Powerpoint Templates and Google slides for Attack Risk
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Rising Number Of Information Security Attacks Information System Security And Risk Administration Plan
Rising Number Of Information Security Attacks Information System Security And Risk Administration PlanThis slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection. Deliver an outstanding presentation on the topic using thisRising Number Of Information Security Attacks Information System Security And Risk Administration Plan. Dispense information and present a thorough explanation of Financial Years, Cyber Attacks, Information Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
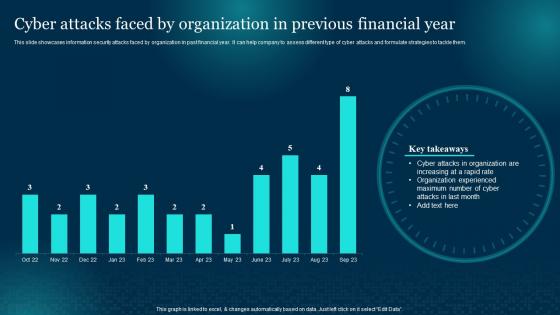 Cyber Attacks Faced By Organization Previous Cybersecurity Risk Analysis And Management Plan
Cyber Attacks Faced By Organization Previous Cybersecurity Risk Analysis And Management PlanThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Deliver an outstanding presentation on the topic using this Cyber Attacks Faced By Organization Previous Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Organization, Financial Year, Experienced using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
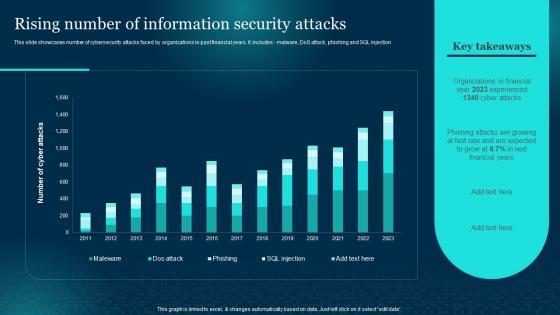 Rising Number Of Information Security Attacks Cybersecurity Risk Analysis And Management Plan
Rising Number Of Information Security Attacks Cybersecurity Risk Analysis And Management PlanThis slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection Present the topic in a bit more detail with this Rising Number Of Information Security Attacks Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Information, Security Attacks, Organizations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategy To Minimize Cyber Attacks Dashboard For Tracking Cyber Attack Risk Levels
Strategy To Minimize Cyber Attacks Dashboard For Tracking Cyber Attack Risk LevelsThe slide represents the dashboard for tracking cyber attack risk levels. It includes information regarding the multiple threat agents, attack methods, preventive controls along with details of risk score and infected systems. Present the topic in a bit more detail with this Strategy To Minimize Cyber Attacks Dashboard For Tracking Cyber Attack Risk Levels. Use it as a tool for discussion and navigation on Dashboard For Tracking, Cyber Attack Risk Levels, Infrastructure Controls, Preventive Controls, Detective Controls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management Dashboard
Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management DashboardThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management Dashboard. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Cyber Supply Chain Risk Management Dashboard
Cyber Security Attacks Response Plan Cyber Supply Chain Risk Management DashboardThis slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Cyber Supply Chain Risk Management Dashboard. Use it as a tool for discussion and navigation on Cyber Supply Chain, Risk Management, Dashboard, Regulatory Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Enterprise Cyber Risk Management Dashboard
Cyber Security Attacks Response Plan Enterprise Cyber Risk Management DashboardThis slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Enterprise Cyber Risk Management Dashboard. Dispense information and present a thorough explanation of Enterprise Cyber, Risk Management, Dashboard, Action Plan Breakdown using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Assessment Program Cyber Attacks Faced By Organization
Cybersecurity Risk Assessment Program Cyber Attacks Faced By OrganizationThis slide provides information regarding the number of cyber attacks faced by the organization and its impact on IT operations and system downtime. It also provides details of percentage rise in such attacks since last month. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Cyber Attacks Faced By Organization. Use it as a tool for discussion and navigation on Cyber Attacks, IT Operations, System Downtime. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels
Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk LevelsThe slide represents the dashboard for tracking cyber attack risk levels. It includes information regarding the multiple threat agents, attack methods, preventive controls along with details of risk score and infected systems. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels. Dispense information and present a thorough explanation of Infrastructure Controls, Preventive Controls, Detective Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Assessment Program Dashboard To Monitor Cyber Attack Incidents
