Powerpoint Templates and Google slides for Access Security Model Broker
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cloud Access Security Broker CASB V2 API Scanning CASB Deployment Model
Cloud Access Security Broker CASB V2 API Scanning CASB Deployment ModelThis slide outlines the overview of the API scanning model of CASB deployment. The purpose of this slide is to showcase its features and introduce APIs and how this deployment works. It also represents the architecture of the API scanning model and its components include mobile and corporate devices and APIs. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 API Scanning CASB Deployment Model. Use it as a tool for discussion and navigation on Corporate Devices, Facilitate Communication, Real Time Protection, Non Intrusive Security Technique. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Overview Of CASB Deployment Models
Cloud Access Security Broker CASB V2 Overview Of CASB Deployment ModelsThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Overview Of CASB Deployment Models. This template helps you present information on four stages. You can also present information on Cloud Access Security Broker, Unmanaged Gadgets, Inline Deployment, Scalable And Strong Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Proxy Based CASB Deployment Model
Cloud Access Security Broker CASB V2 Proxy Based CASB Deployment ModelThis slide outlines the overview of proxy-based CASB deployment. The purpose of this slide is to highlight the proxy-based implementation of the CASB model and it also includes the fundamental modes of proxy deployment, including forward proxy and reverse proxy. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Proxy Based CASB Deployment Model. Dispense information and present a thorough explanation of Proxy Based Implementation, Proxy Deployment, Proxy And Reverse Proxy, Operation Of Several using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Requirements For Appropriate Cloud Security Model
Cloud Access Security Broker CASB V2 Requirements For Appropriate Cloud Security ModelThis slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Introducing Cloud Access Security Broker CASB V2 Requirements For Appropriate Cloud Security Model to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Visibility And Threat Detection, Continuous Compliance, Data Encryption, Strong Authentication, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Reverse Proxy CASB Deployment Model
Cloud Access Security Broker CASB V2 Reverse Proxy CASB Deployment ModelThis slide outlines the overview of the reverse proxy cloud access security model broker. The purpose of this slide is to showcase overview of working and various types of reverse proxy CASB. The main types include regular reverse proxies and load balancers. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Reverse Proxy CASB Deployment Model. This template helps you present information on five stages. You can also present information on Reverse Proxy, Cloud Access Security Model Broker, Web Server Anonymity, Websites With High Traffic using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices To Implement Cloud Access Security Broker Cloud Security Model
Best Practices To Implement Cloud Access Security Broker Cloud Security ModelThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker Cloud Security Model. Dispense information and present a thorough explanation of Implement, Practices, Visibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB Overview Cloud Security Model
Cloud Access Security Broker CASB Overview Cloud Security ModelThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Introducing Cloud Access Security Broker CASB Overview Cloud Security Model to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Visibility, Prevention, Management, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker Implementation Models Cloud Security Model
Cloud Access Security Broker Implementation Models Cloud Security ModelThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out of band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Implementation Models Cloud Security Model. This template helps you present information on three stages. You can also present information on Scanning, Forward, Reverse using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Use Cases Cloud Security Model
Cloud Access Security Broker Use Cases Cloud Security ModelThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker Use Cases Cloud Security Model. Dispense information and present a thorough explanation of Protection, Govern, Secure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Working Process Cloud Security Model
Cloud Access Security Broker Working Process Cloud Security ModelThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Working Process Cloud Security Model. This template helps you present information on three stages. You can also present information on Discovery, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Pillars Of Cloud Access Security Broker Cloud Security Model
Pillars Of Cloud Access Security Broker Cloud Security ModelThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Introducing Pillars Of Cloud Access Security Broker Cloud Security Model to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Compliance, Visibility, Security, using this template. Grab it now to reap its full benefits.
