Comprehensive Training Curriculum on Cybersecurity Awareness Training PPT
What is it
- EduDecks are professionally-created comprehensive decks that provide complete coverage of the subject under discussion
- These are also innovatively-designed for a powerful learning experience and maximum retention
Who is it for?
- EduDecks are for Trainers who want to add punch and flair to program and leave a lasting impact on their trainees
- They are also for Teachers who want to win over their students with content as well design
Why EduDecks?
- EduDecks provide an A-Z coverage of courses on any topic and covers it in both great depth and wide scope
- These slides are also professionally-designed to deliver a punch to your programs
Why Corporate Trainers love us?
- Content created by Industry experts, active in their fields
- Relevant concepts supplemented with industry case studies
- Visually appealing slides with 100% accurate & relevant data
Why Teachers love us?
- Comprehensive curriculum covering all aspects of the topic
- Relevant examples provided with the topics
- Just download and amaze your audience without making any content changes
What you will get
- 03 Structured Sessions
- 20+ Multiple Choice Questions
- 15+ Thought Provoking Discussion Questions
- Detailed Instructor Notes
- 400+ Professionally Designed Slides
People who downloaded this PowerPoint presentation also viewed the following :
Create an Immersive Training Experience
Created by Subject Matter Experts
Professionally Designed Slides
Structured Sessions
Comprehensive Curriculum
Detailed Teaching Notes
Real-Life Case Studies
Assessment Questions
Client Proposal
Complete Curriculum
- What is Cybersecurity?
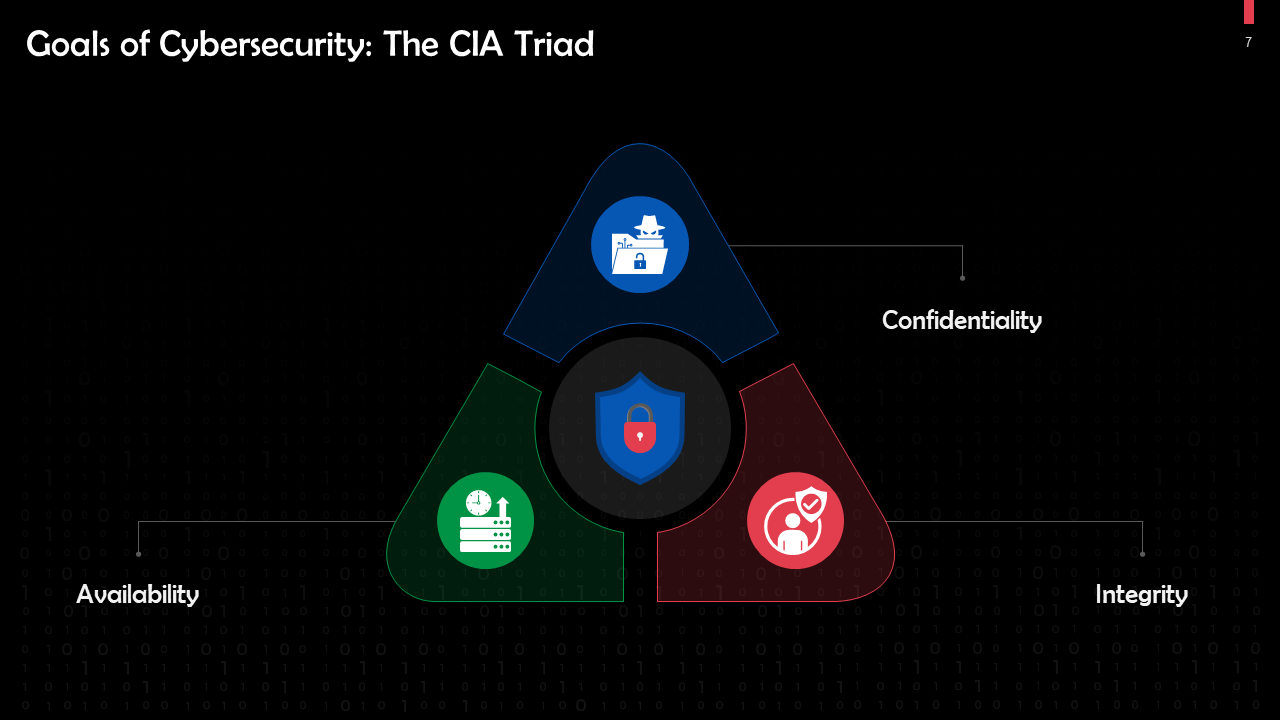
- Goals of Cybersecurity
- Confidentiality
- Integrity
- Availability
- Components of Cybersecurity
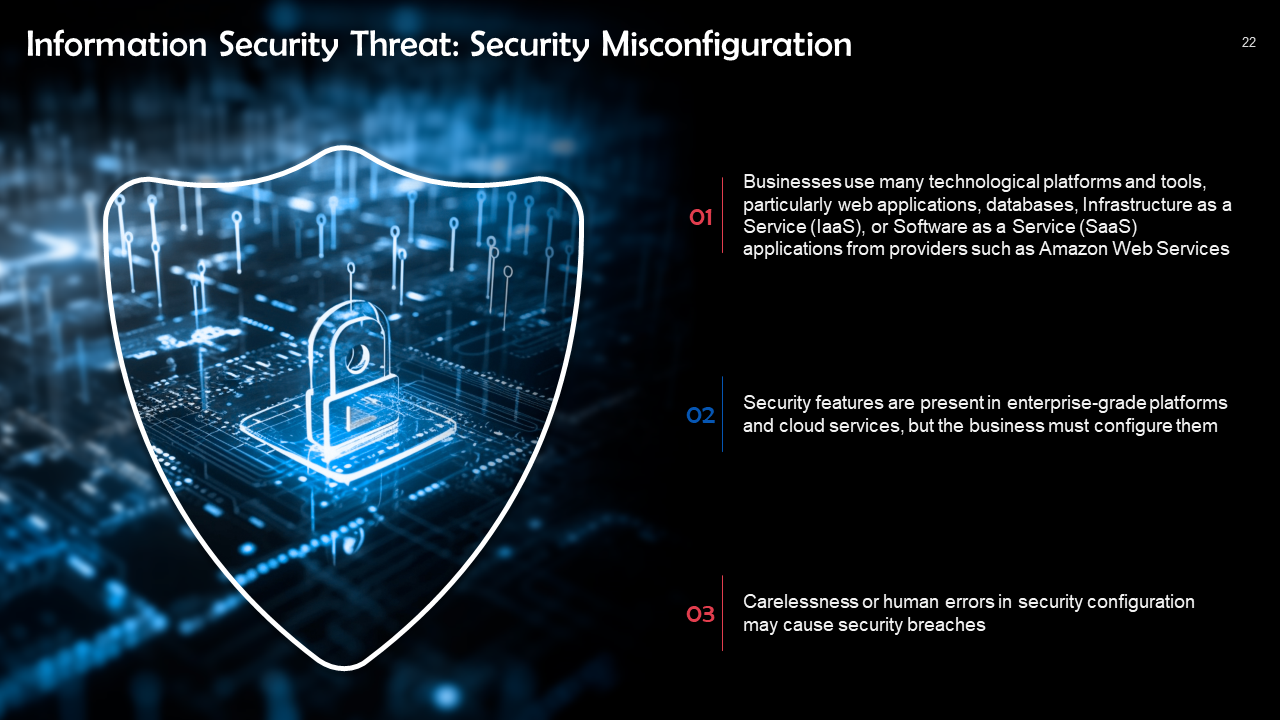
- Information Security
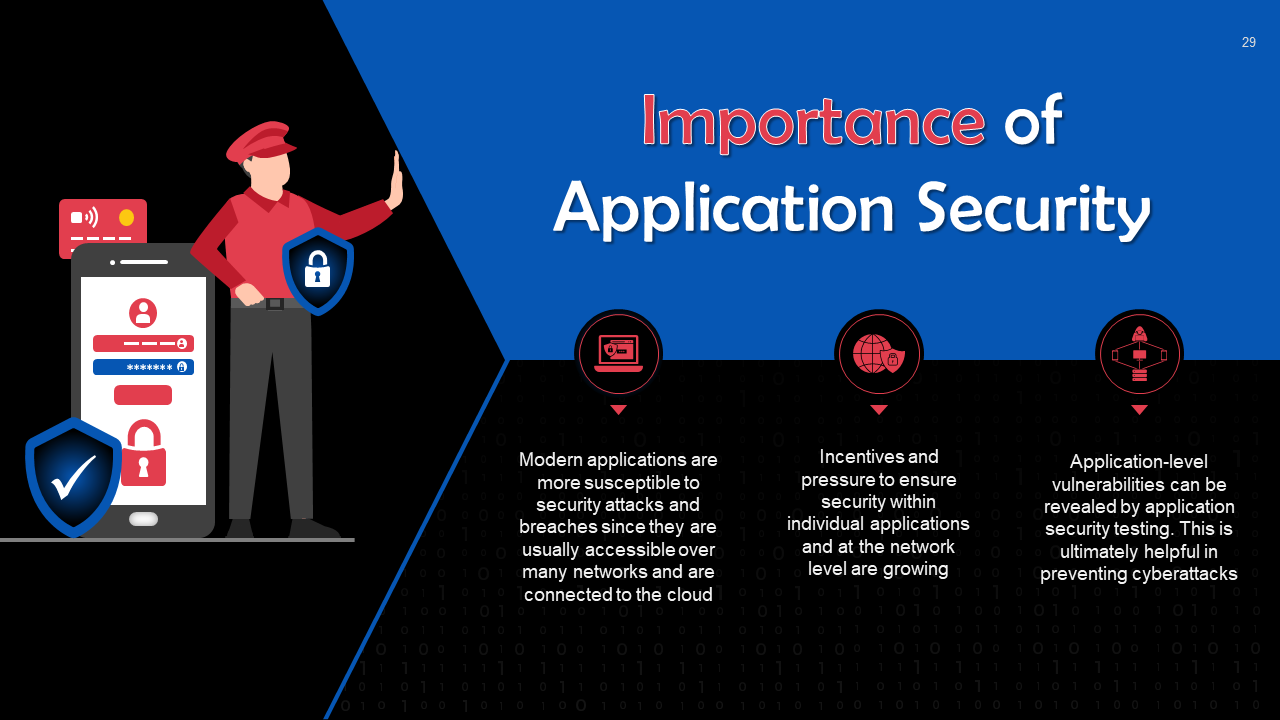
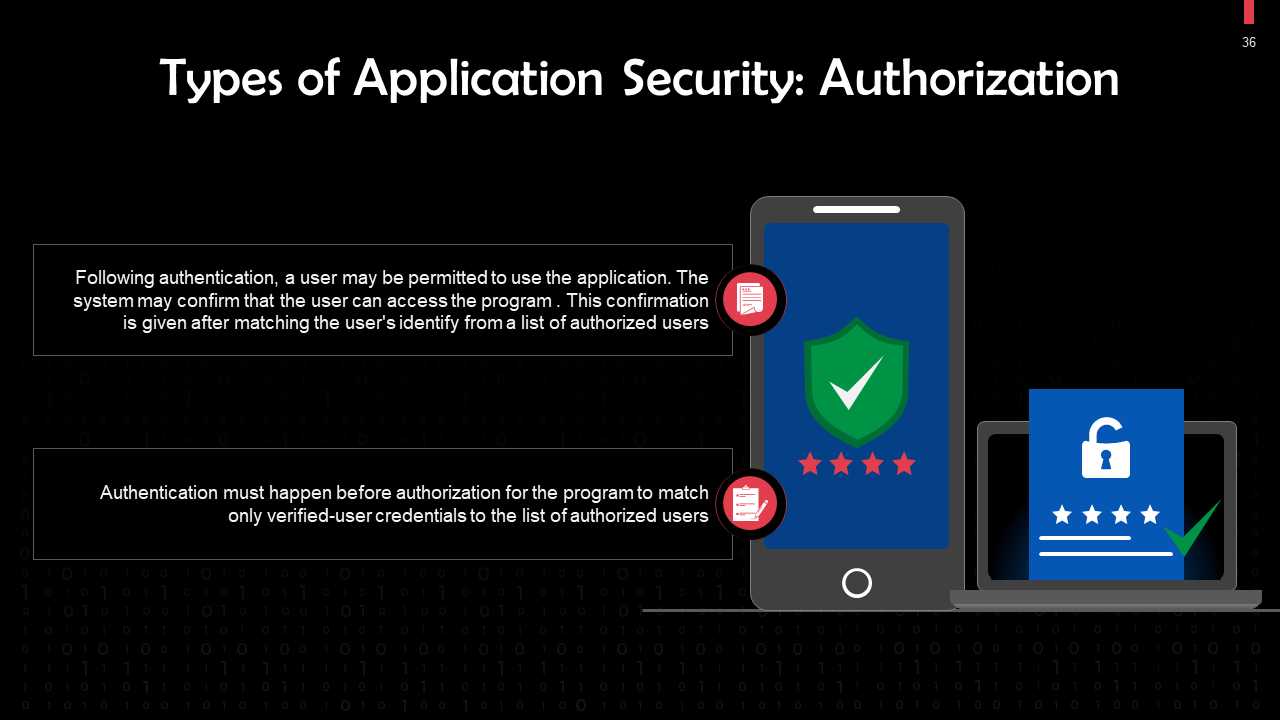
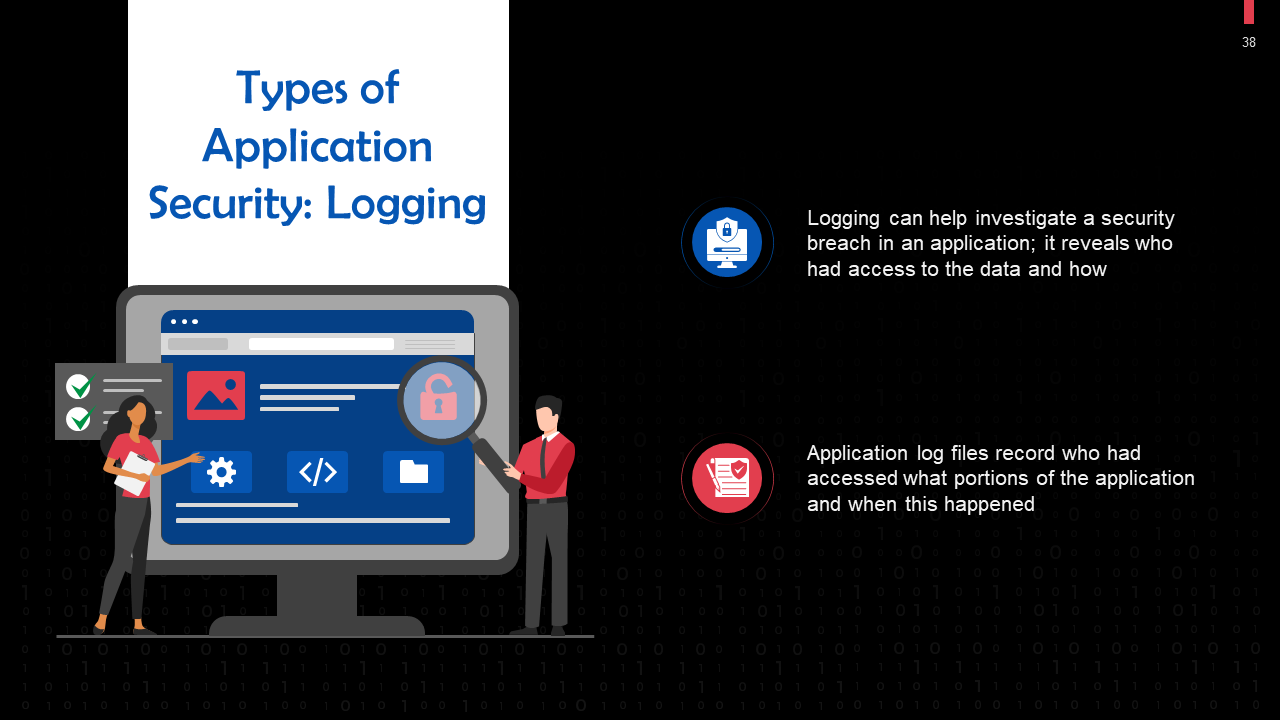
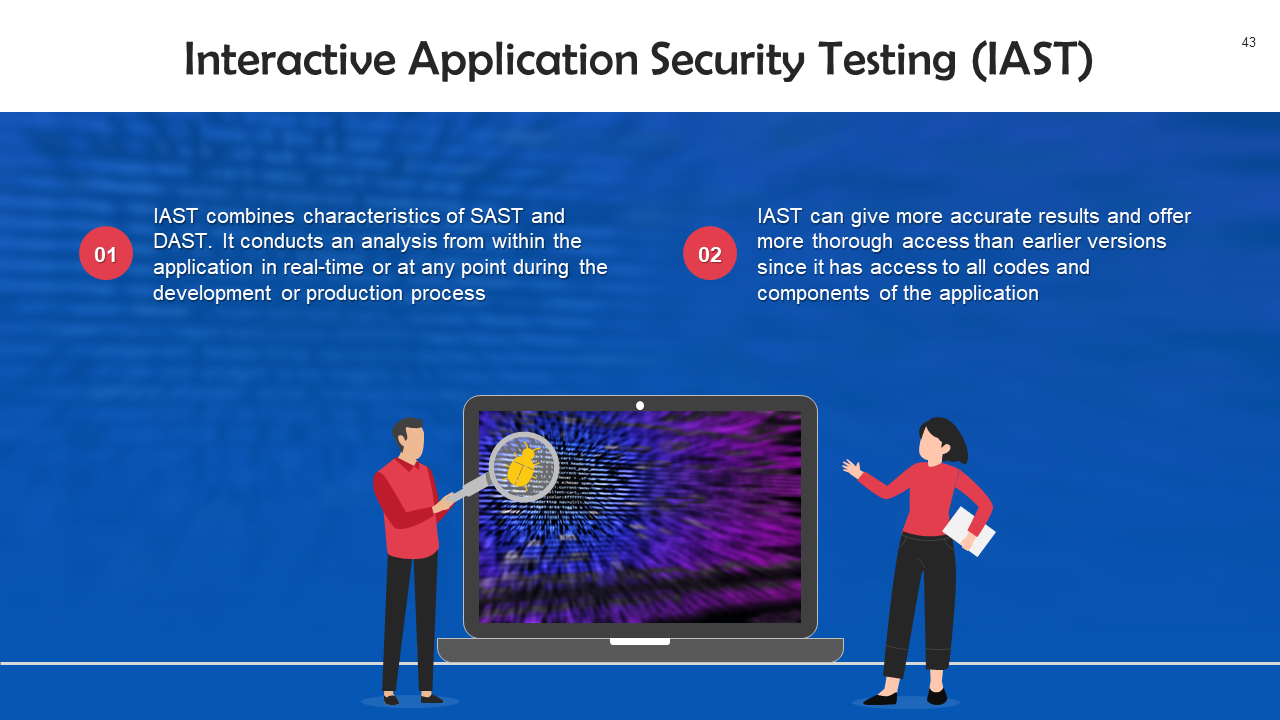
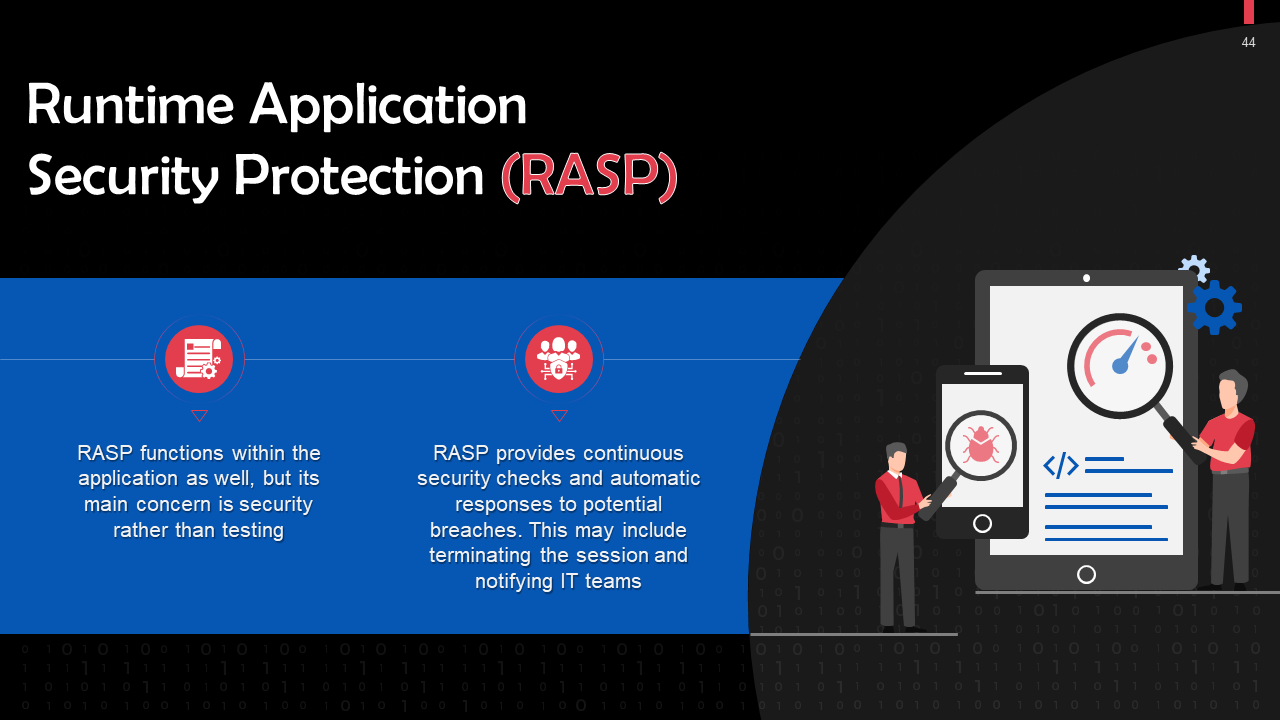
- Application Security
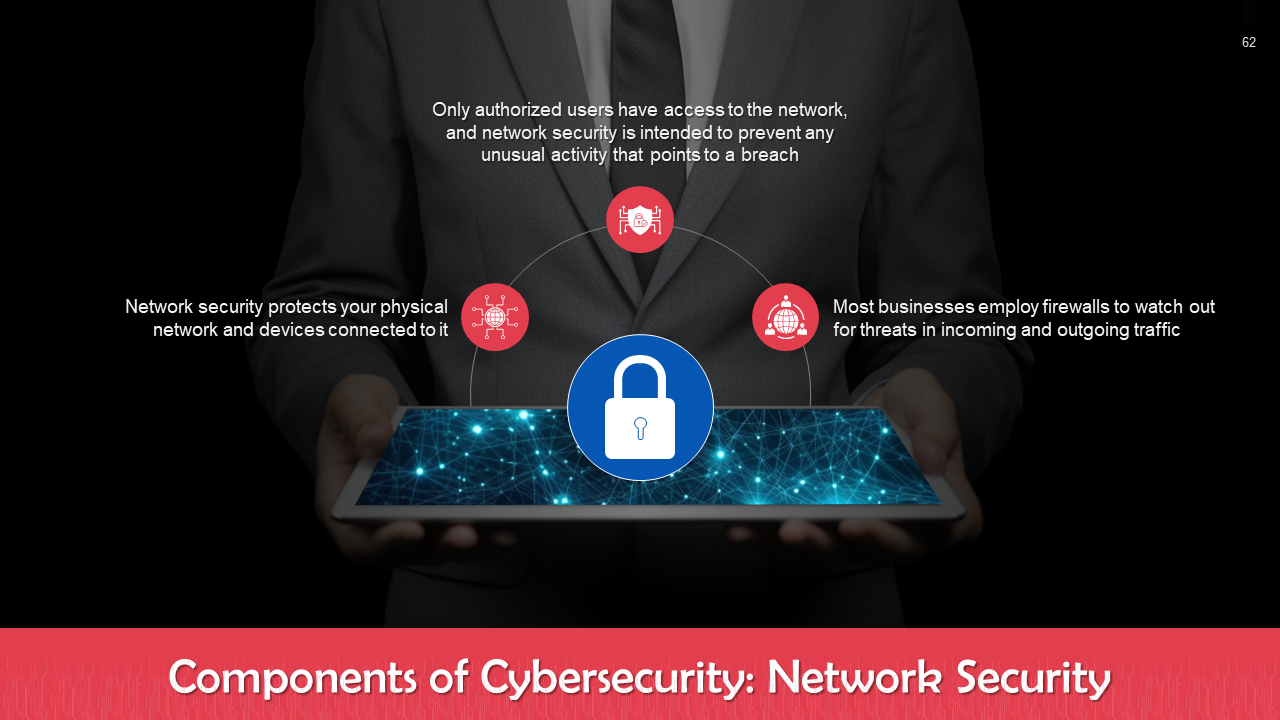
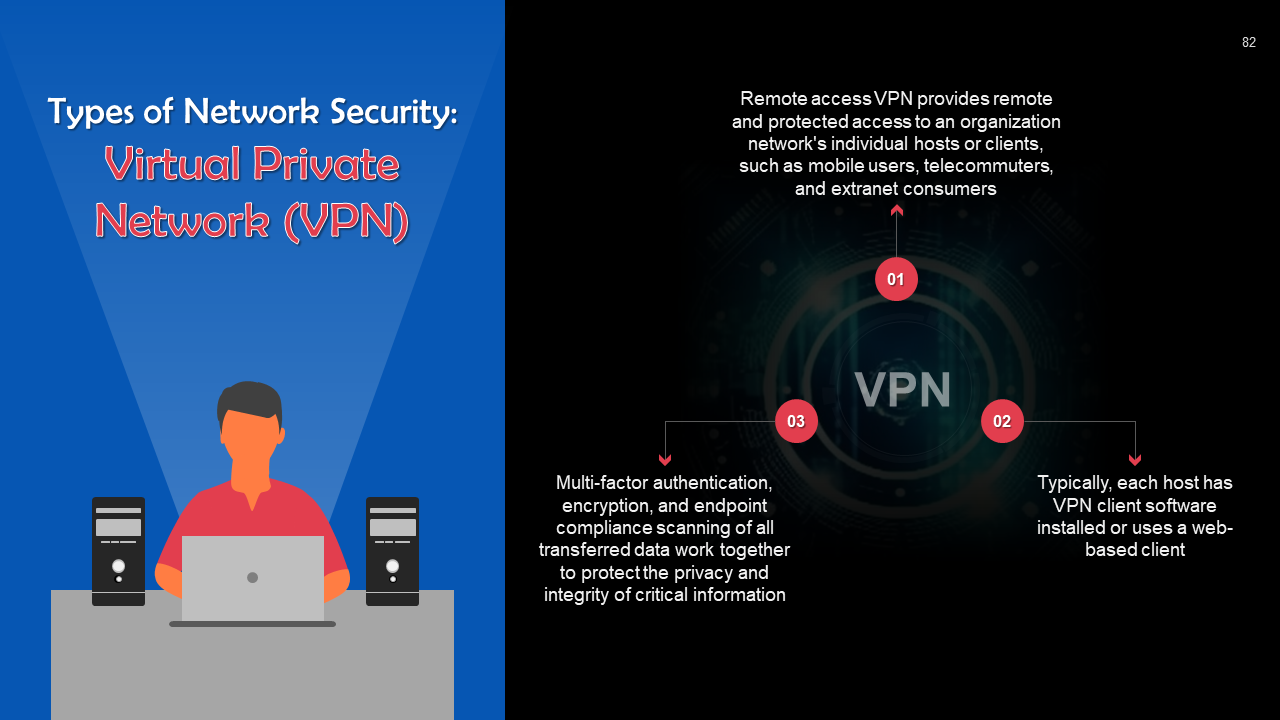
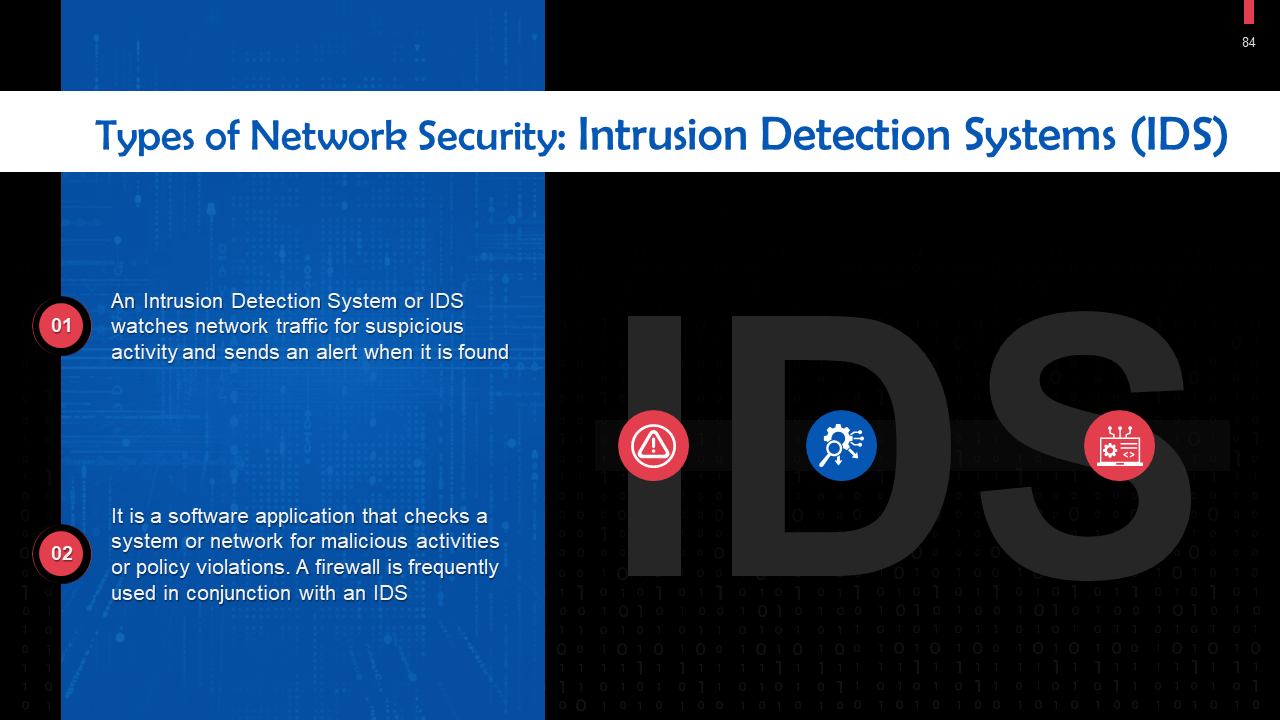
- Network Security
- End-User Security
- Operational Security
- Disaster Recovery Planning
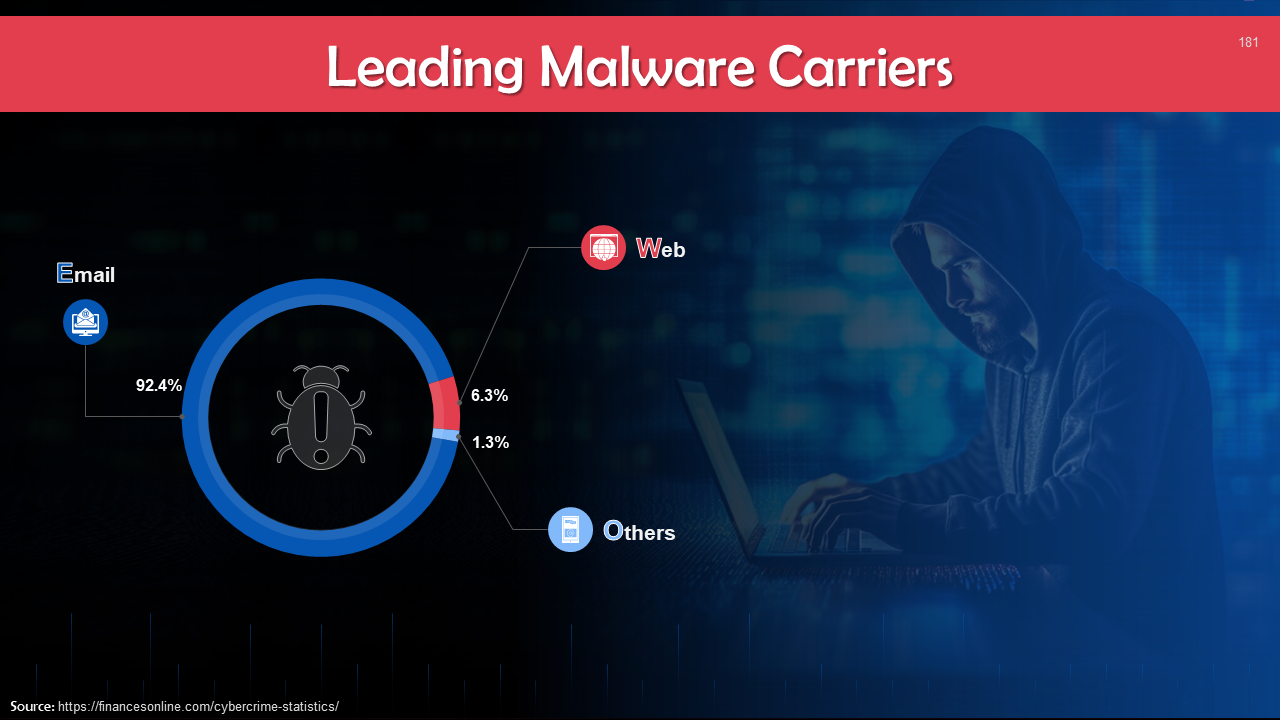
- Cybercrime Statistics
- Introduction to Cyber Attack
- Why do Cyber Attacks happen?
- Who is behind Cyber Attacks?
- What do Cyber Attackers target?
- Business Impact of Cyber Attacks
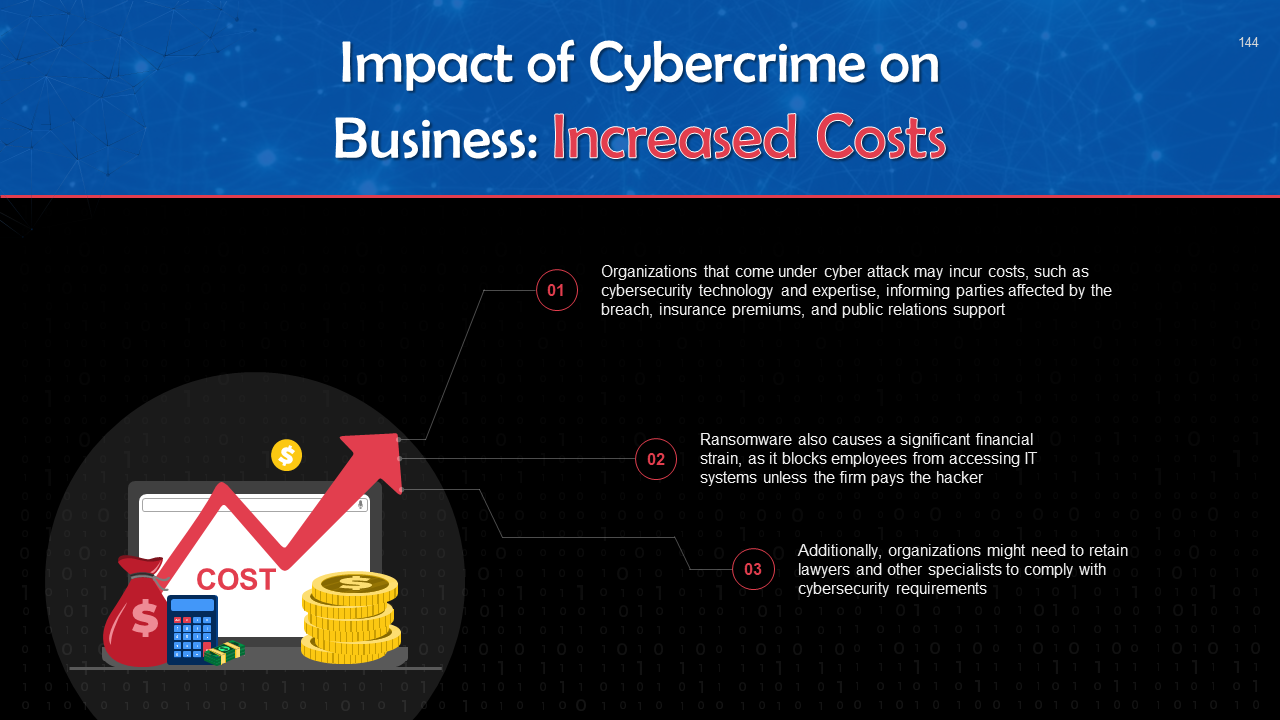
- Increased Costs
- Altered Business Practices
- Operational Disruption
- Lost Revenue
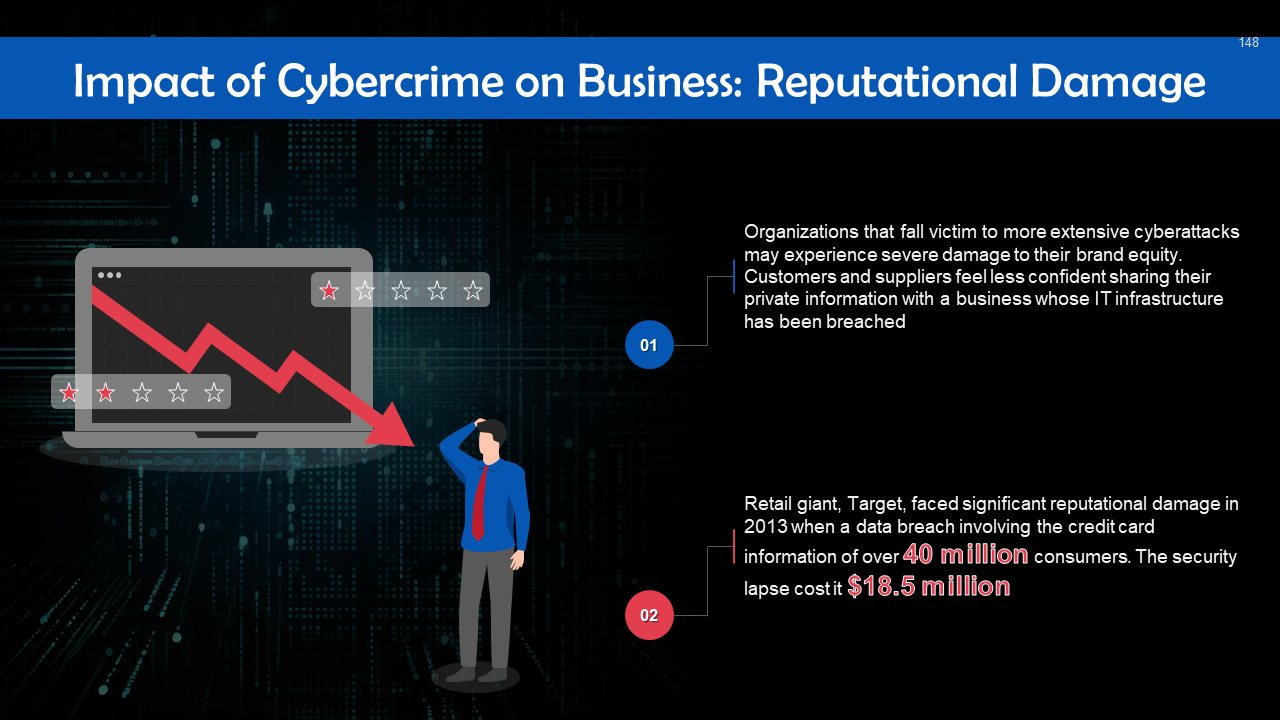
- Reputational Damage
- Stolen Intellectual Property
- Case Studies
- What is Cybersecurity Awareness Training?
- Why is it important?
