Powerpoint Templates and Google slides for Assessment Of Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
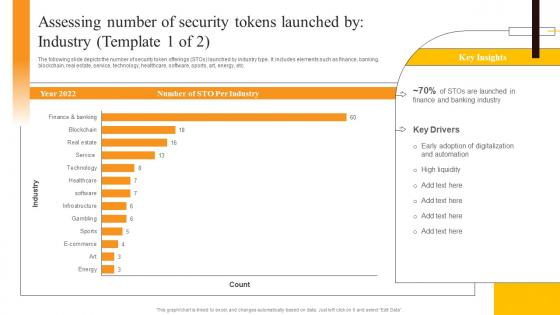 Assessing Number Of Security Tokens Launched By Industry Security Token Offerings BCT SS
Assessing Number Of Security Tokens Launched By Industry Security Token Offerings BCT SSThe following slide depicts the number of security token offerings STOs launched by industry type. It includes elements such as finance, banking, blockchain, real estate, service, technology, healthcare, software, sports, art, energy, etc. Present the topic in a bit more detail with this Assessing Number Of Security Tokens Launched By Industry Security Token Offerings BCT SS. Use it as a tool for discussion and navigation on Assessing Number, Security Tokens, Industry. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
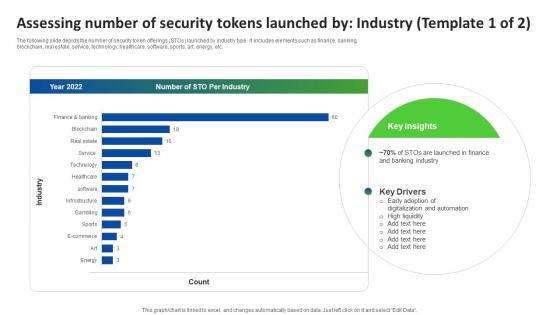 Q142 Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Industry BCT SS V
Q142 Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Industry BCT SS VThe following slide depicts the number of security token offerings STOs launched by industry type. It includes elements such as finance, banking, blockchain, real estate, service, technology, healthcare, software, sports, art, energy, etc. Deliver an outstanding presentation on the topic using this Q142 Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Industry BCT SS V. Dispense information and present a thorough explanation of Early Adoption, Digitalization And Automation, High Liquidity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
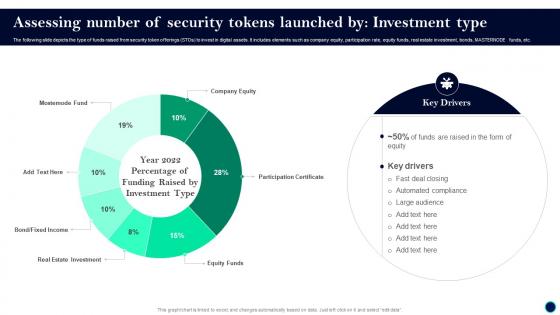
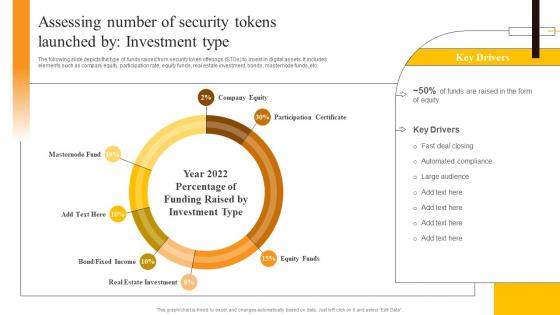 Assessing Number Of Security Tokens Launched By Investment Security Token Offerings BCT SS
Assessing Number Of Security Tokens Launched By Investment Security Token Offerings BCT SSThe following slide depicts the type of funds raised from security token offerings STOs to invest in digital assets. It includes elements such as company equity, participation rate, equity funds, real estate investment, bonds, masternode funds, etc. Deliver an outstanding presentation on the topic using this Assessing Number Of Security Tokens Launched By Investment Security Token Offerings BCT SS. Dispense information and present a thorough explanation of Real Estate Investment, Participation Certificate, Company Equity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
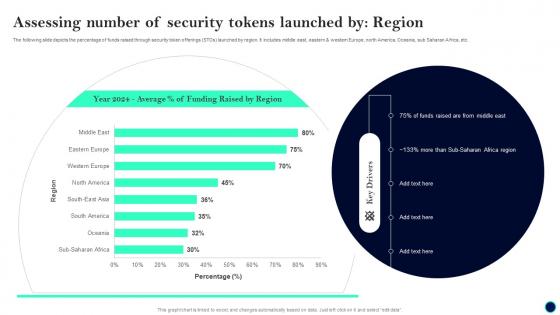
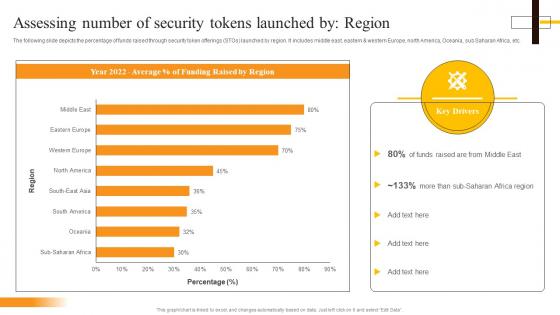 Assessing Number Of Security Tokens Launched By Region Security Token Offerings BCT SS
Assessing Number Of Security Tokens Launched By Region Security Token Offerings BCT SSThe following slide depicts the percentage of funds raised through security token offerings STOs launched by region. It includes middle east, eastern and western Europe, north America, Oceania, sub Saharan Africa, etc. Present the topic in a bit more detail with this Assessing Number Of Security Tokens Launched By Region Security Token Offerings BCT SS. Use it as a tool for discussion and navigation on Assessing Number, Security Tokens, Region. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Assessing Number Of Security Beginners Guide To Successfully Launch Security Token BCT SS V
Assessing Number Of Security Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide depicts the number of security token offerings STOs launched by industry type. It includes elements such as finance, banking, blockchain, real estate, service, technology, healthcare, software, sports, art, energy, etc. Present the topic in a bit more detail with this Assessing Number Of Security Beginners Guide To Successfully Launch Security Token BCT SS V. Use it as a tool for discussion and navigation on Sto Per Industry, Banking Industry, Key Insights. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Assessing Number Of Security Tokens Beginners Guide To Successfully Launch Security Token BCT SS V