-
 Timeline To Implement Cloud Access Security Broker Cloud Security Model
Timeline To Implement Cloud Access Security Broker Cloud Security ModelThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing Timeline To Implement Cloud Access Security Broker Cloud Security Model to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Activity, Identify, Removal, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Broker Implementation Models Secure Access Service Edge Sase
Cloud Security Broker Implementation Models Secure Access Service Edge SaseThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using Cloud Security Broker Implementation Models Secure Access Service Edge Sase. This template helps you present information on three stages. You can also present information on Implementation, Applications, Inline Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Implementation Models SASE Network Security
Cloud Access Security Broker Implementation Models SASE Network SecurityThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out of band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing Cloud Access Security Broker Implementation Models SASE Network Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Scanning, Forward, Reverse, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Best Practices To Implement Cloud Access Security Broker
SD WAN Model Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this SD WAN Model Best Practices To Implement Cloud Access Security Broker. Dispense information and present a thorough explanation of Network And Cloud Infrastructure Monitoring, Protection Against Risks, Specific Risk Prototypes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SD WAN Model Cloud Access Security Broker Casb Overview
SD WAN Model Cloud Access Security Broker Casb OverviewThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Introducing SD WAN Model Cloud Access Security Broker Casb Overview to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Granular Cloud Usage Control, Data Loss Prevention, Cloud Access Security Broker, Risk Visibility, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Cloud Access Security Broker Implementation Models
SD WAN Model Cloud Access Security Broker Implementation ModelsThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using SD WAN Model Cloud Access Security Broker Implementation Models. This template helps you present information on three stages. You can also present information on Cloud Access Security Broker, Api Scanning, Forward Proxy, Reverse Proxy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Cloud Access Security Broker Use Cases
SD WAN Model Cloud Access Security Broker Use CasesThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Present the topic in a bit more detail with this SD WAN Model Cloud Access Security Broker Use Cases. Use it as a tool for discussion and navigation on Cloud Access Security Broker, Covering Protection Against Threats, Governing Usage, Securing Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Cloud Access Security Broker Working Process
SD WAN Model Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing SD WAN Model Cloud Access Security Broker Working Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Classification And Remediation, Control And Transparency Across Data, Risks In The Cloud, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Pillars Of Cloud Access Security Broker Ppt Icon Design Ideas
SD WAN Model Pillars Of Cloud Access Security Broker Ppt Icon Design IdeasThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Increase audience engagement and knowledge by dispensing information using SD WAN Model Pillars Of Cloud Access Security Broker Ppt Icon Design Ideas. This template helps you present information on four stages. You can also present information on Cloud Access Security Broker, Compliance, Visibility, Threat Protection, Data Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
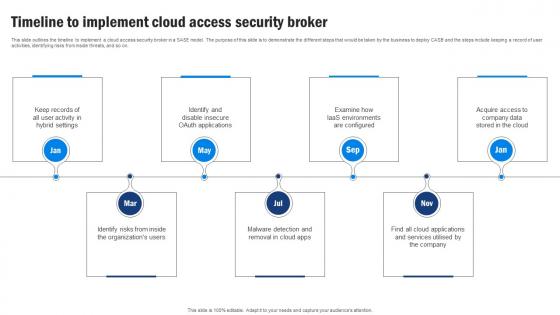 SD WAN Model Timeline To Implement Cloud Access Security Broker
SD WAN Model Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using SD WAN Model Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Cloud Access Security Broker, Environments Are Configured, Identify Risks, Malware Detection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Best Practices To Implement Cloud Access Security Broker
Sase Model Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Present the topic in a bit more detail with this Sase Model Best Practices To Implement Cloud Access Security Broker. Use it as a tool for discussion and navigation on Best Practices, Description, Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Cloud Access Security Broker Casb Overview
Sase Model Cloud Access Security Broker Casb OverviewThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Increase audience engagement and knowledge by dispensing information using Sase Model Cloud Access Security Broker Casb Overview. This template helps you present information on five stages. You can also present information on Risk Visibility, Threat Prevention, Granular Cloud using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Cloud Access Security Broker Implementation Models
Sase Model Cloud Access Security Broker Implementation ModelsThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing Sase Model Cloud Access Security Broker Implementation Models to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Scanning, Forward Proxy, Reverse Proxy, using this template. Grab it now to reap its full benefits.