- Key Takeaways
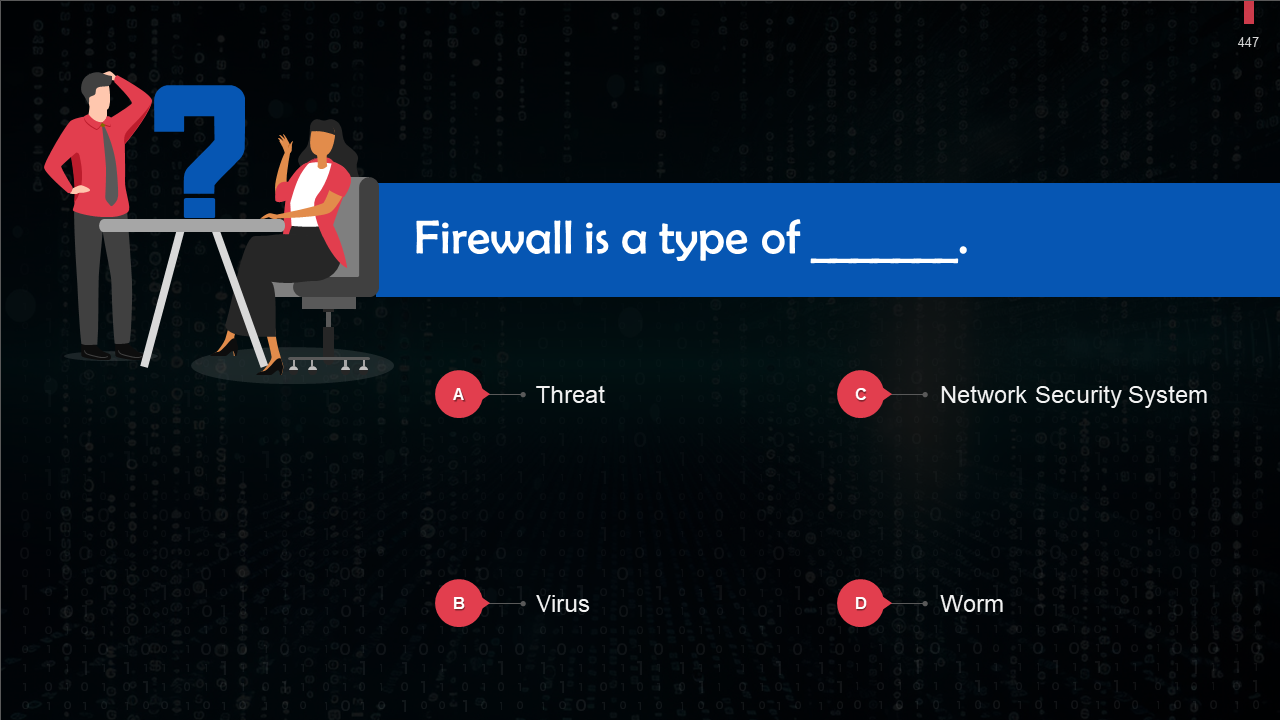
- Let’s Test What We Have Learnt
- Types of Attacks or Threats
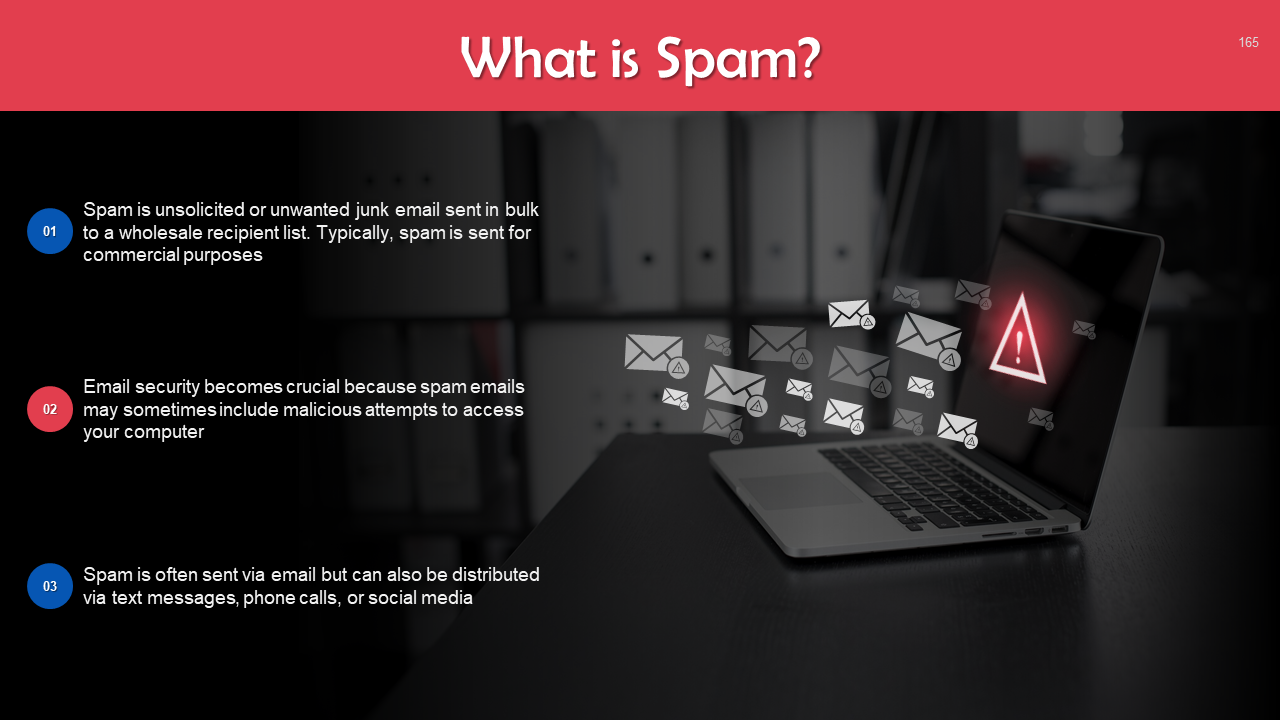
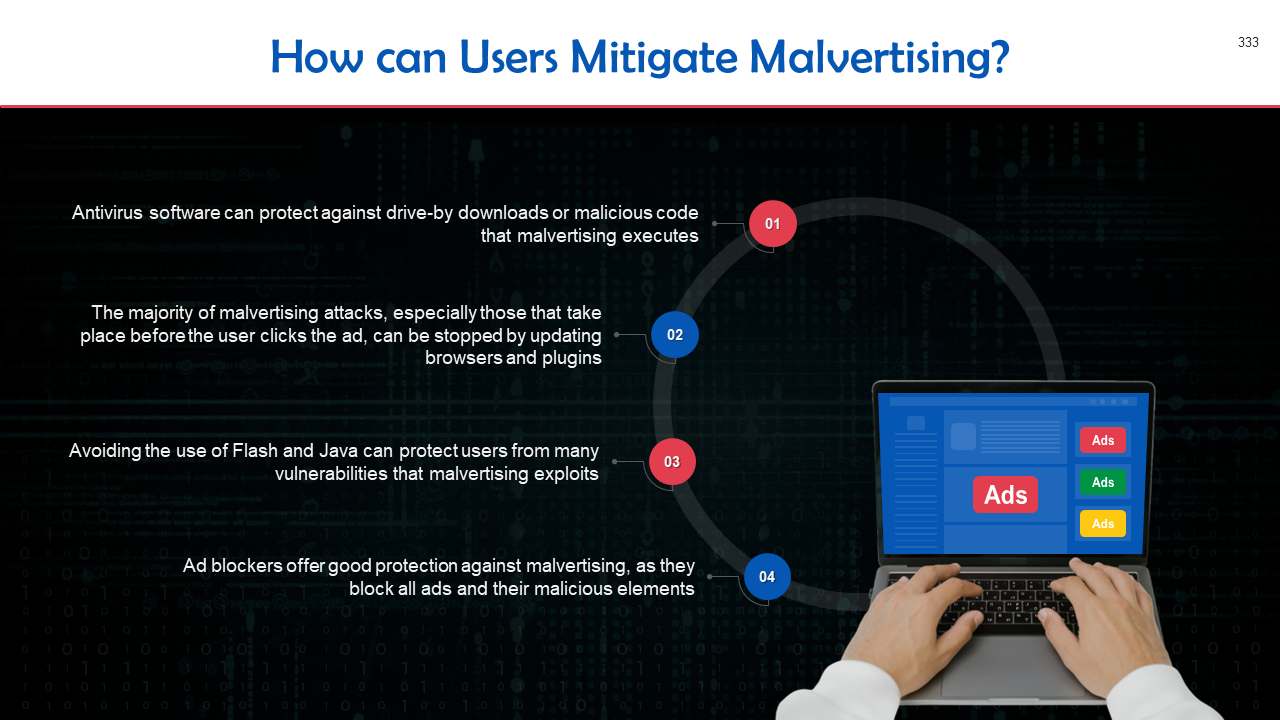
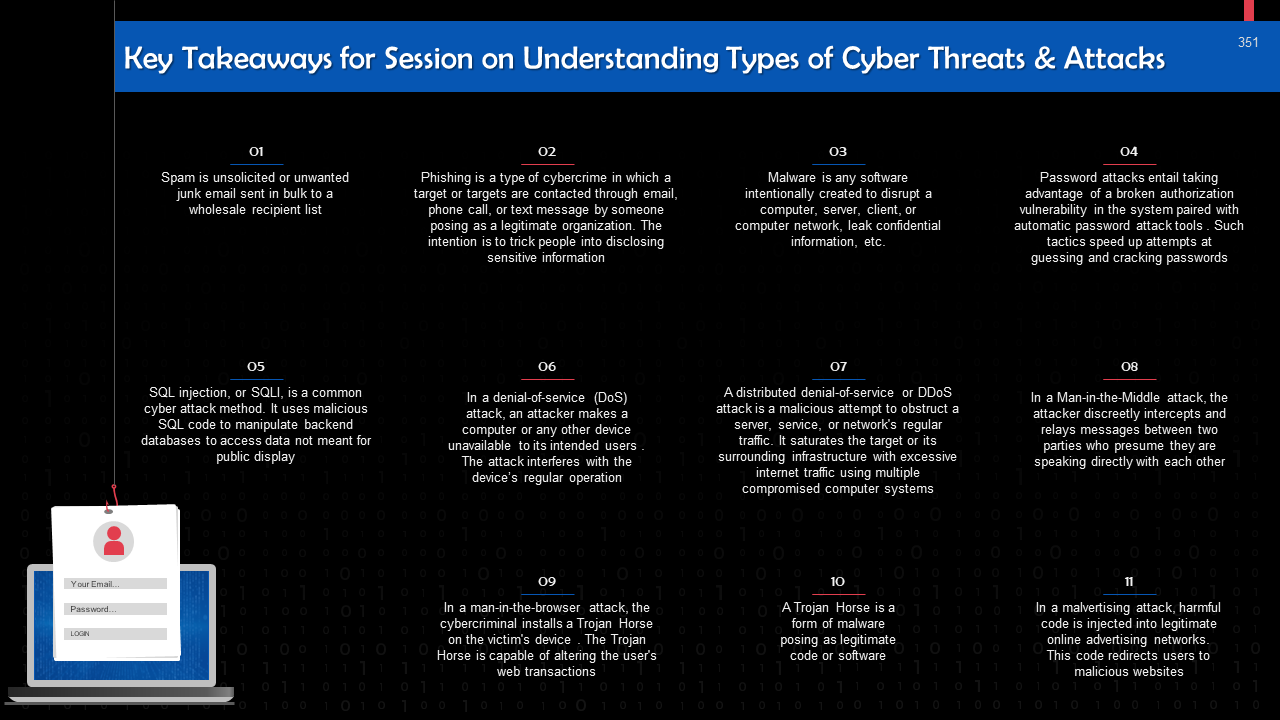
- Phishing Attacks & Spam
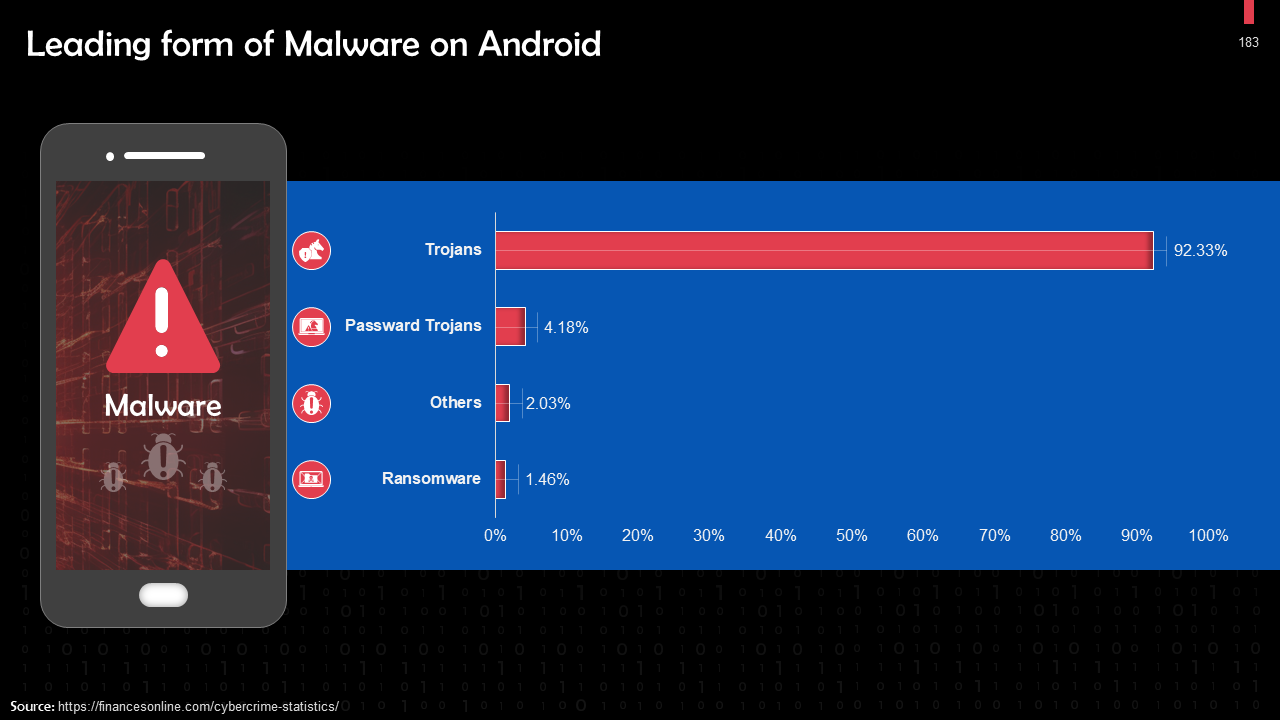
- Malware
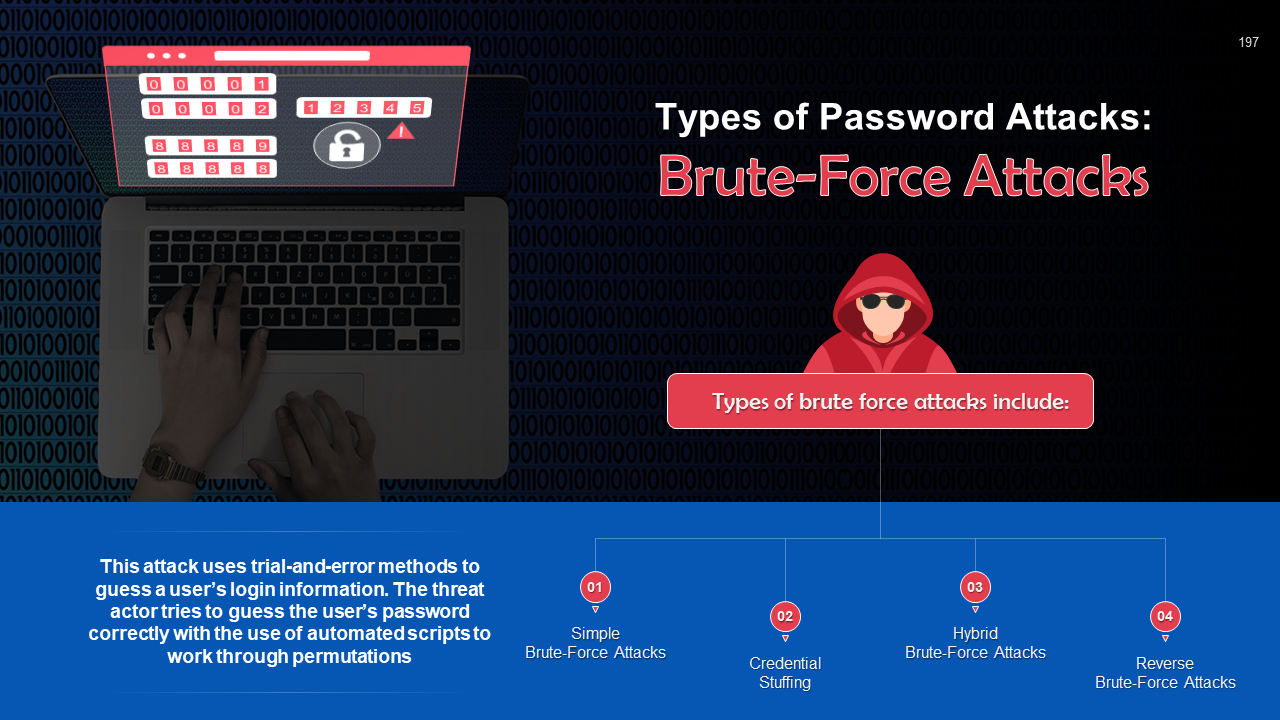
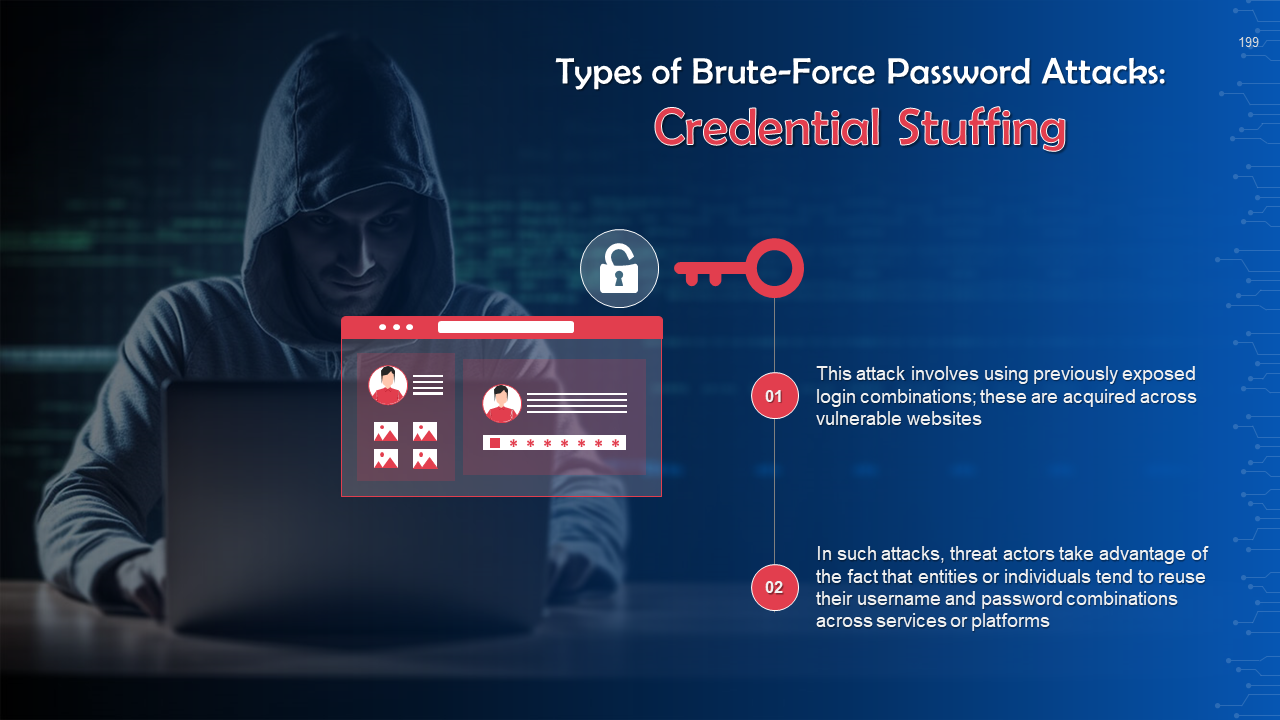
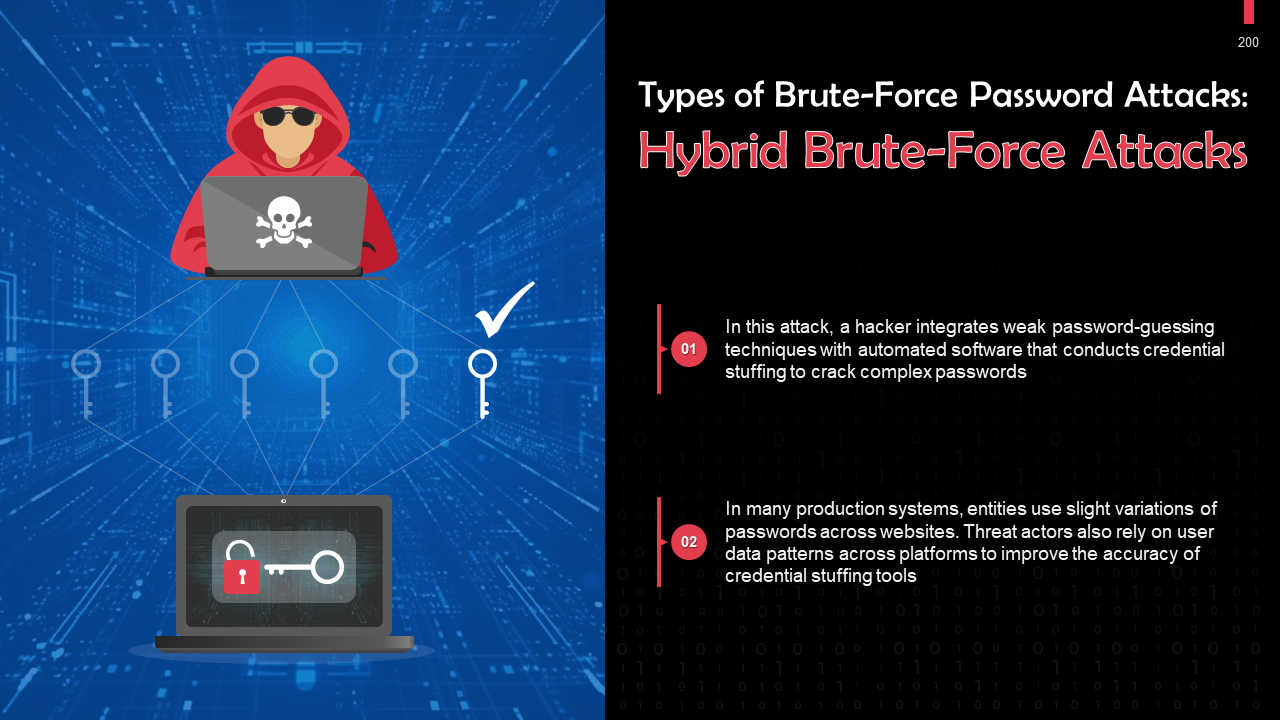
- Password Attack
