Powerpoint Templates and Google slides for Architecture Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cloud Architecture And Security Review Powerpoint Presentation Slides
Cloud Architecture And Security Review Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Cloud Architecture And Security Review Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the sixty six slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Security Architecture Review Of A Cloud Native Environment Powerpoint Presentation Slides
Security Architecture Review Of A Cloud Native Environment Powerpoint Presentation SlidesThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Security Architecture Review Of A Cloud Native Environment Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of Twenty Four slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Cloud Security Architecture Powerpoint Ppt Template Bundles
Cloud Security Architecture Powerpoint Ppt Template BundlesIf you require a professional template with great design, then this Cloud Security Architecture Powerpoint Ppt Template Bundles is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using fourteen slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Data management maturity information security business growth architecture
Data management maturity information security business growth architectureDeliver a credible and compelling presentation by deploying this Data Management Maturity Information Security Business Growth Architecture. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The twelve slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Data Management Maturity Information Security Business Growth Architecture PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Working Components Of Secure Web Gateway Architecture Network Security Using Secure Web Gateway
Working Components Of Secure Web Gateway Architecture Network Security Using Secure Web GatewayThis slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc. Increase audience engagement and knowledge by dispensing information using Working Components Of Secure Web Gateway Architecture Network Security Using Secure Web Gateway. This template helps you present information on five stages. You can also present information on Application Control, Website Content Inspection, Gateway Architecture using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Statistical Graph Illustrating Building Enterprise Security Architecture
Statistical Graph Illustrating Building Enterprise Security ArchitectureThis slide showcases the statistical graph highlighting creating enterprise security architecture which helps an organization to create better,secure and safer environment. It include details such as enhances security support,improves team collaboration,etc. Introducing our Statistical Graph Illustrating Building Enterprise Security Architecture set of slides. The topics discussed in these slides are Devops Security,Building Securitys Success,Key Reasons. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Enterprise IoT Security Network Architecture
Enterprise IoT Security Network ArchitectureThis slide provides a network architecture for IoT security that helps to secure data and privacy with automated solutions for the effective transmission of data. The multiple components are IP capable devices, Resource constrained devices, business systems, etc.Introducing our Enterprise IoT Security Network Architecture set of slides. The topics discussed in these slides are Data Processing, Device Authentication, Business Systems. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 IoT Network Security Architecture Image
IoT Network Security Architecture ImagePresenting our set of slides with IoT Network Security Architecture Image. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Iot Network Security, Architecture Image.
-
 Salesforce Security Architecture In Powerpoint And Google Slides Cpb
Salesforce Security Architecture In Powerpoint And Google Slides CpbPresenting Salesforce Security Architecture In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Salesforce Security Architecture. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Firewall As A Service Fwaas Working And Architecture Of Firewall Security Technology
Firewall As A Service Fwaas Working And Architecture Of Firewall Security TechnologyThis slide demonstrates the architecture and working of traditional firewalls. The purpose of this slide is to illustrate the firewall architecture and working. The main components include corporate network, operation network and control system network. Present the topic in a bit more detail with this Firewall As A Service Fwaas Working And Architecture Of Firewall Security Technology. Use it as a tool for discussion and navigation on Operator Workstation, Administrator Workstation, Control Systems, Data Acquisition, Internal Databases And Servers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 As A Service Deployment Approach Of ZTNA Architecture Zero Trust Security Model
As A Service Deployment Approach Of ZTNA Architecture Zero Trust Security ModelThis slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software. Present the topic in a bit more detail with this As A Service Deployment Approach Of ZTNA Architecture Zero Trust Security Model. Use it as a tool for discussion and navigation on Architecture, Deployment, Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Build Zero Trust Network Access Architecture Zero Trust Security Model
Checklist To Build Zero Trust Network Access Architecture Zero Trust Security ModelThis slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Deliver an outstanding presentation on the topic using this Checklist To Build Zero Trust Network Access Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Architecture, Measures, Organizations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Client Based Approach Of ZTNA Architecture Zero Trust Security Model
Client Based Approach Of ZTNA Architecture Zero Trust Security ModelThis slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Present the topic in a bit more detail with this Client Based Approach Of ZTNA Architecture Zero Trust Security Model. Use it as a tool for discussion and navigation on Architecture, Process, Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 External Components Of Zero Trust Network Architecture Zero Trust Security Model
External Components Of Zero Trust Network Architecture Zero Trust Security ModelThis slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Deliver an outstanding presentation on the topic using this External Components Of Zero Trust Network Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Architecture, Documentation, Potential using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F1585 Zero Trust Network Access Architectural Models Zero Trust Security Model
F1585 Zero Trust Network Access Architectural Models Zero Trust Security ModelThis slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Introducing F1585 Zero Trust Network Access Architectural Models Zero Trust Security Model to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Architectural, Resources, Verification, using this template. Grab it now to reap its full benefits.
