Powerpoint Templates and Google slides for Attack Type
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Understanding Types of Cyber Attacks Training Ppt
Understanding Types of Cyber Attacks Training PptPresenting Training Deck on Understanding Types of Cyber Attacks. This deck comprises of 116 slides. Each slide is well crafted and designed by our PowerPoint experts. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed business presentation, add your content, and present it with confidence.
-
 Types of Attacks in Blockchain Training Module on Blockchain Technology and its Applications Training Ppt
Types of Attacks in Blockchain Training Module on Blockchain Technology and its Applications Training PptPresenting Training Session on Types of Attacks in Blockchain. This presentation deck contains 90 well-researched and uniquely designed slides. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Password Attack Types In Cyber Security Training Ppt
Password Attack Types In Cyber Security Training PptPresenting Password Attack Types in Cyber Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed business presentation, add your content and present it with confidence.
-
 Phishing Attack Types In Cyber Attack Training Ppt
Phishing Attack Types In Cyber Attack Training PptPresenting Phishing Attack Types in Cyber Attack. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Buffer Overflow Attack As A Type Of Dos Attack Training Ppt
Buffer Overflow Attack As A Type Of Dos Attack Training PptPresenting Buffer Overflow Attack as a Type of DoS Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Flood Attack As A Type Of Dos Attack Training Ppt
Flood Attack As A Type Of Dos Attack Training PptPresenting Flood Attack as a Type of DoS Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Types Of Historic Dos Attacks Training Ppt
Types Of Historic Dos Attacks Training PptPresenting Types of Historic DoS Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Smurf Attack As A Type Of Dos Attack Training Ppt
Smurf Attack As A Type Of Dos Attack Training PptPresenting Smurf Attack as a Type of DoS Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Ping Flood Attack As A Type Of Dos Attack Training Ppt
Ping Flood Attack As A Type Of Dos Attack Training PptPresenting Ping Flood Attack as a Type of DoS Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Ping Of Death Attack As A Type Of Dos Attack Training Ppt
Ping Of Death Attack As A Type Of Dos Attack Training PptPresenting Ping of Death Attack as a Type of DoS Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Types Of Man In The Middle Attacks Training Ppt
Types Of Man In The Middle Attacks Training PptPresenting Working of Types of Man in the Middle Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
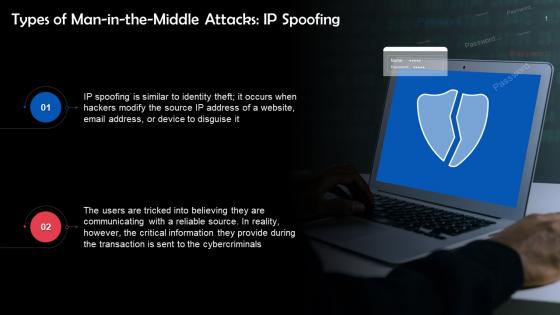 IP Spoofing As A Type Of Man In The Middle Attack Training Ppt
IP Spoofing As A Type Of Man In The Middle Attack Training PptPresenting IP Spoofing as a Type of Man in the Middle Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 HTTP Spoofing As A Type Of Man In The Middle Attack Training Ppt
HTTP Spoofing As A Type Of Man In The Middle Attack Training PptPresenting HTTP Spoofing as a Type of Man in the Middle Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 DNS Spoofing As A Type Of Man In The Middle Attack Training Ppt
DNS Spoofing As A Type Of Man In The Middle Attack Training PptPresenting DNS Spoofing as a Type of Man in the Middle Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Email Spoofing As A Type Of Man In The Middle Attack Training Ppt
Email Spoofing As A Type Of Man In The Middle Attack Training PptPresenting Email Spoofing as a Type of Man in the Middle Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 SSL Hijacking As A Type Of Man In The Middle Attack Training Ppt
SSL Hijacking As A Type Of Man In The Middle Attack Training PptPresenting SSL Hijacking as a Type of Man in the Middle Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Session Hijacking As A Type Of Man In The Middle Attack Training Ppt
Session Hijacking As A Type Of Man In The Middle Attack Training PptPresenting Session Hijacking as a Type of Man in the Middle Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Cache Poisoning As A Type Of Man In The Middle Attack Training Ppt
Cache Poisoning As A Type Of Man In The Middle Attack Training PptPresenting Cache Poisoning as a Type of Man in the Middle Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
