Powerpoint Templates and Google slides for ATS
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Latest Technologies Various Types Of Cyber Attacks On System Ppt Slides Backgrounds
Latest Technologies Various Types Of Cyber Attacks On System Ppt Slides BackgroundsThis slide explains Various types of cyber attacks on system on a system such as malware, phishing, man in the middle, distributed denial of service, brute force, SQL injection, and domain name system. Introducing Latest Technologies Various Types Of Cyber Attacks On System Ppt Slides Backgrounds to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Malware, Phishing, Brute Force, using this template. Grab it now to reap its full benefits.
-
 Addressing Role Of Chief Security Officer At Workplace Strategic Organizational Security Plan
Addressing Role Of Chief Security Officer At Workplace Strategic Organizational Security PlanThis slide provides information regarding role of chief security officer at workplace and determine their key priorities in terms of day to day operations, security, compliance, innovation, etc. Present the topic in a bit more detail with this Addressing Role Of Chief Security Officer At Workplace Strategic Organizational Security Plan. Use it as a tool for discussion and navigation on Compliance, Innovation, Security . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Security Policy Framework At Workplace Strategic Organizational Security Plan
Determine Security Policy Framework At Workplace Strategic Organizational Security PlanThis slide provides information about security policy framework at workplace in terms of management, operational procedures, information, personnel, training, crisis management, etc. Deliver an outstanding presentation on the topic using this Determine Security Policy Framework At Workplace Strategic Organizational Security Plan. Dispense information and present a thorough explanation of Company Policies, Management, Operational Procedures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Introducing Security At Workplace To Ensure Assets Safety Strategic Organizational Security Plan
Introducing Security At Workplace To Ensure Assets Safety Strategic Organizational Security PlanThis slide provides information about introducing security at workplace in order to ensure assets safety and details regarding security mission statement and objectives. Increase audience engagement and knowledge by dispensing information using Introducing Security At Workplace To Ensure Assets Safety Strategic Organizational Security Plan. This template helps you present information on four stages. You can also present information on Security Mission Statement, Strategic Security Objectives, Organizational Strategy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
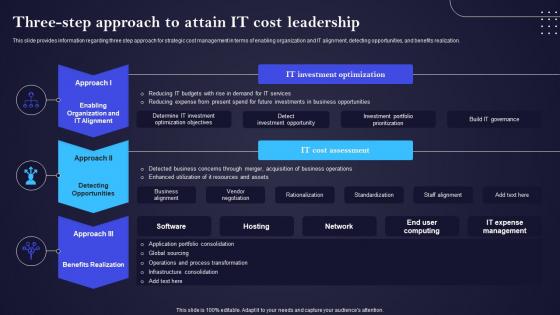 Three Step Approach To Attain It Cost Leadership IT Cost Optimization And Management Strategy SS
Three Step Approach To Attain It Cost Leadership IT Cost Optimization And Management Strategy SSThis slide provides information regarding three step approach for strategic cost management in terms of enabling organization and IT alignment, detecting opportunities, and benefits realization. Present the topic in a bit more detail with this Three Step Approach To Attain IT Cost Leadership IT Cost Optimization And Management Strategy SS. Use it as a tool for discussion and navigation on Approach, Detecting Opportunities, Benefits Realization . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Brand Maintenance Through Effective Deploying Product Branding At Store Brand Branding SS
Brand Maintenance Through Effective Deploying Product Branding At Store Brand Branding SSThis slide provides information regarding implementation of product branding at store in terms of brand identification. It includes identifying product purpose, target audience, core beliefs, close competitor assessment. Increase audience engagement and knowledge by dispensing information using Brand Maintenance Through Effective Deploying Product Branding At Store Brand Branding SS. This template helps you present information on four stages. You can also present information on Analyze Close Competitors, Brand Identification, Product Branding using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Attacks Response Guid Cyber Security Incident Management Checklist During An Incident
Cyber Security Attacks Response Guid Cyber Security Incident Management Checklist During An IncidentThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management during the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using Cyber Security Attacks Response Guid Cyber Security Incident Management Checklist During An Incident. This template helps you present information on one stages. You can also present information on Cyber Security, Incident Management, Checklist During An Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 K56 Deploying Product Branding At Store Transforming Brand Identity Brand Maintenance Branding SS
K56 Deploying Product Branding At Store Transforming Brand Identity Brand Maintenance Branding SSThis slide provides information regarding implementation of product branding at store in terms of transforming brand identity into physical branding. It includes selection colour scheme and mood board, font selection, logo creation, packaging elements. Increase audience engagement and knowledge by dispensing information using K56 Deploying Product Branding At Store Transforming Brand Identity Brand Maintenance Branding SS. This template helps you present information on four stages. You can also present information on Font Selection, Logo Creation, Packaging Elements, Physical Branding using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Three Step Approach To Attain IT Cost Leadership Develop Business Aligned IT Strategy
