Powerpoint Templates and Google slides for Access Networks
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Network Access Control As An Element Of Network Security Training Ppt
Network Access Control As An Element Of Network Security Training PptPresenting Network Access Control as an Element of Network Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Cloud Access Security Brokers As An Element Of Network Security Training Ppt
Cloud Access Security Brokers As An Element Of Network Security Training PptPresenting Cloud Access Security Brokers as an Element of Network Security. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Hosting Storage Server Horizontal Accessibility Network Microphone
Hosting Storage Server Horizontal Accessibility Network MicrophoneDeliver a lucid presentation by utilizing this Hosting Storage Server Horizontal Accessibility Network Microphone. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as Hosting, Storage, Server, Horizontal, Accessibility. All the twelve slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
 Cloud network icon representing internet accessible connection servers
Cloud network icon representing internet accessible connection serversEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Cloud Network Icon Representing Internet Accessible Connection Servers is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With twelve slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
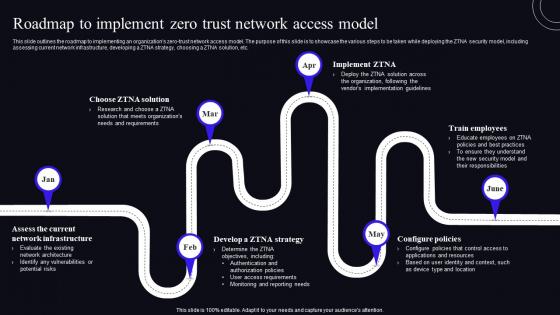 Roadmap To Implement Zero Trust Network Access Model Zero Trust Security Model
Roadmap To Implement Zero Trust Network Access Model Zero Trust Security ModelThis Slide Outlines The Roadmap To Implementing An Organizations Zero-Trust Network Access Model. The Purpose Of This Slide Is To Showcase The Various Steps To Be Taken While Deploying The ZTNA Security Model, Including Assessing Current Network Infrastructure, Developing A ZTNA Strategy, Choosing A ZTNA Solution, Etc. Increase Audience Engagement And Knowledge By Dispensing Information Using Roadmap To Implement Zero Trust Network Access Model Zero Trust Security Model. This Template Helps You Present Information On Six Stages. You Can Also Present Information On Roadmap, Network Infrastructure, Configure Policies Using This PPT Design. This Layout Is Completely Editable So Personaize It Now To Meet Your Audiences Expectations.
-
 Top Tenets Of Zero Trust Network Access Model Zero Trust Security Model
Top Tenets Of Zero Trust Network Access Model Zero Trust Security ModelDeliver an outstanding presentation on the topic using this Top Tenets Of Zero Trust Network Access Model Zero Trust Security Model. Dispense information and present a thorough explanation of Continuous Authentication, Data Protection, Facilitate Least Privilege Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Working Of Zero Trust Network Access Model Zero Trust Security Model
Working Of Zero Trust Network Access Model Zero Trust Security ModelThis slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Deliver an outstanding presentation on the topic using this Working Of Zero Trust Network Access Model Zero Trust Security Model. Dispense information and present a thorough explanation of Demonstrate, Architectures, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE Network Security Global Market Of Secure Access Service Edge
SASE Network Security Global Market Of Secure Access Service EdgeThis slide depicts the global market size of the SASE market by components such as platforms and services. The purpose of this slide is to showcase the compound annual growth rate for the SASE model, including its growth drivers, such as cloud adoption, work from anywhere culture, and so on. Deliver an outstanding presentation on the topic using this SASE Network Security Global Market Of Secure Access Service Edge. Dispense information and present a thorough explanation of Service, Secure, Global using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Access Service Edge Performance Tracking Dashboard SASE Network Security
Secure Access Service Edge Performance Tracking Dashboard SASE Network SecurityThis slide demonstrates the performance tracking dashboard for secure access service edge. The purpose of this slide is to showcase the overall performance of the SASE model, including connections, critical network alarms, critical security alerts, application volume, risky applications, and unblocked security threats. Deliver an outstanding presentation on the topic using this Secure Access Service Edge Performance Tracking Dashboard SASE Network Security. Dispense information and present a thorough explanation of Service, Performance, Tracking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Top Tenets Of Zero Trust Network Access Model Identity Defined Networking