Cybersecurity Risk Assessment Program Dashboard To Monitor Cyber Attack IncidentsThis slide indicates the dashboard to monitor cyber attacks on IT assets of the firm. It includes information regarding the total cyber attack incidents both month and day wise along with the details of threat class, overall risk factor and top vulnerabilities. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Dashboard To Monitor Cyber Attack Incidents. Use it as a tool for discussion and navigation on Dashboard To Monitor, Cyber Attack Incidents, Vulnerabilities, Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Assessment Program Summary Of Key Cyber Attacks Occurred
Cybersecurity Risk Assessment Program Summary Of Key Cyber Attacks OccurredThis slide shows the summary of key of cybers attacks occurred in organization such as phishing, malware attack, denial of service, SQL injections, identity thefts. It also contains details of the cyber attacker origin such as inadvertent actors, malicious insiders. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Summary Of Key Cyber Attacks Occurred. Use it as a tool for discussion and navigation on Cyber Attacks Occurred, Financial Loss, Cyber Attack Origins. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Digital Risk Management Dashboard For Tracking Threats And Attacks
Digital Risk Management Dashboard For Tracking Threats And AttacksThe purpose of this slide is to represent dashboard to monitor risks and cyber threats for efficient risk management. It includes various types of key performance indicators such as types of risks, severities, sources and risk meter. Introducing our Digital Risk Management Dashboard For Tracking Threats And Attacks set of slides. The topics discussed in these slides are Severities, Types Of Risk This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber security risk management determine sequence phases for threat attack
Cyber security risk management determine sequence phases for threat attackThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Determine Sequence Phases For Threat Attack. This template helps you present information on four stages. You can also present information on Reconnaissance, Weaponization, Exploitation, Delivery using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine sequence phases for threat attack contd cyber security risk management
Determine sequence phases for threat attack contd cyber security risk managementThis slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Introducing Determine Sequence Phases For Threat Attack Contd Cyber Security Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Installation, Command And Control, Actions And Objectives, Covering Tracks, using this template. Grab it now to reap its full benefits.
-
 Cyber Attacks On Ukraine Cybersecurity Risks Of An Escalating Russia Ukraine Conflict
Cyber Attacks On Ukraine Cybersecurity Risks Of An Escalating Russia Ukraine ConflictThis slide represents the cybersecurity risks associated with Russia and Ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions. Introducing Cyber Attacks On Ukraine Cybersecurity Risks Of An Escalating Russia Ukraine Conflict to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Infrastructure, Cybersecurity, Potential, Cyberattacks, Financial, using this template. Grab it now to reap its full benefits.
-
 Wiper Malware Attack Cybersecurity Risks Of An Escalating Russia
Wiper Malware Attack Cybersecurity Risks Of An Escalating RussiaThis slide represents the cybersecurity risks associated with Russia and Ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions. Introducing Wiper Malware Attack Cybersecurity Risks Of An Escalating Russia to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Risks Of An Escalating Russia Ukraine Conflict, using this template. Grab it now to reap its full benefits.
-
 Risks Involved In Public Blockchain Attacks Blockchain And Distributed Ledger Technology
Risks Involved In Public Blockchain Attacks Blockchain And Distributed Ledger TechnologyThis slide defines the various risks involved in public blockchains, such as 51 parcent attacks, double spending, and proof of work. Introducing Risks Involved In Public Blockchain Attacks Blockchain And Distributed Ledger Technology to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Risks Involved In Public Blockchain, using this template. Grab it now to reap its full benefits.