-
 F1586 Zero Trust Network Access Architecture Overview Zero Trust Security Model
F1586 Zero Trust Network Access Architecture Overview Zero Trust Security ModelThis slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Present the topic in a bit more detail with this F1586 Zero Trust Network Access Architecture Overview Zero Trust Security Model. Use it as a tool for discussion and navigation on Resources, Architecture, Overview. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1587 Zero Trust Network Access Architecture Workflow Zero Trust Security Model
F1587 Zero Trust Network Access Architecture Workflow Zero Trust Security ModelThis slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Increase audience engagement and knowledge by dispensing information using F1587 Zero Trust Network Access Architecture Workflow Zero Trust Security Model. This template helps you present information on six stages. You can also present information on Architecture, Workflow, Resources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Logical Components Of Zero Trust Architecture Zero Trust Security Model
Logical Components Of Zero Trust Architecture Zero Trust Security ModelThis slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. Deliver an outstanding presentation on the topic using this Logical Components Of Zero Trust Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Components, Architecture, Threat Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Other ZTNA Architecture Deployment Approaches Zero Trust Security Model
Other ZTNA Architecture Deployment Approaches Zero Trust Security ModelThis slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Deliver an outstanding presentation on the topic using this Other ZTNA Architecture Deployment Approaches Zero Trust Security Model. Dispense information and present a thorough explanation of Enhanced Identity Governance, Micro Segmentation, Software Defined Network Perimeters using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Pro Browser Based Approach Of ZTNA Architecture Zero Trust Security Model
Pro Browser Based Approach Of ZTNA Architecture Zero Trust Security ModelThis slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps. Deliver an outstanding presentation on the topic using this Pro Browser Based Approach Of ZTNA Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Architecture, Approach, Overview using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Security Model
Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Security ModelThis slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach. Present the topic in a bit more detail with this Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Security Model. Use it as a tool for discussion and navigation on Architecture, Deployment, Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Functions Of Zero Trust Network Access Architecture Zero Trust Security Model
Working Functions Of Zero Trust Network Access Architecture Zero Trust Security ModelThis slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Introducing Working Functions Of Zero Trust Network Access Architecture Zero Trust Security Model to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Architecture, Abnormalities, Processing, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Network Access Vs Zero Trust Architecture Zero Trust Security Model
Zero Trust Network Access Vs Zero Trust Architecture Zero Trust Security ModelThis slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Deliver an outstanding presentation on the topic using this Zero Trust Network Access Vs Zero Trust Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Architecture, Implementation, Technologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Security Workday Database Architecture In Powerpoint And Google Slides Cpb
Data Security Workday Database Architecture In Powerpoint And Google Slides CpbPresenting Data Security Workday Database Architecture In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase Four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Data Security Workday, Database Architecture. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Architecture Of Citrix Secure Web Gateway Proxy Solution Network Security Using Secure Web Gateway
Architecture Of Citrix Secure Web Gateway Proxy Solution Network Security Using Secure Web GatewayThis slide represents the Secure Web Gateway solution provided by Citrix. The purpose of this slide is to demonstrate the architecture of Citrixs SWG solution. The key components included are users, firewall, internet, logstream, SWG appliance, etc. Deliver an outstanding presentation on the topic using this Architecture Of Citrix Secure Web Gateway Proxy Solution Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Architecture, Company Complaint Internal, Malware Restricted Websites using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Integration Of Swg Inside Sase Architecture Network Security Using Secure Web Gateway
Integration Of Swg Inside Sase Architecture Network Security Using Secure Web GatewayThis slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc. Deliver an outstanding presentation on the topic using this Integration Of Swg Inside Sase Architecture Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Architecture, Integration, Environment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Web Gateway Architecture And Working Network Security Using Secure Web Gateway