Top Tenets Of Zero Trust Network Access Model Identity Defined NetworkingPresent the topic in a bit more detail with this Top Tenets Of Zero Trust Network Access Model Identity Defined Networking Use it as a tool for discussion and navigation on Top Tenets, Trust Network, Access Model This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Top Tenets Of Zero Trust Network Access Model Ppt File Example
Top Tenets Of Zero Trust Network Access Model Ppt File ExampleDeliver an outstanding presentation on the topic using this Top Tenets Of Zero Trust Network Access Model Ppt File Example. Dispense information and present a thorough explanation of Top Tenets, Zero Trust Network, Access Model using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Suppliers Limited Access Networks In Powerpoint And Google Slides Cpb
Suppliers Limited Access Networks In Powerpoint And Google Slides CpbPresenting Suppliers Limited Access Networks In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Suppliers Limited Access Networks. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Network Management Cloud Access Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Network Management Cloud Access Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon is perfect for representing wireless cloud access. It features a vibrant blue cloud with a white antenna, making it eye-catching and easy to identify. Its ideal for use in presentations, websites, and other digital projects.
-
 Network Management Cloud Access Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Network Management Cloud Access Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMonotone PowerPoint Icon on Wireless Cloud Access is a simple, yet powerful vector graphic that is perfect for presentations or webpages. It is a modern, minimalistic design that conveys a strong message of connectivity and access to the cloud. It is a great choice for any project that needs a professional, yet eye-catching design.
-
 Wireless Network Cloud Access Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Wireless Network Cloud Access Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon is perfect for representing wireless cloud access. It features a vibrant blue cloud with a white antenna, making it eye-catching and easy to identify. Its ideal for use in presentations, websites, and other digital projects.
-
 Wireless Network Cloud Access Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Wireless Network Cloud Access Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMonotone PowerPoint Icon on Wireless Cloud Access is a simple, yet powerful vector graphic that is perfect for presentations or webpages. It is a modern, minimalistic design that conveys a strong message of connectivity and access to the cloud. It is a great choice for any project that needs a professional, yet eye-catching design.
-
 Wireless Mail Access Network Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Wireless Mail Access Network Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon is the perfect way to represent wireless mail access. It features a blue and green mail icon with a white wireless signal emanating from it, making it an eye-catching and informative visual. It is a great way to illustrate the concept of wireless mail access in a presentation.
-
 Wireless Mail Access Network Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Wireless Mail Access Network Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is perfect for illustrating wireless mail access. It features a simple design with a mail envelope icon and a wireless signal symbol. It is an ideal choice for presentations, infographics, and other visuals.
-
 Before Vs After Zero Trust Network Access Implementation Zero Trust Security Model
Before Vs After Zero Trust Network Access Implementation Zero Trust Security ModelThis slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Deliver an outstanding presentation on the topic using this Before Vs After Zero Trust Network Access Implementation Zero Trust Security Model. Dispense information and present a thorough explanation of Implementation, Distributed, Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Benefits Of Zero Trust Network Access ZTNA Zero Trust Security Model
Benefits Of Zero Trust Network Access ZTNA Zero Trust Security ModelThis Slide Represents The Benefits Of Zero Trust Network Access, A Component Of SASE Technology. The Purpose Of This Slide Is To Demonstrate The Multiple Benefits Of ZTNA To Businesses And Users. It Also Caters To The Security Benefits Such As Increased Control And Visibility, Invisible Infrastructure, And Simple App Segmentation. Present The Topic In A Bit More Detail With This Benefits Of Zero Trust Network Access ZTNA Zero Trust Security Model. Use It As A Tool For Discussion And Navigation On Deployment, Experiences, Appliances. This Template Is Free To Edit As Deemed Fit For Your Organization. Therefore Download It Now.
