Powerpoint Templates and Google slides for ATS
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Strategies For Promoting Global Mindset At Business Global Market Expansion For Product
Strategies For Promoting Global Mindset At Business Global Market Expansion For ProductThe slide highlights various strategies for creating a global mindset at workplace to ensure successful product market expansion. Various strategies included are inter organizational discussions, get international expertise, ensure transparency, etc.Introducing Strategies For Promoting Global Mindset At Business Global Market Expansion For Product to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Inter Organizational Discussions, Learning Environment, Cultural Relationships, using this template. Grab it now to reap its full benefits.
-
 Attention Grabbing Marketing In Powerpoint And Google Slides Cpb
Attention Grabbing Marketing In Powerpoint And Google Slides CpbPresenting Attention Grabbing Marketing In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Attention Grabbing Marketing. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Edge Computing Technology Use Case Data Aggregation At Edge For Smart Parking AI SS
Edge Computing Technology Use Case Data Aggregation At Edge For Smart Parking AI SSThis slide showcases use case of data aggregation at edge for smart parking, which helps developers of this technology to further enhance their devices. It provides details about network intersection, model training, etc. Increase audience engagement and knowledge by dispensing information using Edge Computing Technology Use Case Data Aggregation At Edge For Smart Parking AI SS. This template helps you present information on three stages. You can also present information on Use Case Scenario, Edge Intersection And Processing, Hybrid Edge Deployment, Data Aggregation At Edge using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Inside Nike A Deep Dive Using Athletes For Nikes Influencer Marketing Strategy SS V
Inside Nike A Deep Dive Using Athletes For Nikes Influencer Marketing Strategy SS VThis slide showcases how Nike uses athletes to influence its target audiences to make purchases and generate sales. It includes Sponsorships, Product Promotion, Social Media Campaign, Brand Ambassadors and Personalized Campaigns. Increase audience engagement and knowledge by dispensing information using Inside Nike A Deep Dive Using Athletes For Nikes Influencer Marketing Strategy SS V This template helps you present information on Five stages. You can also present information on Establish Own Platform, Build Customer Interest, Build Ecosystem using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda For Phishing Attacks And Strategies To Mitigate Them V2 Ppt Ideas Infographic Template
Agenda For Phishing Attacks And Strategies To Mitigate Them V2 Ppt Ideas Infographic TemplateIntroducing Agenda For Phishing Attacks And Strategies To Mitigate Them V2 Ppt Ideas Infographic Template to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Phishing Attacks, Phishing Techniques, Working Structure, Awareness Training Program, using this template. Grab it now to reap its full benefits.
-
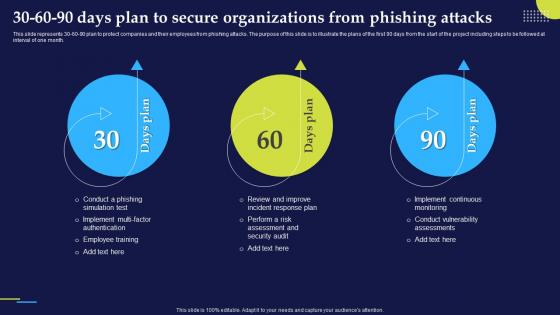 Phishing Attacks And Strategies To Mitigate Them V2 30 60 90 Days Plan To Secure Organizations
Phishing Attacks And Strategies To Mitigate Them V2 30 60 90 Days Plan To Secure OrganizationsThis slide represents 30-60-90 plan to protect companies and their employees from phishing attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 30 60 90 Days Plan To Secure Organizations. This template helps you present information on three stages. You can also present information on Phishing Attacks, Implement Continuous Monitoring, Conduct Vulnerability Assessments using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Angler Phishing Working And Example
Phishing Attacks And Strategies To Mitigate Them V2 About Angler Phishing Working And ExampleThis slide talks about the angler phishing attacks conducted on internet using social media platforms. The purpose of this slide is to illustrate how fraudulent tweets or texts containing malicious links and misleading information, can be used by scammers to trick individuals. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 About Angler Phishing Working And Example. Use it as a tool for discussion and navigation on Angler Phishing Attacks, Social Media Platforms, Fraudulent Tweets, Texts Containing Malicious, Misleading Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Email Phishing Overview And Impact
Phishing Attacks And Strategies To Mitigate Them V2 About Email Phishing Overview And ImpactThis slide talks about the email phishing cyber scams in which attacker sends fake mails to the target. The purpose of this slide to provide few examples of cyber phishing emails containing malicious links and attachments to target different organizations. Introducing Phishing Attacks And Strategies To Mitigate Them V2 About Email Phishing Overview And Impact to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Legitimate Business, Generic Requests, Dangerous Websites, Login Information, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Evil Twin Phishing Overview And Example