Secure Web Gateway Architecture And Working Network Security Using Secure Web GatewayThis slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. Present the topic in a bit more detail with this Secure Web Gateway Architecture And Working Network Security Using Secure Web Gateway. Use it as a tool for discussion and navigation on Architecture, Approaches, Enterprises. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Iot Security Architecture Principles On Device Layer Introduction To Internet Of Things IoT SS
Iot Security Architecture Principles On Device Layer Introduction To Internet Of Things IoT SSThis slide exhibits security architecture principles on device and communication layer. It showcases iot ecosystem elements such as user, devices, gateway, connection, cloud, and applications. Present the topic in a bit more detail with this Iot Security Architecture Principles On Device Layer Introduction To Internet Of Things IoT SS. Use it as a tool for discussion and navigation on Iot Solution Elements, Important Security Principles. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Grid Computing Architecture Introduction To Grid Computing Security Model
Grid Computing Architecture Introduction To Grid Computing Security ModelThis slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. Deliver an outstanding presentation on the topic using this Grid Computing Architecture Introduction To Grid Computing Security Model. Dispense information and present a thorough explanation of Grid Computing Security Model, Security Components, Authentication And Delegation, Intrusion Detection, Anti Virus Management, Policy Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Grid Computing Architecture Key Components Of Grid Computing Security
Grid Computing Architecture Key Components Of Grid Computing SecurityThis slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Introducing Grid Computing Architecture Key Components Of Grid Computing Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Security Component, Grid Computing Network, Protects The System, Authentication And Authorization Processes, using this template. Grab it now to reap its full benefits.
-
 Architecture Security In Powerpoint And Google Slides Cpb
Architecture Security In Powerpoint And Google Slides CpbPresenting our Architecture Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Architecture Security. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cloud Cyber Security System Architecture
Cloud Cyber Security System ArchitectureThis slide showcases cyber security system architecture for business cloud data protection from hacks. This further includes key takeaways such as business having cloud misconfiguration that pose serious hazards. Introducing our Cloud Cyber Security System Architecture set of slides. The topics discussed in these slides are Emulated Components, Cyber Security, System Architecture. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Access Security Broker CASB V2 Architectural Components Ppt Gallery Microsoft
Cloud Access Security Broker CASB V2 Architectural Components Ppt Gallery MicrosoftThis slide outlines the main components of Cloud Access Security Broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Architectural Components Ppt Gallery Microsoft. Dispense information and present a thorough explanation of Cloud Access Security, Broker Architectural, Connectivity Gateway, Software As A Service using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Overview Of Cloud Access Security Broker Architecture
Cloud Access Security Broker CASB V2 Overview Of Cloud Access Security Broker ArchitectureThis slide gives an overview of Cloud Access Security Broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Overview Of Cloud Access Security Broker Architecture. Dispense information and present a thorough explanation of Visibility, Compliance, Threat Protection, Enterprise Integration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Lorawan Lorawan Network Security Architecture Block Diagram
Lorawan Lorawan Network Security Architecture Block DiagramThis slide provide a summary of the security architecture of the LoRaWAN network. It shows the various components involved in securing the network, including the application server, network server, device, join server, and root key. Present the topic in a bit more detail with this Lorawan Lorawan Network Security Architecture Block Diagram. Use it as a tool for discussion and navigation on Device Manufacturers, Architecture, Application Servers . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secops V2 Conceptual Architecture Of Security Operations Center
Secops V2 Conceptual Architecture Of Security Operations CenterThis slide describes the conceptual architecture of the security operations center. The purpose of this slide is to highlight the architecture of SecOps and the elements that formalize the architecture. The main components include network taps, operating systems, apps, security elements, etc. Deliver an outstanding presentation on the topic using this Secops V2 Conceptual Architecture Of Security Operations Center. Dispense information and present a thorough explanation of Conceptual Architecture, Security Operations Center, Network Taps, Operating Systems, Security Elements using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
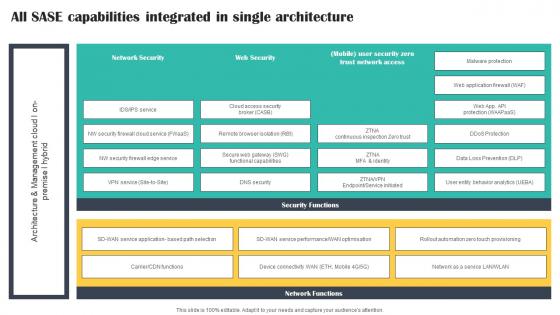 All SASE Capabilities Integrated In Single Architecture Cloud Security Model
All SASE Capabilities Integrated In Single Architecture Cloud Security ModelPresent the topic in a bit more detail with this All SASE Capabilities Integrated In Single Architecture Cloud Security Model. Use it as a tool for discussion and navigation on Capabilities, Integrated, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Architecture And Working Of SD Wide Area Network Cloud Security Model