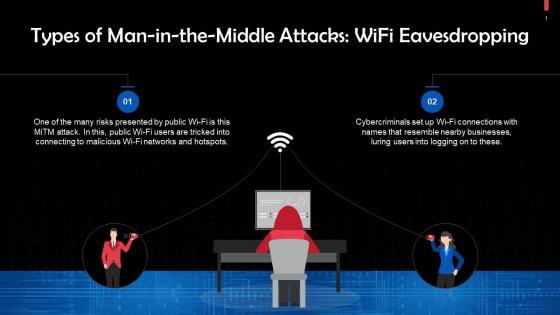 Wi Fi Eavesdropping As A Type Of Man In The Middle Attack Training Ppt
Wi Fi Eavesdropping As A Type Of Man In The Middle Attack Training PptPresenting Wi-Fi Eavesdropping as a Type of Man in the Middle Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Different Types Of Phishing Attacks Training Ppt
Different Types Of Phishing Attacks Training PptPresenting Different Types of Phishing Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Spear Phishing As A Type Of Phishing Attack Training Ppt
Spear Phishing As A Type Of Phishing Attack Training PptPresenting Spear Phishing as a Type of Phishing Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Whaling As A Type Of Phishing Attack Training Ppt
Whaling As A Type Of Phishing Attack Training PptPresenting Whaling as a Type of Phishing Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Vishing As A Type Of Phishing Attack Training Ppt
Vishing As A Type Of Phishing Attack Training PptPresenting Vishing as a Type of Phishing Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Smishing As A Type Of Phishing Attack Training Ppt
Smishing As A Type Of Phishing Attack Training PptPresenting Smishing as a Type of Phishing Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Email Phishing As A Type Of Phishing Attack Training Ppt
Email Phishing As A Type Of Phishing Attack Training PptPresenting Email Phishing as a Type of Phishing Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Search Engine Phishing As A Type Of Phishing Attack Training Ppt
Search Engine Phishing As A Type Of Phishing Attack Training PptPresenting Search Engine Phishing as a Type of Phishing Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Different Types Of Password Attacks Training Ppt
Different Types Of Password Attacks Training PptPresenting Different Types of Password Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Types Of Phishing Password Attacks In Cyber Security Training Ppt
Types Of Phishing Password Attacks In Cyber Security Training PptPresenting Types of Phishing Password Attacks in Cyber Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Clone Phishing As A Type Of Password Attack Training Ppt
Clone Phishing As A Type Of Password Attack Training PptPresenting Clone Phishing as a Type of Password Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Types Of Brute Force Password Attacks Training Ppt
Types Of Brute Force Password Attacks Training PptPresenting Types of Brute Force Password Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Credential Stuffing As A Type Of Brute Force Password Attack Training Ppt
Credential Stuffing As A Type Of Brute Force Password Attack Training PptPresenting Credential Stuffing as a Type of Brute Force Password Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Keylogging As A Type Of Password Attack Training Ppt
Keylogging As A Type Of Password Attack Training PptPresenting Keylogging as a Type of Password Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Table Of Contents For Types Of Attacks In Blockchain Training Ppt
Table Of Contents For Types Of Attacks In Blockchain Training PptPresenting Table of Contents for Types of Attacks in Blockchain. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Major Types Of User Wallet Attacks On Blockchain Training Ppt
Major Types Of User Wallet Attacks On Blockchain Training PptPresenting Major Types of User Wallet Attacks on Blockchain. Our PowerPoint experts have included all the necessary templates, designs, icons, graphs, and other essential material. This deck is well crafted by extensive research. Slides consist of amazing visuals and appropriate content. These PPT slides can be instantly downloaded with just a click. Compatible with all screen types and monitors. Supports Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Multiple Types Of Blockchain Network Attack On Blockchain Network Training Ppt
Multiple Types Of Blockchain Network Attack On Blockchain Network Training PptPresenting Multiple Types of Blockchain Network Attack on Blockchain Network. Our PowerPoint experts have included all the necessary templates, designs, icons, graphs, and other essential material. This deck is well crafted by extensive research. Slides consist of amazing visuals and appropriate content. These PPT slides can be instantly downloaded with just a click. Compatible with all screen types and monitors. Supports Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Key Takeaways From Types Of Attacks In Blockchain Session Training Ppt
