 51 Percent Attack With Workflow BCT SS V
Blockchain And Cybersecurity Overview Of Blockchain 51 Percent Attack With Workflow BCT SS VThe following slide showcases brief introduction of 51percent attack to analyze hashing power of cryptocurrency users. It includes elements such at mining faster rate, malicious user, along with its workflow, etc. Present the topic in a bit more detail with this Blockchain And Cybersecurity Overview Of Blockchain 51 Percent Attack With Workflow BCT SS V Use it as a tool for discussion and navigation on Public Blockchain, Public Network, Maximum Miners This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threats In Blockchain How Does Phishing Attack Works On Blockchain Network BCT SS V
Cyber Threats In Blockchain How Does Phishing Attack Works On Blockchain Network BCT SS VThe following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain How Does Phishing Attack Works On Blockchain Network BCT SS V This template helps you present information on Seven stages. You can also present information on Steals Data From User System, Obtains Information From System using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Threats In Blockchain Overview And Workflow Process Of Eclipse Attack BCT SS V
Cyber Threats In Blockchain Overview And Workflow Process Of Eclipse Attack BCT SS VThe following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer-to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. Introducing Cyber Threats In Blockchain Overview And Workflow Process Of Eclipse Attack BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Target Node, Attacker Nodes, Participating Nodes using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Overview And Working Process Of Ddos Attack BCT SS V
Cyber Threats In Blockchain Overview And Working Process Of Ddos Attack BCT SS VThe following slide illustrates brief introduction of distributed denial of service DDoS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Overview And Working Process Of Ddos Attack BCT SS V This template helps you present information on Three stages. You can also present information on Internet Traffic, Perform Operations, Website Hostage using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Threats In Blockchain Overview Of Blockchain 51 Percent Attack With Workflow BCT SS V
Cyber Threats In Blockchain Overview Of Blockchain 51 Percent Attack With Workflow BCT SS VThe following slide showcases brief introduction of 51percent attack to analyze hashing power of cryptocurrency users. It includes elements such at mining faster rate, malicious user, along with its workflow, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Overview Of Blockchain 51 Percent Attack With Workflow BCT SS V This template helps you present information on Four stages. You can also present information on Mining Capability, Mining Capabilities, Much Faster Rate using this PPT design. This layout is completely editable so personaize it now
-
 Ransomware In Digital Age About Procedure And Working Of Ransomware Attack
Ransomware In Digital Age About Procedure And Working Of Ransomware AttackThis slide highlights the working of ransomware from how it infect the system or network and what the common procedure they follow such as infection, execution, ransom demand and other. Increase audience engagement and knowledge by dispensing information using Ransomware In Digital Age About Procedure And Working Of Ransomware Attack. This template helps you present information on four stages. You can also present information on Infection, Execution, Ransom Demand, Ransomware Attack, Malicious Attachment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Does Phishing Attack Works On Blockchain Network Guide For Blockchain BCT SS V
How Does Phishing Attack Works On Blockchain Network Guide For Blockchain BCT SS VThe following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Introducing How Does Phishing Attack Works On Blockchain Network Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Attacker, Phishing Email, Internet Network using this template. Grab it now to reap its full benefits.
-
 Overview And Workflow Process Of Eclipse Attack Guide For Blockchain BCT SS V
Overview And Workflow Process Of Eclipse Attack Guide For Blockchain BCT SS VThe following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer-to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. Present the topic in a bit more detail with this Overview And Workflow Process Of Eclipse Attack Guide For Blockchain BCT SS V Use it as a tool for discussion and navigation on Overview, Eclipse Attack Works, Malicious Nodes This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview And Working Process Of Ddos Attack Guide For Blockchain BCT SS V
Overview And Working Process Of Ddos Attack Guide For Blockchain BCT SS VThe following slide illustrates brief introduction of distributed denial of service DDoS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc. Introducing Overview And Working Process Of Ddos Attack Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Overview, Perform Operations, Excessive Internet Traffic using this template. Grab it now to reap its full benefits.
