Powerpoint Templates and Google slides for Access To Network
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
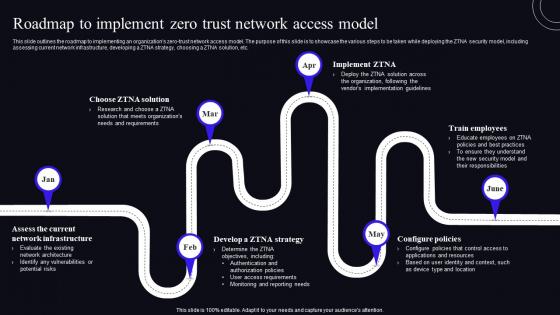 Roadmap To Implement Zero Trust Network Access Model Zero Trust Security Model
Roadmap To Implement Zero Trust Network Access Model Zero Trust Security ModelThis Slide Outlines The Roadmap To Implementing An Organizations Zero-Trust Network Access Model. The Purpose Of This Slide Is To Showcase The Various Steps To Be Taken While Deploying The ZTNA Security Model, Including Assessing Current Network Infrastructure, Developing A ZTNA Strategy, Choosing A ZTNA Solution, Etc. Increase Audience Engagement And Knowledge By Dispensing Information Using Roadmap To Implement Zero Trust Network Access Model Zero Trust Security Model. This Template Helps You Present Information On Six Stages. You Can Also Present Information On Roadmap, Network Infrastructure, Configure Policies Using This PPT Design. This Layout Is Completely Editable So Personaize It Now To Meet Your Audiences Expectations.
-
 Checklist To Build Zero Trust Network Access Architecture Zero Trust Security Model
Checklist To Build Zero Trust Network Access Architecture Zero Trust Security ModelThis slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Deliver an outstanding presentation on the topic using this Checklist To Build Zero Trust Network Access Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Architecture, Measures, Organizations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Reasons To Adopt Zero Trust Network Access Model Zero Trust Security Model
Reasons To Adopt Zero Trust Network Access Model Zero Trust Security ModelThis slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Introducing Reasons To Adopt Zero Trust Network Access Model Zero Trust Security Model to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Businesses, Resources, Organizations, using this template. Grab it now to reap its full benefits.
-
 Steps To Implement Zero Trust Network Access Model Zero Trust Security Model
Steps To Implement Zero Trust Network Access Model Zero Trust Security ModelThis slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Present the topic in a bit more detail with this Steps To Implement Zero Trust Network Access Model Zero Trust Security Model. Use it as a tool for discussion and navigation on Architecture, Protection, Monitor The Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Timeline To Implement Zero Trust Network Access Model Zero Trust Security Model
Timeline To Implement Zero Trust Network Access Model Zero Trust Security ModelThis slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Introducing Timeline To Implement Zero Trust Network Access Model Zero Trust Security Model to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, Implementation, Applications, using this template. Grab it now to reap its full benefits.