-
 Cyber Attack Risk In Powerpoint And Google Slides Cpb
Cyber Attack Risk In Powerpoint And Google Slides CpbPresenting our Cyber Attack Risk In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Cyber Attack Risk This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
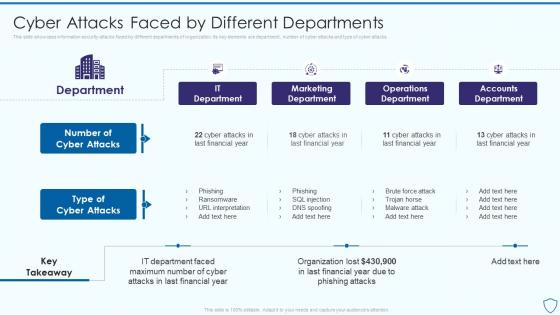 Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By Different
Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By DifferentThis slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks Deliver an outstanding presentation on the topic using this Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By Different. Dispense information and present a thorough explanation of Marketing Department, Operations Department, Accounts Department using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Attacks Faced By Risk Assessment And Management Plan For Information Security
Information Security Attacks Faced By Risk Assessment And Management Plan For Information SecurityThis slide showcases most common information attacks faced by organization. It includes malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack Deliver an outstanding presentation on the topic using this Information Security Attacks Faced By Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Malware, Phishing, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 User Wallet Attack Risk Colored Icon In Powerpoint Pptx Png And Editable Eps Format
User Wallet Attack Risk Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable User wallet attack risk colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 User Wallet Attack Risk Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
User Wallet Attack Risk Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable User wallet attack risk monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Zero Day Attack With Risk Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Zero Day Attack With Risk Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Zero day attack with risk colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Zero Day Attack With Risk Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Zero Day Attack With Risk Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Zero day attack with risk monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Cyber Attacks Faced By Different Departments Information Security Risk Management
Cyber Attacks Faced By Different Departments Information Security Risk ManagementThis slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Introducing Cyber Attacks Faced By Different Departments Information Security Risk Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispense information on Department, Number Of Cyber Attacks, Type Of Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Financial Impact Of Information Security Attacks Information Security Risk Management
Financial Impact Of Information Security Attacks Information Security Risk ManagementThis slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Present the topic in a bit more detail with this Financial Impact Of Information Security Attacks Information Security Risk Management. Use it as a tool for discussion and navigation on Malicious Insiders, Social Engineering, Information Security Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now
-
 Information Security Attacks Faced By Organization Information Security Risk Management
Information Security Attacks Faced By Organization Information Security Risk ManagementThis slide showcases most common information attacks faced by organization. It includes malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. Increase audience engagement and knowledge by dispensing information using Information Security Attacks Faced By Organization Information Security Risk Management. This template helps you present information on six stages. You can also present information on Phishing, Information Security, Organization using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Information System Security And Risk Administration Plan Information Security Attacks Faced By Organization
Information System Security And Risk Administration Plan Information Security Attacks Faced By OrganizationThis slide showcases most common information attacks faced by organization. It includes malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. Increase audience engagement and knowledge by dispensing information using Information System Security And Risk Administration Plan Information Security Attacks Faced By Organization. This template helps you present information on six stages. You can also present information on Sql Injection, Zero Day Exploit, Phishing Attack Accounts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Attacks Faced By Different Departments Information System Security And Risk Administration Plan