-
 Checklist To Build Zero Trust Network Access Architecture Zero Trust Security Model
Checklist To Build Zero Trust Network Access Architecture Zero Trust Security ModelThis slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Deliver an outstanding presentation on the topic using this Checklist To Build Zero Trust Network Access Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Architecture, Measures, Organizations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Critical Principles Of Zero Trust Network Access Model Zero Trust Security Model
Critical Principles Of Zero Trust Network Access Model Zero Trust Security ModelThis slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. Present the topic in a bit more detail with this Critical Principles Of Zero Trust Network Access Model Zero Trust Security Model. Use it as a tool for discussion and navigation on Description, Segmentation, Validation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1585 Zero Trust Network Access Architectural Models Zero Trust Security Model
F1585 Zero Trust Network Access Architectural Models Zero Trust Security ModelThis slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Introducing F1585 Zero Trust Network Access Architectural Models Zero Trust Security Model to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Architectural, Resources, Verification, using this template. Grab it now to reap its full benefits.
-
 F1586 Zero Trust Network Access Architecture Overview Zero Trust Security Model
F1586 Zero Trust Network Access Architecture Overview Zero Trust Security ModelThis slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Present the topic in a bit more detail with this F1586 Zero Trust Network Access Architecture Overview Zero Trust Security Model. Use it as a tool for discussion and navigation on Resources, Architecture, Overview. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1587 Zero Trust Network Access Architecture Workflow Zero Trust Security Model
F1587 Zero Trust Network Access Architecture Workflow Zero Trust Security ModelThis slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Increase audience engagement and knowledge by dispensing information using F1587 Zero Trust Network Access Architecture Workflow Zero Trust Security Model. This template helps you present information on six stages. You can also present information on Architecture, Workflow, Resources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 F1588 Zero Trust Network Access Implementation Challenges Zero Trust Security Model
F1588 Zero Trust Network Access Implementation Challenges Zero Trust Security ModelThis slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on Present the topic in a bit more detail with this F1588 Zero Trust Network Access Implementation Challenges Zero Trust Security Model. Use it as a tool for discussion and navigation on Implementation, Organizations, Productivity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1589 Zero Trust Network Access Performance Tracking Dashboard Zero Trust Security Model
F1589 Zero Trust Network Access Performance Tracking Dashboard Zero Trust Security ModelThis slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. Deliver an outstanding presentation on the topic using this F1589 Zero Trust Network Access Performance Tracking Dashboard Zero Trust Security Model. Dispense information and present a thorough explanation of Performance, Dashboard, Represents using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F1590 Zero Trust Network Access System Use Cases Zero Trust Security Model
F1590 Zero Trust Network Access System Use Cases Zero Trust Security ModelThis slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Present the topic in a bit more detail with this F1590 Zero Trust Network Access System Use Cases Zero Trust Security Model. Use it as a tool for discussion and navigation on Internal Firewall Replacement, Limiting User Access, Network Access Control Replacement. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1591 Zero Trust Network Access User Flow Overview Zero Trust Security Model
F1591 Zero Trust Network Access User Flow Overview Zero Trust Security ModelThis slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Deliver an outstanding presentation on the topic using this F1591 Zero Trust Network Access User Flow Overview Zero Trust Security Model. Dispense information and present a thorough explanation of Authentication, Process, Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F1592 Zero Trust Network Access ZTNA Introduction Zero Trust Security Model
F1592 Zero Trust Network Access ZTNA Introduction Zero Trust Security ModelThis slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Present the topic in a bit more detail with this F1592 Zero Trust Network Access ZTNA Introduction Zero Trust Security Model. Use it as a tool for discussion and navigation on Introduction, Appliances, Infrastructure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1593 Zero Trust Network Access Vs Virtual Private Network Zero Trust Security Model