Assessing Number Of Security Tokens Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide depicts the percentage of funds raised through security token offerings STOs launched by region. It includes middle east, eastern and western Europe, north America, Oceania, sub Saharan Africa, etc. Deliver an outstanding presentation on the topic using this Assessing Number Of Security Tokens Beginners Guide To Successfully Launch Security Token BCT SS V. Dispense information and present a thorough explanation of Assessing Number, Security Tokens Launched, Region using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Beginners Guide To Successfully Launch Security Token Assessing Number Of Security BCT SS V
Beginners Guide To Successfully Launch Security Token Assessing Number Of Security BCT SS VThe following slide depicts the type of funds raised from security token offerings STOs to invest in digital assets. It includes elements such as company equity, participation rate, equity funds, real estate investment, bonds, MASTERNODE funds, etc. Present the topic in a bit more detail with this Beginners Guide To Successfully Launch Security Token Assessing Number Of Security BCT SS V. Use it as a tool for discussion and navigation on Key Drivers, Deal Closing, Automated Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Securing Food Safety In Online Statistics To Assess Need Of Outsourcing Food Delivery App
Securing Food Safety In Online Statistics To Assess Need Of Outsourcing Food Delivery AppThis slide covers statistics to assess need of integrating third party platform for delivering food. It involves features such as free and fast delivery or discounts. Present the topic in a bit more detail with this Securing Food Safety In Online Statistics To Assess Need Of Outsourcing Food Delivery App. Use it as a tool for discussion and navigation on Statistics To Assess, Need Outsourcing Food Delivery App. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Q143 Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Region BCT SS V
Q143 Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Region BCT SS VThe following slide depicts the percentage of funds raised through security token offerings STOs launched by region. It includes middle east, eastern and western Europe, north America, Oceania, sub Saharan Africa, etc. Present the topic in a bit more detail with this Q143 Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Region BCT SS V. Use it as a tool for discussion and navigation on Funds Raised, Sub Saharan, Africa Region. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Assessing Number Of Security Tokens Launched By Ultimate Guide Smart BCT SS V
Assessing Number Of Security Tokens Launched By Ultimate Guide Smart BCT SS VThe following slide depicts the type of funds raised from security token offerings STOs to invest in digital assets. It includes elements such as company equity, participation rate, equity funds, real estate investment, bonds, masternode funds, etc. Present the topic in a bit more detail with this Assessing Number Of Security Tokens Launched By Ultimate Guide Smart BCT SS V. Use it as a tool for discussion and navigation on Fast Deal Closing, Automated Compliance, Large Audience. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Region BCT SS V
Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Region BCT SS VThe following slide depicts the percentage of funds raised through security token offerings STOs launched by region. It includes middle east, eastern and western Europe, north America, Oceania, sub Saharan Africa, etc. Present the topic in a bit more detail with this Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Region BCT SS V. Use it as a tool for discussion and navigation on Funds Raised, Sub Saharan, Africa Region. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data security it assessment matrix of cyber risks ppt slides outline
Data security it assessment matrix of cyber risks ppt slides outlineThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Present the topic in a bit more detail with this Data Security IT Assessment Matrix Of Cyber Risks Ppt Slides Outline. Use it as a tool for discussion and navigation on Systems Involved, Owner Tenant, Mobile, Web Applications, Health Care. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security assessment matrix of cyber risks ppt grid
Computer system security assessment matrix of cyber risks ppt gridThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Increase audience engagement and knowledge by dispensing information using Computer System Security Assessment Matrix Of Cyber Risks Ppt Grid. This template helps you present information on one stages. You can also present information on Industrial, Data Center, Multifamily, Retail, Access using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comparative Assessment Of ZTNA Version 1 0 And 2 0 Zero Trust Security Model
Comparative Assessment Of ZTNA Version 1 0 And 2 0 Zero Trust Security ModelThis Slide Represents The Comparison Between Zero Trust Network Access Versions 1.0 And 2.0. The Purpose Of This Slide Is To Demonstrate The Overview Of Both Versions, Including Differences. It Also Includes The Architecture Of Both Versions Of Zero-Trust Network Access. Deliver An Outstanding Presentation On The Topic Using This Comparative Assessment Of ZTNA Version 1 0 And 2 0 Zero Trust Security Model. Dispense Information And Present A Thorough Explanation Of Comparative, Assessment, Applications Using The Slides Given. This Template Can Be Altered And Personalized To Fit Your Needs. It Is Also Available For Immediate Download. So Grab It Now.
-
 Comparative Assessment Of Security Compliance Tools
Comparative Assessment Of Security Compliance ToolsThis slide shows security compliance tools analysis and comparison which helps to determine best and effective tools for business. It further includes tools such as vanta, drata, sprinto etc. Presenting our well structured Comparative Assessment Of Security Compliance Tools. The topics discussed in this slide are Industries Involved, Market Segment.This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
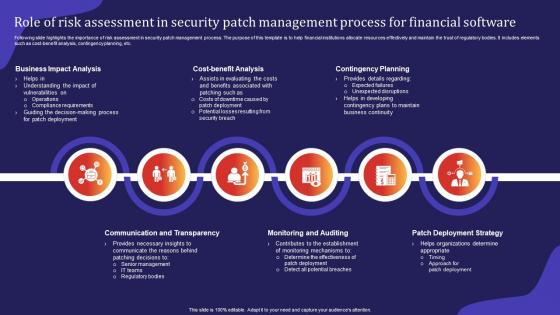 Role Of Risk Assessment In Security Patch Management Process For Financial Software
Role Of Risk Assessment In Security Patch Management Process For Financial SoftwareFollowing slide highlights the importance of risk assessment in security patch management process. The purpose of this template is to help financial institutions allocate resources effectively and maintain the trust of regulatory bodies. It includes elements such as cost benefit analysis, contingency planning, etc.Introducing our premium set of slides with Role Of Risk Assessment In Security Patch Management Process For Financial Software. Ellicudate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Contingency Planning, Communication Transparency, Monitoring Auditing. So download instantly and tailor it with your information.