-
 Approaches To Implement Zero Trust Network Access Cloud Security Model
Approaches To Implement Zero Trust Network Access Cloud Security ModelThis slide depicts the two primary approaches to implementing zero trust network access for organizations. The purpose of this slide is to showcase the endpoint initiated and service initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Deliver an outstanding presentation on the topic using this Approaches To Implement Zero Trust Network Access Cloud Security Model. Dispense information and present a thorough explanation of Network, Access, Implement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Approaches To Implement Zero Trust Network Access
Sase Security Approaches To Implement Zero Trust Network AccessThis slide depicts the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Deliver an outstanding presentation on the topic using this Sase Security Approaches To Implement Zero Trust Network Access. Dispense information and present a thorough explanation of Approaches, Organizations, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Approaches To Implement Zero Trust Network Access Secure Access Service Edge Sase
Approaches To Implement Zero Trust Network Access Secure Access Service Edge SaseThis slide depicts the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Deliver an outstanding presentation on the topic using this Approaches To Implement Zero Trust Network Access Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Approaches, Endpoint Initiated, Service Initiated using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Implement Cloud Access Security Broker SASE Network Security
Best Practices To Implement Cloud Access Security Broker SASE Network SecurityThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker SASE Network Security. Dispense information and present a thorough explanation of Visibility, Risk, Release using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE Network Security Approaches To Implement Zero Trust Network Access
SASE Network Security Approaches To Implement Zero Trust Network AccessThis slide depicts the two primary approaches to implementing zero trust network access for organizations. The purpose of this slide is to showcase the endpoint initiated and service initiated approach of zero trust network access. It also includes how users access business services and applications in both approaches. Increase audience engagement and knowledge by dispensing information using SASE Network Security Approaches To Implement Zero Trust Network Access. This template helps you present information on two stages. You can also present information on Program, Environment, Service using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE Network Security Budget To Implement Secure Access Service Edge
SASE Network Security Budget To Implement Secure Access Service EdgeThis slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD WAN, SWG, ZTNA, CASB, and FWaaS. Deliver an outstanding presentation on the topic using this SASE Network Security Budget To Implement Secure Access Service Edge. Dispense information and present a thorough explanation of Network, Secure, Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE Network Security Checklist To Implement Secure Access Service Edge
SASE Network Security Checklist To Implement Secure Access Service EdgePresent the topic in a bit more detail with this SASE Network Security Checklist To Implement Secure Access Service Edge. Use it as a tool for discussion and navigation on Responsible, Service, Secure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE Network Security Introduction To Secure Access Service Edge SASE
SASE Network Security Introduction To Secure Access Service Edge SASEThis slide represents the introduction of SASE cloud security technology. The purpose of this slide is to demonstrate the core capabilities, benefits and key components of SASE. The key components include SD WAN, FWaaS, ZTNA, CASB, SWG, and unified management. Increase audience engagement and knowledge by dispensing information using SASE Network Security Introduction To Secure Access Service Edge SASE. This template helps you present information on three stages. You can also present information on Combination, Private, Irrespective using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE Network Security Roadmap To Implement Secure Access Service Edge
SASE Network Security Roadmap To Implement Secure Access Service EdgeThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Introducing SASE Network Security Roadmap To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Providers, Deployment, using this template. Grab it now to reap its full benefits.
-
 SASE Network Security Timeline To Implement Cloud Access Security Broker
SASE Network Security Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing SASE Network Security Timeline To Implement Cloud Access Security Broker to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Activity, Applications, Company, using this template. Grab it now to reap its full benefits.
-
 Timeline To Implement Secure Access Service Edge SASE Network Security
Timeline To Implement Secure Access Service Edge SASE Network SecurityThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing Timeline To Implement Secure Access Service Edge SASE Network Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Solutions, Regularly, using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Firewall Techniques To Restrict Access And Ensure Web Client Security
Firewall Network Security Firewall Techniques To Restrict Access And Ensure Web Client SecurityThis slide outlines the many ways to control access and guarantee web client security policy. The purpose of this slide is to highlight the firewall techniques to limit user access and confirm web user security, such as service control, direction control, user control and behavior control. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Firewall Techniques To Restrict Access And Ensure Web Client Security This template helps you present information on Four stages. You can also present information on Market By Deployment, Market By Solution using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Approaches To Implement Zero Trust Network Access
SD WAN Model Approaches To Implement Zero Trust Network AccessThis slide depicts the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Increase audience engagement and knowledge by dispensing information using SD WAN Model Approaches To Implement Zero Trust Network Access. This template helps you present information on one stages. You can also present information on Zero Trust Network Access, Service Initiated Approach, Business Services And Applications, Cloud Environment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Approaches To Implement Zero Trust Network Access
Sase Model Approaches To Implement Zero Trust Network AccessThis slide depicts the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Introducing Sase Model Approaches To Implement Zero Trust Network Access to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Service Initiated, Endpoint Initiated, using this template. Grab it now to reap its full benefits.