Key Takeaways From Types Of Attacks In Blockchain Session Training PptPresenting Key Takeaways from Types of Attacks in Blockchain Session. These slides are 100 Percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Most Common Types Of IoT Botnet Attacks Improving IoT Device Cybersecurity IoT SS
Most Common Types Of IoT Botnet Attacks Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase various types of Internet of Things IoT botnet attacks. Bruce force attack, Phishing, Device Bricking, and Cryptocurrency Mining are the most common types which are outlined in slide. Present the topic in a bit more detail with this Most Common Types Of IoT Botnet Attacks Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Phishing, Bricking, Mining. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Most Common Types Of Ransomware Attack Improving IoT Device Cybersecurity IoT SS
Most Common Types Of Ransomware Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline various types of ransomware attack which can cause financial loss to company. It covers information about Scareware, Screen Lockers, DDoS Distributed Denial of Service Extortion, Encrypting Ransomware, etc. Deliver an outstanding presentation on the topic using this Most Common Types Of Ransomware Attack Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Scareware, Lockers, Mobile using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Various Types Of Dos Attack Improving IoT Device Cybersecurity IoT SS
Various Types Of Dos Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline multiple types of Denial of Service Dos attack. It covers information about application layer, buffer overflow, DNS Domain Name Server amplification, and ping of death. Deliver an outstanding presentation on the topic using this Various Types Of Dos Attack Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Application, Layer, Death using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Various Types Of IoT Password Attack Improving IoT Device Cybersecurity IoT SS
Various Types Of IoT Password Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to delineate multiple types of Internet of Things IoT password attack. Phishing, Dictionary Attack, Credential Stuffing, and Keyloggers are the major attacks which are mentioned in slide. Present the topic in a bit more detail with this Various Types Of IoT Password Attack Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Phishing, Dictionary, Credential. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain And Cybersecurity Various Types Of Crypto Phishing Attacks BCT SS V
Blockchain And Cybersecurity Various Types Of Crypto Phishing Attacks BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Introducing Blockchain And Cybersecurity Various Types Of Crypto Phishing Attacks BCT SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing, Whaling Phishing, Clone Phishing using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS V
Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS V This template helps you present information on Three stages. You can also present information on Spear Phishing, Whaling Phishing, Clone Phishing using this PPT design. This layout is completely editable so personaize it now
-
 Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber Attacks
Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber AttacksThis slide represents the different types of cyber-attacks throughout the year, including the percentage of total loss caused by these attacks. Present the topic in a bit more detail with this Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber Attacks. Use it as a tool for discussion and navigation on Cyber Attacks Throughout, Online Or Web Based Attacks, Malware Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Various Types Of Crypto Phishing Attacks Guide For Blockchain BCT SS V
Various Types Of Crypto Phishing Attacks Guide For Blockchain BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Introducing Various Types Of Crypto Phishing Attacks Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing, Whaling Phishing, Clone Phishing using this template. Grab it now to reap its full benefits.