Three Step Approach To Attain IT Cost Leadership Develop Business Aligned IT StrategyThis slide provides information regarding three step approach for strategic cost management in terms of enabling organization and IT alignment, detecting opportunities, and benefits realization. Present the topic in a bit more detail with this Three Step Approach To Attain IT Cost Leadership Develop Business Aligned IT Strategy. Use it as a tool for discussion and navigation on Enabling Organization, Detecting Opportunities, Benefits Realization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agenda For Cyber Security Attacks Response Plan Ppt Infographic Template Background Images
Agenda For Cyber Security Attacks Response Plan Ppt Infographic Template Background ImagesIntroducing Agenda For Cyber Security Attacks Response Plan Ppt Infographic Template Background Images to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Security, Attacks Response Plan, Security Incidents, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Comparative Analysis Of Cyber Security Incident Mitigation Software
Cyber Security Attacks Response Comparative Analysis Of Cyber Security Incident Mitigation SoftwareThis slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Comparative Analysis Of Cyber Security Incident Mitigation Software. Use it as a tool for discussion and navigation on Comparative Analysis, Cyber Security Incident, Mitigation Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Cyber Security Incident Management Team Roles And Responsibilities
Cyber Security Attacks Response Cyber Security Incident Management Team Roles And ResponsibilitiesPresent the topic in a bit more detail with this Cyber Security Attacks Response Cyber Security Incident Management Team Roles And Responsibilities. Use it as a tool for discussion and navigation on Cyber Security Incident, Management Team, Roles And Responsibilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Gap Analysis Representing Current Situation Of Cybersecurity Incident
Cyber Security Attacks Response Gap Analysis Representing Current Situation Of Cybersecurity IncidentThis slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Present the topic in a bit more detail with this Cyber Security Attacks Response Gap Analysis Representing Current Situation Of Cybersecurity Incident. Use it as a tool for discussion and navigation on Gap Analysis, Representing Current Situation, Cybersecurity Incident, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Impact Of Implementing Cyber Security Incident Management
Cyber Security Attacks Response Impact Of Implementing Cyber Security Incident ManagementThis slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Impact Of Implementing Cyber Security Incident Management. Dispense information and present a thorough explanation of Cyber Security Incident, Management On Organization, Software Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Key Lessons Learned By Organization From Cyber Security Incident
Cyber Security Attacks Response Key Lessons Learned By Organization From Cyber Security IncidentIncrease audience engagement and knowledge by dispensing information using Cyber Security Attacks Response Key Lessons Learned By Organization From Cyber Security Incident. This template helps you present information on three stages. You can also present information on Key Lessons Learned By Organization, Cyber Security, Incident Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Attacks Response Plan Benefits Of Implementing Web Application Firewall
Cyber Security Attacks Response Plan Benefits Of Implementing Web Application FirewallThis slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Benefits Of Implementing Web Application Firewall. Use it as a tool for discussion and navigation on Fights Vulnerabilities, Application Firewall, Confidential Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Best Practices For Cybersecurity Incident Management
Cyber Security Attacks Response Plan Best Practices For Cybersecurity Incident ManagementThis slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Introducing Cyber Security Attacks Response Plan Best Practices For Cybersecurity Incident Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Incident Management Process, Incident Management Plan, Responsibilities, Team Members, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Plan Common Sources Of Precursors And Indicators
Cyber Security Attacks Response Plan Common Sources Of Precursors And IndicatorsThis slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Common Sources Of Precursors And Indicators. Use it as a tool for discussion and navigation on Precursors And Indicators, Suspicious Data, Identify Malicious Activity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Comparative Analysis Of Web Application Firewall Products
Cyber Security Attacks Response Plan Comparative Analysis Of Web Application Firewall ProductsThis slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Comparative Analysis Of Web Application Firewall Products. Dispense information and present a thorough explanation of Comparative Analysis, Web Application, Firewall Products using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Cyber Security Attacks Response Plan For Table Of Contents