Phishing Attacks And Strategies To Mitigate Them V2 About Evil Twin Phishing Overview And ExampleThis slide talks about evil twin cyber attacks. The purpose of this slide is to outline the types of information that can be accessed by scammers of evil twin attacks. This slide also illustrates the flow of evil twin scams which include legitimate Wi-Fi, fake access point, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 About Evil Twin Phishing Overview And Example. Dispense information and present a thorough explanation of Users Network Activity, Secret Login Information, Twin Cyber Attacks, Service Set Identifier using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Identity Theft Overview And Techniques
Phishing Attacks And Strategies To Mitigate Them V2 About Identity Theft Overview And TechniquesThis slide talks about the major crime committed by phishers named as identity theft. The purpose of this slide is to outline the ways of stealing information such as robbery, computer fraud, social networking sites, mail theft and dumpster diving. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 About Identity Theft Overview And Techniques. Use it as a tool for discussion and navigation on Shady Internet Schemes, Private Government Records, Social Media Account, Social Security Card. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Man In The Middle Phishing Scams Overview
Phishing Attacks And Strategies To Mitigate Them V2 About Man In The Middle Phishing Scams OverviewThis slide demonstrates the idea behind man-in-the-middle phishing attacks. The purpose of this slide is to illustrate the concept of MITM attack by comparing normal scenario and MITM attack which includes attacker, proxy server, real website, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 About Man In The Middle Phishing Scams Overview. Dispense information and present a thorough explanation of Attacker Secretly Monitors, Manipulate Sensitive, Personal Information, Online Banking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Pharming Phishing Identification
Phishing Attacks And Strategies To Mitigate Them V2 About Pharming Phishing IdentificationThis slide talks about the pharming phishing cyber scams. The purpose of this slide is to illustrate the ways of recognizing pharming scams such as URL, design and HTTP vs HTTPS. This slide also illustrates the architecture of pharming phishing attack. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 About Pharming Phishing Identification. Use it as a tool for discussion and navigation on Uniform Resource Locator, Hypertext Transfer Protocol, Hypertext Transfer Protocol Secure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Phishing Attacks Overview And Impact
Phishing Attacks And Strategies To Mitigate Them V2 About Phishing Attacks Overview And ImpactThis slide demonstrates the overview of cyber phishing attacks. The purpose of this slide is to talk about the effectiveness of phishing scams. This slide also outlines the issues which can be caused by phishing attacks such as disclosure of private data, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 About Phishing Attacks Overview And Impact. This template helps you present information on five stages. You can also present information on Malware Injections, Compromised Accounts, Financial Penalties, Illicit Transactions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Pop Up Phishing Overview And Examples
Phishing Attacks And Strategies To Mitigate Them V2 About Pop Up Phishing Overview And ExamplesThis slide talks about the pop-up phishing attacks conducted by sending pop-up messages to the targets. The purpose of this slide is to illustrate how fraudulent and mis-leading pop-ups are displayed to the users which are clone of the original pop-ups. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 About Pop Up Phishing Overview And Examples. Dispense information and present a thorough explanation of Original System Pop Up, Phishing Pop Up, Fraudulent, Mis Leading Pop Ups using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Search Engine Phishing Overview
Phishing Attacks And Strategies To Mitigate Them V2 About Search Engine Phishing OverviewThis slide talks about search engine phishing scams. The purpose of this slide is to explain how phishers use their own-built websites to trick victims. This slide also represents examples of search engine phishing websites which are indexed by reliable browsers. Introducing Phishing Attacks And Strategies To Mitigate Them V2 About Search Engine Phishing Overview to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Commit Fraud Against User, Steal Users Identity, Harm Victims Reputation, Reliable Search Engines, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Smishing Attacks Working And Example
Phishing Attacks And Strategies To Mitigate Them V2 About Smishing Attacks Working And ExampleThis slide talks about the smishing cyber attacks conducted by sending text messages to the targets. The purpose of this slide is to illustrate how fraudulent texts are sent to the users which contains malicious links and other mis-leading information. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 About Smishing Attacks Working And Example. This template helps you present information on three stages. You can also present information on Personal Information, Contains Malicious Link, Fraudulent Activities, Smishing Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Spear Phishing Overview And Example