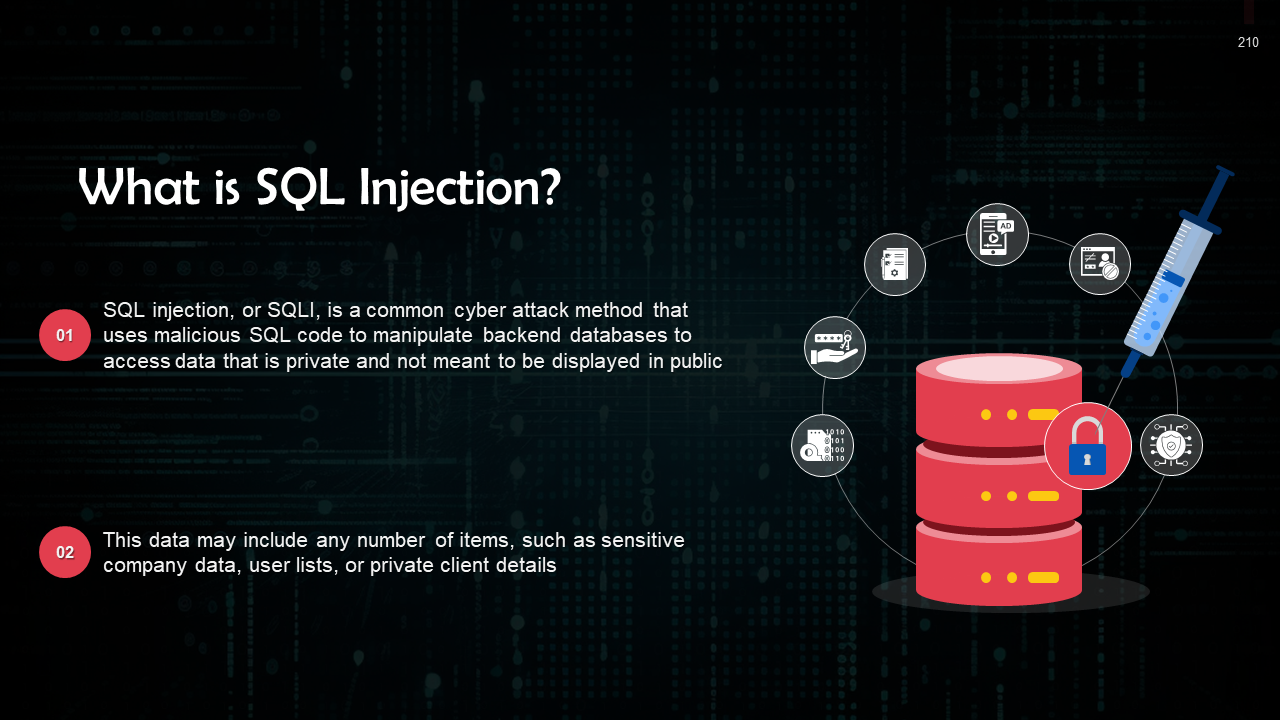
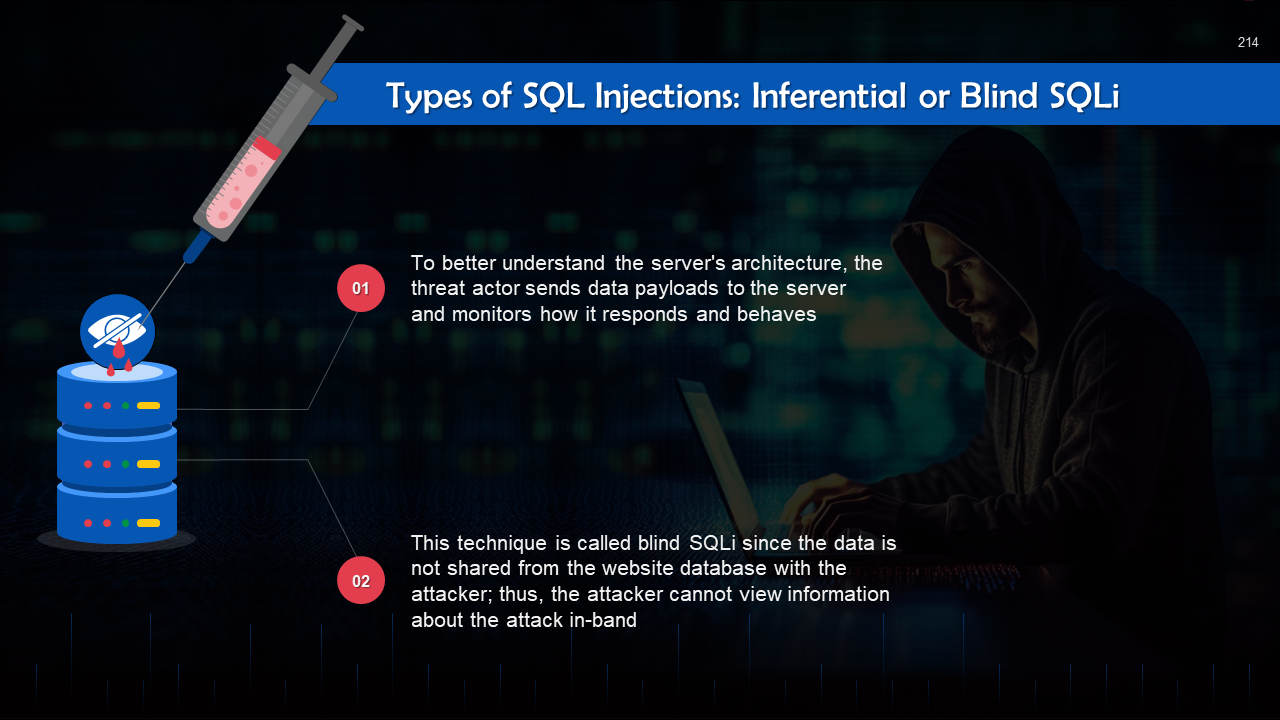
- SQL Injection Attack
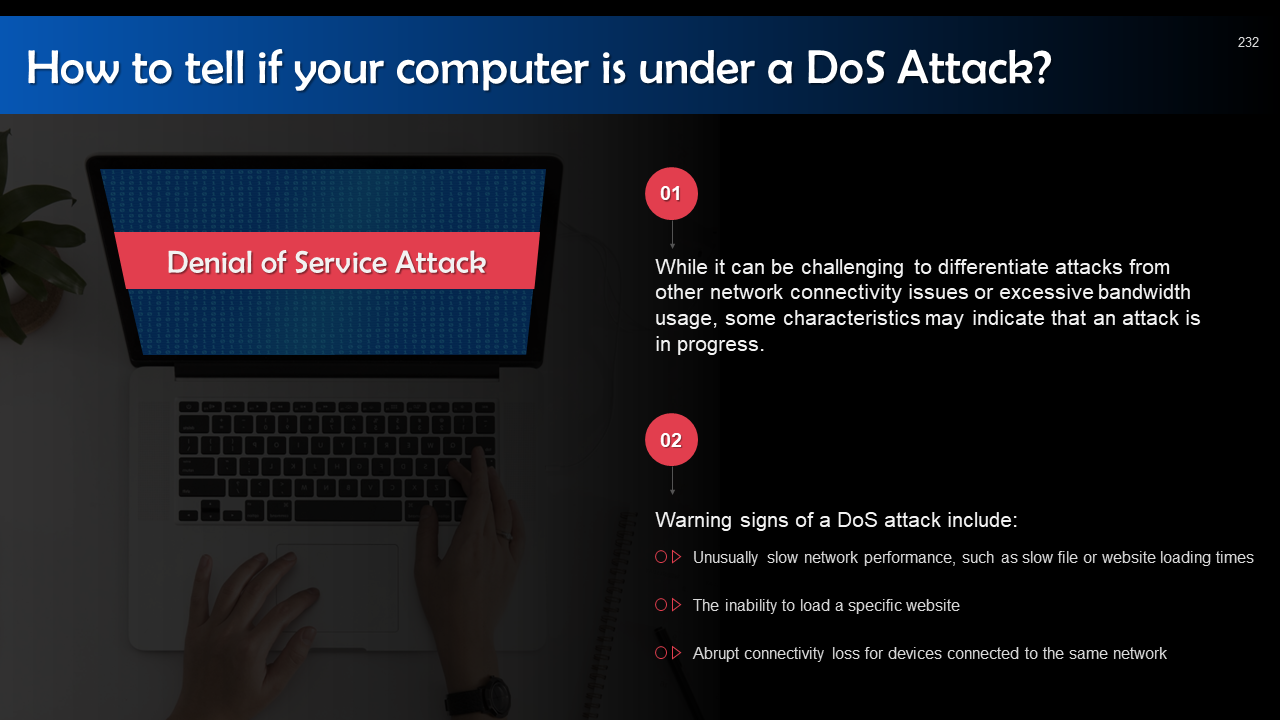
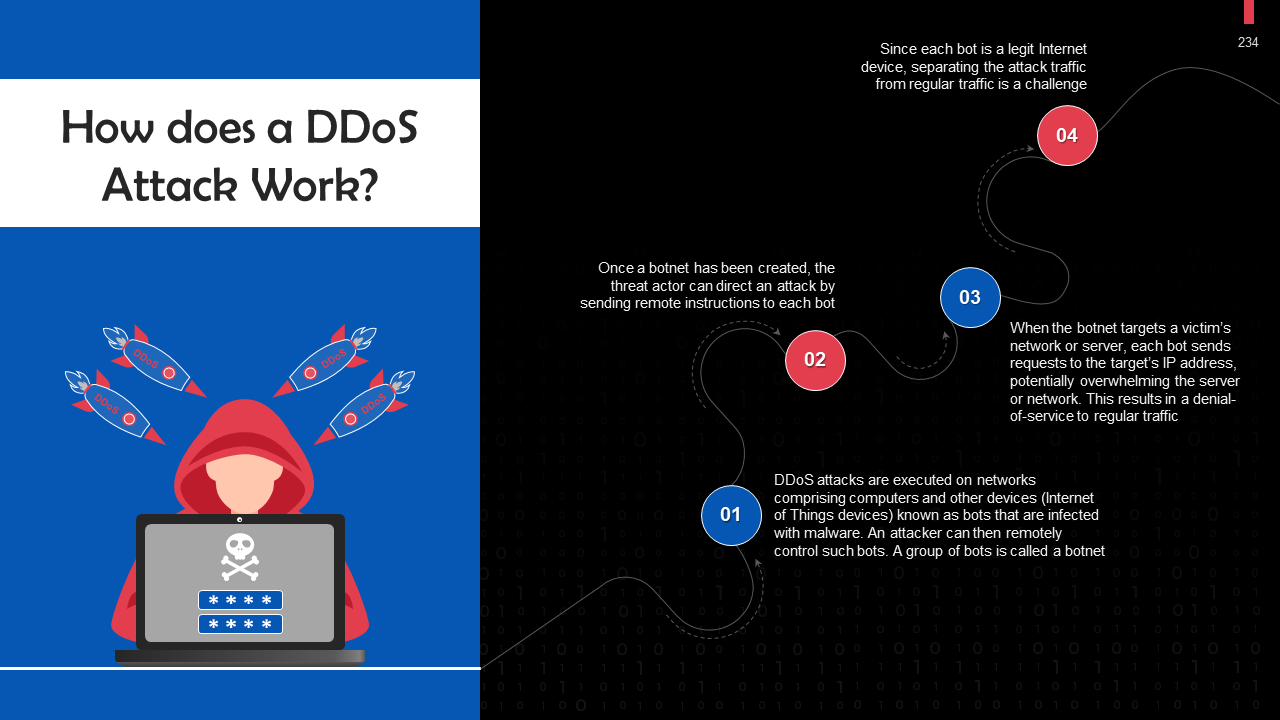
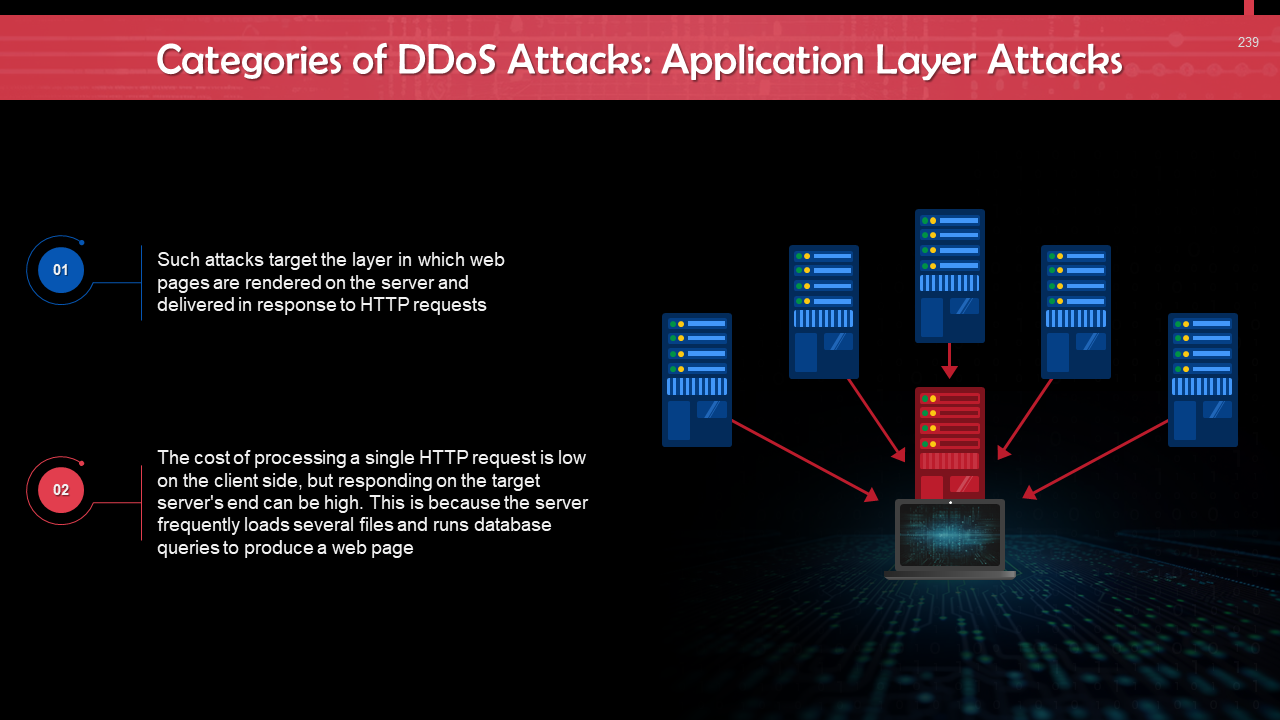
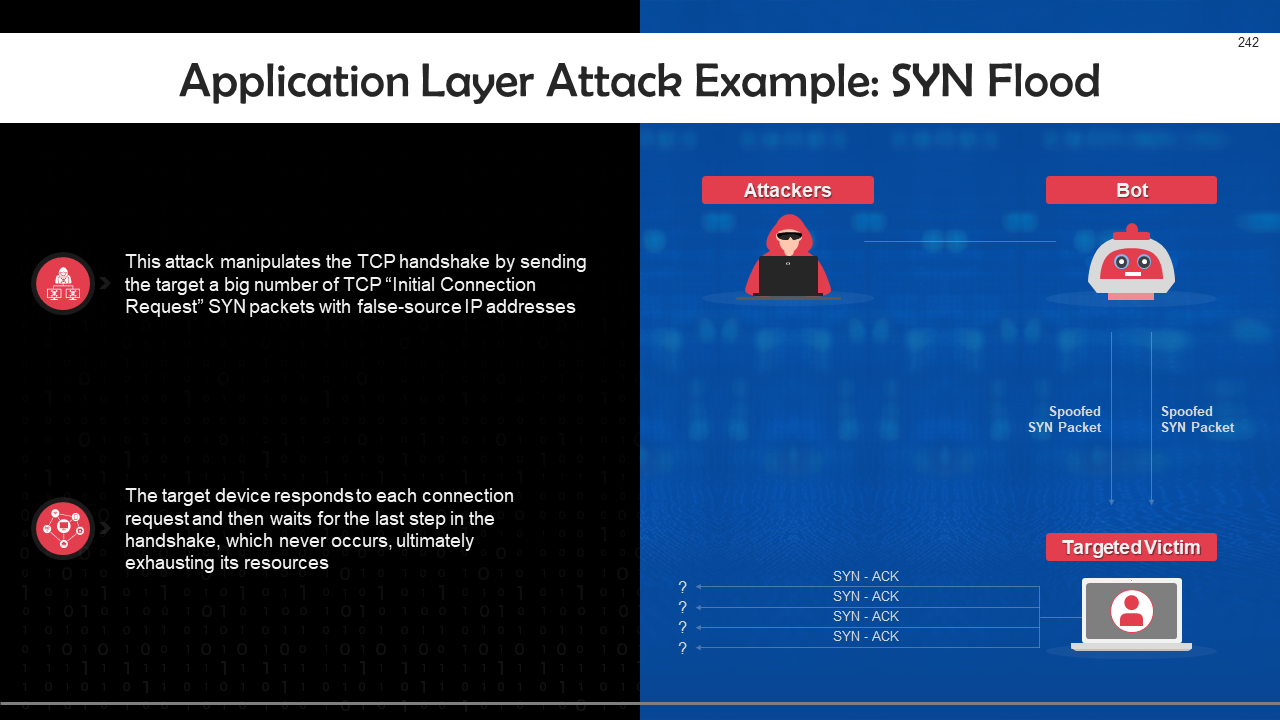
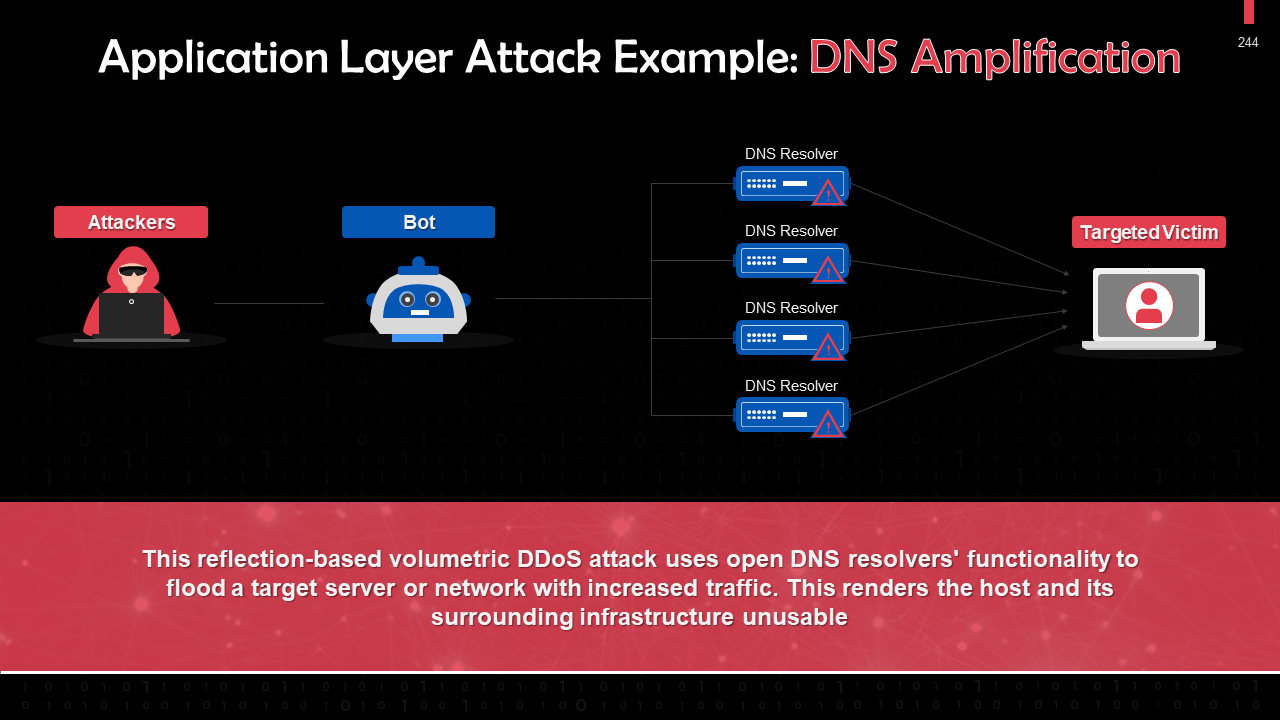
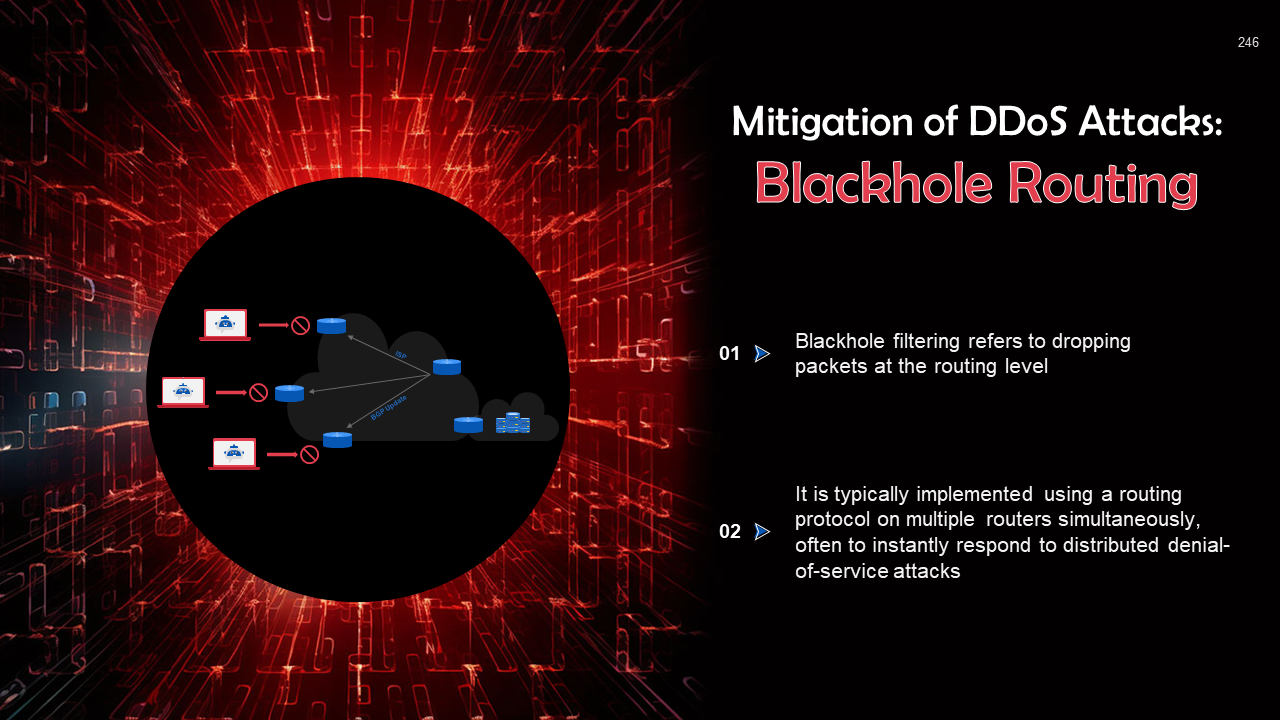
- DoS & DDoS Attack
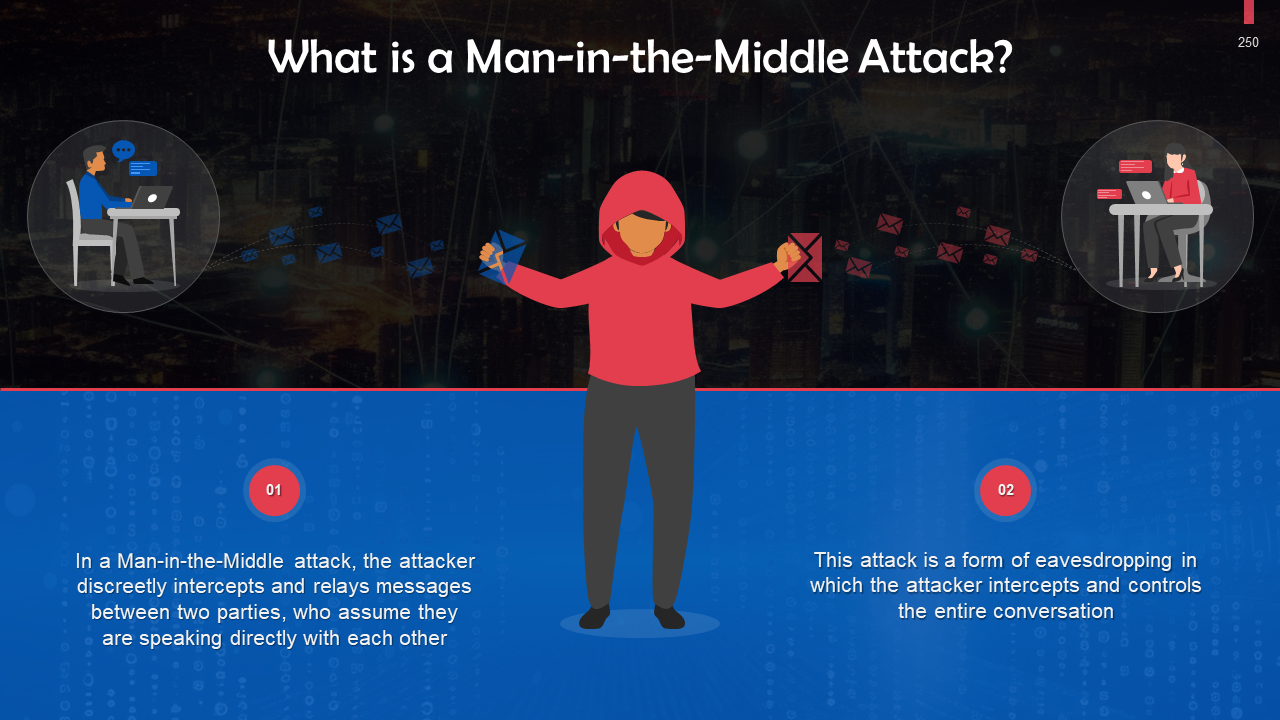
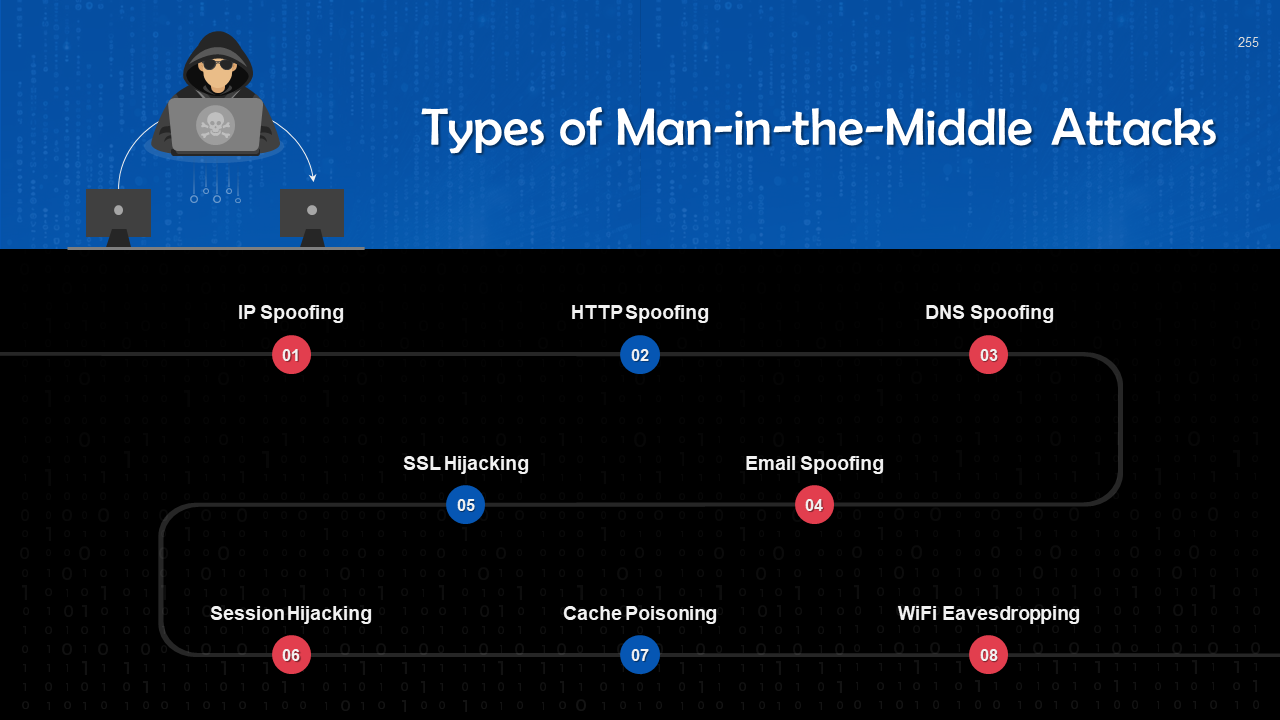
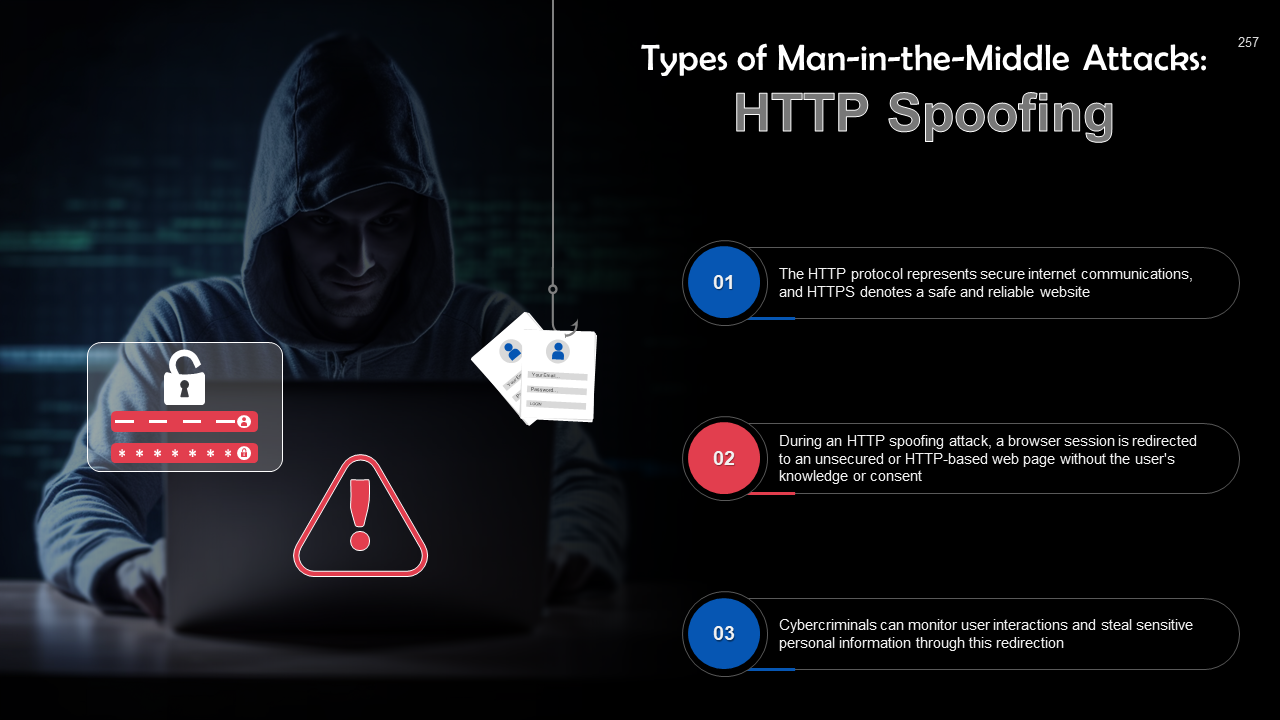