-
 Sase Model Cloud Access Security Broker Use Cases
Sase Model Cloud Access Security Broker Use CasesThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Present the topic in a bit more detail with this Sase Model Cloud Access Security Broker Use Cases. Use it as a tool for discussion and navigation on Protection Against Threats, Govern Usage, Secure Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Cloud Access Security Broker Working Process
Sase Model Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Sase Model Cloud Access Security Broker Working Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Discovery, Classification, Remediation, using this template. Grab it now to reap its full benefits.
-
 Sase Model Pillars Of Cloud Access Security Broker
Sase Model Pillars Of Cloud Access Security BrokerThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Increase audience engagement and knowledge by dispensing information using Sase Model Pillars Of Cloud Access Security Broker. This template helps you present information on four stages. You can also present information on Compliance, Visibility, Threat Prevention using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Timeline To Implement Cloud Access Security Broker
Sase Model Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using Sase Model Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Hybrid Settings, Environments Are Configured, Cloud App using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE IT Cloud Access Security Broker Implementation Models Ppt Powerpoint Template
SASE IT Cloud Access Security Broker Implementation Models Ppt Powerpoint TemplateThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing SASE IT Cloud Access Security Broker Implementation Models Ppt Powerpoint Template to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on API Scanning, Forward Proxy, Reverse Proxy, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Cloud Access Security Broker CASB Ppt Model Guidelines
Icons Slide For Cloud Access Security Broker CASB Ppt Model GuidelinesPresenting our well crafted Icons Slide For Cloud Access Security Broker CASB Ppt Model Guidelines set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly
-
 Overview Of CASB Deployment Models Cloud Access Security Broker CASB
Overview Of CASB Deployment Models Cloud Access Security Broker CASBThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out of band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing Overview Of CASB Deployment Models Cloud Access Security Broker CASB. to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Deployment Models, Api Scanning, Forward Proxy, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB API Scanning CASB Deployment Model
Cloud Access Security Broker CASB API Scanning CASB Deployment ModelThis slide outlines the overview of the API scanning model of CASB deployment. The purpose of this slide is to showcase its features and introduce APIs and how this deployment works. It also represents the architecture of the API scanning model and its components include mobile and corporate devices and APIs. Present the topic in a bit more detail with this Cloud Access Security Broker CASB API Scanning CASB Deployment Model. Use it as a tool for discussion and navigation on Features, Apis, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB Future Use Of Emerging Technologies In CASB Model
Cloud Access Security Broker CASB Future Use Of Emerging Technologies In CASB ModelThis slide gives an overview of the technologies that can be used in the cloud access security broker model in the future. The purpose of this slide is to showcase the various emerging technologies that can help CASB to grow in the future. The technologies include AI, ML, CSPM, data privacy and protection, etc. Present the topic in a bit more detail with this Cloud Access Security Broker CASB Future Use Of Emerging Technologies In CASB Model. Use it as a tool for discussion and navigation on Technologies, Description, Zero Trust Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB Proxy Based CASB Deployment Model
Cloud Access Security Broker CASB Proxy Based CASB Deployment ModelThis slide outlines the overview of proxy based CASB deployment. The purpose of this slide is to highlight the proxy based implementation of the CASB model and it also includes the fundamental modes of proxy deployment, including forward proxy and reverse proxy. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB Proxy Based CASB Deployment Model. Dispense information and present a thorough explanation of Standard Modes, Operation Of Several, Origin Server using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB Reverse Proxy CASB Deployment Model
Cloud Access Security Broker CASB Reverse Proxy CASB Deployment ModelThis slide outlines the overview of the reverse proxy cloud access security model broker. The purpose of this slide is to showcase overview of working and various types of reverse proxy CASB. The main types include regular reverse proxies and load balancers. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB Reverse Proxy CASB Deployment Model. Dispense information and present a thorough explanation of Overview, Internet, Reverse Proxy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Pillar Data Security Ppt Portfolio Model
Cloud Access Security Broker Pillar Data Security Ppt Portfolio ModelThis slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Introducing Cloud Access Security Broker Pillar Data Security Ppt Portfolio Model. to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Technologies, Sophisticated, Functions, using this template. Grab it now to reap its full benefits.