Phishing Attacks And Strategies To Mitigate Them V2 About Spear Phishing Overview And ExampleThis slide talks about spear phishing cyber attacks in which scammer targets a specific individual or specific group of persons. The purpose of this slide is to illustrate example of a mail used by phishers to conduct spear phishing cyber attacks. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 About Spear Phishing Overview And Example. Use it as a tool for discussion and navigation on Huge Corporations, Employees Receive Requests, Unfamiliar People, Spear Phishing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Vishing Attacks Overview And Identification
Phishing Attacks And Strategies To Mitigate Them V2 About Vishing Attacks Overview And IdentificationThis slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 About Vishing Attacks Overview And Identification. Dispense information and present a thorough explanation of Personal Information, Fraudsters Fake, Internal Revenue Service, Signs Of Vishing Attack using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Whale Phishing CEO Fraud Overview
Phishing Attacks And Strategies To Mitigate Them V2 About Whale Phishing CEO Fraud OverviewThis slide talks about the whaling phishing attack which is also known as CEO fraud. The purpose of this slide is to explain how attackers target senior executives of organizations to conduct whale phishing cyber attacks by sending fraud mails to the employees. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 About Whale Phishing CEO Fraud Overview. Use it as a tool for discussion and navigation on Attacks Targeting Senior Executives, Fraud Mails, Phishing Cyber Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Benefits Of Comprehensive Training Programs
Phishing Attacks And Strategies To Mitigate Them V2 Benefits Of Comprehensive Training ProgramsThis slide outlines the benefits of comprehensive training programs in organizations. These include align with company database, instructional library, auto-enrolment service, inform about real risks, track and evaluate and plan a year ahead. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Benefits Of Comprehensive Training Programs to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Instructional Library, Track And Evaluate, Automatically Manage Phishing Trainees, Cyber Security Microlessons, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Checklist To Secure Organizations From Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Checklist To Secure Organizations From PhishingThis slide outlines the steps to be taken to protect the organization and its employees from phishing attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Checklist To Secure Organizations From Phishing. Use it as a tool for discussion and navigation on Phishing Attacks, Real Time Monitoring, Spam Filters, Multi Factor Authentication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Clone Phishing Attacks Preventive Measures
Phishing Attacks And Strategies To Mitigate Them V2 Clone Phishing Attacks Preventive MeasuresThis slide talks about the various steps that can be taken to prevent clone phishing attacks. These include review senders address, preview links before opening them, use a password manager, investigate spoofed replies, double check URL addresses, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Clone Phishing Attacks Preventive Measures. This template helps you present information on eight stages. You can also present information on Investigate Spoofed Replies, Clone Phishing Attacks Preventive, Resemble Authentic Email Addresses using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Different Types Of Smishing Cyber Scams
Phishing Attacks And Strategies To Mitigate Them V2 Different Types Of Smishing Cyber ScamsThis slide talks about the various types of smishing cyber attacks. The purpose of this slide is to briefly explain different techniques of smishing scams used by the attackers to scam users. These are covid-19 smishing, financial services smishing, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Different Types Of Smishing Cyber Scams to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Smishing Scams, Financial Services Smishing, Gift Smishing, Customer Support Smishing, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Examples Of Clone Phishing Cyber Scams
Phishing Attacks And Strategies To Mitigate Them V2 Examples Of Clone Phishing Cyber ScamsThis slide demonstrates the various examples of clone phishing cyber scams. The purpose of this slide is to illustrate different types of clone phishing emails targeting different individuals. These include customer support scams, fake virus scams and refund scams. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Examples Of Clone Phishing Cyber Scams. This template helps you present information on three stages. You can also present information on Customer Support Scams, Fake Virus Scams, Refund Scams, Clone Phishing Cyber Scams using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Execution Of Man In The Middle Cyber Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Execution Of Man In The Middle Cyber AttacksThis slide illustrates the process of executing man-in-the-middle cyber attacks. The purpose of this slide is to outline the two stages of execution of MITM scams. These stages are interception and decryption. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Execution Of Man In The Middle Cyber Attacks. Use it as a tool for discussion and navigation on Cyber Attacks, Interception And Decryption, Online Data Transfer, Intercepting User Traffic. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 For Table Of Contents