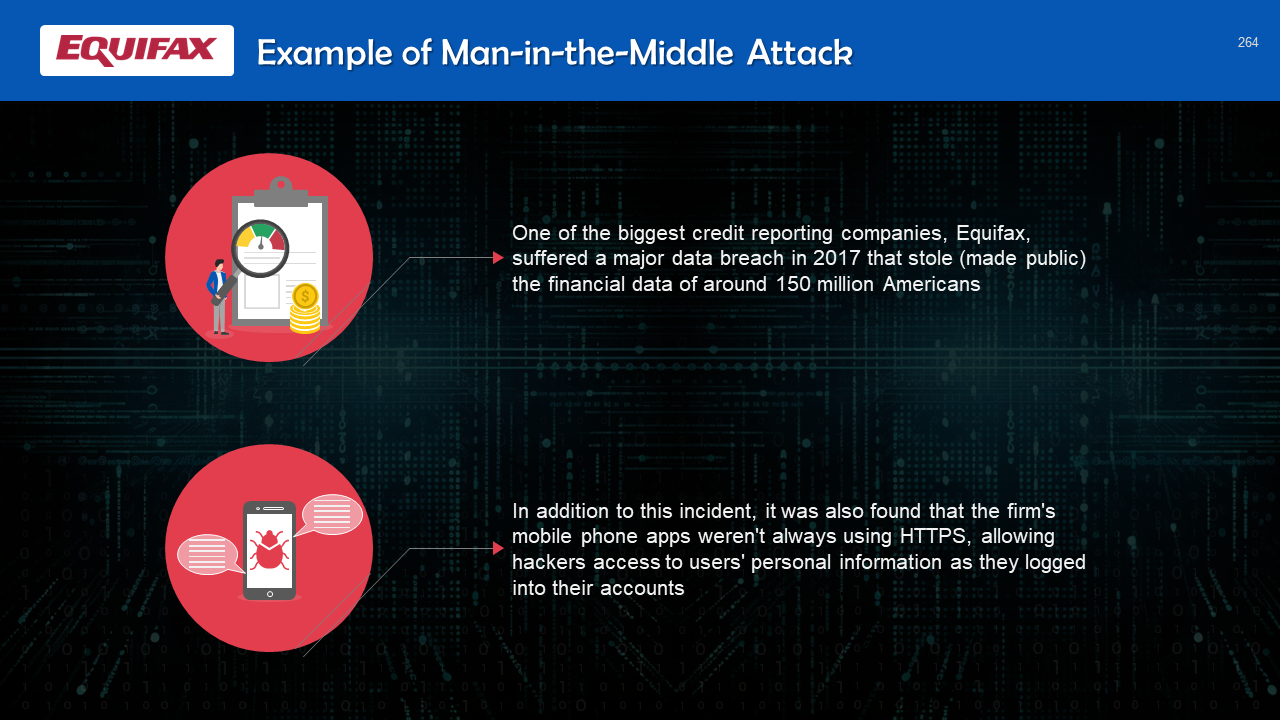
- Man-in-the-Middle Attack
- Man-in-the-Browser Attack
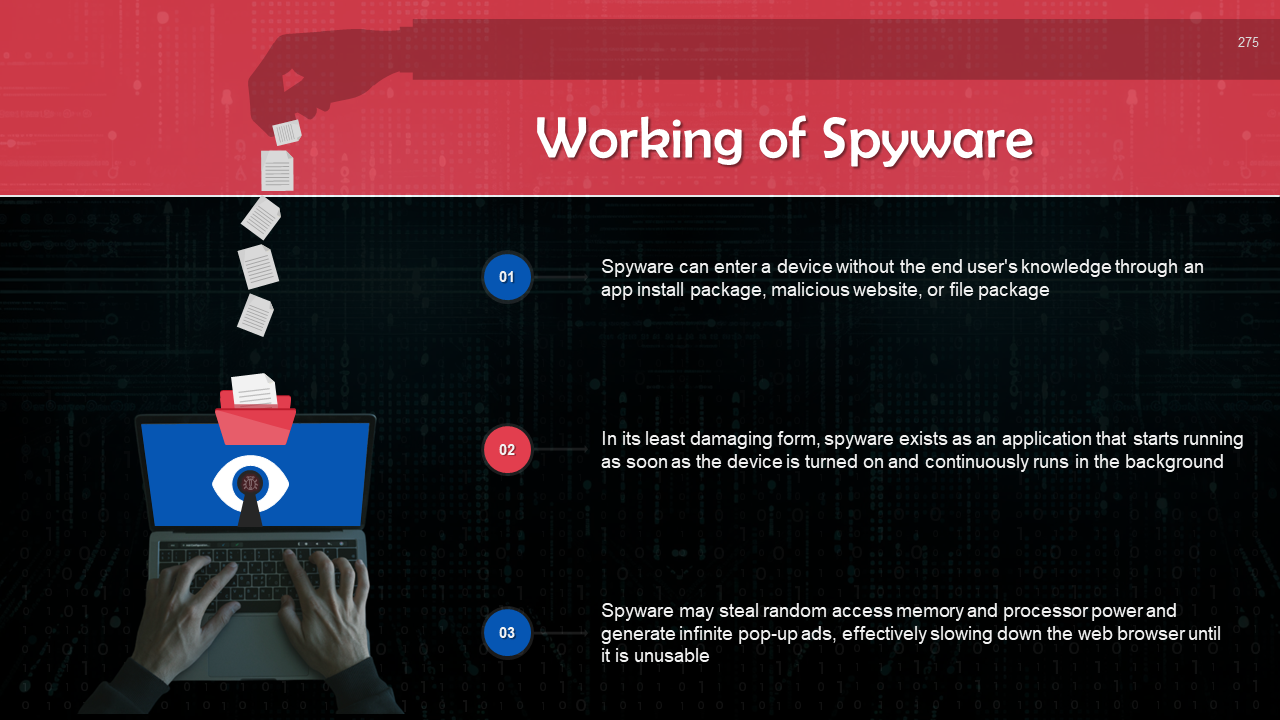
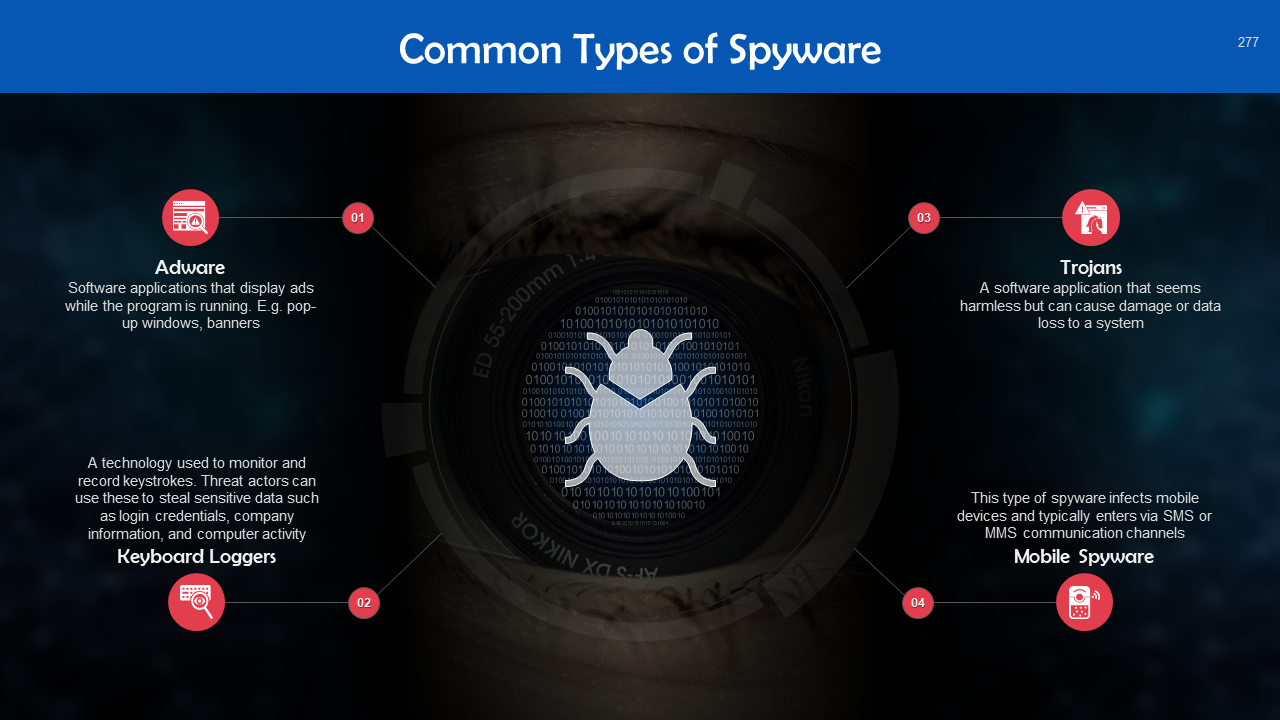
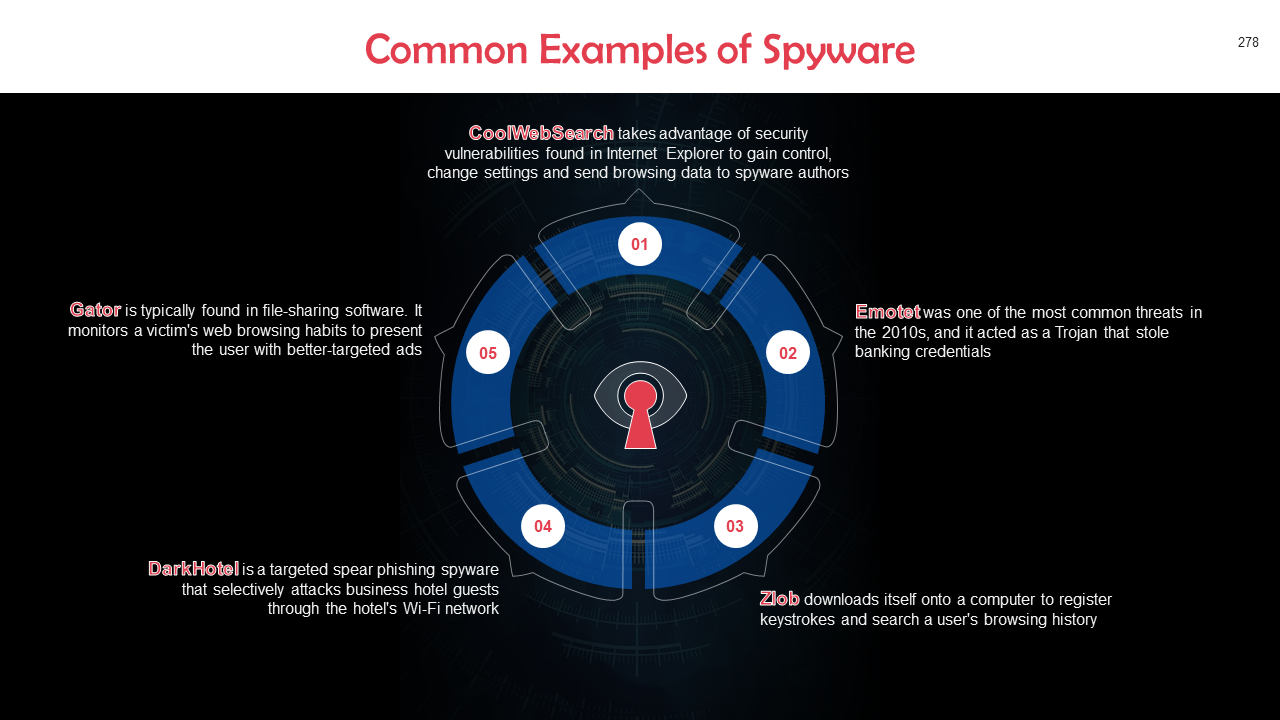
- Spyware
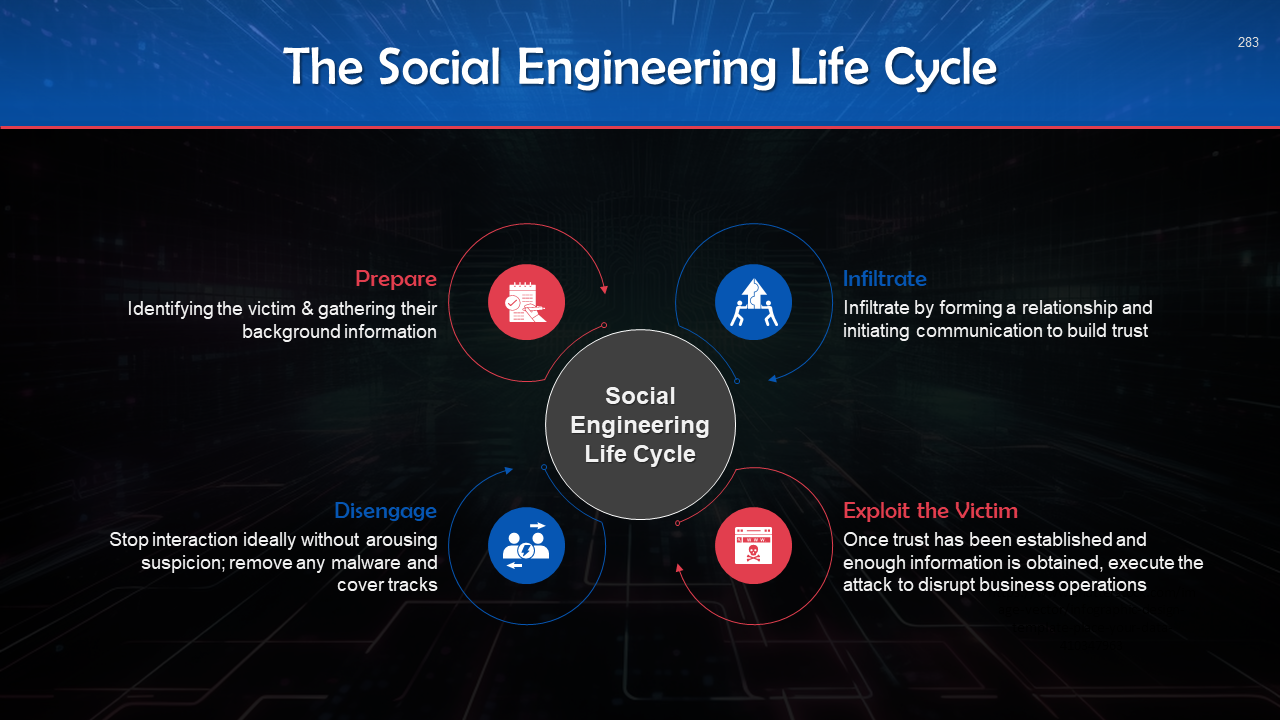
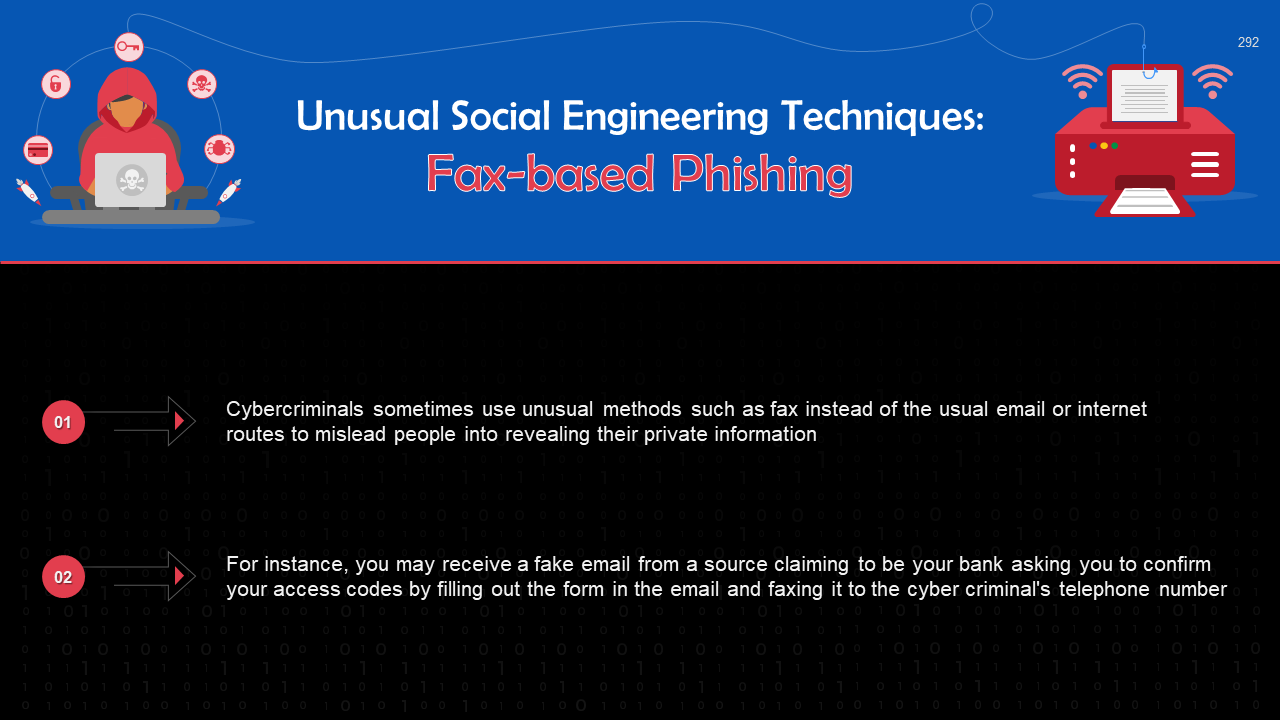
- Social Engineering
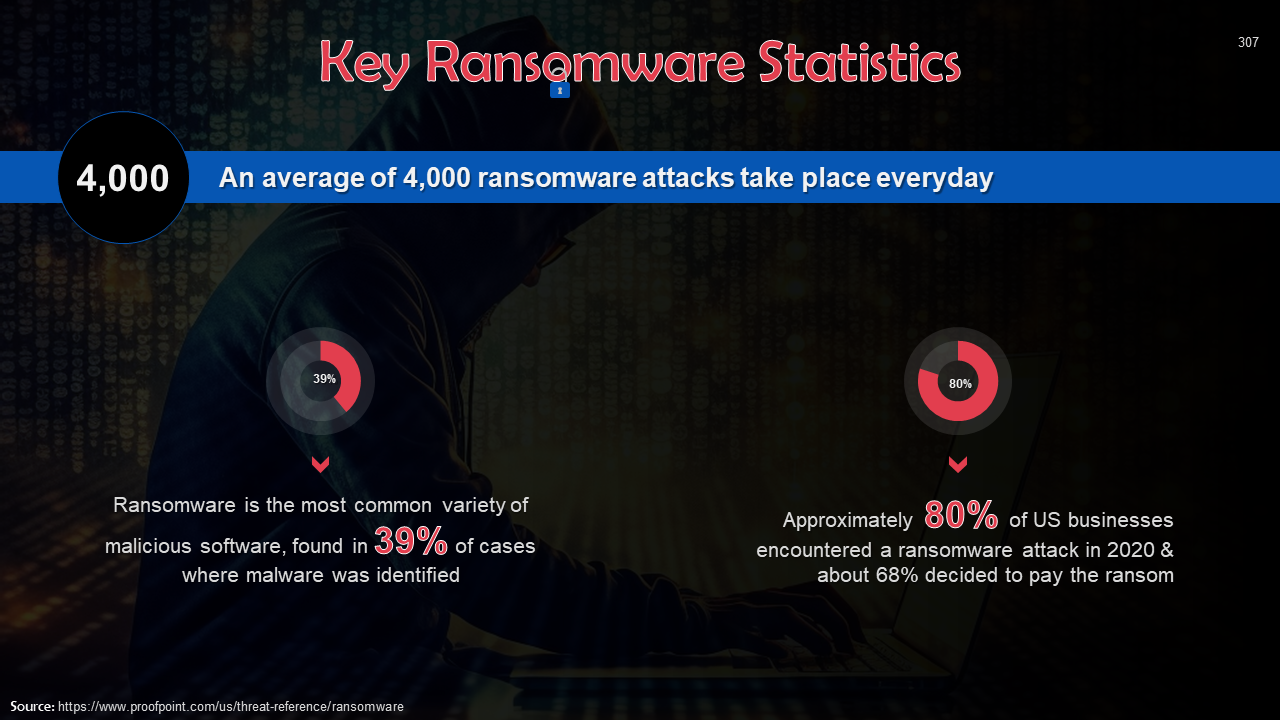
- Ransomware Attacks
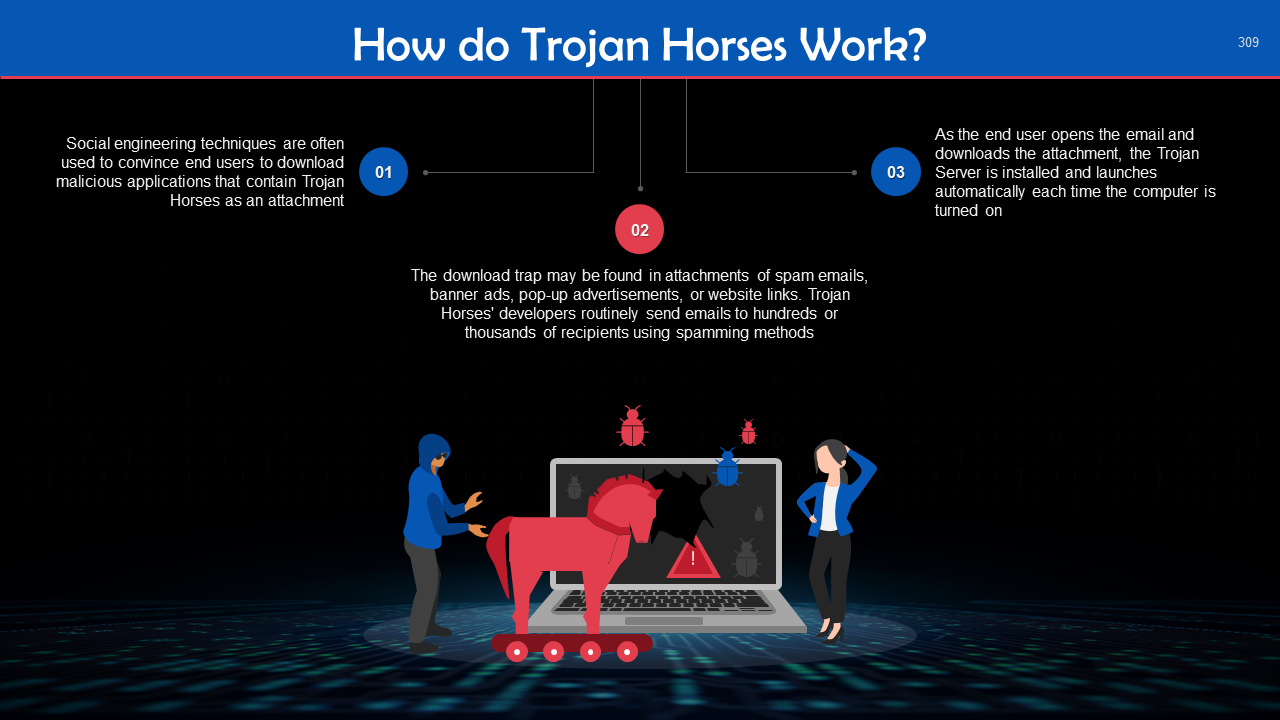
- Trojan Horses
- Cryptojacking