F1593 Zero Trust Network Access Vs Virtual Private Network Zero Trust Security ModelThis slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access. Deliver an outstanding presentation on the topic using this F1593 Zero Trust Network Access Vs Virtual Private Network Zero Trust Security Model. Dispense information and present a thorough explanation of Infrastructure, Configuration, Equipment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Features Of Zero Trust Network Access Security Model Zero Trust Security Model
Features Of Zero Trust Network Access Security Model Zero Trust Security ModelThis slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Present the topic in a bit more detail with this Features Of Zero Trust Network Access Security Model Zero Trust Security Model. Use it as a tool for discussion and navigation on Organizations, Applications, Infrastructure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Main Pillars Of Zero Network Trust Access Zero Trust Security Model
Main Pillars Of Zero Network Trust Access Zero Trust Security ModelThis slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation. Present the topic in a bit more detail with this Main Pillars Of Zero Network Trust Access Zero Trust Security Model. Use it as a tool for discussion and navigation on Application, Infrastructure, Orchestration Automation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Reasons To Adopt Zero Trust Network Access Model Zero Trust Security Model
Reasons To Adopt Zero Trust Network Access Model Zero Trust Security ModelThis slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Introducing Reasons To Adopt Zero Trust Network Access Model Zero Trust Security Model to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Businesses, Resources, Organizations, using this template. Grab it now to reap its full benefits.
-
 Steps To Implement Zero Trust Network Access Model Zero Trust Security Model
Steps To Implement Zero Trust Network Access Model Zero Trust Security ModelThis slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Present the topic in a bit more detail with this Steps To Implement Zero Trust Network Access Model Zero Trust Security Model. Use it as a tool for discussion and navigation on Architecture, Protection, Monitor The Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Technologies Used In Zero Trust Network Access Zero Trust Security Model
Technologies Used In Zero Trust Network Access Zero Trust Security ModelThis slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer. Deliver an outstanding presentation on the topic using this Technologies Used In Zero Trust Network Access Zero Trust Security Model. Dispense information and present a thorough explanation of Technologies, Techniques, Protection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Timeline To Implement Zero Trust Network Access Model Zero Trust Security Model
Timeline To Implement Zero Trust Network Access Model Zero Trust Security ModelThis slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Introducing Timeline To Implement Zero Trust Network Access Model Zero Trust Security Model to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, Implementation, Applications, using this template. Grab it now to reap its full benefits.
-
 Top Zero Trust Network Access Software Solutions Zero Trust Security Model
Top Zero Trust Network Access Software Solutions Zero Trust Security ModelThis slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. Present the topic in a bit more detail with this Top Zero Trust Network Access Software Solutions Zero Trust Security Model. Use it as a tool for discussion and navigation on Software, Solutions, Implementation . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Traditional Security Models Vs Zero Trust Network Access Zero Trust Security Model
Traditional Security Models Vs Zero Trust Network Access Zero Trust Security ModelThis slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Present the topic in a bit more detail with this Traditional Security Models Vs Zero Trust Network Access Zero Trust Security Model. Use it as a tool for discussion and navigation on Dependence, Foundation, Attack Surface. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Training Program For Zero Trust Network Access Model Zero Trust Security Model
Training Program For Zero Trust Network Access Model Zero Trust Security ModelThis slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Deliver an outstanding presentation on the topic using this Training Program For Zero Trust Network Access Model Zero Trust Security Model. Dispense information and present a thorough explanation of Micro Segmentation, Solutions, Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Types Of Zero Trust Network Access ZTNA Models Zero Trust Security Model
Types Of Zero Trust Network Access ZTNA Models Zero Trust Security ModelThis Slide Describes The Various Types Of Zero-Trust Network Access Models. The Purpose Of This Slide Is To Demonstrate The Various ZTNA Models And Core Elements Of ZTNA Implementation. The Model Types Include User Protection, Workload Protection, And Device Protection. Present The Topic In A Bit More Detail With This Types Of Zero Trust Network Access ZTNA Models Zero Trust Security Model. Use It As A Tool For Discussion And Navigation On Knowledge Conviction, Disruptive Technologies, Cultural Mindset Change. This Template Is Free To Edit As Deemed Fit For Your Organization. Therefore Download It Now.