Phishing Attacks And Strategies To Mitigate Them V2 For Table Of ContentsIntroducing Phishing Attacks And Strategies To Mitigate Them V2 For Table Of Contents to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Overview And Identification, Working, Vishing Cyber Scams In Businesses, Preventive Measures, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Guidelines To Stay Safe From Phishing Scams
Phishing Attacks And Strategies To Mitigate Them V2 Guidelines To Stay Safe From Phishing ScamsThis slide outlines the various preventive measures to stay safe from phishing attacks. These include know how to spot phishing scams, avoid clicking that link, install free anti-phishing extensions, change passwords regularly, install firewalls, never miss updates, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Guidelines To Stay Safe From Phishing Scams. This template helps you present information on five stages. You can also present information on Reveal Sensitive Information, Change Passwords Regularly, Information To Unsafe Websites, Avoid Clicking That Link using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 How Does A Phishing Attack Work
Phishing Attacks And Strategies To Mitigate Them V2 How Does A Phishing Attack WorkThis slide demonstrates the working flow of a phishing attack. The purpose of this slide is to outline the various phases of phishing scams such as campaign crafted, payloads, impersonation, execution, ransomware and encrypts on target. Introducing Phishing Attacks And Strategies To Mitigate Them V2 How Does A Phishing Attack Work to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Campaign Crafted, Payloads, Impersonation, Execution, Encrypts On Target, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 How Does Vishing Attack Works
Phishing Attacks And Strategies To Mitigate Them V2 How Does Vishing Attack WorksThis slide illustrates the working procedure of a vishing attack. The purpose of this slide is to explain the working flow of vishing cyber attack. The key components include attacker, target, spoofed caller ID, SMS to victim, file execution confirmation, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 How Does Vishing Attack Works. Use it as a tool for discussion and navigation on Execution Confirmation, Sending Confirmation, Vishing Attack Works. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 How To Protect Users From Vishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 How To Protect Users From Vishing AttacksThis slide talks about the ways to protect users from vishing attacks. These include avoid calls from robots, never respond to audio-automated calls, verify the identity of the caller, never share personal information over the call, use multi-factor authentication, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 How To Protect Users From Vishing Attacks. Dispense information and present a thorough explanation of Vishing Attacks, Audio Automated Calls, Personal Information, Multi Factor Authentication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Identification And Prevention Of Angler Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Identification And Prevention Of Angler PhishingThis slide talks about the various methods of identifying angler phishing cyber attacks. The purpose of this slide is to help users identify angler phishing scams. These include notifications, abnormal direct messages, links to the different websites, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Identification And Prevention Of Angler Phishing. Use it as a tool for discussion and navigation on Identification And Prevention, Angler Phishing Scams, Abnormal Direct Messages, Credentials In Direct Messages. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Man In The Middle MITM Phishing Attack Diagram
Phishing Attacks And Strategies To Mitigate Them V2 Man In The Middle MITM Phishing Attack DiagramThis slide demonstrates the working flow of man-in-the-middle phishing attacks using MITM phishing toolkit cloud server. This slide also elaborates the various real-world examples of MITM attacks such as Equifaxs mobile application, superfish and DigiNotar. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Man In The Middle MITM Phishing Attack Diagram. Dispense information and present a thorough explanation of Phishing Attack Diagram, Equifaxs Mobile Application, Toolkit Cloud Server, Intended Website Server using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
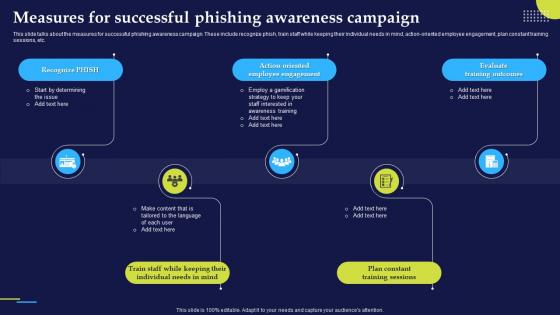 Phishing Attacks And Strategies To Mitigate Them V2 Measures For Successful Phishing Awareness Campaign
Phishing Attacks And Strategies To Mitigate Them V2 Measures For Successful Phishing Awareness CampaignThis slide talks about the measures for successful phishing awareness campaign. These include recognize phish, train staff while keeping their individual needs in mind, action-oriented employee engagement, plan constant training sessions, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Measures For Successful Phishing Awareness Campaign to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Action Oriented Employee Engagement, Evaluate Training Outcomes, Phishing Awareness Campaign, Plan Constant Training Sessions, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Multi Layered Approach To Phishing Defenses