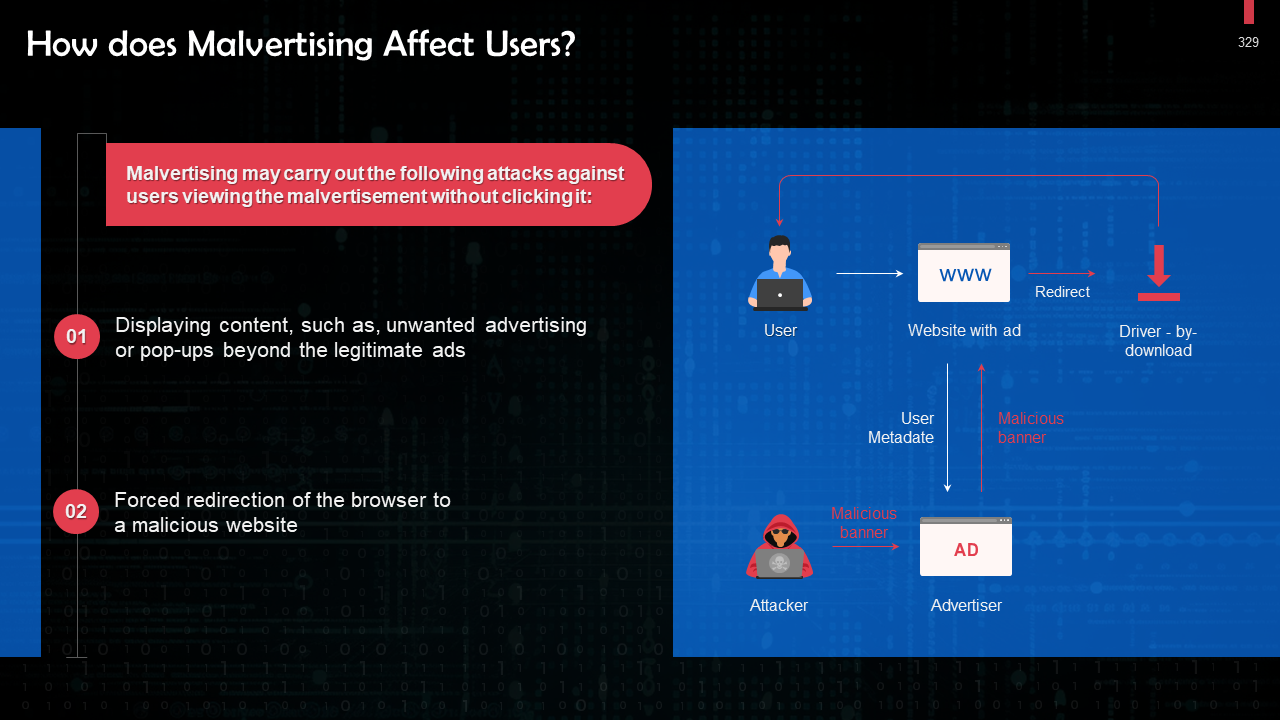
- Malvertising Attacks
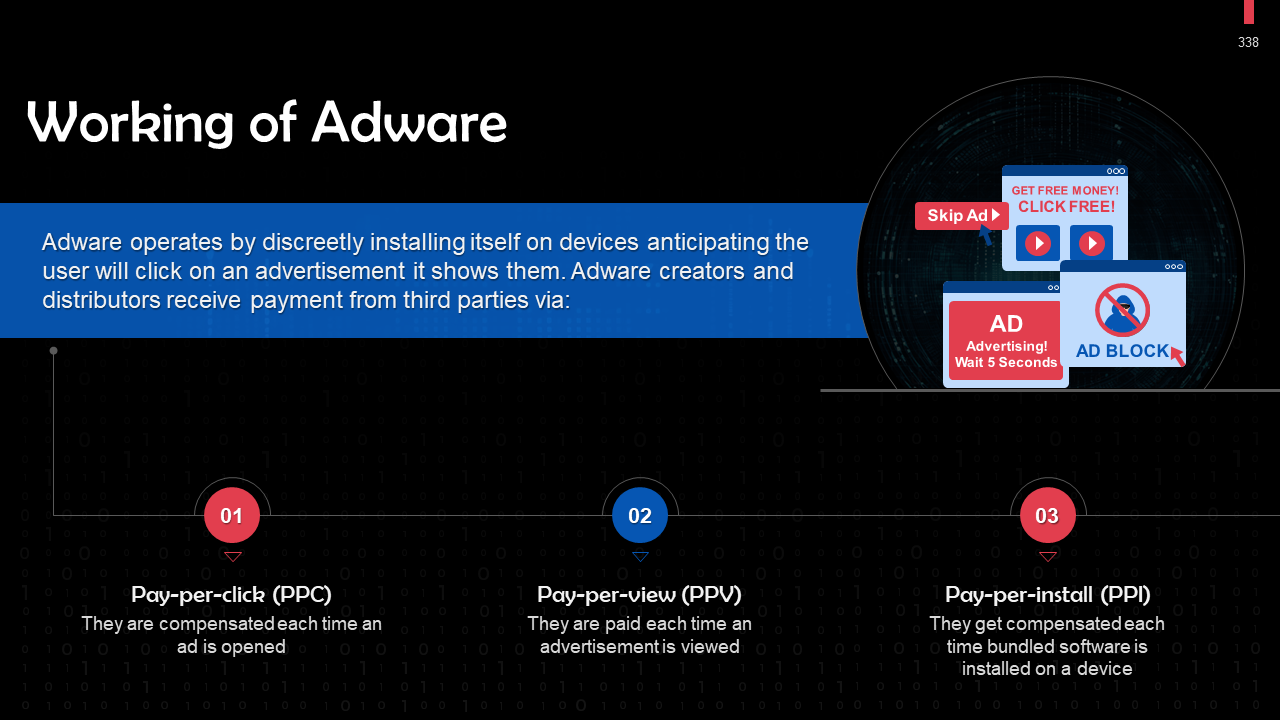
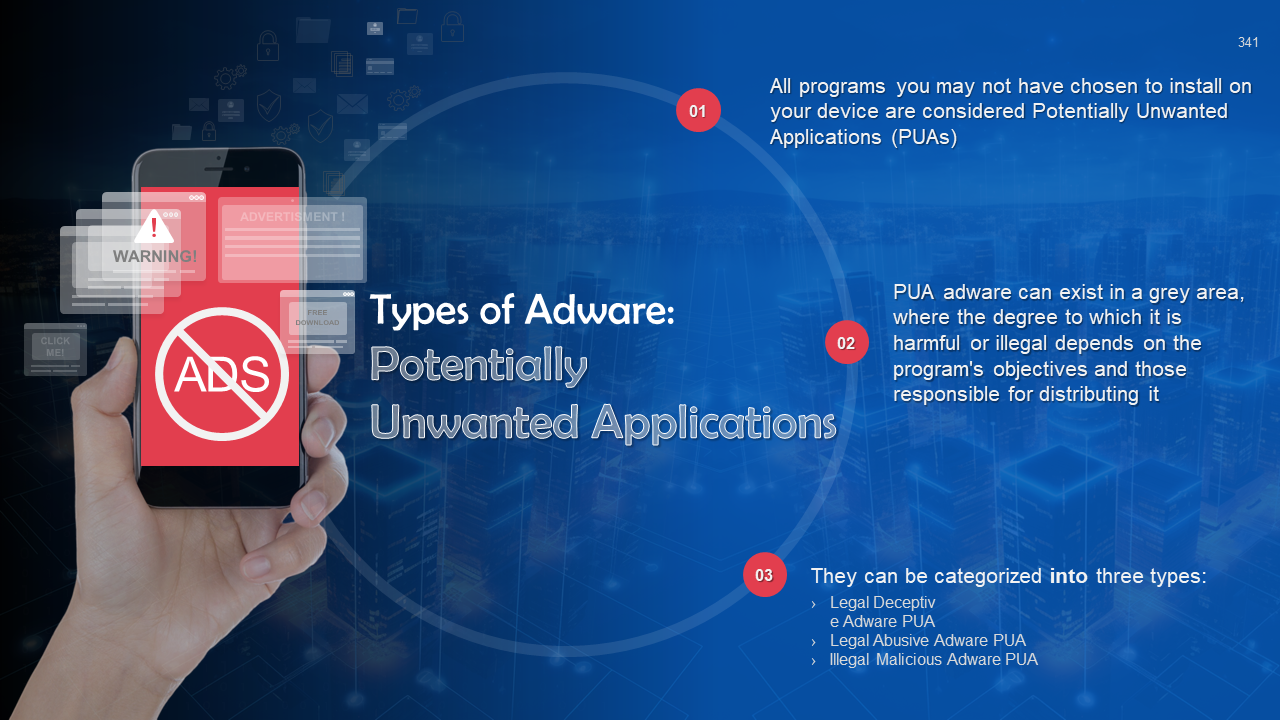
- Adware
- Key Takeaways
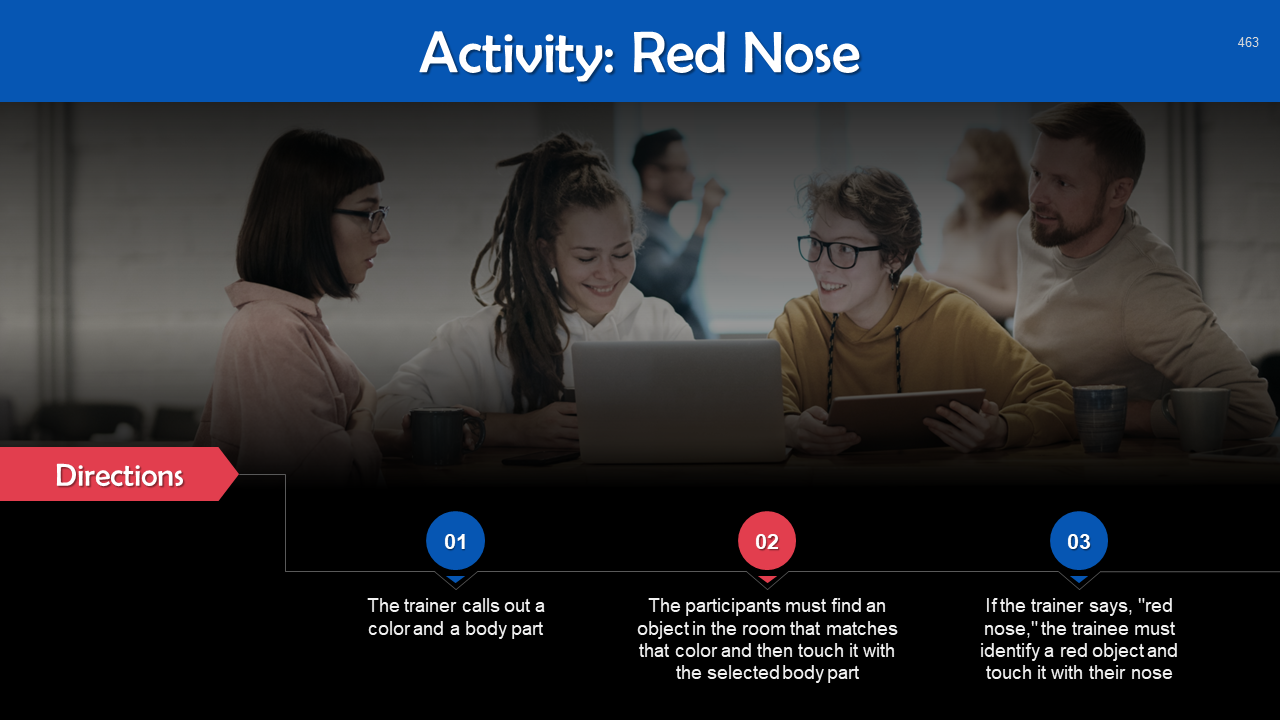
- Let’s Discuss
- Let’s Test What We Have Learnt
- How Can Employees Help in Improving Cyber Security
- Remote Work Security Awareness
- Secure Mobile Devices
- Safe Web Browsing
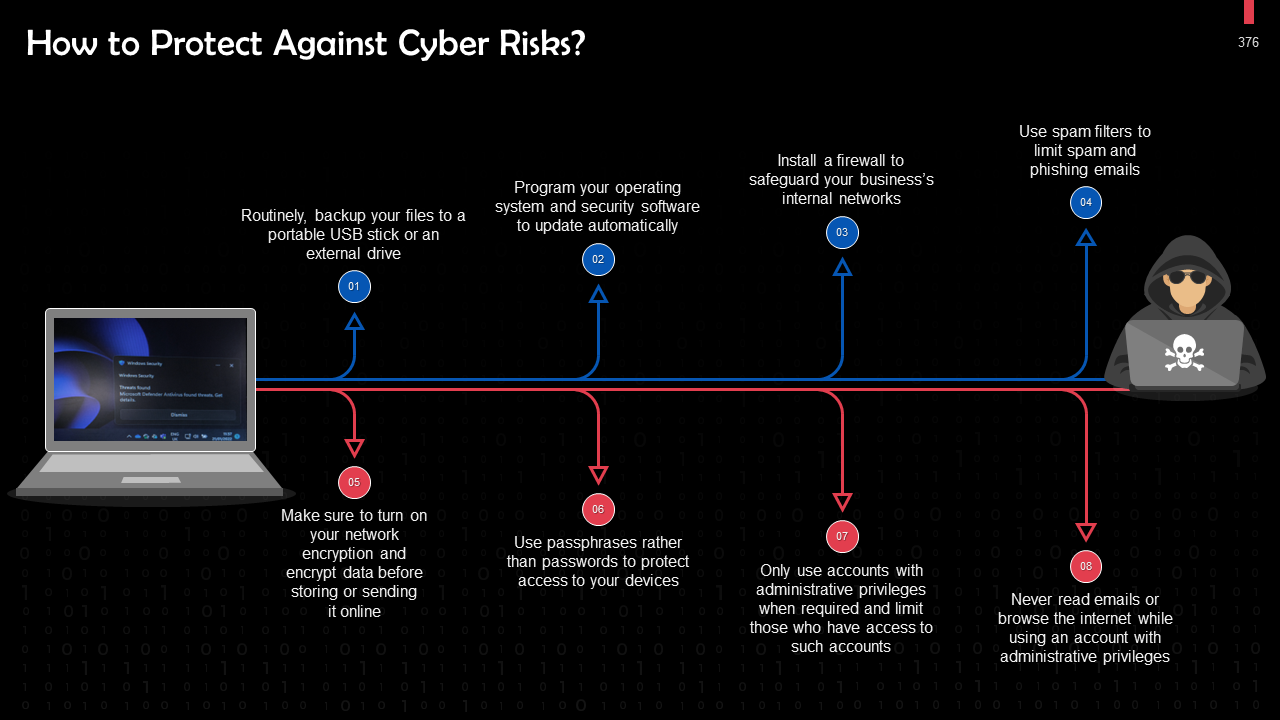
- How to protect your Organization from Cyber Attacks?