Cyber Attacks Faced By Different Departments Information System Security And Risk Administration PlanThis slide showcases information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Present the topic in a bit more detail with this Cyber Attacks Faced By Different Departments Information System Security And Risk Administration Plan. Use it as a tool for discussion and navigation on It Department, Marketing Department, Operations Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Impact Of Information Security Attacks Information System Security And Risk Administration Plan
Financial Impact Of Information Security Attacks Information System Security And Risk Administration PlanThis slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Introducing Financial Impact Of Information Security Attacks Information System Security And Risk Administration Plan to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering, Web Based Attacks, Stolen Devices, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Risk Analysis And Management Plan Cyber Attacks Faced By Different Departments
Cybersecurity Risk Analysis And Management Plan Cyber Attacks Faced By Different DepartmentsThis slide showcases information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks Present the topic in a bit more detail with this Cybersecurity Risk Analysis And Management Plan Cyber Attacks Faced By Different Departments. Use it as a tool for discussion and navigation on Departments, Information, Cyber Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Impact Of Information Security Attacks Cybersecurity Risk Analysis And Management Plan
Financial Impact Of Information Security Attacks Cybersecurity Risk Analysis And Management PlanThis slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type Present the topic in a bit more detail with this Financial Impact Of Information Security Attacks Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Financial, Information, Organizations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Attacks Faced By Organization Cybersecurity Risk Analysis And Management Plan
Information Security Attacks Faced By Organization Cybersecurity Risk Analysis And Management PlanThis slide showcases most common information attacks faced by organization. It includes - malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack Increase audience engagement and knowledge by dispensing information using Information Security Attacks Faced By Organization Cybersecurity Risk Analysis And Management Plan. This template helps you present information on six stages. You can also present information on Information, Organization, Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda For Strategy To Minimize Cyber Attacks Risks Ppt Icon Clipart Images
Agenda For Strategy To Minimize Cyber Attacks Risks Ppt Icon Clipart ImagesIntroducing Agenda For Strategy To Minimize Cyber Attacks Risks Ppt Icon Clipart Images to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Risk Assessment, Cyber Attacks Risks, Attacks Frequency, Cybersecurity Risk, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Strategy To Minimize Cyber Attacks Risks Ppt Icon Templates
Icons Slide For Strategy To Minimize Cyber Attacks Risks Ppt Icon TemplatesPresenting our premium Icons Slide For Strategy To Minimize Cyber Attacks Risks Ppt Icon Templates set of slides with flexible icons. The icons are designed by our group of professionals. Add these Icons Slide For Strategy To Minimize Cyber Attacks Risks Ppt Icon Templates to your presentation to make it visually appealing. Also, edit them according to your requirement. Download it and captive your audience.
-
 Strategy To Minimize Cyber Attacks Framework For Cybersecurity Risk Management
Strategy To Minimize Cyber Attacks Framework For Cybersecurity Risk ManagementThis slide indicates the framework for cybersecurity risk management. The major sub components of model are data sources, cyber intelligence and monitoring, threat and vulnerabilities, executive board and IT governance. Present the topic in a bit more detail with this Strategy To Minimize Cyber Attacks Framework For Cybersecurity Risk Management. Use it as a tool for discussion and navigation on Information Sharing, Components Of Framework, Framework For Cybersecurity, Risk Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategy To Minimize Cyber Attacks Key Approaches To Minimize Cyber Attacks Risks