-
 Checklist To Build Zero Trust Network Access Architecture Identity Defined Networking
Checklist To Build Zero Trust Network Access Architecture Identity Defined NetworkingThis slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Deliver an outstanding presentation on the topic using this Checklist To Build Zero Trust Network Access Architecture Identity Defined Networking Dispense information and present a thorough explanation of Device Identity, Communication Channel, Network Segmentation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Reasons To Adopt Zero Trust Network Access Model Identity Defined Networking
Reasons To Adopt Zero Trust Network Access Model Identity Defined NetworkingThis slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Introducing Reasons To Adopt Zero Trust Network Access Model Identity Defined Networking to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Devices, Access Business, Network Activity using this template. Grab it now to reap its full benefits.
-
 Roadmap To Implement Zero Trust Network Access Model Identity Defined Networking
Roadmap To Implement Zero Trust Network Access Model Identity Defined NetworkingThis slide outlines the roadmap to implementing the zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including identifying assets and defining the protection surface, understanding the businesss existing security model, etc. Introducing Roadmap To Implement Zero Trust Network Access Model Identity Defined Networking to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Architecture, Monitor The Network, Businesss Existing using this template. Grab it now to reap its full benefits.
-
 Steps To Implement Zero Trust Network Access Model Identity Defined Networking
Steps To Implement Zero Trust Network Access Model Identity Defined NetworkingThis slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Present the topic in a bit more detail with this Steps To Implement Zero Trust Network Access Model Identity Defined Networking Use it as a tool for discussion and navigation on Mapping Transaction, Monitor The Network, Protection Surface This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Timeline To Implement Zero Trust Network Access Model Identity Defined Networking
Timeline To Implement Zero Trust Network Access Model Identity Defined NetworkingThis slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Introducing Timeline To Implement Zero Trust Network Access Model Identity Defined Networking to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Assess The Environment, Data Network, Timeline using this template. Grab it now to reap its full benefits.
-
 Checklist To Build Zero Trust Network Access Architecture Ppt Diagram Lists
Checklist To Build Zero Trust Network Access Architecture Ppt Diagram ListsThis slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Deliver an outstanding presentation on the topic using this Checklist To Build Zero Trust Network Access Architecture Ppt Diagram Lists. Dispense information and present a thorough explanation of Public Network, Network Topology, Devices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Reasons To Adopt Zero Trust Network Access Model Zero Trust Architecture ZTA
Reasons To Adopt Zero Trust Network Access Model Zero Trust Architecture ZTAThis slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Introducing Reasons To Adopt Zero Trust Network Access Model Zero Trust Architecture ZTA to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Traditional Network, Apps Directly, VPN, using this template. Grab it now to reap its full benefits.
-
 Steps To Implement Zero Trust Network Access Model Zero Trust Architecture ZTA
Steps To Implement Zero Trust Network Access Model Zero Trust Architecture ZTAThis slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Present the topic in a bit more detail with this Steps To Implement Zero Trust Network Access Model Zero Trust Architecture ZTA. Use it as a tool for discussion and navigation on Protection Surface, Security Model, Mapping Transaction Flows. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Timeline To Implement Zero Trust Network Access Model Ppt File Designs
Timeline To Implement Zero Trust Network Access Model Ppt File DesignsThis slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Introducing Timeline To Implement Zero Trust Network Access Model Ppt File Designs to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Zero Trust Team, Network, Applications, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Architecture ZTA Roadmap To Implement Zero Trust Network Access Model
Zero Trust Architecture ZTA Roadmap To Implement Zero Trust Network Access ModelThis slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. Introducing Zero Trust Architecture ZTA Roadmap To Implement Zero Trust Network Access Model to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Network Infrastructure, Ztna Solution, Configure Policies, using this template. Grab it now to reap its full benefits.
-
 ZTNA Roadmap To Implement Zero Trust Network Access Model
ZTNA Roadmap To Implement Zero Trust Network Access ModelThis slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. Increase audience engagement and knowledge by dispensing information using ZTNA Roadmap To Implement Zero Trust Network Access Model. This template helps you present information on six stages. You can also present information on Implement ZTNA, Configure Policies, Choose ZTNA Solution using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 0814 wifi access point connected to mobile phone and laptop over wireless network ppt slides
0814 wifi access point connected to mobile phone and laptop over wireless network ppt slidesWe are proud to present our 0814 wifi access point connected to mobile phone and laptop over wireless network ppt slides. This image slide displays Wi-Fi access point connected various technology devices. This image slide has been designed with graphic of wireless router, mobile phone, laptop and computer. This image slide depicts networking. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template to express views on wireless networking in your presentations. This image may also be used in computer education presentations. This image slide will impart professional appearance to your presentations.