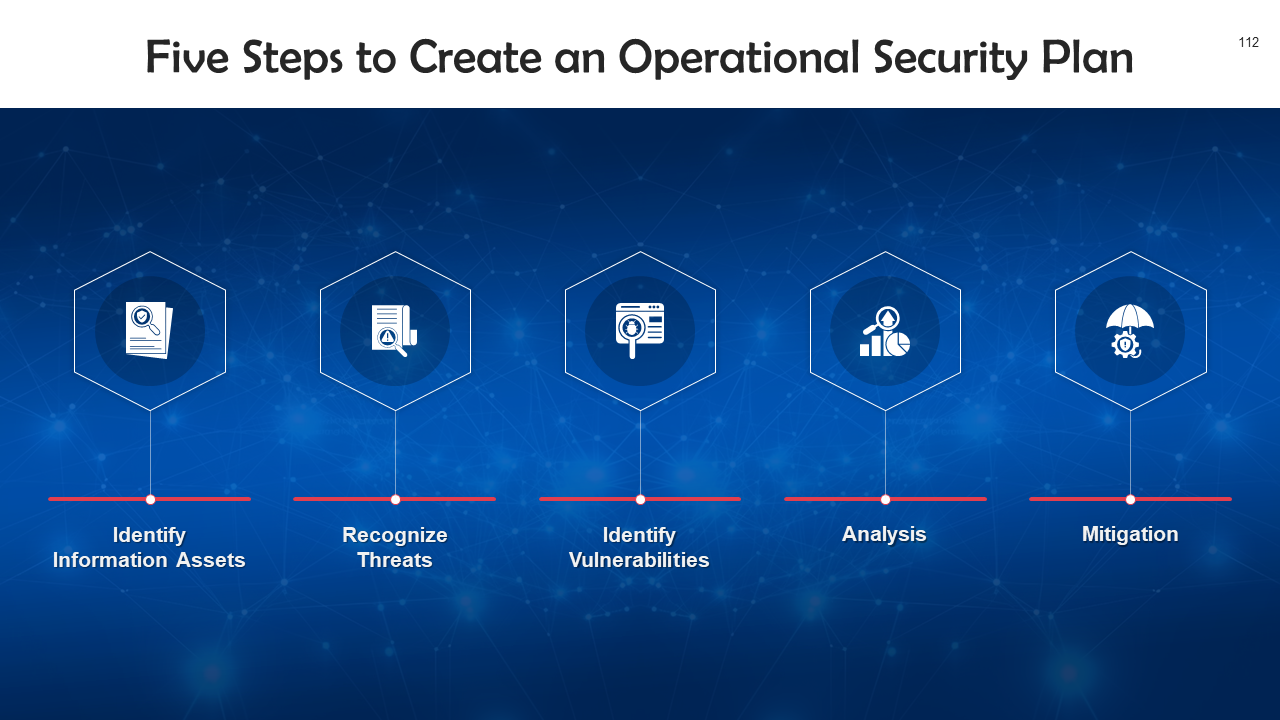
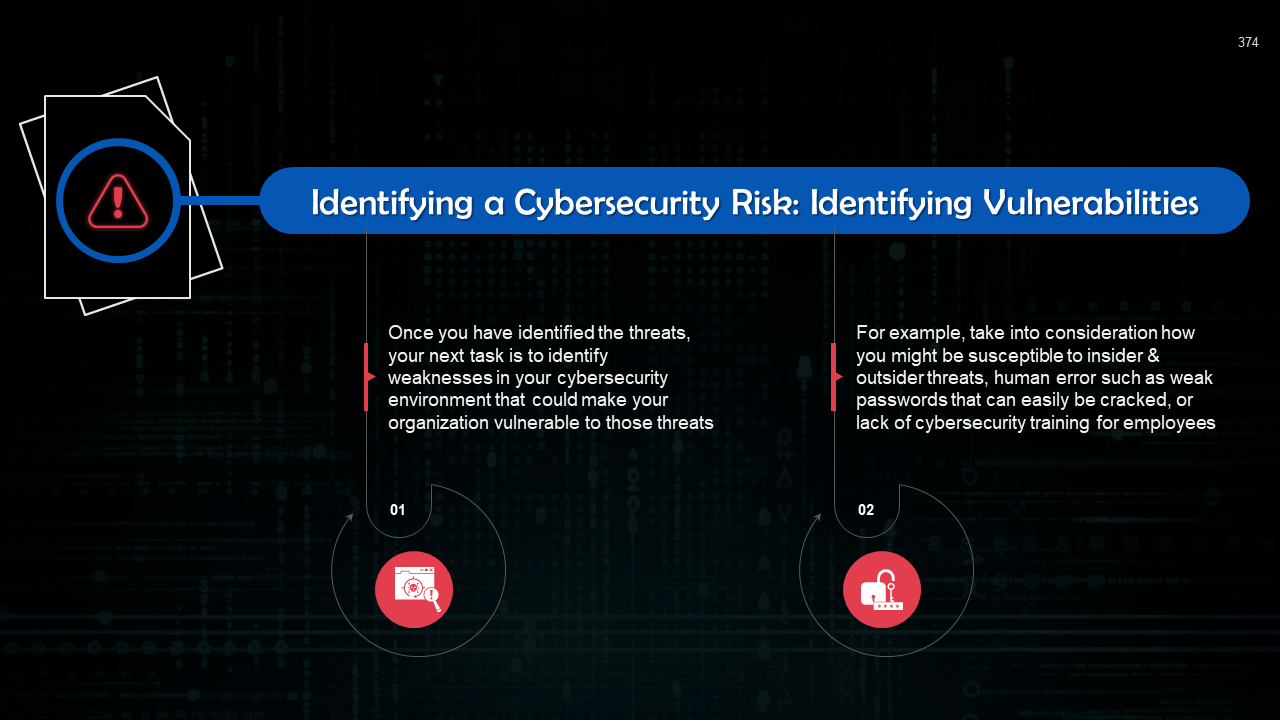
- Identifying Risks
- Protecting against Risks
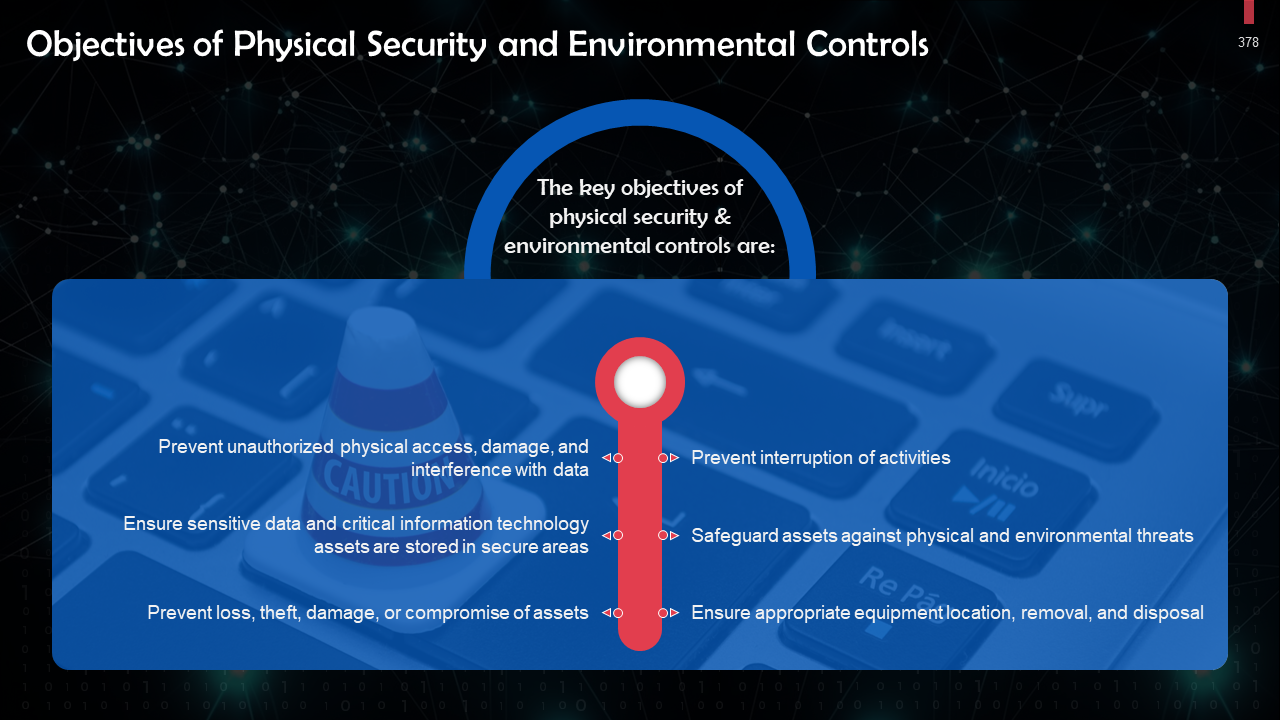
- Physical Security & Environmental Controls
- Data Privacy Management
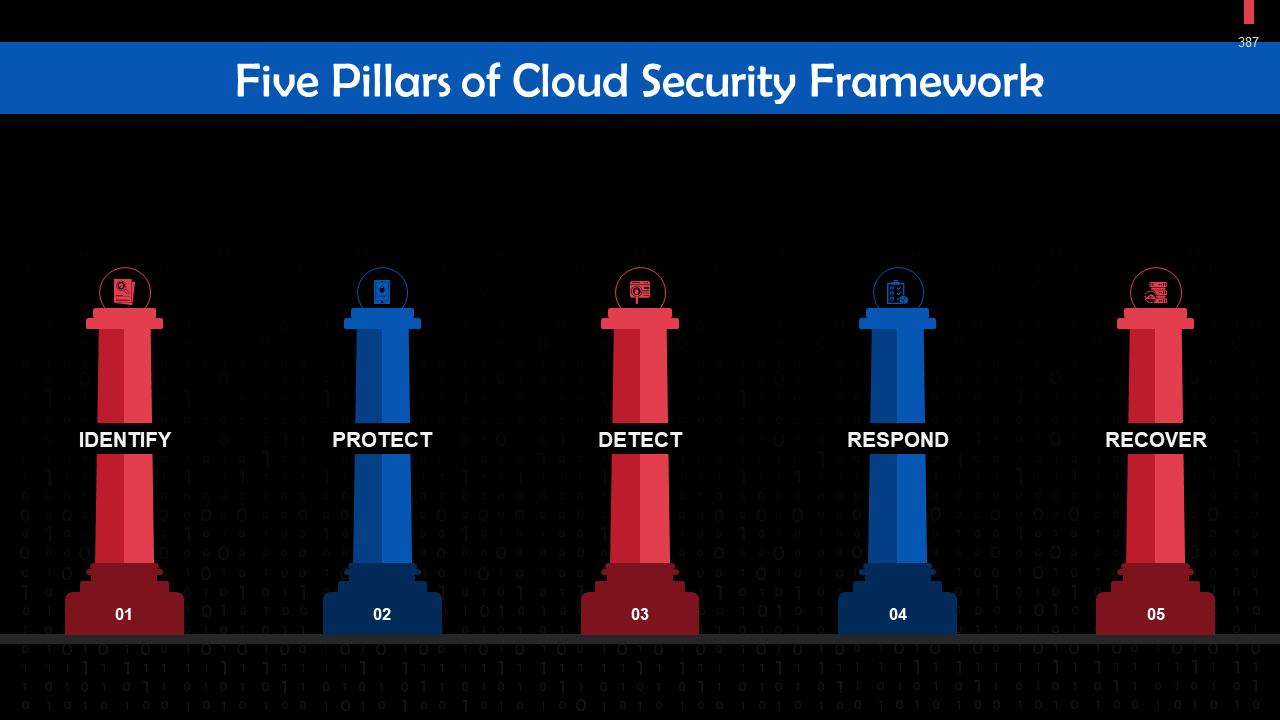
- Cloud Security
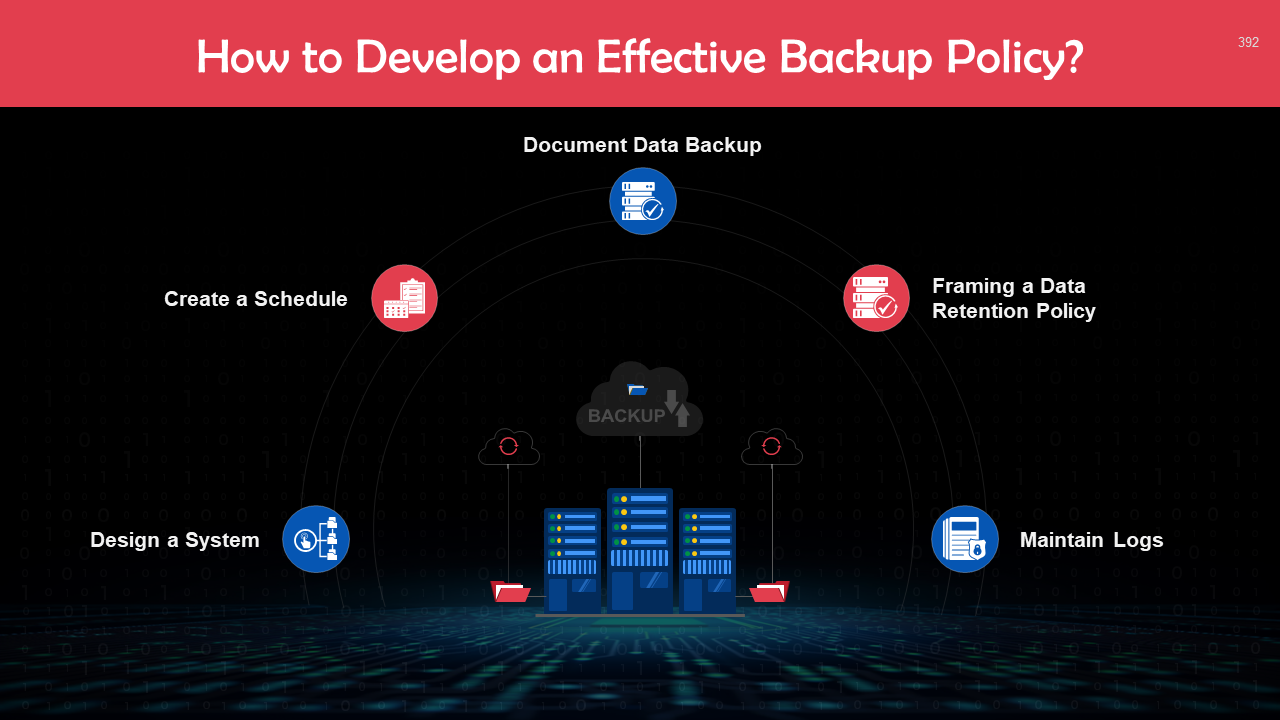
- Backup & Recovery
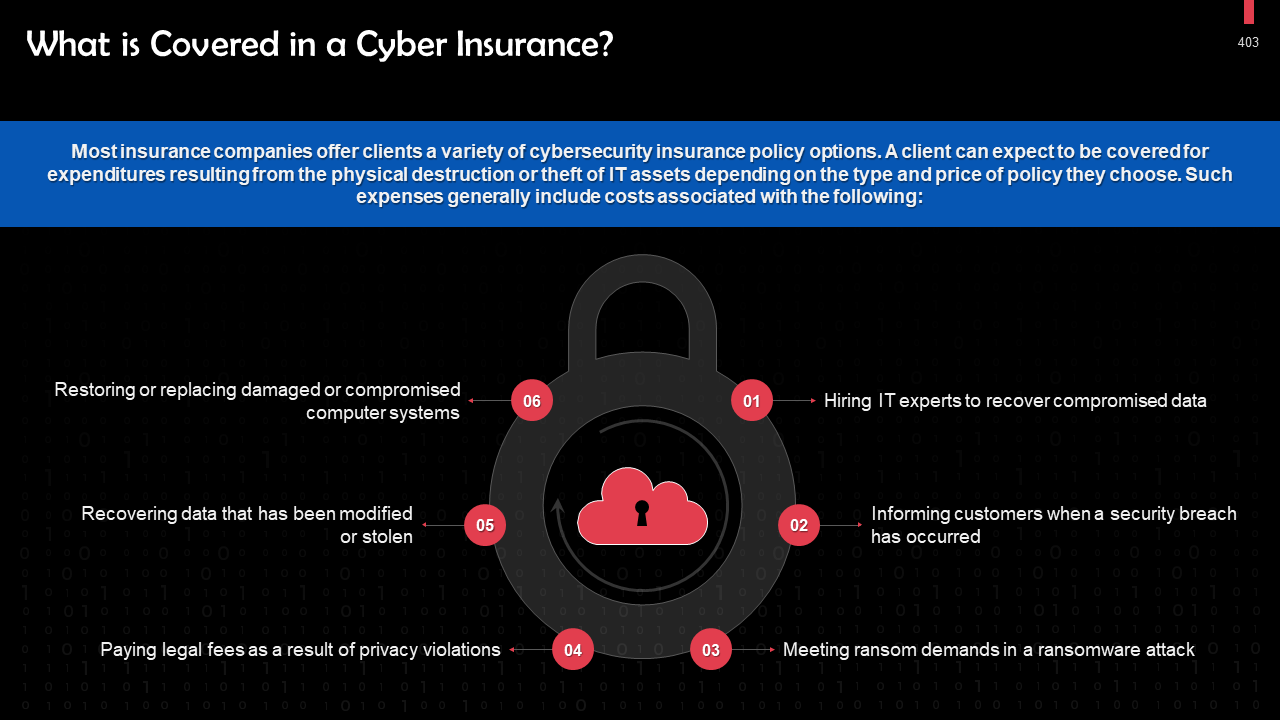
- Cyber Insurance
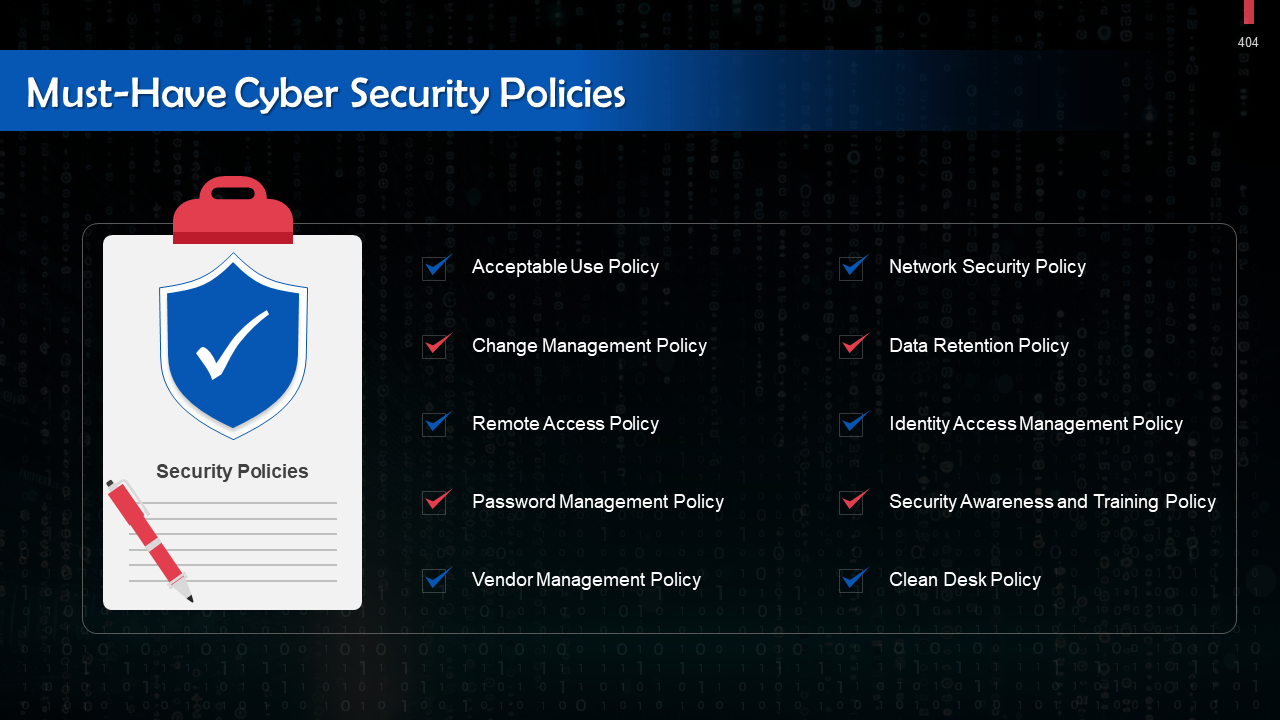
- Cybersecurity Policies
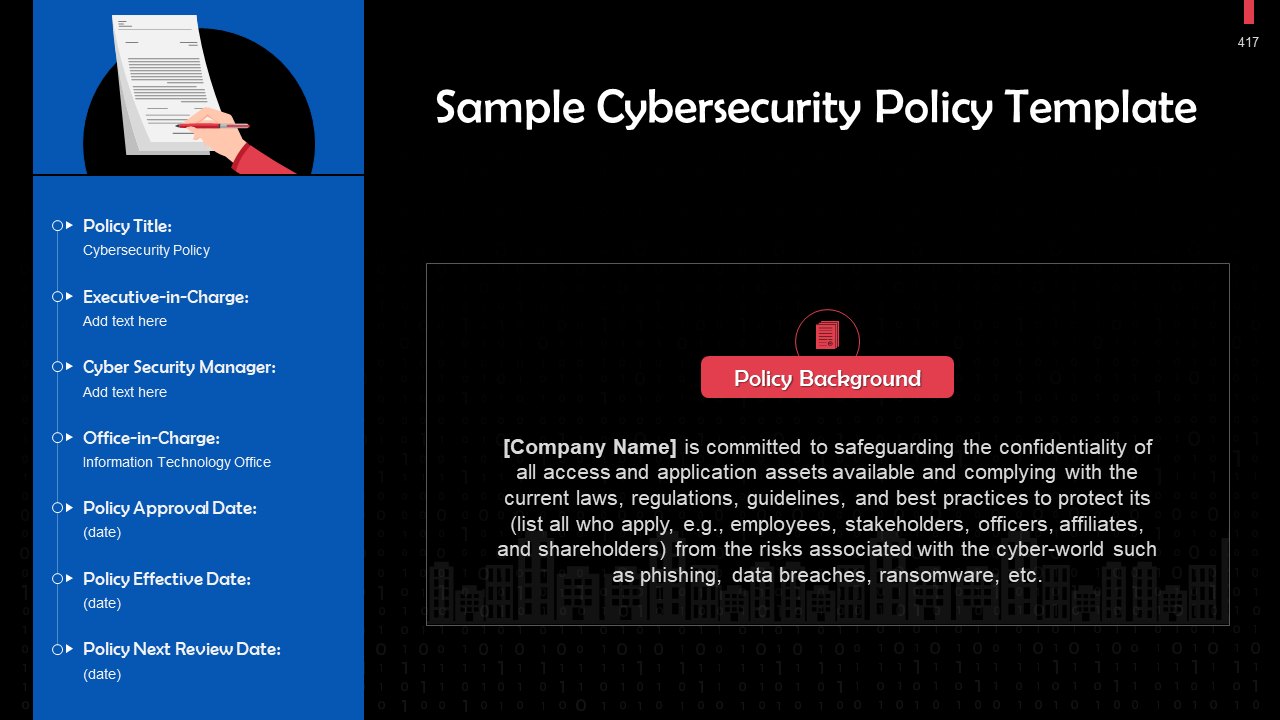
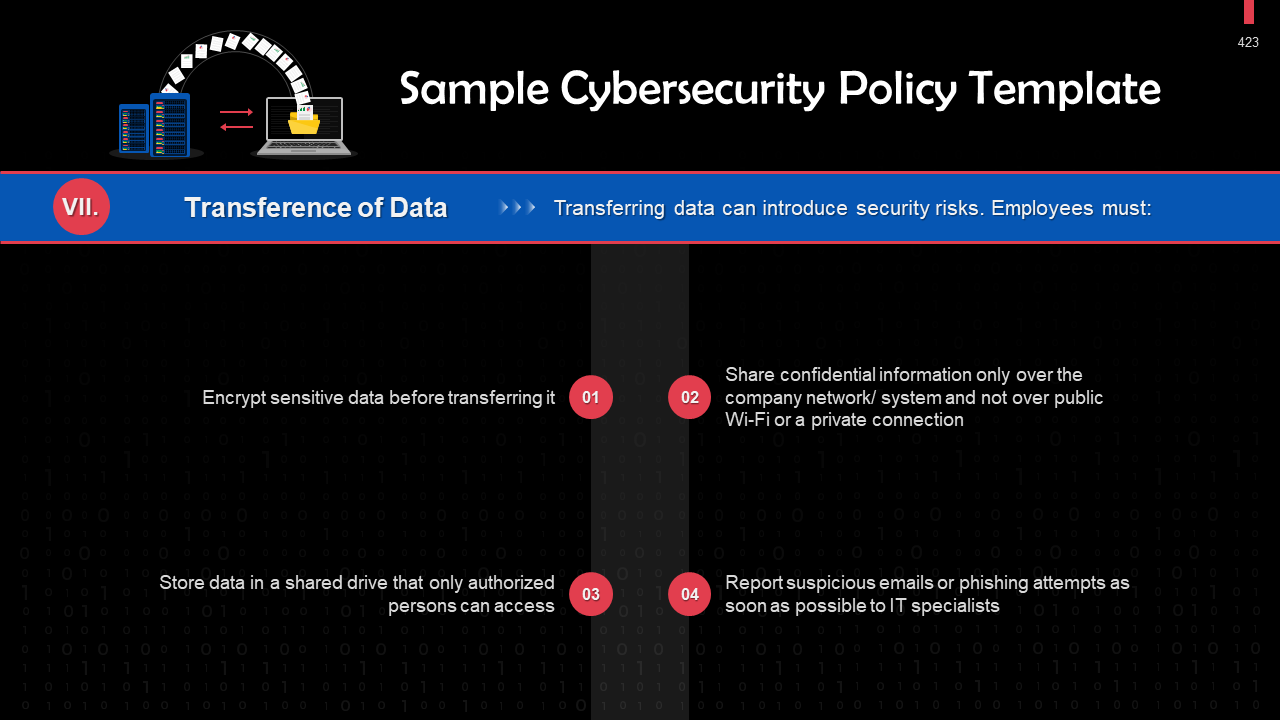
- Sample Organization Policy for Cybersecurity
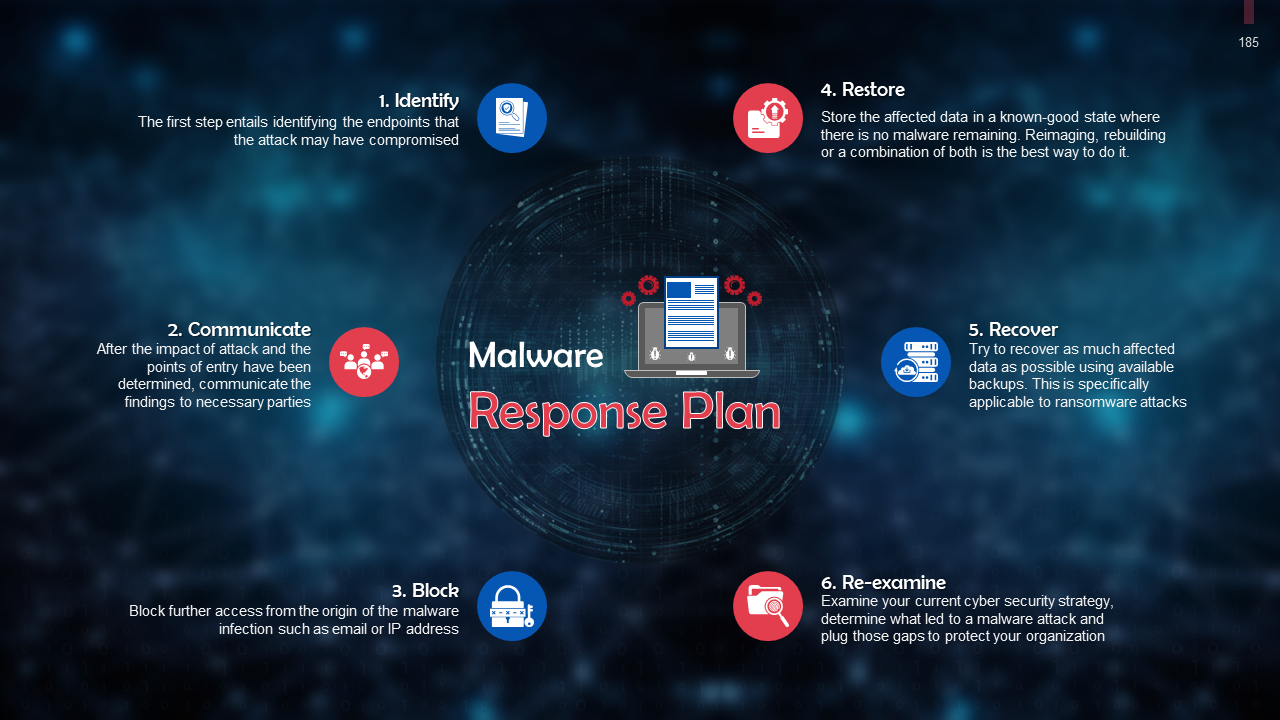
- Cybersecurity Incident Response Plan
- Cybersecurity Dos & Don’ts
- Cybersecurity Checklists & Posters
- Key Takeaways
- Let’s Discuss
- Let’s Test What We Have Learnt
Sample Instructor Notes
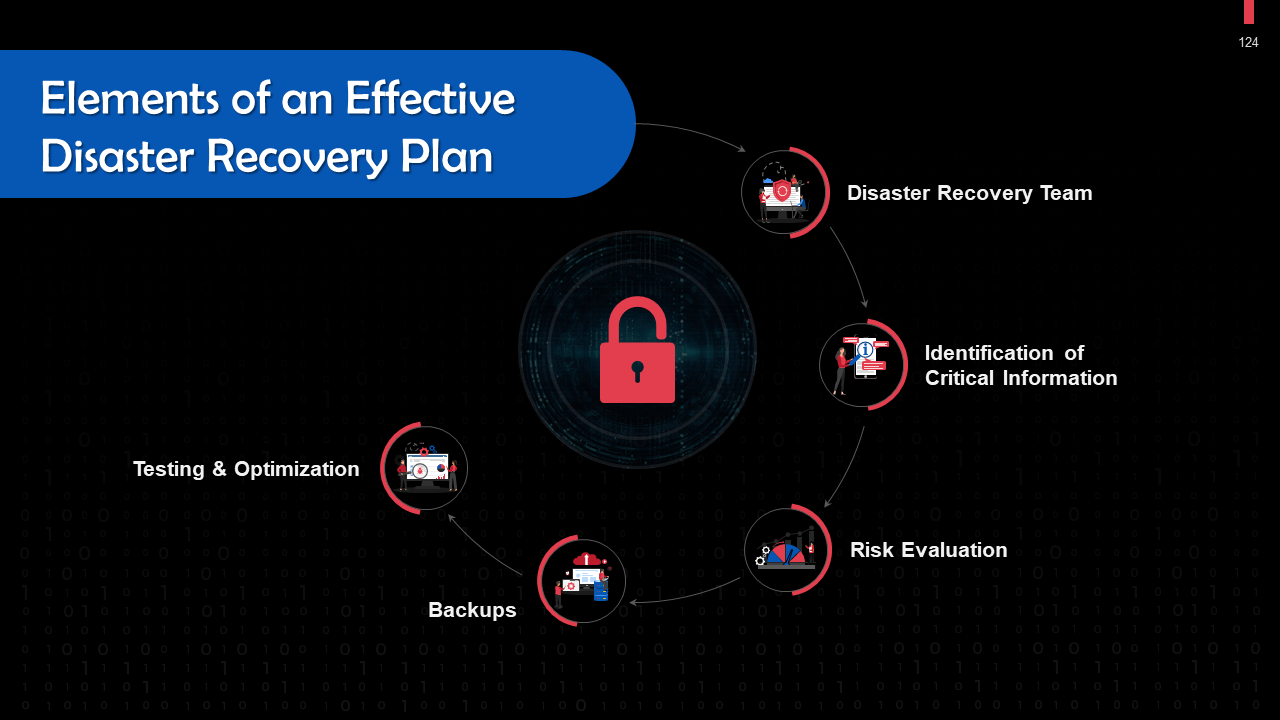
What is this slide for: Elements of an Effective Disaster Recovery Plan
This slide covers: This slide lists important elements in an effective disaster recovery plan. These are: Disaster recovery team, identification of critical information, risk evaluation, backups, and testing & optimization.
Instructor’s Notes:
- Disaster Recovery Team: A designated team of experts should develop, implement, and manage the disaster recovery plan. The roles and duties of each team member should be specified. The team must be able to communicate with one another, staff members, vendors, and clients in case of a cyberattack
- Identification of Critical Information: A solid disaster recovery plan outlines the systems, applications, data, and other resources that are most important for maintaining company operations. The plan also documents measures that must be taken to recover data
- Risk Evaluation: Analyze any potential risks to your organization. Plan the steps and resources necessary to restore operations based on the type of incident
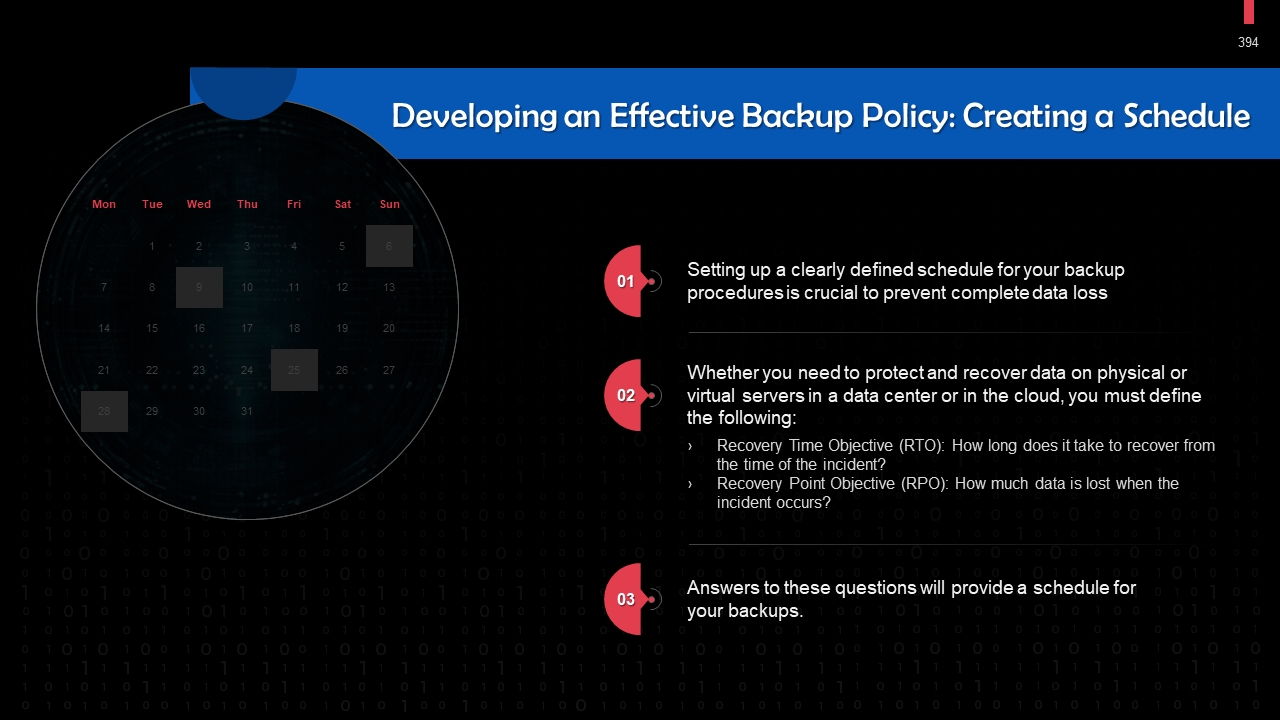
- Backups: Determine what needs a backup, who should perform backups, and how these should be implemented. Include a Recovery Point Objective (RPO) that specifies the frequency of backups along with a Recovery Time Objective (RTO) that states the maximum permissible downtime permitted after a security breach
- Testing & Optimization: The recovery team should regularly evaluate its strategy to address ever-evolving threats and business needs. In planning how to respond to a cyber-attack, it’s critical that organizations test and optimize their security and data protection strategies
What is this slide for: Steps to Remove an Active Ransomware Infection
This slide covers: This slide illustrates steps that active ransomware infection. Most ransomware attacks are detected only after data encryption is done; however, some steps must be taken immediately.
Instructor’s Notes:
- Quarantine the System: Some ransomware strains attempt to spread to other computers and associated drives. You can control its spread by blocking access to other potential recipients
- Leave the PC ON: A computer may become unstable if files are encrypted, and you can lose volatile memory when a computer is turned off can happen. Keep the computer running to increase the likelihood of recovery
- Create a Backup: For some ransomware versions, decrypting files is possible without paying the ransom. Create a backup of any encrypted files on a removable drive in case a solution is available in the future. Files are damaged during an unsuccessful decryption attempt
- Check for Decryptors: Check with the No More Ransom Project to check if a free decryptor is available. If so, run it on a copy of the encrypted data to see if it can restore the files
- Ask for Help: Computers sometimes keep backup copies of files stored on them. A digital forensics expert may be able to recover these copies if the malware has not deleted them
- Wipe and Restore: Restore the system from a clean backup or operating system installation. This ensures that the malware is completely deleted from the device
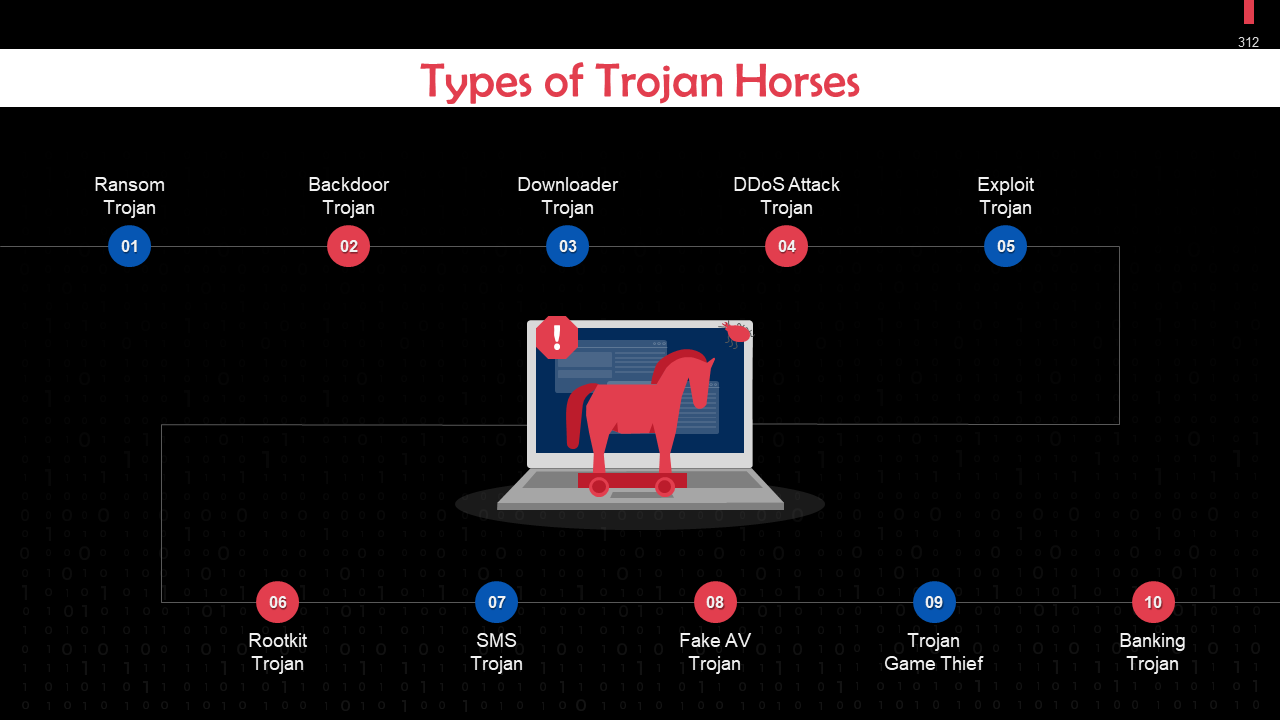
This slide covers: This slide highlights types of trojan horses. These are: Ransom trojan, backdoor trojan, downloader trojan, DDoS trojan, exploit trojan, rootkit trojan, SMS trojan, fake AV trojan, trojan game thief, and banking trojan.
Instructor’s Notes:
- Ransom Trojan: This Trojan malware demands ransom from users in exchange for the restoration of an infected device and its contents
- Backdoor Trojan: The threat actor sets up access points to the network using this malware