-
 Various Types Of Crypto Phishing Attacks Securing Blockchain Transactions A Beginners Guide BCT SS V
Various Types Of Crypto Phishing Attacks Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Increase audience engagement and knowledge by dispensing information using Various Types Of Crypto Phishing Attacks Securing Blockchain Transactions A Beginners Guide BCT SS V. This template helps you present information on three stages. You can also present information on Spear Phishing, Whaling Phishing, Clone Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Types Of Cybersecurity Attacks In Education
Types Of Cybersecurity Attacks In EducationThis slide depicts the types of cybersecurity attacks in education. This slide aims to help education businesses adopt suitable measures to prevent cyberattacks. It includes a graphical analysis and key insights Introducing our Types Of Cybersecurity Attacks In Education set of slides. The topics discussed in these slides are Cyberattacks In Education, Education Is Phishing. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Email Security Best Practices Common Types Of Email Security Attacks
Email Security Best Practices Common Types Of Email Security AttacksThe purpose of this slide is to discuss the different types of email security threats in current digital era. These email security attacks are phishing, social engineering, spear phishing, ransomware, malware and spoofing. Introducing Email Security Best Practices Common Types Of Email Security Attacks to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Phishing, Social Engineering, Spear Phishing, Ransomware, using this template. Grab it now to reap its full benefits.
-
 Introduction To Types Of Attacks In Cyberterrorism Strategic Guide To Implement Strategy SS
Introduction To Types Of Attacks In Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the different types of attacks in cyber terrorism. It includes attacks such as DoS and DDoS attack, Man-in-the-Middle MITM attack, Phishing attack, Whale phishing attack, Spear phishing attack and Ransomware attack.Increase audience engagement and knowledge by dispensing information using Introduction To Types Of Attacks In Cyberterrorism Strategic Guide To Implement Strategy SS. This template helps you present information on six stages. You can also present information on Whale Phishing Attack, Spear Phishing Attack, Ransomware Attack, Phishing Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Types Of Cyber Attacks Faced By How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS
Types Of Cyber Attacks Faced By How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SSThis slide showcases various types of cyber attacks that significantly damage the organization resources and reputation. Different types of attacks faced are Malware, Phishing, Man in middle attack, SQL injection etc. Introducing Types Of Cyber Attacks Faced By How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Software, Financial, Results, using this template. Grab it now to reap its full benefits.
-
 Types Of Attacks On Proof Of Work System Complete Guide On How Blockchain BCT SS
Types Of Attacks On Proof Of Work System Complete Guide On How Blockchain BCT SSThis slide mentions the various types of attacks that can be encountered on proof of work system used for blockchain mining and their corresponding description and solutions. Attacks mentioned include Sybil attacks and Denial of Service attacks. Present the topic in a bit more detail with this Types Of Attacks On Proof Of Work System Complete Guide On How Blockchain BCT SS. Use it as a tool for discussion and navigation on Description, Solutions, Denial Of Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Unlocking The Impact Of Technology Types Of Cyber Attacks Faced By Organisations
Unlocking The Impact Of Technology Types Of Cyber Attacks Faced By OrganisationsThis slide showcases various types of cyber attacks faced by organisations. This template focuses on threat prevention rather than threat detection in an organisation. It includes information related to malware attacks, password guessing, etc. Introducing Unlocking The Impact Of Technology Types Of Cyber Attacks Faced By Organisations to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Password Guessing Attack, Malware Attack, Phishing Attack, Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Advanced Technologies Various Types Of Cyber Attacks On System
Advanced Technologies Various Types Of Cyber Attacks On SystemThis slide explains Various types of cyber attacks on system on a system such as malware, phishing, man in the middle, distributed denial of service, brute force, SQL injection, and domain name system. Introducing Advanced Technologies Various Types Of Cyber Attacks On System to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Malware, Phishing, Brute Force, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Overview Of Different Types Of Phishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Overview Of Different Types Of Phishing AttacksThis slide outlines the various types of cyber phishing attacks. The types include email phishing, HTTPS phishing, whaling, smishing, angler phishing, pharming, spear phishing, pop-up phishing, clone phishing, evil twin scams, watering hole attacks, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Overview Of Different Types Of Phishing Attacks. Use it as a tool for discussion and navigation on Phishing Attacks, Watering Hole Attacks, Angler Phishing, Search Engine. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 K101 Different Types Of Vishing Cyber Attacks Phishing Attacks And Strategies To Mitigate Them V2