Architecture And Working Of SD Wide Area Network Cloud Security ModelThis slide represents the architecture and working of a software defined wide area network. The purpose of this slide is to demonstrate the different types of SD WAN architectures, such as on premise, cloud enabled and cloud enabled with backbone. It also caters to the basic operation of SD WAN. Increase audience engagement and knowledge by dispensing information using Architecture And Working Of SD Wide Area Network Cloud Security Model. This template helps you present information on three stages. You can also present information on Working, Architecture, Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE Identity Centric Architecture Overview Cloud Security Model
SASE Identity Centric Architecture Overview Cloud Security ModelThis slide outlines the overview of the centric architecture of the secure access service edge. The purpose of this slide is to demonstrate the various services executed by SASE architecture and components involved in this, such as enterprise data center, internet, internet edge, distributed edge, etc. Deliver an outstanding presentation on the topic using this SASE Identity Centric Architecture Overview Cloud Security Model. Dispense information and present a thorough explanation of Identity, Architecture, Overview using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Access Service Edge Architecture Characteristics Cloud Security Model
Secure Access Service Edge Architecture Characteristics Cloud Security ModelThis slide represents the architectural characteristics of a secure access service edge. The purpose of this slide is to showcase the features of SASE architecture that include identity driven, cloud native, support for all edges, and global distribution. Increase audience engagement and knowledge by dispensing information using Secure Access Service Edge Architecture Characteristics Cloud Security Model. This template helps you present information on four stages. You can also present information on Identity, Native, Support using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Access Service Edge SASE Architecture Cloud Security Model
Secure Access Service Edge SASE Architecture Cloud Security ModelThis slide represents the SASE architecture overview and its goals. The purpose of this slide is to demonstrate the secure access service edge architecture and its goals. The building blocks of SASE architecture include SWG, CASB, ZTNA, FWaaS, SD WAN, Thin Edge, and so on. Present the topic in a bit more detail with this Secure Access Service Edge SASE Architecture Cloud Security Model. Use it as a tool for discussion and navigation on Service, Secure, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Zero Trust Architecture To Enhance Digital Security How Digital Transformation DT SS
Zero Trust Architecture To Enhance Digital Security How Digital Transformation DT SSThis slide presents various measures to establish zero-trust architecture across organization that requires authentication for every action based on granular policies. It includes measures such as strong identity and access management, multi-factor authentication, role based access controls , encryption and data protection measures. Deliver an outstanding presentation on the topic using this Zero Trust Architecture To Enhance Digital Security How Digital Transformation DT SS. Dispense information and present a thorough explanation of Protection Measures, Access Management, Role Based Access Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Architecture And Working Of Sd Wide Area Network
Sase Security Architecture And Working Of Sd Wide Area NetworkThis slide represents the architecture and working of a software-defined wide area network. The purpose of this slide is to demonstrate the different types of SD-WAN architectures, such as on-premise, cloud-enabled and cloud-enabled with backbone. It also caters to the basic operation of SD-WAN. Present the topic in a bit more detail with this Sase Security Architecture And Working Of Sd Wide Area Network. Use it as a tool for discussion and navigation on Architecture, Enterprises, Connections. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Sase Identity Centric Architecture Overview
Sase Security Sase Identity Centric Architecture OverviewThis slide outlines the overview of the centric architecture of the secure access service edge. The purpose of this slide is to demonstrate the various services executed by SASE architecture and components involved in this, such as enterprise data center, internet, internet edge, distributed edge, etc. Deliver an outstanding presentation on the topic using this Sase Security Sase Identity Centric Architecture Overview. Dispense information and present a thorough explanation of Architecture, Overview, Concurrently using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Secure Access Service Edge Architecture Characteristics
Sase Security Secure Access Service Edge Architecture CharacteristicsThis slide represents the architectural characteristics of a secure access service edge. The purpose of this slide is to showcase the features of SASE architecture that include identity-driven, cloud-native, support for all edges, and global distribution. Introducing Sase Security Secure Access Service Edge Architecture Characteristics to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Identity Driven, Support For All Edges, Globally Distributed, using this template. Grab it now to reap its full benefits.
