Business Impact of Cyber Attacks Training Ppt
The PPT Training Module on Business Impact of Cyber Attacks provides an extensive overview of cybersecurity and its significance in protecting businesses. It begins with What is Cybersecurity. followed by Goals of Cybersecurity, emphasizing the critical concepts of Confidentiality, Integrity, and Availability. Then, it delves into the Components of Cybersecurity and offers eye-opening Cybercrime Statistics. Introduction to Cyber Attack, sets the stage for understanding the motivations behind cyber attacks, the typical perpetrators, and their common targets. It also focuses on the Business Impact of Cyber Attacks, detailing how these incidents lead to increased costs, altered business practices, operational disruptions, lost revenue, reputational damage, and intellectual property theft. Case Studies provides real-world insights into these impacts. The PPT Deck also has Key Takeaways and Discussion Questions related to the topic to make the training session more interactive. The deck contains PPT slides on About Us, Vision, Mission, Goal, 30-60-90 Days Plan, Timeline, Roadmap, Training Completion Certificate, Energizer Activities, Client Proposal, and Assessment Form.
You must be logged in to download this presentation.
 Impress your
Impress your audience
Editable
of Time
PowerPoint presentation slides
Presenting Training Deck on Business Impact of Cyber Attacks. This deck comprises of 39 slides. Each slide is well crafted and designed by our PowerPoint experts. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed business presentation, add your content, and present it with confidence.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 3
This slide gives the definition of cybersecurity. The application of technology, techniques, and controls to defend systems, networks, programs, devices, and data against cyberattacks is known as cybersecurity.
Slide 4
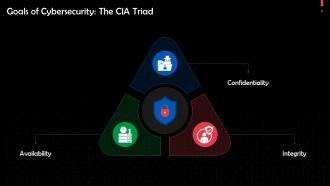
This slide depicts the three main goals of cybersecurity. These are confidentiality, integrity, and availability.
Slide 5
This slide talks about confidentiality as a goal of cybersecurity. Confidentiality helps in preventing unauthorized disclosure of information. It includes data security, granting access to permitted individuals while preventing unauthorized parties from discovering anything about its contents.
Slide 6
This slide discusses the tools for accomplishing cybersecurity’s goal of confidentiality. These are: Encryption, access control, authorization, authentication, and physical security.
Instructor’s Notes:
- Encryption: Applying an algorithm to modify data so that unauthorized users cannot understand its content is known as encryption
- Access Control: It refers to the set of guidelines that control who has access to a system or a physical or digital resource
- Authorization: Another security precaution is authorization, which involves getting permission to obtain or perform something. It is employed to determine whether a system or person is granted access to resources
- Authentication: A user's identity or role is verified through an authentication process
- Physical Security: Physical security prevents unauthorized access to IT assets such as buildings, machinery, personnel, resources, and other kind of information or knowledge. It protects against physical threats, including burglary, vandalism, fire, and natural disasters
Slide 7
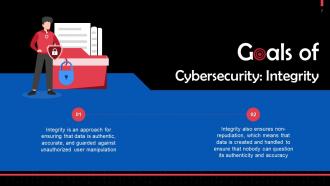
This slide talks about integrity as a goal of cybersecurity. Integrity is an approach for ensuring that data is authentic, accurate, and protected against unauthorized user manipulation.
Slide 8
This slide discusses the tools for accomplishing cybersecurity’s goal of integrity. These are backups, checksums, and codes for data correction.
Instructor’s Notes:
- Backups: Backup is archiving data on a regular basis. It is the process of duplicating data or data files that can be used if the originals are lost or destroyed
- Checksums: A checksum is a number used to determine whether a file or data transmission is genuine. In other words, it's the computation of a function that converts the contents of a file into a numerical value. They are frequently used to verify the identity of two pieces of data by comparing them
- Codes for Data Correction: It's a way to store data so that any minor modifications can be found and fixed automatically
Slide 9
This slide talks about availability as a goal of cybersecurity. The capability of individuals with authorization to view and modify information efficiently and promptly is known as availability.