-
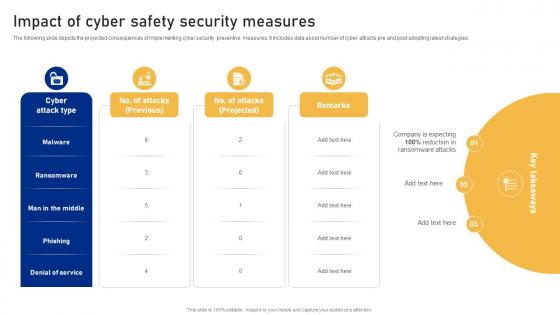 Impact Of Cyber Safety Security Measures Cyber Risk Assessment
Impact Of Cyber Safety Security Measures Cyber Risk AssessmentThe following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies. Present the topic in a bit more detail with this Impact Of Cyber Safety Security Measures Cyber Risk Assessment Use it as a tool for discussion and navigation on Cyber Attack, Ransomware, Projected This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Cyber Security Policies And Practices Cyber Risk Assessment
Impact Of Cyber Security Policies And Practices Cyber Risk AssessmentThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, Introducing Impact Of Cyber Security Policies And Practices Cyber Risk Assessment to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Security Guidelines, Management, Privacy Policies using this template. Grab it now to reap its full benefits.
-
 Comparative Assessment Of EDR Security Solutions Tools
Comparative Assessment Of EDR Security Solutions ToolsThis slide represents EDR software tools and includes tools, solution scope, delivery model, features, pricing, and rating. Presenting our well structured Comparative Assessment Of EDR Security Solutions Tools. The topics discussed in this slide are Symantec Endpoint Protection, Crowd Strike Falcon Insight, Threat Intelligence, Detect Hidden Packages. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Comparative Assessment Of ACH Payment Processors Enhancing Transaction Security With E Payment
Comparative Assessment Of ACH Payment Processors Enhancing Transaction Security With E PaymentMentioned slide illustrates comparative analysis of various ACH Automated Clearing House payment processors which can be leveraged by businesses to making bank transfer. It includes key attributes such as ACH processors, best attribute, features, rating, price, and company size. Deliver an outstanding presentation on the topic using this Comparative Assessment Of ACH Payment Processors Enhancing Transaction Security With E Payment Dispense information and present a thorough explanation of ACH Payment Processors, Best Attribute, Features using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Cashless And Contactless Payment Enhancing Transaction Security With E Payment
Comparative Assessment Of Cashless And Contactless Payment Enhancing Transaction Security With E PaymentMentioned slide showcases comparative analysis between cashless and contactless payment system which can be implemented by businesses to improve cashflow management. It includes key attributes such as meaning, closed and open loop system, Present the topic in a bit more detail with this Comparative Assessment Of Cashless And Contactless Payment Enhancing Transaction Security With E Payment Use it as a tool for discussion and navigation on Attributes, Cashless Payment, Contactless Payment This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of Debit And Credit Card Enhancing Transaction Security With E Payment
Comparative Assessment Of Debit And Credit Card Enhancing Transaction Security With E PaymentMentioned slide shows comparative analysis of debit and credit card payment options which can be used by businesses for making daily payments. It includes key attributes such as funds availability, spending limit, charges, interest charges reward points, repayment, etc. Deliver an outstanding presentation on the topic using this Comparative Assessment Of Debit And Credit Card Enhancing Transaction Security With E Payment Dispense information and present a thorough explanation of Attributes, Credit Card, Debit Card using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Multiple Mobile Wallet Applications Enhancing Transaction Security With E Payment
Comparative Assessment Of Multiple Mobile Wallet Applications Enhancing Transaction Security With E PaymentFollowing slide shows comparative analysis of multiple types of mobile wallet which can be leverages by business to go contactless. It includes key components such as features, transaction level, payment fees, transaction time, security and type of wallet. Present the topic in a bit more detail with this Comparative Assessment Of Multiple Mobile Wallet Applications Enhancing Transaction Security With E Payment Use it as a tool for discussion and navigation on Features, Transaction Level, Payment Fees This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of QR Code Generating Professionals Enhancing Transaction Security With E Payment
Comparative Assessment Of QR Code Generating Professionals Enhancing Transaction Security With E PaymentFollowing slide showcases comparative analysis of multiple code generators whose services can be leveraged by businesses to design customized QR code. It includes key attributes such as Deliver an outstanding presentation on the topic using this Comparative Assessment Of QR Code Generating Professionals Enhancing Transaction Security With E Payment Dispense information and present a thorough explanation of Attributes, QR Code Generator Pro, Flow Code using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Various Payment Cryptocurrencies Enhancing Transaction Security With E Payment