Strategy To Minimize Cyber Attacks Key Approaches To Minimize Cyber Attacks RisksThis slide indicates the key approaches to minimize the risk associated with cyber attacks. The approaches discussed are update and upgrade outdated software, control accounts access, introduce signed software execution policies, regularly track network intrusions and use multifactor authentication. Increase audience engagement and knowledge by dispensing information using Strategy To Minimize Cyber Attacks Key Approaches To Minimize Cyber Attacks Risks. This template helps you present information on five stages. You can also present information on Control Accounts Access, Software Execution Policies, Multifactor Authentication, Regularly Track Network Intrusions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategy To Minimize Cyber Attacks Mapping Of Multiple Cyber Attacks Using Risk Heat Map
Strategy To Minimize Cyber Attacks Mapping Of Multiple Cyber Attacks Using Risk Heat MapThis slide shows the mapping of cyber attacks based on the likelihood of risk occurrence and its impact. It also contains details of attacks segmentation and the control actions that must be taken such as track, monitor and mitigate against such cyber attacks. Present the topic in a bit more detail with this Strategy To Minimize Cyber Attacks Mapping Of Multiple Cyber Attacks Using Risk Heat Map. Use it as a tool for discussion and navigation on Random Malware Attack, Phishing Attack, Fraudulently Obtain, Sensitive Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategy To Minimize Cyber Attacks Multistep Approach To Conduct Cybersecurity Risk Assessment
Strategy To Minimize Cyber Attacks Multistep Approach To Conduct Cybersecurity Risk AssessmentThis slide indicates the multistep approach to conduct cybersecurity risk assessment in business organization. The major steps of process are risk identification, quantification, evaluation, mitigation and monitoring. Introducing Strategy To Minimize Cyber Attacks Multistep Approach To Conduct Cybersecurity Risk Assessment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Risk Identification, Risk Mapping, Risk Evaluation, Risk Mitigation And Monitoring, using this template. Grab it now to reap its full benefits.
-
 Strategy To Minimize Cyber Attacks Risk Register To Measure Cyber Attacks Vulnerabilities
Strategy To Minimize Cyber Attacks Risk Register To Measure Cyber Attacks VulnerabilitiesThis slide indicates the risk register to measure the cyber attack risk vulnerabilities faced by an organization. It includes information regarding the multiple risks in terms of vulnerability exploited, impact level, likelihood of occurrence and control recommended. Deliver an outstanding presentation on the topic using this Strategy To Minimize Cyber Attacks Risk Register To Measure Cyber Attacks Vulnerabilities. Dispense information and present a thorough explanation of Financial Transactions, Credentials Compromised, Cloud Network Compromised using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
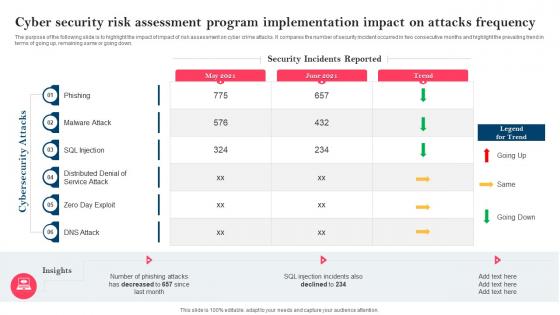 Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program Implementation
Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program ImplementationThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Present the topic in a bit more detail with this Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program Implementation. Use it as a tool for discussion and navigation on Cyber Security, Risk Assessment, Program Implementation, Impact On Attacks Frequency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategy To Minimize Cyber Attacks Risks For Table Of Content Ppt Icon Elements
Strategy To Minimize Cyber Attacks Risks For Table Of Content Ppt Icon ElementsIncrease audience engagement and knowledge by dispensing information using Strategy To Minimize Cyber Attacks Risks For Table Of Content Ppt Icon Elements. This template helps you present information on one stages. You can also present information on Cyber Attacks Risks, Cyber Attacks Risk Mitigation, Mitigation Plan using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents For Strategy To Minimize Cyber Attacks Risks
Table Of Contents For Strategy To Minimize Cyber Attacks RisksIntroducing Table Of Contents For Strategy To Minimize Cyber Attacks Risks to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Attacks Faced By Organization, Risk Heatmap, Risk Register, Mitigation Plan, Cybersecurity Risk Assessment Program, using this template. Grab it now to reap its full benefits.
-
 Adopt Cyber Security Data Policies Cyber Attack Risks Mitigation
Adopt Cyber Security Data Policies Cyber Attack Risks MitigationThe following slide highlights various cyber security policies to manage data control and breach. It includes elements such as network security, data, workstations, remote access etc. Introducing Adopt Cyber Security Data Policies Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Network Security Policies, Data Security Policies, Workstation Policies, using this template. Grab it now to reap its full benefits.