-
 0814 wireless computer networking wifi access point connected to globe computers ppt slides
0814 wireless computer networking wifi access point connected to globe computers ppt slidesHigh-resolution images and the graphics. Edit the layout or the background of slide icons. Use of purposeful artwork in the slide icons. User-friendly when operated with the Google Slides. Indicating icons to fit in the presentation objective. Customize the background with your company’s brand name. Useful for the business professionals, managers and planners, marketing individuals.
-
 Introduction To Open Random Access Network Ran Open Ran It Ppt Professional Example Topics
Introduction To Open Random Access Network Ran Open Ran It Ppt Professional Example TopicsThis slide represents the introduction to open RAN standards in telecommunication systems, a partnership between device manufacturers and telecommunications to overcome the interoperability challenge. Deliver an outstanding presentation on the topic using this Introduction To Open Random Access Network Ran Open Ran It Ppt Professional Example Topics. Dispense information and present a thorough explanation of Introduction, Telecommunications, Interoperability Challenge using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Open Ran Technology Introduction To Open Random Access Network Ran Ppt Professional Display
Open Ran Technology Introduction To Open Random Access Network Ran Ppt Professional DisplayThis slide represents the introduction to open RAN standards in telecommunication systems, a partnership between device manufacturers and telecommunications to overcome the interoperability challenge. Deliver an outstanding presentation on the topic using this Open Ran Technology Introduction To Open Random Access Network Ran Ppt Professional Display. Dispense information and present a thorough explanation of Introduction, Telecommunications, Businesses using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE IT Approaches To Implement Zero Trust Network Access Ppt Demonstration
SASE IT Approaches To Implement Zero Trust Network Access Ppt DemonstrationThis slide depicts the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Introducing SASE IT Approaches To Implement Zero Trust Network Access Ppt Demonstration to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Endpoint Initiated, Service Initiated, using this template. Grab it now to reap its full benefits.
-
 ZTNA Checklist To Build Zero Trust Network Access Architecture
ZTNA Checklist To Build Zero Trust Network Access ArchitectureThis slide outlines the checklist to develop a zero trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Present the topic in a bit more detail with this ZTNA Checklist To Build Zero Trust Network Access Architecture. Use it as a tool for discussion and navigation on Network, Resources, Communication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 ZTNA Reasons To Adopt Zero Trust Network Access Model
ZTNA Reasons To Adopt Zero Trust Network Access ModelThis slide represents the importance of implementing the zero trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work from home culture, revealing IP addresses, network transparency, and so on. Introducing ZTNA Reasons To Adopt Zero Trust Network Access Model to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Internet, Resources, Devices, using this template. Grab it now to reap its full benefits.
-
 ZTNA Steps To Implement Zero Trust Network Access Model
ZTNA Steps To Implement Zero Trust Network Access ModelThis slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Present the topic in a bit more detail with this ZTNA Steps To Implement Zero Trust Network Access Model. Use it as a tool for discussion and navigation on Mapping Transaction Flows, Protection Surface, Design Ztna Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 ZTNA Timeline To Implement Zero Trust Network Access Model
ZTNA Timeline To Implement Zero Trust Network Access ModelIntroducing ZTNA Timeline To Implement Zero Trust Network Access Model to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Assess The Environment, Implement, Technology, using this template. Grab it now to reap its full benefits.
-
 Open RAN 5G Introduction To Open RANdom Access Network RAN
Open RAN 5G Introduction To Open RANdom Access Network RANThis slide represents the introduction to open RAN standards in telecommunication systems, a partnership between device manufacturers and telecommunications to overcome the interoperability challenge. Deliver an outstanding presentation on the topic using this Open RAN 5G Introduction To Open RANdom Access Network RAN. Dispense information and present a thorough explanation of System Integrator, Management, Control using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.