-
 Working Functions Of Zero Trust Network Access Architecture Zero Trust Security Model
Working Functions Of Zero Trust Network Access Architecture Zero Trust Security ModelThis slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Introducing Working Functions Of Zero Trust Network Access Architecture Zero Trust Security Model to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Architecture, Abnormalities, Processing, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Network Access Vs Zero Trust Architecture Zero Trust Security Model
Zero Trust Network Access Vs Zero Trust Architecture Zero Trust Security ModelThis slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Deliver an outstanding presentation on the topic using this Zero Trust Network Access Vs Zero Trust Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Architecture, Implementation, Technologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Relationship Between Secure Access Service Edge And Network Security Using Secure Web Gateway
Relationship Between Secure Access Service Edge And Network Security Using Secure Web GatewayThis slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc. Present the topic in a bit more detail with this Relationship Between Secure Access Service Edge And Network Security Using Secure Web Gateway. Use it as a tool for discussion and navigation on Relationship, Distributed, Environment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Storage Area Network San Storage Area Network Attacks Unauthorized Access
Storage Area Network San Storage Area Network Attacks Unauthorized AccessThis Slide Represents The Unauthorized Type Of SAN Attack, Including Its Control Points. This Slide Aims To Give An Overview Of Unauthorized Access And The Various Control Points That Can Prevent Unauthorized Access, Including Out-Of-Band And In-Band Management Apps, Device-To-Device, Device-To-Fabric, And So On. Present The Topic In A Bit More Detail With This Storage Area Network San Storage Area Network Attacks Unauthorized Access. Use It As A Tool For Discussion And Navigation On Unauthorized, Overview, Service. This Template Is Free To Edit As Deemed Fit For Your Organization. Therefore Download It Now.
-
 Approaches To Implement Zero Trust Network Access Cloud Security Model
Approaches To Implement Zero Trust Network Access Cloud Security ModelThis slide depicts the two primary approaches to implementing zero trust network access for organizations. The purpose of this slide is to showcase the endpoint initiated and service initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Deliver an outstanding presentation on the topic using this Approaches To Implement Zero Trust Network Access Cloud Security Model. Dispense information and present a thorough explanation of Network, Access, Implement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Benefits Of Zero Trust Network Access ZTNA Cloud Security Model
Benefits Of Zero Trust Network Access ZTNA Cloud Security ModelThis slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Deliver an outstanding presentation on the topic using this Benefits Of Zero Trust Network Access ZTNA Cloud Security Model. Dispense information and present a thorough explanation of Benefits, Description, Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Types Of Zero Trust Network Access ZTNA Models Cloud Security Model
Types Of Zero Trust Network Access ZTNA Models Cloud Security ModelThis slide describes the various types of zero trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Increase audience engagement and knowledge by dispensing information using Types Of Zero Trust Network Access ZTNA Models Cloud Security Model. This template helps you present information on three stages. You can also present information on Change, Technologies, Knowledge using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Working Of Zero Trust Network Access Cloud Security Model
Working Of Zero Trust Network Access Cloud Security ModelThis slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Deliver an outstanding presentation on the topic using this Working Of Zero Trust Network Access Cloud Security Model. Dispense information and present a thorough explanation of Working, Network, Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Zero Trust Network Access Vs Virtual Private Network Cloud Security Model
Zero Trust Network Access Vs Virtual Private Network Cloud Security ModelThis slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application level access. Present the topic in a bit more detail with this Zero Trust Network Access Vs Virtual Private Network Cloud Security Model. Use it as a tool for discussion and navigation on Workforce, Network, Private. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Zero Trust Network Access ZTNA Introduction Cloud Security Model