-
 Adopting Strategies By Cyber Attack Type Cyber Attack Risks Mitigation
Adopting Strategies By Cyber Attack Type Cyber Attack Risks MitigationThe following slide depicts the various strategies to manage data control and breach. It includes elements such as attrition, malware, hacking, social tactic, improper usage, train and educate employees, automate identification, data management etc. Present the topic in a bit more detail with this Adopting Strategies By Cyber Attack Type Cyber Attack Risks Mitigation. Use it as a tool for discussion and navigation on Educate Employees, Data Management, Automate Attack Identification. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encrypt And Create Backup Of Useful Data Cyber Attack Risks Mitigation
Encrypt And Create Backup Of Useful Data Cyber Attack Risks MitigationThe following slide illustrates various methods to encrypt and back-up key data to avoid information loss and improved accessibility. It includes elements such as network attached storage, cloud storage services, flat backup system, details, advantages, disadvantages, cost, Deliver an outstanding presentation on the topic using this Encrypt And Create Backup Of Useful Data Cyber Attack Risks Mitigation. Dispense information and present a thorough explanation of Network Attached Storage, Cloud Storage Services, Flat Backup System using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impact Of Cyber Security Policies And Practices Cyber Attack Risks Mitigation
Impact Of Cyber Security Policies And Practices Cyber Attack Risks MitigationThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, etc. Present the topic in a bit more detail with this Impact Of Cyber Security Policies And Practices Cyber Attack Risks Mitigation. Use it as a tool for discussion and navigation on Inadequate Security Guidelines, Inappropriate Privacy Policies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implement Tactics To Prevent Cyber Attacks Cyber Attack Risks Mitigation
Implement Tactics To Prevent Cyber Attacks Cyber Attack Risks MitigationThe following slide illustrates some activities to minimize the probability of cybercrimes within the organization. It includes elements such as utilizing anti virus, preventing to open suspicious emails, keeping systems up to date etc. Introducing Implement Tactics To Prevent Cyber Attacks Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Prevent Opening Suspicious Emails, Keep Systems Up To Date, Leverage Firewalls, using this template. Grab it now to reap its full benefits.
-
 Leverage Strong And Complex Password Management Cyber Attack Risks Mitigation
Leverage Strong And Complex Password Management Cyber Attack Risks MitigationThe following slide illustrates some practices to ensure strong password management and restrict access to data. It includes activities such as avoiding weak passwords, encryption, multi-factor authentication, conducting test etc. Increase audience engagement and knowledge by dispensing information using Leverage Strong And Complex Password Management Cyber Attack Risks Mitigation. This template helps you present information on four stages. You can also present information on Select Strong Password, Multi Factor Authentication, Conduct Password Test using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Monitor And Assess Vendor Risk Management Cyber Attack Risks Mitigation
Monitor And Assess Vendor Risk Management Cyber Attack Risks MitigationThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Introducing Monitor And Assess Vendor Risk Management Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Web Application Security, Infrastructure Security, Vendor Management, using this template. Grab it now to reap its full benefits.
-
 Multiple Strategic Cyber Security Approaches Cyber Attack Risks Mitigation
Multiple Strategic Cyber Security Approaches Cyber Attack Risks MitigationThe following slide depicts various cyber safety approaches to encrypt and back up key data to avoid information loss and improved accessibility. It includes elements such as data, application, infrastructure, network, devices, automation etc. Increase audience engagement and knowledge by dispensing information using Multiple Strategic Cyber Security Approaches Cyber Attack Risks Mitigation. This template helps you present information on one stage. You can also present information on Identities, Organization Policy, Threat Intelligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Organize Cyber Security Training For Employees Regularly Cyber Attack Risks Mitigation
Organize Cyber Security Training For Employees Regularly Cyber Attack Risks MitigationThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Introducing Organize Cyber Security Training For Employees Regularly Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Document Management, Response Process, Social Media Policy, using this template. Grab it now to reap its full benefits.