-
 Overview Of Blockchain 51 Percent Attack With Workflow Guide For Blockchain BCT SS V
Overview Of Blockchain 51 Percent Attack With Workflow Guide For Blockchain BCT SS VThe following slide showcases brief introduction of 51 percent attack to analyze hashing power of cryptocurrency users. It includes elements such at mining faster rate, malicious user, along with its workflow, etc. Present the topic in a bit more detail with this Overview Of Blockchain 51 Percent Attack With Workflow Guide For Blockchain BCT SS V Use it as a tool for discussion and navigation on Overview, Blockchain Network, Public Network This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 How Does Phishing Attack Works Securing Blockchain Transactions A Beginners Guide BCT SS V
How Does Phishing Attack Works Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Increase audience engagement and knowledge by dispensing information using How Does Phishing Attack Works Securing Blockchain Transactions A Beginners Guide BCT SS V. This template helps you present information on six stages. You can also present information on Attackers Dispense Email, Steals Data, Obtains Information From System using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Decoding Blockchain Mining Types Of Attacks On Proof Of Work System BCT SS V
Decoding Blockchain Mining Types Of Attacks On Proof Of Work System BCT SS VThis slide mentions the various types of attacks that can be encountered on proof of work system used for blockchain mining and their corresponding description and solutions. Attacks mentioned include Sybil attacks and Denial of Service attacks. Present the topic in a bit more detail with this Decoding Blockchain Mining Types Of Attacks On Proof Of Work System BCT SS V. Use it as a tool for discussion and navigation on Sybil Attacks, Proof Of Work System, Diversify Connections, Potentially Leading To A Monopoly. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Types Of Attacks On Proof Of Work Mastering Blockchain Mining A Step By Step Guide BCT SS V
Types Of Attacks On Proof Of Work Mastering Blockchain Mining A Step By Step Guide BCT SS VThis slide mentions the various types of attacks that can be encountered on proof of work system used for blockchain mining and their corresponding description and solutions. Attacks mentioned include Sybil attacks and Denial of Service attacks. Increase audience engagement and knowledge by dispensing information using Types Of Attacks On Proof Of Work Mastering Blockchain Mining A Step By Step Guide BCT SS V. This template helps you present information on four stages. You can also present information on Sybil Attacks, Manipulate Actions, Bitcoin Transactions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Types Of Attacks On Proof Of Work System Everything You Need To Know About Blockchain BCT SS V
Types Of Attacks On Proof Of Work System Everything You Need To Know About Blockchain BCT SS VThis slide mentions the various types of attacks that can be encountered on proof of work system used for blockchain mining and their corresponding description and solutions. Attacks mentioned include Sybil attacks and Denial of Service attacks. Present the topic in a bit more detail with this Types Of Attacks On Proof Of Work System Everything You Need To Know About Blockchain BCT SS V. Use it as a tool for discussion and navigation on Sybil Attacks, Denial Of Service, Attacks, Solutions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Process Of Phishing Attacks In Devices Mobile Security
Working Process Of Phishing Attacks In Devices Mobile SecurityThis slide depicts about the working of phishing attacks in mobile devices which include attacker, victim, phishing website and legitimate website. Deliver an outstanding presentation on the topic using this Working Process Of Phishing Attacks In Devices Mobile Security Dispense information and present a thorough explanation of Sends Email To Victim, Legitimate Website using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber threat management workplace determine sequence phases for attack
Cyber threat management workplace determine sequence phases for attackThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Increase audience engagement and knowledge by dispensing information using Cyber Threat Management Workplace Determine Sequence Phases For Attack. This template helps you present information on four stages. You can also present information on Reconnaissance, Weaponization, Delivery, Exploitation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine Sequence Phases For Threat Attack Contd Vulnerability Administration At Workplace
Determine Sequence Phases For Threat Attack Contd Vulnerability Administration At WorkplaceThis slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Increase audience engagement and knowledge by dispensing information using Determine Sequence Phases For Threat Attack Contd Vulnerability Administration At Workplace. This template helps you present information on four stages. You can also present information on Installation, Communication, Sequence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Vulnerability Administration At Workplace Sequence Phases For Threat Attack
Vulnerability Administration At Workplace Sequence Phases For Threat AttackThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Deliver an outstanding presentation on the topic using this Vulnerability Administration At Workplace Sequence Phases For Threat Attack. Dispense information and present a thorough explanation of Reconnaissance, Weaponization, Exploitation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Attacks Work In Powerpoint And Google Slides Cpb
Attacks Work In Powerpoint And Google Slides CpbPresenting our Attacks Work In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Attacks Work. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Overview And Workflow Process Of Eclipse Attack Ultimate Guide For Blockchain BCT SS
Overview And Workflow Process Of Eclipse Attack Ultimate Guide For Blockchain BCT SSThe following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer-to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. Deliver an outstanding presentation on the topic using this Overview And Workflow Process Of Eclipse Attack Ultimate Guide For Blockchain BCT SS Dispense information and present a thorough explanation of Target Node, Attacker Nodes, Participating Nodes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ultimate Guide For Blockchain How Does Phishing Attack Works On Blockchain Network BCT SS
Ultimate Guide For Blockchain How Does Phishing Attack Works On Blockchain Network BCT SSThe following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Increase audience engagement and knowledge by dispensing information using Ultimate Guide For Blockchain How Does Phishing Attack Works On Blockchain Network BCT SS This template helps you present information on Seven stages. You can also present information on Phishing Email, Attacker, Internet Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ultimate Guide For Blockchain Overview And Working Process Of Ddos Attack BCT SS
Ultimate Guide For Blockchain Overview And Working Process Of Ddos Attack BCT SSThe following slide showcases brief introduction of 51 Percent attack to analyze hashing power of cryptocurrency users. It includes elements such at mining faster rate, malicious user, along with its workflow, etc. Deliver an outstanding presentation on the topic using this Ultimate Guide For Blockchain Overview And Working Process Of Ddos Attack BCT SS Dispense information and present a thorough explanation of Close The Attack, Website Hostage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ultimate Guide For Blockchain Overview Of Blockchain 51 Percent Attack With Workflow BCT SS
Ultimate Guide For Blockchain Overview Of Blockchain 51 Percent Attack With Workflow BCT SSThe following slide illustrates brief introduction of phishing attacks impacting blockchian to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc. Introducing Ultimate Guide For Blockchain Overview Of Blockchain 51 Percent Attack With Workflow BCT SS to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Mining Capabilities, Blockchain Network, Public Network using this template. Grab it now to reap its full benefits.