Phishing Attacks And Strategies To Mitigate Them V2 Multi Layered Approach To Phishing DefensesThis slide represents the multi-layered approach to phishing defenses. These include create difficulty for attackers to reach users, guide users in identifying and reporting phishing emails, save your organization from unexpected phishing scams, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Multi Layered Approach To Phishing Defenses. Use it as a tool for discussion and navigation on Multi Layered Approach, Reporting Phishing Emails, Unexpected Phishing Scams. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Pharming Phishing Types And Prevention Techniques
Phishing Attacks And Strategies To Mitigate Them V2 Pharming Phishing Types And Prevention TechniquesThis slide demonstrates the different types pf pharming phishing scams. The primary types include malware-based pharming and DNS pharming. This slide also outlines the ways which helps to prevent a pharming attack such as verify the URL, install VPN, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Pharming Phishing Types And Prevention Techniques. Dispense information and present a thorough explanation of Pharming Phishing Scams, Malware Based Pharming, Pharming Attack, Prevention Techniques using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Phishing Awareness Training Program For Employees
Phishing Attacks And Strategies To Mitigate Them V2 Phishing Awareness Training Program For EmployeesThis slide represents the training program for employees which will help them to prevent various cyber security scams in business. The purpose of this slide is to outline the mode, venue and schedule for the different training programs. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Phishing Awareness Training Program For Employees. This template helps you present information on one stages. You can also present information on Phishing Awareness Training, Program For Employees, Training Programs, Security Scams In Business using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Popular Man In The Middle Phishing Kits Used
Phishing Attacks And Strategies To Mitigate Them V2 Popular Man In The Middle Phishing Kits UsedThis slide outlines the various phishing kits used by attackers to conduct man-in-the-middle scams. The purpose of thus slide is to describe the reported year and use of different MITM kits such as Evilginx2, Modlishka, Muraena, EvilnoVNC and EvilProxy. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Popular Man In The Middle Phishing Kits Used. Use it as a tool for discussion and navigation on Creates Special Tokens, Uniform Resource Locator, Expose Phishing Content, Stolen Session Cookie. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Preventive Measures For Man In The Middle Cyber
Phishing Attacks And Strategies To Mitigate Them V2 Preventive Measures For Man In The Middle CyberThis slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Preventive Measures For Man In The Middle Cyber to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Secure Connections, Avoid Phishing Emails, Endpoint Security, Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Primary Techniques Employed In Phishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Primary Techniques Employed In Phishing AttacksThis slide demonstrates the ways utilized by phishers to attack victims. The purpose of this slide is to outline the different methods used by attackers to trick victims. The primary means of attacks are text messages, emails and phone calls from unknown sources. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Primary Techniques Employed In Phishing Attacks. This template helps you present information on three stages. You can also present information on Primary Techniques Employed, Phishing Attacks, Phishers To Attack Victims, Attackers To Trick Victims using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Real World Examples Of Smishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Real World Examples Of Smishing AttacksThis slide demonstrates the real-world example of smishing cyber attacks which targeted different individuals and organizations. The popular scams are early access apple iPhone 12 scam, USPS and FedEx scams and mandatory online COVID-19 test scam. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Real World Examples Of Smishing Attacks to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Real World Examples, Smishing Attacks, Smishing Cyber Attacks, Individuals And Organizations, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Resources And Training That Companies Can Provide
Phishing Attacks And Strategies To Mitigate Them V2 Resources And Training That Companies Can ProvideThis slide demonstrates the resources and training that can be provided by companies to their staff. These include employee training, check to see if you have already been breached, be aware of the various phishing attacks, invest in security education, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Resources And Training That Companies Can Provide. This template helps you present information on five stages. You can also present information on Employee Training, Security Education, Phishing Attacks, Resources And Training using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Roadmap To Secure Organizations From Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Roadmap To Secure Organizations From PhishingThis slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Roadmap To Secure Organizations From Phishing to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implement Technical Controls, Establish Policies And Procedures, Employee Training, Baseline Security Assessment, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Steps To Identify Whaling Phishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Steps To Identify Whaling Phishing AttacksThis slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Steps To Identify Whaling Phishing Attacks. This template helps you present information on six stages. You can also present information on Flag Emails Received, Near Similar Email Domains, Spot Grammar, Cross Verify Sensitive Requests using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Steps To Take After Spear Phishing Scam