Slide 10
This slide discusses the tools for accomplishing cybersecurity’s goal of availability. These are physical protection and computational redundancy.
Instructor’s Notes:
- Physical Protection: Physical protection is the ability to maintain information accessibility despite physical challenges, and it ensures that crucial information technologies and sensitive data are stored securely
- Computational Redundancy: Computational redundancy is implemented as a fault-tolerant system against inadvertent errors. It includes computers and storage systems that serve as backups if a system fails
Slide 11
This slide lists the components of cybersecurity. These are: Information security, application security, network security, end-user security, operational security, and disaster recovery planning.
Slide 12
This slide depicts key statistics for the financial loss that global cybercrime causes.
Slide 13
This slide gives us information about devices that are most vulnerable to cybercrime and leading malware carriers.
Slide 14
This slide gives the definition of a cyber attack. Cyberattacks are attempts to gain unauthorized access to computer systems to steal, expose, change, disable, or destroy information.
Slide 15
This slide lists reasons behind cyber attacks. Cyber attackers may have criminal, personal, or political motives.
Slide 16
This slide discusses who is behind cyber attacks. Cyber threats or attacks can be classified into two categories: Outsider and Insider threats.
Instructor’s Notes:
- External or outsider cyber risks can include: Criminal organizations or gangs, professional hackers (actors who receive state funding), amateur hackers or hacktivists
- Internal or insider cyber risks: Users with valid access to a company's resources who intentionally or unintentionally misuse them are known as insider threats. They consist of the following: Workers that disregard security policies and procedures, current or past employees who are not happy, business associates, customers, vendors, or suppliers with access to the system
Slide 17
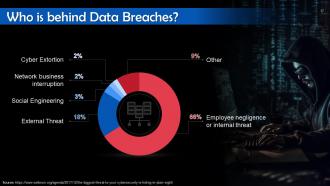
This slide tells us about who is behind cyber attacks or data breaches. As per a Data Breach Investigations Report by Verizon, most cyber attacks are caused because of employee negligence, followed by organized criminal groups, insiders, business partners, and affiliated groups.
Slide 18
This slide lists things that cyber attackers are aiming for. Some of these include: Information on business finances, lists of clients, client financial information, databases of customers that contain Personally Identifiable Information (PII), etc.
Slide 19
This slide highlights well-known and hidden costs of cyber incidents. Some easily identifiable impact includes legal fees, cybersecurity improvements, etc. Some hidden impact includes operational disruption, reputation damage, etc. The hidden impact is far more damaging than the more easily identifiable negative consequences.
Slide 20
This slide gives an overview of how cyber attacks can impact businesses. Cyber attacks can lead to increased costs, change in business practices, operational disruption, loss in revenue, reputational damage, and stolen intellectual property.
Slide 21
This slide talks about how cybercrime can lead to increased business costs. Organizations that come under cyber attack may incur costs, such as cybersecurity technology and expertise, notifying affected parties of a breach, insurance premiums, and public relations support.
Slide 22
This slide discusses how cybercrime affects business practices. To prevent leakage of sensitive data, companies must reconsider how they gather and retain data.
Slide 23
This slide talks about how cybercrime can lead to operational disruption. In addition to direct financial losses, organizations often incur indirect costs from cyberattacks, such as significant business interruptions that lead to revenue loss.
Slide 24
This slide discusses how cybercrime can lead to losses in revenue. A cyberattack may cause a sudden decline in sales as cautious clients go elsewhere to protect themselves against cybercrime.