Cyber Security Attacks Response Plan Cyber Security Attacks Response Plan For Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Cyber Security Attacks Response Plan Cyber Security Attacks Response Plan For Table Of Contents. This template helps you present information on one stages. You can also present information on Cyber Security Attacks, Response Plan, Incident Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Attacks Response Plan Cyber Security Crisis Management Action Plan Timeline
Cyber Security Attacks Response Plan Cyber Security Crisis Management Action Plan TimelineThis slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Cyber Security Crisis Management Action Plan Timeline. Use it as a tool for discussion and navigation on Incident Response, Business Continuity, Review And Recovery, Management Action, Plan Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Cyber Security Event And Incident Flow Diagram
Cyber Security Attacks Response Plan Cyber Security Event And Incident Flow DiagramThis slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Cyber Security Event And Incident Flow Diagram. Dispense information and present a thorough explanation of Cyber Security Event, Incident Flow Diagram, Business Operations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Cyber Security Incident Handler Contact Information
Cyber Security Attacks Response Plan Cyber Security Incident Handler Contact InformationThis slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Cyber Security Incident Handler Contact Information. Use it as a tool for discussion and navigation on Cyber Security, Incident Handler, Contact Information, Forensic Expert. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Cyber Security Incident Response Plan Timeline
Cyber Security Attacks Response Plan Cyber Security Incident Response Plan TimelineThis slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Cyber Security Incident Response Plan Timeline. Dispense information and present a thorough explanation of Cyber Security, Incident Response, Plan Timeline, Operations Resume using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Cyber Security Incidents Follow Up Report
Cyber Security Attacks Response Plan Cyber Security Incidents Follow Up ReportThis slide represents the follow up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Cyber Security Incidents Follow Up Report. Use it as a tool for discussion and navigation on Cyber Security Incidents, Follow Up Report, Management Team. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Cyber Security Threats Detection Techniques
Cyber Security Attacks Response Plan Cyber Security Threats Detection TechniquesThis slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Cyber Security Threats Detection Techniques. Dispense information and present a thorough explanation of Cyber Security Threats, Detection Techniques, Compromised Credentials using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Five Phases Of Cybersecurity Incident Management
Cyber Security Attacks Response Plan Five Phases Of Cybersecurity Incident ManagementThis slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Introducing Cyber Security Attacks Response Plan Five Phases Of Cybersecurity Incident Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Plan And Prepare, Post Incident Activity, Assess And Design, Incident Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Plan Impact Of Cybersecurity Incidents On Organization
Cyber Security Attacks Response Plan Impact Of Cybersecurity Incidents On OrganizationThis slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Attacks Response Plan Impact Of Cybersecurity Incidents On Organization. This template helps you present information on six stages. You can also present information on Reputational Damage, Stolen Intellectual Property, Altered Business Practices, Operational Disruption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Attacks Response Plan Key Issues Faced By Organization Due To Cybersecurity Incidents
Cyber Security Attacks Response Plan Key Issues Faced By Organization Due To Cybersecurity IncidentsThis slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Introducing Cyber Security Attacks Response Plan Key Issues Faced By Organization Due To Cybersecurity Incidents to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Faced By Organization Due, Cybersecurity Incidents, Confidential Information , using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Plan Key Parameters To Select Cyber Security Containment Strategy
Cyber Security Attacks Response Plan Key Parameters To Select Cyber Security Containment StrategyThis slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Attacks Response Plan Key Parameters To Select Cyber Security Containment Strategy. This template helps you present information on five stages. You can also present information on Cyber Security, Containment Strategy, Incident Management Solutions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Attacks Response Plan Strategies To Analyze Cyber Security Incidents
Cyber Security Attacks Response Plan Strategies To Analyze Cyber Security IncidentsThis slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Introducing Cyber Security Attacks Response Plan Strategies To Analyze Cyber Security Incidents to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Profile Network And Systems, Understand Normal Behaviors, Perform Event Correlation, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Plan Various Cyber Security Incidents Detected By It Department