Phishing Attacks And Strategies To Mitigate Them V2 Steps To Take After Spear Phishing ScamIntroducing Phishing Attacks And Strategies To Mitigate Them V2 Steps To Take After Spear Phishing Scam to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing Scam, Change Your Passwords, Backup Your Files, Conduct A Hardware Scan, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Strategies To Identify Smishing Cyber Scams
Phishing Attacks And Strategies To Mitigate Them V2 Strategies To Identify Smishing Cyber ScamsThis slide talks about the various methods of identifying smishing cyber attacks. The purpose of this slide is to help users identify smishing scams. These include suspicious texts from unknown numbers, unrequested links and files, money transfer requests, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Strategies To Identify Smishing Cyber Scams. Use it as a tool for discussion and navigation on Smishing Cyber Attacks, Smishing Scams, Unrequested Links And Files, Money Transfer Requests. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Techniques Used By Cybercriminals To Conduct
Phishing Attacks And Strategies To Mitigate Them V2 Techniques Used By Cybercriminals To ConductThis slide demonstrates the techniques used by scammers to conduct watering hole attacks. These methods are cross-site scripting, DMS cache poisoning, drive-by downloads, malvertising, etc. This slide also outlines common intelligence gathering methods. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Techniques Used By Cybercriminals To Conduct. Use it as a tool for discussion and navigation on Social Networking Sites, Demographic Information From Websites, Social Engineering, Keyloggers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Timeline To Secure Organizations From Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Timeline To Secure Organizations From PhishingThis slide shows the timeline to protect organizations from phishing for different organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Timeline To Secure Organizations From Phishing. This template helps you present information on five stages. You can also present information on Implement Technical Controls, Employee Training, Establish Policies And Procedures, Timely Evaluation And Updates using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Tools Provided By Google To Prevent Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Tools Provided By Google To Prevent PhishingThis slide demonstrates the different tools provided by Google to prevent and report cyber phishing scams. These include to spot phishing mails with the help of Gmail, utilize safe browsing in chrome, look for unsafe saved passwords, password alert for chrome, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Tools Provided By Google To Prevent Phishing. Dispense information and present a thorough explanation of Safe Browsing In Chrome, Phishing Mails Detection With Gmail, Two Step Verification, Password Alert For Chrome using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Tricks Employed By Malicious Websites To Scam
Phishing Attacks And Strategies To Mitigate Them V2 Tricks Employed By Malicious Websites To ScamThis slide talks about various tricks utilized by fraudulent websites to scam the visitors. The purpose of this slide is to make users aware of such different tricks such as free or discount offers, low interest rates or free credit cards, employment opportunities, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Tricks Employed By Malicious Websites To Scam to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Employment Opportunities, Emergency Warnings, Malicious Websites, Scam Victims, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Understanding The Process Of E Mail Based Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Understanding The Process Of E Mail Based PhishingThis slide demonstrates the procedure of email-based phishing attacks. The purpose of this slide is to explain how fake websites are used by attackers to get the sensitive data of the users. The key components include database, fake website, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Understanding The Process Of E Mail Based Phishing. Use it as a tool for discussion and navigation on Email Based Phishing Attacks, Fake Website, Phishing Email, Original Website. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Prevention Email Signing And Code
Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Prevention Email Signing And CodeThis slide talks about the techniques which can help in protecting organizations from phishing and vishing attacks. The purpose of this slide is to explain two important methods of preventing cyber scams. These techniques are email signing and code signing. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Prevention Email Signing And Code. Dispense information and present a thorough explanation of Vishing Attacks Prevention, Email Signing And Code Signing, Preventing Cyber Scams using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Warning Signs Of Pop Up Phishing Scams
Phishing Attacks And Strategies To Mitigate Them V2 Warning Signs Of Pop Up Phishing ScamsThis slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Warning Signs Of Pop Up Phishing Scams to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Terrible Pop Up Advertisement, Pop Up Phishing Cyber Attacks, Install Their Malware, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Why Businesses Fall Victim To Phishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Why Businesses Fall Victim To Phishing AttacksThis slide outlines the various reasons responsible for businesses to fall victim to different phishing attacks. These include inadequate employee training, never evaluate the success of the training, careless browsing habits of the employees, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Why Businesses Fall Victim To Phishing Attacks. This template helps you present information on five stages. You can also present information on Inadequate Employee Training, Training Or Policy Improvement, Organizations Are Unaware, Changing Phishing Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Working Of Phishing Training Programs
Phishing Attacks And Strategies To Mitigate Them V2 Working Of Phishing Training ProgramsIntroducing Phishing Attacks And Strategies To Mitigate Them V2 Working Of Phishing Training Programs to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Start With Employee Training, Make Fictitious Phishing Campaigns, Track Progress And Upgrade, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Working Of Watering Hole Phishing Attack
Phishing Attacks And Strategies To Mitigate Them V2 Working Of Watering Hole Phishing AttackThis slide represents the working process of watering hole phishing attacks. The purpose of this slide is to illustrate the flow diagram of watering hole phishing scams. The key points include research and identification, analysis, preparation and execution. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Working Of Watering Hole Phishing Attack. This template helps you present information on four stages. You can also present information on Analysis, Research And Identification, Preparation, Execution, Phishing Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Working Procedure Of Spear Phishing Attack
Phishing Attacks And Strategies To Mitigate Them V2 Working Procedure Of Spear Phishing AttackThis slide illustrates the structure of spear phishing attack. The purpose of this slide is to explain the working flow of spear phishing attack. The key components include attacker, phishing email, targeted users, exploited system, internal network, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Working Procedure Of Spear Phishing Attack to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Email, Targeted Users, Exploited System, Internal Network, Attacker, using this template. Grab it now to reap its full benefits.
-
 Real World Examples Of Watering Hole Phishing Attacks And Strategies To Mitigate Them V2
Real World Examples Of Watering Hole Phishing Attacks And Strategies To Mitigate Them V2This slide describes the real-world examples of watering hole phishing scams. These include Facebook, Twitter, Microsoft, and Apple scam, LuckyMouse scam, International Civil Aviation Organization ICAO scam, Ccleaner scam and Holy Water scam. Increase audience engagement and knowledge by dispensing information using Real World Examples Of Watering Hole Phishing Attacks And Strategies To Mitigate Them V2. This template helps you present information on four stages. You can also present information on International Civil Aviation, Organization Scam, Watering Hole Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Content For Phishing Attacks And Strategies To Mitigate Them V2
Table Of Content For Phishing Attacks And Strategies To Mitigate Them V2Introducing Table Of Content For Phishing Attacks And Strategies To Mitigate Them V2 to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Attacks Prevention, Phishing Attacks Awareness Training, Phishing Attacks Introduction, using this template. Grab it now to reap its full benefits.
-
 Type Promotion Attracts Attention In Powerpoint And Google Slides Cpb
Type Promotion Attracts Attention In Powerpoint And Google Slides CpbPresenting Type Promotion Attracts Attention In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase Four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Type Promotion Attracts Attention This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Attended Robotic Process Automation Streamlining Operations With Artificial Intelligence
Attended Robotic Process Automation Streamlining Operations With Artificial IntelligenceThis slide defines the attended Robotic Process Automation and how tasks are performed in this type of automation through human intervention. Deliver an outstanding presentation on the topic using this Attended Robotic Process Automation Streamlining Operations With Artificial Intelligence. Dispense information and present a thorough explanation of Process, Automation, Operational Efficiency using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





