Powerpoint Templates and Google slides for Analysis Of Security Attacks
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Root Cause Analysis Of IoT Password Attacks Internet Of Things IoT Security Cybersecurity SS
Root Cause Analysis Of IoT Password Attacks Internet Of Things IoT Security Cybersecurity SSThis slide showcases root cause analysis of internet of things IoT password attacks, referable for related businesses. It provides details about cybercriminal, login page, IoT device, video recordings, etc. Increase audience engagement and knowledge by dispensing information using Root Cause Analysis Of IoT Password Attacks Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on two stages. You can also present information on Record Conversation, Password Attack, Cyber Criminal, Root Cause Analysis using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
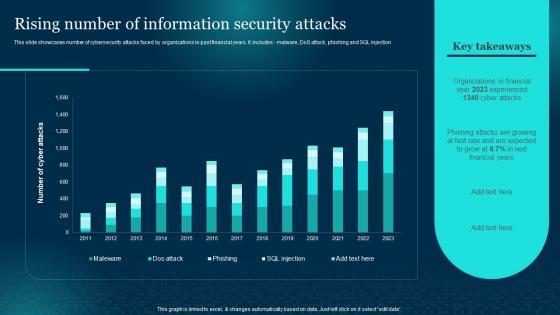 Rising Number Of Information Security Attacks Cybersecurity Risk Analysis And Management Plan
Rising Number Of Information Security Attacks Cybersecurity Risk Analysis And Management PlanThis slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection Present the topic in a bit more detail with this Rising Number Of Information Security Attacks Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Information, Security Attacks, Organizations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Impact Of Information Security Attacks Cybersecurity Risk Analysis And Management Plan
Financial Impact Of Information Security Attacks Cybersecurity Risk Analysis And Management PlanThis slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type Present the topic in a bit more detail with this Financial Impact Of Information Security Attacks Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Financial, Information, Organizations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Comparative Analysis Of Cyber Security Incident Mitigation Software
Cyber Security Attacks Response Comparative Analysis Of Cyber Security Incident Mitigation SoftwareThis slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Comparative Analysis Of Cyber Security Incident Mitigation Software. Use it as a tool for discussion and navigation on Comparative Analysis, Cyber Security Incident, Mitigation Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Gap Analysis Representing Current Situation Of Cybersecurity Incident
Cyber Security Attacks Response Gap Analysis Representing Current Situation Of Cybersecurity IncidentThis slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Present the topic in a bit more detail with this Cyber Security Attacks Response Gap Analysis Representing Current Situation Of Cybersecurity Incident. Use it as a tool for discussion and navigation on Gap Analysis, Representing Current Situation, Cybersecurity Incident, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Comparative Analysis Of Web Application Firewall Products
Cyber Security Attacks Response Plan Comparative Analysis Of Web Application Firewall ProductsThis slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Comparative Analysis Of Web Application Firewall Products. Dispense information and present a thorough explanation of Comparative Analysis, Web Application, Firewall Products using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Implementation For Cyber Security Department Wise Incident Analysis Of Malware Attacks
Firewall Implementation For Cyber Security Department Wise Incident Analysis Of Malware AttacksThis slide represents the number of attacks on each department in an organization. The purpose of this slide is to showcase the department-wise incident analysis of cyber-attacks on different departments such as finance, R and D, sales and marketing HR, IT, and others. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Department Wise Incident Analysis Of Malware Attacks. Dispense information and present a thorough explanation of Research And Development, Sales And Marketing, Incident Analysis, Malware Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Current Analysis Of Security Attacks Faced Implementing Organizational Security Training
Current Analysis Of Security Attacks Faced Implementing Organizational Security TrainingThe slide showcases analysis of current situation occurred in organization regarding IT and cloud security attacks. It includes graph, key objective and key takeaways. Present the topic in a bit more detail with this Current Analysis Of Security Attacks Faced Implementing Organizational Security Training. Use it as a tool for discussion and navigation on Graph Projecting Current Analysis, Security Attacks, Key Objective. This template is free to edit as deemed fit for your organization. Therefore download it now.