-
 DDOS Attack Works In Powerpoint And Google Slides Cpb
DDOS Attack Works In Powerpoint And Google Slides CpbPresenting DDOS Attack Works In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like DDOS Attack Works. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Fix Anxiety Attack Workplace In Powerpoint And Google Slides Cpb
Fix Anxiety Attack Workplace In Powerpoint And Google Slides CpbIntroducing Fix Anxiety Attack Workplace In Powerpoint And Google Slides Cpb to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Fix Anxiety Attack Workplace, using this template. Grab it now to reap its full benefits.
-
 How Ddos Attack Works In Implementing Blockchain Security Solutions
How Ddos Attack Works In Implementing Blockchain Security SolutionsThis slide represents the overview of distributed denialofservice DDOS attacks in blockchain technology. This slide aims to showcase how distributed denialofservice DDOS works to exploit a blockchain network by generating multiple requests from a single source.Present the topic in a bit more detail with this How Ddos Attack Works In Implementing Blockchain Security Solutions. Use it as a tool for discussion and navigation on Network Resource Unavailable, Mitigation Strategies, Distinguishing Malicious. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 About Angler Phishing Working And Example Phishing Attacks And Strategies
About Angler Phishing Working And Example Phishing Attacks And StrategiesThis slide talks about the angler phishing attacks conducted on internet using social media platforms. The purpose of this slide is to illustrate how fraudulent tweets or texts containing malicious links and misleading information, can be used by scammers to trick individuals.Present the topic in a bit more detail with this About Angler Phishing Working And Example Phishing Attacks And Strategies. Use it as a tool for discussion and navigation on Sensitive Information, Fraudster Establishes, Working Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 About Smishing Attacks Working And Example Phishing Attacks And Strategies
About Smishing Attacks Working And Example Phishing Attacks And StrategiesThis slide talks about the smishing cyber attacks conducted by sending text messages to the targets. The purpose of this slide is to illustrate how fraudulent texts are sent to the users which contains malicious links and other mis leading information.Increase audience engagement and knowledge by dispensing information using About Smishing Attacks Working And Example Phishing Attacks And Strategies. This template helps you present information on three stages. You can also present information on Criminal Investigation, Arrest Warrant, Provide Personal using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Does A Phishing Attack Work Phishing Attacks And Strategies
How Does A Phishing Attack Work Phishing Attacks And StrategiesThis slide demonstrates the working flow of a phishing attack. The purpose of this slide is to outline the various phases of phishing scams such as campaign crafted, payloads, impersonation, execution, ransomware and encrypts on target.Increase audience engagement and knowledge by dispensing information using How Does A Phishing Attack Work Phishing Attacks And Strategies. This template helps you present information on six stages. You can also present information on Campaign Crafted, Targeted Individuals, Attacked System using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Does Vishing Attack Works Phishing Attacks And Strategies
How Does Vishing Attack Works Phishing Attacks And StrategiesThis slide illustrates the working procedure of a vishing attack. The purpose of this slide is to explain the working flow of vishing cyber attack. The key components include attacker, target, spoofed caller ID, SMS to victim, file execution confirmation, etc.Deliver an outstanding presentation on the topic using this How Does Vishing Attack Works Phishing Attacks And Strategies. Dispense information and present a thorough explanation of Execution Confirmation, Phisher Receives, Sending Confirmation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Working Of Phishing Training Programs Phishing Attacks And Strategies
Working Of Phishing Training Programs Phishing Attacks And StrategiesThis slide demonstrates the working of phishing training programs for organizations. These include start with employee training, make fictitious phishing campaigns, reinforce the phishing awareness training and track progress and upgrade.Increase audience engagement and knowledge by dispensing information using Working Of Phishing Training Programs Phishing Attacks And Strategies. This template helps you present information on four stages. You can also present information on Employee Training, Phishing Campaigns, Awareness Training using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.