Cyber Security Attacks Response Plan Various Cyber Security Incidents Detected By It DepartmentThis slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Attacks Response Plan Various Cyber Security Incidents Detected By It Department. This template helps you present information on five stages. You can also present information on Insider Threat, Phishing Attack, Malware Attack, Password Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Attacks Response Plan Ways To Detect Cyber Security Incidents
Cyber Security Attacks Response Plan Ways To Detect Cyber Security IncidentsThis slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Introducing Cyber Security Attacks Response Plan Ways To Detect Cyber Security Incidents to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Privileged User Accounts, Outbound Network Traffic, Changes In Configuration, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response User Awareness Training Program To Prevent Cyber Security Incidents
Cyber Security Attacks Response User Awareness Training Program To Prevent Cyber Security IncidentsThis slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response User Awareness Training Program To Prevent Cyber Security Incidents. Dispense information and present a thorough explanation of User Awareness, Training Program, Prevent Cyber Security Incidents using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incident Communication Strategy Cyber Security Attacks Response Plan
Cyber Security Incident Communication Strategy Cyber Security Attacks Response PlanThis slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. Introducing Cyber Security Incident Communication Strategy Cyber Security Attacks Response Plan to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Senior Management, Communication Strategy, Stakeholder Needs, Suppliers, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Handling Checklist Cyber Security Attacks Response Plan
Cyber Security Incident Handling Checklist Cyber Security Attacks Response PlanThis slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post incident activity. Present the topic in a bit more detail with this Cyber Security Incident Handling Checklist Cyber Security Attacks Response Plan. Use it as a tool for discussion and navigation on Containment, Eradication And Recovery, Detection And Analysis, Handling Checklist Acquisition. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Management Checklist After An Incident Cyber Security Attacks Response
Cyber Security Incident Management Checklist After An Incident Cyber Security Attacks ResponseThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Checklist After An Incident Cyber Security Attacks Response. This template helps you present information on one stages. You can also present information on Cyber Security, Incident Management, Checklist After An Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Management Team Structure Cyber Security Attacks Response Plan
Cyber Security Incident Management Team Structure Cyber Security Attacks Response PlanThis slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team. Deliver an outstanding presentation on the topic using this Cyber Security Incident Management Team Structure Cyber Security Attacks Response Plan. Dispense information and present a thorough explanation of Cyber Security, Incident Management, Team Structure, Human Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incident Response Lifecycle Cyber Security Attacks Response Plan
Cyber Security Incident Response Lifecycle Cyber Security Attacks Response PlanThis slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Deliver an outstanding presentation on the topic using this Cyber Security Incident Response Lifecycle Cyber Security Attacks Response Plan. Dispense information and present a thorough explanation of Preparation, Detection And Analysis, Containment Eradication And Recovery using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incident Response Process Flow Chart Cyber Security Attacks Response Plan
Cyber Security Incident Response Process Flow Chart Cyber Security Attacks Response PlanThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Present the topic in a bit more detail with this Cyber Security Incident Response Process Flow Chart Cyber Security Attacks Response Plan. Use it as a tool for discussion and navigation on Cyber Threat Intelligence, Agency User Reporting, Instrumentation, Cyber Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response Plan
Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response PlanThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response Plan. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Icons Slide For Cyber Security Attacks Response Plan Ppt Infographic Template Backgrounds
Icons Slide For Cyber Security Attacks Response Plan Ppt Infographic Template BackgroundsIntroducing our well researched set of slides titled Icons Slide For Cyber Security Attacks Response Plan Ppt Infographic Template Backgrounds. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table Of Contents For Cyber Security Attacks Response Plan Ppt Infographic Template Deck
Table Of Contents For Cyber Security Attacks Response Plan Ppt Infographic Template DeckIntroducing Table Of Contents For Cyber Security Attacks Response Plan Ppt Infographic Template Deck to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Dashboards, Cyber Security, Incident Management, Incident Response Management, using this template. Grab it now to reap its full benefits.