-
 Sase Security Secure Access Service Edge Sase Architecture
Sase Security Secure Access Service Edge Sase ArchitectureThis slide represents the SASE architecture overview and its goals. The purpose of this slide is to demonstrate the secure access service edge architecture and its goals. The building blocks of SASE architecture include SWG, CASB, ZTNA, FWaaS, SD-WAN, Thin Edge, and so on. Present the topic in a bit more detail with this Sase Security Secure Access Service Edge Sase Architecture. Use it as a tool for discussion and navigation on Architecture, Incorporate, Business. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 All Sase Capabilities Integrated In Single Architecture Secure Access Service Edge Sase
All Sase Capabilities Integrated In Single Architecture Secure Access Service Edge SasePresent the topic in a bit more detail with this All Sase Capabilities Integrated In Single Architecture Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Architecture, Management, Malware Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Architecture And Working Of Sd Wide Area Network Secure Access Service Edge Sase
Architecture And Working Of Sd Wide Area Network Secure Access Service Edge SaseThis slide represents the architecture and working of a software-defined wide area network. The purpose of this slide is to demonstrate the different types of SD-WAN architectures, such as on-premise, cloud-enabled and cloud-enabled with backbone. It also caters to the basic operation of SD-WAN. Present the topic in a bit more detail with this Architecture And Working Of Sd Wide Area Network Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Architecture, Enterprises, Connections. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Identity Centric Architecture Overview Secure Access Service Edge Sase
Sase Identity Centric Architecture Overview Secure Access Service Edge SaseThis slide outlines the overview of the centric architecture of the secure access service edge. The purpose of this slide is to demonstrate the various services executed by SASE architecture and components involved in this, such as enterprise data center, internet, internet edge, distributed edge, etc. Present the topic in a bit more detail with this Sase Identity Centric Architecture Overview Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Architecture, Overview, Demonstrates. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Service Edge Architecture Characteristics Secure Access Service Edge Sase
Secure Service Edge Architecture Characteristics Secure Access Service Edge SaseThis slide represents the architectural characteristics of a secure access service edge. The purpose of this slide is to showcase the features of SASE architecture that include identity-driven, cloud-native, support for all edges, and global distribution. Increase audience engagement and knowledge by dispensing information using Secure Service Edge Architecture Characteristics Secure Access Service Edge Sase. This template helps you present information on four stages. You can also present information on Identity Driven, Support For All Edges, Globally Distributed using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Service Sase Architecture Secure Access Service Edge Sase
Secure Service Sase Architecture Secure Access Service Edge SaseThis slide represents the SASE architecture overview and its goals. The purpose of this slide is to demonstrate the secure access service edge architecture and its goals. The building blocks of SASE architecture include SWG, CASB, ZTNA, FWaaS, SD-WAN, Thin Edge, and so on. Present the topic in a bit more detail with this Secure Service Sase Architecture Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Service, Architecture, Requirements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Industrial Internet Of Things Iiot Security Architecture Guide Of Integrating Industrial Internet
Industrial Internet Of Things Iiot Security Architecture Guide Of Integrating Industrial InternetThis slide covers industrial internet of things security architecture. It involves key technologies such as integrity scanning, machine learning, behavior analysis, anti malware and risk detection. Present the topic in a bit more detail with this Industrial Internet Of Things Iiot Security Architecture Guide Of Integrating Industrial Internet. Use it as a tool for discussion and navigation on Integration, Communication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Security In Cloud Computing Architecture Cloud Cryptography