Comparative Assessment Of Various Payment Cryptocurrencies Enhancing Transaction Security With E PaymentMentioned slide demonstrates comparative analysis of various crypto coins which can be used by businesses in cashless payment. It includes key points such as launch year, trading value, transaction rate, transaction fees, privacy, block time, and trading history. Present the topic in a bit more detail with this Comparative Assessment Of Various Payment Cryptocurrencies Enhancing Transaction Security With E Payment Use it as a tool for discussion and navigation on Launch Year, Ticker Symbol, Current Trading Value This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Assessment Of Mobile Wallet Application Enhancing Transaction Security With E Payment
Impact Assessment Of Mobile Wallet Application Enhancing Transaction Security With E PaymentMentioned slide provides information about mobile wallet payment implementation impact on business activities. It includes impacts such as easy customer data analytics, offer reward and loyalty points, smooth workflow, and improved security. Increase audience engagement and knowledge by dispensing information using Impact Assessment Of Mobile Wallet Application Enhancing Transaction Security With E Payment This template helps you present information on four stages. You can also present information on Easy Customer Data Analytics, Smooth Workflow, Improved Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Proactively Assess The Impact Of Potential Security Internet Of Things IoT Security Cybersecurity SS
Proactively Assess The Impact Of Potential Security Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of impact assessment on internet of things IoT device security events, referable for businesses in developing mitigation process. It provides details about threat model, security layers, etc. Introducing Proactively Assess The Impact Of Potential Security Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Comprehensive Security, Assessment And Security Layers, Credential Provisioning, using this template. Grab it now to reap its full benefits.
-
 Comparative Assessment Of Cyber Security Tools In Automotive Industry
Comparative Assessment Of Cyber Security Tools In Automotive IndustryThis slide highlights comparison of digital security tools in automobile sector. The purpose of this slide is to aid businesses in utilizing reliable software for managing automotive cybersecurity. It includes elements such as intrusion detection, secure boot, etc. Introducing our Comparative Assessment Of Cyber Security Tools In Automotive Industry set of slides. The topics discussed in these slides are Intrusion Detection, Access Control, Network Monitoring This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Assessment Of Threat Intelligence Teams In Security Operation Center
Comparative Assessment Of Threat Intelligence Teams In Security Operation CenterThe below slide highlights the threat intelligence types that offer a foundation for establishment of security operation center. The parameters for evaluation are description, use case, and benefit. Introducing our premium set of slides with name Comparative Assessment Of Threat Intelligence Teams In Security Operation Center. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Tactical, Strategic, Operational. So download instantly and tailor it with your information.
-
 Comparative Assessment Of Fraud Prevention Initiatives Implementing E Commerce Security Measures
Comparative Assessment Of Fraud Prevention Initiatives Implementing E Commerce Security MeasuresThis slide showcases comparative assessment of fraud prevention strategies by company, referable for businesses facing similar situation. It include companies, position, recent fraud incidents and ongoing efforts. Deliver an outstanding presentation on the topic using this Comparative Assessment Of Fraud Prevention Initiatives Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Position, Action Plan, Recent Ecommerce Fraud Incidents using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of IT Security Awareness Training Tools Cybersecurity SS
Comparative Assessment Of IT Security Awareness Training Tools Cybersecurity SSThis slide represents comparison between IT security awareness training tools based on features such as audio mixing, text animation, time mapping, titles and captions etc. Deliver an outstanding presentation on the topic using this Comparative Assessment Of IT Security Awareness Training Tools Cybersecurity SS. Dispense information and present a thorough explanation of Time Mapping, Text Animation, Tram Reviews, Security Awareness Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS
Comparative Assessment Of Endpoint Security Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases comparative analysis for endpoint security tools. It provides details about endpoint firewall, compatibility, data loss prevention, regulatory compliance, etc.Present the topic in a bit more detail with this Comparative Assessment Of Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Regulatory Compliance, Data Loss Prevention, Endpoint Firewall. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of Encryption Algorithms For Organizational Data Security
Comparative Assessment Of Encryption Algorithms For Organizational Data SecurityThis slide provides a comparative assessment of various data encryption algorithms on different parameters. The multiple parameters used for assessment are encryption standard and use cases. Introducing our premium set of slides with Comparative Assessment Of Encryption Algorithms For Organizational Data Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Aes, Tdes, Twofish, Blowfish. So download instantly and tailor it with your information.