-
 Omnichannel Strategies For Digital Loan Application Through Bank Atm Machines
Omnichannel Strategies For Digital Loan Application Through Bank Atm MachinesThis slide covers services offered by BankWorld ATM to its customers to provide them with omnichannel experience. It includes services such as balance inquiry, cashwithrawal facilities, bill payments, online deposits, personal loans, ATM services, etc. Introducing Omnichannel Strategies For Digital Loan Application Through Bank Atm Machines to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Balance Inquiry, Cash Withdrawal, Funds Transfer, Loan Services, using this template. Grab it now to reap its full benefits.
-
 Achieving Data Lineage At Phases Of Data Pipeline Data Lineage Types It
Achieving Data Lineage At Phases Of Data Pipeline Data Lineage Types ItThis slide outlines the process of achieving data lineage at various phases of the data pipelines, and the steps include data ingestion, data processing, query history and data lakes. It is mandatory to keep track of every operation or process performed on the data. Introducing Achieving Data Lineage At Phases Of Data Pipeline Data Lineage Types It to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Data Ingestion, Data Processing, Query History, using this template. Grab it now to reap its full benefits.
-
 Sports Flag Athletes Competition Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Sports Flag Athletes Competition Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Sports flag athletes competition colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Sports Flag Athletes Competition Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Sports Flag Athletes Competition Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Sports flag athletes competition monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Attention Detail In Powerpoint And Google Slides Cpb
Attention Detail In Powerpoint And Google Slides CpbPresenting our Attention Detail In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Attention Detail. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 DDOS Attack In Powerpoint And Google Slides Cpb
DDOS Attack In Powerpoint And Google Slides CpbPresenting DDOS Attack In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like DDOS Attack. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Broadcasting Marketing To Gain Viewers Attention Increasing Sales Through Traditional Media
Broadcasting Marketing To Gain Viewers Attention Increasing Sales Through Traditional MediaThis slide showcases broadcasting marketing to generate leads and conversions. It includes creating brand exposure and enlarging the top of funnel to gain customers. Introducing Broadcasting Marketing To Gain Viewers Attention Increasing Sales Through Traditional Media to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Unaware, Aware, Interested, Evaluating, using this template. Grab it now to reap its full benefits.
-
 Steps To Build Employee Collaboration At Workplace
Steps To Build Employee Collaboration At WorkplaceThis slide highlights steps to build employee collaboration aimed to develop trust by acknowledging ideas and feedback and make them feel accepted by peers. It covers avoiding wasteful meetings, implementing technologies and accepting feedback or udeas. Introducing our premium set of slides with Steps To Build Employee Collaboration At Workplace. Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Avoid Wasteful Meetings, Implement Right Technologies. So download instantly and tailor it with your information.