Data Security In Cloud Computing Architecture Cloud CryptographyThis slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data-in-transit, data-at-rest and legal and regulatory issues. Present the topic in a bit more detail with this Data Security In Cloud Computing Architecture Cloud Cryptography. Use it as a tool for discussion and navigation on Architecture, Cryptographic, Data Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Autonomous Mobile Robots Architecture AMRs In Autonomous Security Robots ASRs
Autonomous Mobile Robots Architecture AMRs In Autonomous Security Robots ASRsThis slide describes the application of autonomous security robots to help security personnel. AMRs are also beneficial for cutting the high personnel costs and a thorough inspection of the incidents if anything suspicious is found. Deliver an outstanding presentation on the topic using this Autonomous Mobile Robots Architecture AMRs In Autonomous Security Robots ASRs. Dispense information and present a thorough explanation of Autonomous Security Robots, Security Personnel, Security Is A Rapidly Expanding, Future Inspection And Analysis using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Layered Defense Architecture For Secured Network
Layered Defense Architecture For Secured NetworkThis slide covers architecture of layer defense to protect integrity of information and to provide full enterprise security protection. It includes physical control, technical control and administrative control. Presenting our set of slides with Layered Defense Architecture For Secured Network. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Physical Control, Technical Control, Administrative Control.
-
 SASE Network Security All SASE Capabilities Integrated In Single Architecture
SASE Network Security All SASE Capabilities Integrated In Single ArchitectureDeliver an outstanding presentation on the topic using this SASE Network Security All SASE Capabilities Integrated In Single Architecture. Dispense information and present a thorough explanation of Network, Security, Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE Network Security Architecture And Working Of SD Wide Area Network
SASE Network Security Architecture And Working Of SD Wide Area NetworkThis slide represents the architecture and working of a software defined wide area network. The purpose of this slide is to demonstrate the different types of SD WAN architectures, such as on premise, cloud enabled and cloud enabled with backbone. It also caters to the basic operation of SD WAN. Present the topic in a bit more detail with this SASE Network Security Architecture And Working Of SD Wide Area Network. Use it as a tool for discussion and navigation on Architecture, Operation, Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE Network Security SASE Identity Centric Architecture Overview
SASE Network Security SASE Identity Centric Architecture OverviewThis slide outlines the overview of the centric architecture of the secure access service edge. The purpose of this slide is to demonstrate the various services executed by SASE architecture and components involved in this, such as enterprise data center, internet, internet edge, distributed edge, etc. Present the topic in a bit more detail with this SASE Network Security SASE Identity Centric Architecture Overview. Use it as a tool for discussion and navigation on Identities, Solutions, Activities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Access Service Edge Architecture Characteristics SASE Network Security
Secure Access Service Edge Architecture Characteristics SASE Network SecurityThis slide represents the architectural characteristics of a secure access service edge. The purpose of this slide is to showcase the features of SASE architecture that include identity driven, cloud native, support for all edges, and global distribution. Introducing Secure Access Service Edge Architecture Characteristics SASE Network Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Native, Support, Globally, using this template. Grab it now to reap its full benefits.
-
 Secure Access Service Edge SASE Architecture SASE Network Security
Secure Access Service Edge SASE Architecture SASE Network SecurityThis slide represents the SASE architecture overview and its goals. The purpose of this slide is to demonstrate the secure access service edge architecture and its goals. The building blocks of SASE Architecture include SWG, CASB, ZTNA, FWaaS, SD WAN, Thin Edge, and so on. Present the topic in a bit more detail with this Secure Access Service Edge SASE Architecture SASE Network Security. Use it as a tool for discussion and navigation on Connected, Presence, Scalable. This template is free to edit as deemed fit for your organization. Therefore download it now.