-
 Passive Active And Offensive Cyber Security Strategies Cyber Attack Risks Mitigation
Passive Active And Offensive Cyber Security Strategies Cyber Attack Risks MitigationThe following slide showcases passive, active and offensive cyber safety techniques to ensure customer data safety. It includes elements such as inspecting vulnerabilities, penetration testing, deception technology, threat hunting etc. Increase audience engagement and knowledge by dispensing information using Passive Active And Offensive Cyber Security Strategies Cyber Attack Risks Mitigation. This template helps you present information on three stages. You can also present information on Passive Safety, Active Safety, Offensive Safety using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Proactive And Reactive Phases Of Cyber Security Cyber Attack Risks Mitigation
Proactive And Reactive Phases Of Cyber Security Cyber Attack Risks MitigationThe following slide depicts the stages of cyber security to avoid information loss and improved accessibility. It includes elements such as managing attack surface, optimizing process, stakeholder engagement etc. Introducing Proactive And Reactive Phases Of Cyber Security Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Proactive, Managing Attack Surface, Optimize Process, Stakeholder Engagement, using this template. Grab it now to reap its full benefits.
-
 Stages Of Implementing Cyber Security Strategies Cyber Attack Risks Mitigation
Stages Of Implementing Cyber Security Strategies Cyber Attack Risks MitigationThe following slide highlights major stages of executing cyber security techniques to ensure effective implementation. It includes elements such as plan, analyze, upgrade, continuous improvement etc. Increase audience engagement and knowledge by dispensing information using Stages Of Implementing Cyber Security Strategies Cyber Attack Risks Mitigation. This template helps you present information on four stages. You can also present information on Plan Strategy, Implement Strategy, Analyse Strategy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Create Cyber Security Strategies Cyber Attack Risks Mitigation
Steps To Create Cyber Security Strategies Cyber Attack Risks MitigationThe following slide illustrates some steps to create and implement cybersecurity techniques. It includes elements such as determining threat type, selecting security framework, optimizing plan, implementing strategy etc. Introducing Steps To Create Cyber Security Strategies Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Comprehend Threat Landscape, Evaluate Cybersecurity Maturity, Optimize Cybersecurity Program, using this template. Grab it now to reap its full benefits.
-
 Strategic Cyber Security Action Plan Cyber Attack Risks Mitigation
Strategic Cyber Security Action Plan Cyber Attack Risks MitigationThe following slide depicts action plan to minimize impact of cyber attacks. It includes elements such as understand, develop, deliver, assess organizational principles, evaluate alternatives, examine possible alternatives, execute actions etc. Increase audience engagement and knowledge by dispensing information using Strategic Cyber Security Action Plan Cyber Attack Risks Mitigation. This template helps you present information on three stages. You can also present information on Understand, Develop, Deliver, Organizational Principles using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategic Framework For Cyber Attack Reduction Cyber Attack Risks Mitigation
Strategic Framework For Cyber Attack Reduction Cyber Attack Risks MitigationThe following slide showcases the framework to plan cyber-attack reduction actions and responsible heads. It includes elements such as strategic, tactical, operational, technical etc. Introducing Strategic Framework For Cyber Attack Reduction Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strategic, Tactical, Operational, Technical, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Cyber Attack Risks Mitigation Strategies Ppt Slides
Table Of Contents For Cyber Attack Risks Mitigation Strategies Ppt SlidesIntroducing Table Of Contents For Cyber Attack Risks Mitigation Strategies Ppt Slides to increase your presentation threshold. Encompassed with fifteen stages, this template is a great option to educate and entice your audience. Dispence information on Security Strategies, Strategic Framework, Password Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response Plan
Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response PlanThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response Plan. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