K101 Different Types Of Vishing Cyber Attacks Phishing Attacks And Strategies To Mitigate Them V2This slide talks about the various types of vishing cyber attacks. The purpose of this slide is to briefly explain different techniques of vishing scams used by the attackers to scam users. These are caller ID spoofing, dumpster diving, wardialing, etc. Increase audience engagement and knowledge by dispensing information using K101 Different Types Of Vishing Cyber Attacks Phishing Attacks And Strategies To Mitigate Them V2. This template helps you present information on four stages. You can also present information on Security And It Infrastructure, Voice Over Internet Protocol, Transmission Of Voice, Phishing Attack Victims using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Different Types Of Smishing Cyber Scams
Phishing Attacks And Strategies To Mitigate Them V2 Different Types Of Smishing Cyber ScamsThis slide talks about the various types of smishing cyber attacks. The purpose of this slide is to briefly explain different techniques of smishing scams used by the attackers to scam users. These are covid-19 smishing, financial services smishing, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Different Types Of Smishing Cyber Scams to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Smishing Scams, Financial Services Smishing, Gift Smishing, Customer Support Smishing, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Pharming Phishing Types And Prevention Techniques
Phishing Attacks And Strategies To Mitigate Them V2 Pharming Phishing Types And Prevention TechniquesThis slide demonstrates the different types pf pharming phishing scams. The primary types include malware-based pharming and DNS pharming. This slide also outlines the ways which helps to prevent a pharming attack such as verify the URL, install VPN, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Pharming Phishing Types And Prevention Techniques. Dispense information and present a thorough explanation of Pharming Phishing Scams, Malware Based Pharming, Pharming Attack, Prevention Techniques using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Emerging Technologies Various Types Of Cyber Attacks On System
Emerging Technologies Various Types Of Cyber Attacks On SystemThis slide explains Various types of cyber attacks on system on a system such as malware, phishing, man in the middle, distributed denial of service, brute force, SQL injection, and domain name system. Increase audience engagement and knowledge by dispensing information using Emerging Technologies Various Types Of Cyber Attacks On System. This template helps you present information on seven stages. You can also present information on Malware, Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Trending Technologies Various Types Of Cyber Attacks On System
Trending Technologies Various Types Of Cyber Attacks On SystemThis slide explains Various types of cyber attacks on system on a system such as malware, phishing, man in the middle, distributed denial of service, brute force, SQL injection, and domain name system. Increase audience engagement and knowledge by dispensing information using Trending Technologies Various Types Of Cyber Attacks On System. This template helps you present information on eight stages. You can also present information on Malware, Phishing, Brute Force using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Dos Attack Types In Powerpoint And Google Slides Cpb
Dos Attack Types In Powerpoint And Google Slides CpbPresenting Dos Attack Types In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Dos Attack Types. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Types Of Attacks Prevented By Cloud Cryptography Cloud Cryptography
Types Of Attacks Prevented By Cloud Cryptography Cloud CryptographyThis purpose of this slide is to explain how cloud cryptography can help prevent several types of attacks that can compromise the confidentiality, integrity, and availability of data in cloud environments. These include Man-in-the-middle MitM attacks, data breaches, insider attacks, etc. Increase audience engagement and knowledge by dispensing information using Types Of Attacks Prevented By Cloud Cryptography Cloud Cryptography. This template helps you present information on four stages. You can also present information on Data Breaches, Insider Attacks, Denial Of Service using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.