-
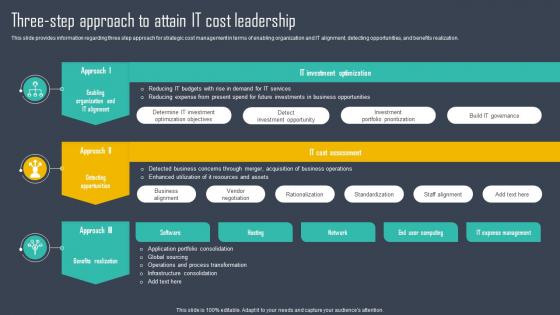 Strategic Framework To Manage IT Three Step Approach To Attain It Cost Leadership Strategy SS
Strategic Framework To Manage IT Three Step Approach To Attain It Cost Leadership Strategy SSThis slide provides information regarding three step approach for strategic cost management in terms of enabling organization and IT alignment, detecting opportunities, and benefits realization. Deliver an outstanding presentation on the topic using this Strategic Framework To Manage IT Three Step Approach To Attain It Cost Leadership Strategy SS. Dispense information and present a thorough explanation of Determine IT Investment, Detect Investment Opportunity, Investment Portfolio Prioritization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cost Revenue Optimization Revise Existing Products Price To Attain Cost Leadership
Cost Revenue Optimization Revise Existing Products Price To Attain Cost LeadershipThis slide provides information regarding an initiative by firm to alter the price of existing products which are considered as overpriced by customer. The initiative will help firm in boosting the sale of such products and attain cost leadership. Deliver an outstanding presentation on the topic using this Cost Revenue Optimization Revise Existing Products Price To Attain Cost Leadership. Dispense information and present a thorough explanation of Brand, Forecasted Growth, Sales using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Practices for structuring bonus program at workplace
Practices for structuring bonus program at workplaceThis slide presents practices to structure a bonus and incentive plan to motivate and engage employees. It includes key elements such as engage appropriate people, mind map bonus program and implement program. Presenting our set of slides with practices for structuring bonus program at workplace. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Appropriate, Program, Implement.
-
 K55 Cyber Security Attacks Response Cyber Security Incident Management Checklist Before
K55 Cyber Security Attacks Response Cyber Security Incident Management Checklist BeforeThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management before the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using K55 Cyber Security Attacks Response Cyber Security Incident Management Checklist Before. This template helps you present information on one stages. You can also present information on Cyber Security, Incident Management, Checklist Before An Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Atm Self Service Technology Machine Icon
Atm Self Service Technology Machine IconIntroducing our Atm Self Service Technology Machine Icon set of slides. The topics discussed in these slides are Service, Technology. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Lineage Importance It Achieving Data Lineage At Phases Of Data Pipeline
Data Lineage Importance It Achieving Data Lineage At Phases Of Data PipelineThis slide outlines the process of achieving data lineage at various phases of the data pipelines, and the steps include data ingestion, data processing, query history and data lakes. It is mandatory to keep track of every operation or process performed on the data. Present the topic in a bit more detail with this Data Lineage Importance It Achieving Data Lineage At Phases Of Data Pipeline. Use it as a tool for discussion and navigation on Data Ingestion, Data Processing, Query History. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Running Employee Wellness Program At Workplace Employee Retention Strategies To Reduce Staffing Cost
Running Employee Wellness Program At Workplace Employee Retention Strategies To Reduce Staffing CostThe purpose of this slide is to showcase a comprehensive wellness program that can be undertaken by corporates to improve the mental health of employees. It covers information about the campaign objectives, trainer details, types of activities, description, and duration. Deliver an outstanding presentation on the topic using this Running Employee Wellness Program At Workplace Employee Retention Strategies To Reduce Staffing Cost. Dispense information and present a thorough explanation of Meditation, Stretching, Workplace using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Flight Attendant Salary United In Powerpoint And Google Slides Cpb
Flight Attendant Salary United In Powerpoint And Google Slides CpbPresenting our Flight Attendant Salary United In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Flight Attendant Salary United. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Volume Based Dos Attacks In Powerpoint And Google Slides Cpb
Volume Based Dos Attacks In Powerpoint And Google Slides CpbPresenting Volume Based Dos Attacks In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase Three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Volume Based Dos Attacks. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.