-
 Comparative Assessment Of Wireless Lan Security Protocols
Comparative Assessment Of Wireless Lan Security ProtocolsThis slide represents comparative assessment of various WLAN security protocols that assist companies in selecting relevant protocol suitable for specific use cases. It includes various protocols such as WEP, WPA, WPA2, and WPA3 Presenting our well structured Comparative Assessment Of Wireless Lan Security Protocols The topics discussed in this slide are Year Release, Cryptographic Technique, Session Key SizeThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
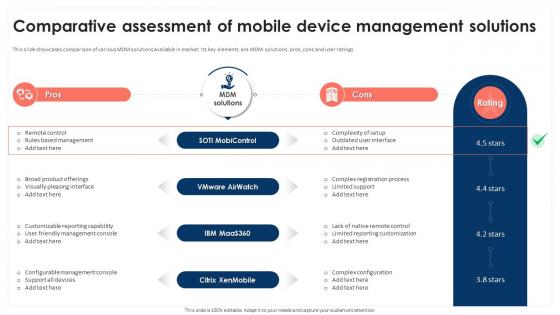 Comparative Assessment Of Mobile Device Management Solutions Mobile Device Security Cybersecurity SS
Comparative Assessment Of Mobile Device Management Solutions Mobile Device Security Cybersecurity SSThis slide showcases comparison of various MDM solutions available in market. Its key elements are MDM solutions, pros, cons and user ratings Increase audience engagement and knowledge by dispensing information using Comparative Assessment Of Mobile Device Management Solutions Mobile Device Security Cybersecurity SS This template helps you present information on Two stages. You can also present information on SOTI Mobicontrol, Vmware Airwatch, Citrix Xenmobile using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Assessing Cost Of Information Breach In Risk Assessment And Management Plan For Information Security
Assessing Cost Of Information Breach In Risk Assessment And Management Plan For Information SecurityPresent the topic in a bit more detail with this Assessing Cost Of Information Breach In Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Information, Sources, Engineering. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Market Growth Of Information Security Industry Risk Assessment And Management Plan For Information Security
Market Growth Of Information Security Industry Risk Assessment And Management Plan For Information SecurityThis slide showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compunded annual growth rate of industry Deliver an outstanding presentation on the topic using this Market Growth Of Information Security Industry Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Growth, Information, Security Industry using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Rising Number Of Information Security Attacks Risk Assessment And Management Plan For Information Security
Rising Number Of Information Security Attacks Risk Assessment And Management Plan For Information SecurityThis slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection Present the topic in a bit more detail with this Rising Number Of Information Security Attacks Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Organizations, Information, Cybersecurity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents Risk Assessment And Management Plan For Information Security
Table Of Contents Risk Assessment And Management Plan For Information SecurityDeliver an outstanding presentation on the topic using this Table Of Contents Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Assessment, Organization, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Assessing Cost Of Information Breach In Different Countries Information Security Risk Management
Assessing Cost Of Information Breach In Different Countries Information Security Risk ManagementDeliver an outstanding presentation on the topic using this Assessing Cost Of Information Breach In Different Countries Information Security Risk Management. Dispense information and present a thorough explanation of Assessing, Information Breach, Different Countries using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Assessing Cost Of Information Breach In Different Information System Security And Risk Administration Plan
Assessing Cost Of Information Breach In Different Information System Security And Risk Administration PlanPresent the topic in a bit more detail with this Assessing Cost Of Information Breach In Different Information System Security And Risk Administration Plan. Use it as a tool for discussion and navigation on Past Decade, Social Engineering, Advanced Persistent Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Risk Assessment And Management Dashboard Development And Implementation Of Security
Cyber Security Risk Assessment And Management Dashboard Development And Implementation Of SecurityThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Dashboard Development And Implementation Of Security. Dispense information and present a thorough explanation of Medium Risk, Unresolved Side, Inactive Accounts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
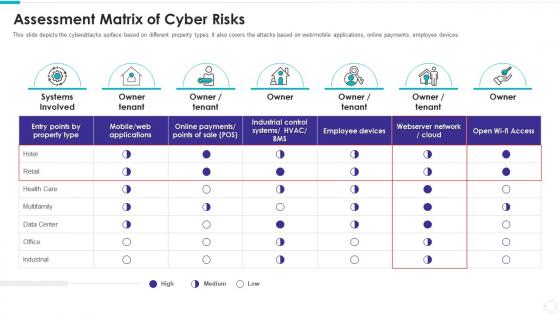 Electronic information security assessment matrix of cyber risks