Zero Trust Network Access ZTNA Introduction Cloud Security ModelThis slide represents the overview of zero trust network access, including its architecture. The purpose of this slide is to demonstrate the overview and use cases of ZTNA. The primary use cases include authentication and access control and holistic control and visibility. Deliver an outstanding presentation on the topic using this Zero Trust Network Access ZTNA Introduction Cloud Security Model. Dispense information and present a thorough explanation of Network, Access, Introduction using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Approaches To Implement Zero Trust Network Access
Sase Security Approaches To Implement Zero Trust Network AccessThis slide depicts the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Deliver an outstanding presentation on the topic using this Sase Security Approaches To Implement Zero Trust Network Access. Dispense information and present a thorough explanation of Approaches, Organizations, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Benefits Of Zero Trust Network Access Ztna
Sase Security Benefits Of Zero Trust Network Access ZtnaThis slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Deliver an outstanding presentation on the topic using this Sase Security Benefits Of Zero Trust Network Access Ztna. Dispense information and present a thorough explanation of Description, Segmentation, Demonstrate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Types Of Zero Trust Network Access Ztna Models
Sase Security Types Of Zero Trust Network Access Ztna ModelsThis slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Deliver an outstanding presentation on the topic using this Sase Security Types Of Zero Trust Network Access Ztna Models. Dispense information and present a thorough explanation of Knowledge Conviction, Disruptive Technologies, Cultural Mindset Change using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Working Of Zero Trust Network Access
Sase Security Working Of Zero Trust Network AccessThis slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Deliver an outstanding presentation on the topic using this Sase Security Working Of Zero Trust Network Access. Dispense information and present a thorough explanation of Resources, Situations, Multiprotocol using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Zero Network Access Vs Virtual Private Network Ppt Show Design Templates
Sase Security Zero Network Access Vs Virtual Private Network Ppt Show Design TemplatesThis slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access. Present the topic in a bit more detail with this Sase Security Zero Network Access Vs Virtual Private Network Ppt Show Design Templates. Use it as a tool for discussion and navigation on Equipment, Infrastructure, Configuration . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Zero Trust Network Access Ztna Introduction
Sase Security Zero Trust Network Access Ztna IntroductionThis slide represents the overview of zero trust network access, including its architecture. The purpose of this slide is to demonstrate the overview and use cases of ZTNA. The primary use cases include authentication and access control and holistic control and visibility. Deliver an outstanding presentation on the topic using this Sase Security Zero Trust Network Access Ztna Introduction. Dispense information and present a thorough explanation of Introduction, Businesss, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sd Wan And Secure Access Service Edge Sase Software Defined Wide Area Network
Sd Wan And Secure Access Service Edge Sase Software Defined Wide Area NetworkThis slide represents the relationship between secure access service edge and software-defined wide area network. It also includes the benefits of SASE and its security features, such as software-defined WAN, firewall as a service, zero-trust network access, cloud access security broker, secure web gateway, and unified management Deliver an outstanding presentation on the topic using this Sd Wan And Secure Access Service Edge Sase Software Defined Wide Area Network. Dispense information and present a thorough explanation of Regulations, Application, Combination using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Access Service Edge Vs Sd Wan Software Defined Wide Area Network
Secure Access Service Edge Vs Sd Wan Software Defined Wide Area NetworkThis slide compares secure access service edge and software-defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD-WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access. Present the topic in a bit more detail with this Secure Access Service Edge Vs Sd Wan Software Defined Wide Area Network. Use it as a tool for discussion and navigation on Business, Requirements, Locations . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Approaches To Implement Zero Trust Network Access Secure Access Service Edge Sase
Approaches To Implement Zero Trust Network Access Secure Access Service Edge SaseThis slide depicts the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Deliver an outstanding presentation on the topic using this Approaches To Implement Zero Trust Network Access Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Approaches, Endpoint Initiated, Service Initiated using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.