- Downloader Trojan: This type of trojan typically targets already compromised devices and installs a new version of malicious software on the device
- DDoS Trojan: These can be deployed to multiple devices to create a botnet, or a zombie network, which can then be used to execute a DDoS attack
- Exploit Trojan: As their name suggests, these Trojans identify and take advantage of vulnerabilities within software applications to gain access to the system
- Rootkit Trojan: Rootkits operate close to or within the operating system's kernel, which gives them the capability to initiate commands to the computer. This trojan provides unauthorized access to threat actors. It is challenging to detect as it can conceal its presence on the infected device
- SMS Trojan: This is a mobile device attack in which the Trojan malware can send and intercept text messages. It can also generate revenue by sending SMS messages to premium-rate numbers
- Fake AV Trojan: Disguised as antivirus software, this trojan is ransomware that demands users to pay to detect or remove threats. The issues that the program claims to have found are usually fake
- Trojan Game Thief: This trojan targets online gamers and attempts to access their gaming account login information
- Banking Trojan: This trojan targets financial accounts and is created to steal data related to bank accounts, credit or debit cards, or other online payment systems
FAQs
We provide training decks on a wide variety of business and technical topics such as Diversity & Inclusion, Customer Service, Search Engine Optimization, Blockchain Technology, and many more. These are ready-to-present decks that can be downloaded and presented in their current form. These decks are carefully created by industry experts, designed by professionals to deliver a power packed training session.
We want our training decks to evoke curiosity and inspire passion for learning. Each training deck consists of multiple sessions with impeccably designed slides to explain concepts in-depth, key takeaways to summarize sessions, discussions, and multiple-choice questions to assess trainees’ learning. The deck also contains activities and memes to break the monotony and make the training more interactive. Each training deck comes with an assessment form and editable proposal to help pitch your training to clients with success.
It depends on the trainer's content delivery pace, but each deck is created to ensure that training content is for a minimum of 16 hours.
Yes. A significant segment of our customers are professional mentors, coaches and teachers. You can create presentations with our content and distribute these to your trainees. The only caveat is that you cannot share your subscription to our content with others; the license is not transferable. Also, you cannot resell SlideTeam content to others.
Each slide is 100% editable in PowerPoint. Every element of the slide – text, icons, images, vectors, color scheme, etc. can be modified to build an effective PowerPoint presentation. Simply DOWNLOAD, EDIT, and PRESENT!
All PPT slides are compatible with PowerPoint 2007 and above. Some diagrams will not show up correctly with older versions of PowerPoint, like PowerPoint 2003 or lower, because of rendering issues. Yes, they work with PowerPoint for MAC, and decks are compatible with Google Slides too.
Absolutely yes! Our decks are yours to keep and build upon even after your subscription expires. You will not be able to download any additional decks once your subscription expires, but the ones you've downloaded are yours to keep forever.
Our entire website is HTTPS secure, and our payment system is managed by PayPal and Stripe, two of the world's leaders in credit card payment systems and very respected companies in online payments. This makes our systems 100% secure. We do not store or have access to any credit card information ourselves. We direct you to these third-party secure sites with 100% secure SSL connections where you can safely purchase a subscription and then direct you back to our site to download products.
You are allowed to log in and download content from 3 computers. Our website keeps track of login IP addresses, MAC Address Usage, and Browser and Computer Operating System fingerprinting, and you will not be able to log in from more than three computers.

2 Item(s)
-
by Derick Meyer
4/580%Fantastic collection. Loved how we can personalize these templates as per the requirements.
-
by Darron Hunter
4/580%The templates are handy and I can personalize them as per my needs. Glad to be your subscriber!
2 Item(s)