Electronic information security assessment matrix of cyber risksThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Present the topic in a bit more detail with this Electronic Information Security Assessment Matrix Of Cyber Risks. Use it as a tool for discussion and navigation on Systems Involved, Owner Tenant, Data Center, Industrial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative assessment of managing critical threat vulnerabilities and security threats
Comparative assessment of managing critical threat vulnerabilities and security threatsThis slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Present the topic in a bit more detail with this Comparative Assessment Of Managing Critical Threat Vulnerabilities And Security Threats. Use it as a tool for discussion and navigation on Insider Threat, Social Engineering, Maintenance Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Technological assessment of managing critical threat vulnerabilities and security threats
Technological assessment of managing critical threat vulnerabilities and security threatsThis slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Present the topic in a bit more detail with this Technological Assessment Of Managing Critical Threat Vulnerabilities And Security Threats. Use it as a tool for discussion and navigation on Industry Standard, Firms Standard, Customer Satisfaction Score. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative assessment of various threat agents corporate security management
Comparative assessment of various threat agents corporate security managementThis slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an outstanding presentation on the topic using this Comparative Assessment Of Various Threat Agents Corporate Security Management. Dispense information and present a thorough explanation of Insider Threat, Social Engineering, Threat Agents using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Technological assessment of firm current management corporate security management
Technological assessment of firm current management corporate security managementThis slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver an outstanding presentation on the topic using this Technological Assessment Of Firm Current Management Corporate Security Management. Dispense information and present a thorough explanation of Incidents Handling Rate, Client Onboarding, Service Failure Rate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Hotel Safety And Security Solutions
Comparative Assessment Of Hotel Safety And Security SolutionsThis slide covers comparative assessment of hotel safety and security solutions. It involves parameters of comparison such as anti slip solution, fire retarder, anti theft, test alarms and cost involved. Introducing our Comparative Assessment Of Hotel Safety And Security Solutions set of slides. The topics discussed in these slides are Comparative, Assessment, Solutions. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cybersecurity Criticality Assessment Of Identified Assets Information Security Program
Cybersecurity Criticality Assessment Of Identified Assets Information Security ProgramFollowing slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. Present the topic in a bit more detail with this Cybersecurity Criticality Assessment Of Identified Assets Information Security Program. Use it as a tool for discussion and navigation on Criticality Assessment Of Identified Assets. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Assessment Matrix Of Cyber Risks
Information Security Assessment Matrix Of Cyber RisksThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Present the topic in a bit more detail with this Information Security Assessment Matrix Of Cyber Risks. Use it as a tool for discussion and navigation on Assessment Matrix Of Cyber Risks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Criticality Assessment Of Identified Assets Introducing A Risk Based Approach To Cyber Security
Criticality Assessment Of Identified Assets Introducing A Risk Based Approach To Cyber SecurityFollowing slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost.Deliver an outstanding presentation on the topic using this Criticality Assessment Of Identified Assets Introducing A Risk Based Approach To Cyber Security Dispense information and present a thorough explanation of Infrastructure Hardware, Routers And Switches, Server Computers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
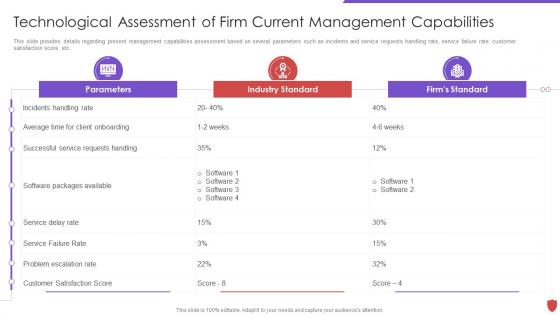 Technological assessment of firm current capabilities cyber security risk management
Technological assessment of firm current capabilities cyber security risk managementThis slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver an outstanding presentation on the topic using this Technological Assessment Of Firm Current Capabilities Cyber Security Risk Management. Dispense information and present a thorough explanation of Parameters, Industry Standard, Firms Standard, Service Delay Rate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security Assessment Matrix Of Network Risks
Network Security Assessment Matrix Of Network RisksThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web mobile applications, online payments, employee devices. Present the topic in a bit more detail with this Network Security Assessment Matrix Of Network Risks. Use it as a tool for discussion and navigation on Assessment Matrix Of Network Risks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of Operational Technology Security Vendors
Comparative Assessment Of Operational Technology Security VendorsMentioned slide showcase various vendors who offers operational technology OT security solutions to business organizations. Organization can choose the best among security vendors by making comparison on the basis of features, deployment, operating systems, price and ratings. Present the topic in a bit more detail with this Comparative Assessment Of Operational Technology Security Vendors. Use it as a tool for discussion and navigation on Types Vendors, Key Features, Deployment, Operating Systems, Pricing In USD, Ratings. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Assessment Matrix Of Cyber Risks
Information Technology Security Assessment Matrix Of Cyber RisksThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an outstanding presentation on the topic using this Information Technology Security Assessment Matrix Of Cyber Risks. Dispense information and present a thorough explanation of Assessment Matrix Of Cyber Risks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enhancing overall project security it comparative assessment of various threat agents affecting
Enhancing overall project security it comparative assessment of various threat agents affectingThis slide provides information regarding comparative assessment of different threat agents impacting IT project safety comparing on various parameters such as data loss impact, skills required to handle threat, etc. Present the topic in a bit more detail with this Enhancing Overall Project Security It Comparative Assessment Of Various Threat Agents Affecting. Use it as a tool for discussion and navigation on Assessment, Operations, Maintenance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enhancing overall project security it technological assessment of firm current
Enhancing overall project security it technological assessment of firm currentThis slide provides information regarding present management capabilities technological assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Present the topic in a bit more detail with this Enhancing Overall Project Security It Technological Assessment Of Firm Current. Use it as a tool for discussion and navigation on Technological, Assessment, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of Security Building A Security Awareness Program
Comparative Assessment Of Security Building A Security Awareness ProgramThe purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. Present the topic in a bit more detail with this Comparative Assessment Of Security Building A Security Awareness Program. Use it as a tool for discussion and navigation on Course Description, Comparative Assessment, Online Courses. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of Managed Security Service Packages
Comparative Assessment Of Managed Security Service PackagesMentioned slide delineates comparison of managed security service packages on the basis of bronze, silver and gold plan. The services covered in the packages are incident prevention, detection and response. Introducing our Comparative Assessment Of Managed Security Service Packages set of slides. The topics discussed in these slides are Threat Intelligence, Vulnerability Management, Security Analytics. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Estimated Impact Of Information Security Risk Assessment And Management Plan For Information Security
Estimated Impact Of Information Security Risk Assessment And Management Plan For Information SecurityThis slide showcases capabilities of organization regarding information and data security after risk management plan. Its key components are risk management functions, required standard rating and actual standard rating Present the topic in a bit more detail with this Estimated Impact Of Information Security Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Management, Information, Components. This template is free to edit as deemed fit for your organization. Therefore download it now.