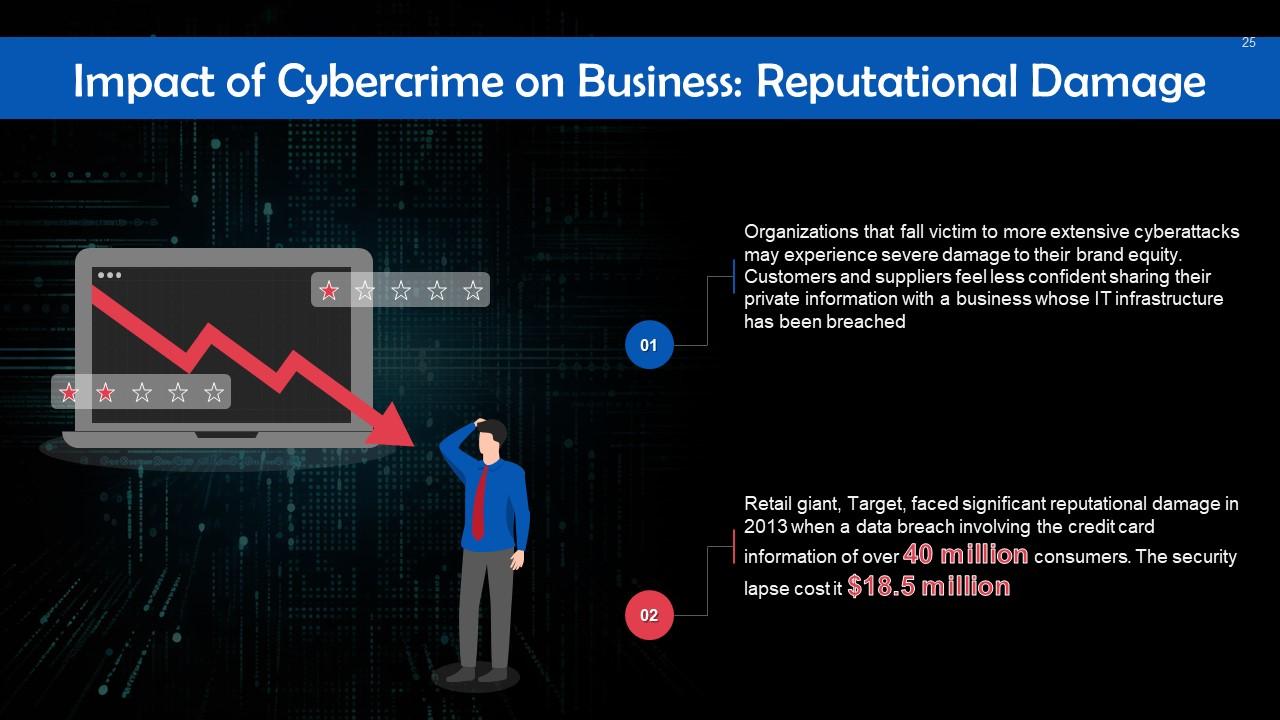
Slide 25
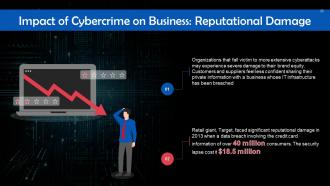
This slide talks about the reputational damage that cybercrime inflicts on businesses. Organizations that fall victim to more extensive cyberattacks see a rapid erosion in their brand equity. Customers and suppliers might feel less confident sharing their private information with a business whose IT infrastructure has been breached.
Instructor’s Notes: Research indicates that publicly traded corporations are likely to have a short-term decline in market value in addition to decreased institutional trust.
Slide 26
This slide discusses how intellectual property is stolen during cyberattacks. Products, technology, and go-to-market plans are frequently among a company's most valuable assets. A large portion of this intellectual property is stored in the cloud, which makes it susceptible to data breaches or cyberattacks.
Slide 27
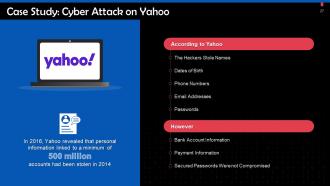
This slide gives information about a cyber attack on yahoo. In 2016, Yahoo revealed that personal information linked to a minimum of 500 million accounts had been stolen in 2014.
Slide 28
This slide highlights the financial implications of the 2014 data breach on Yahoo. The breaches affected Verizon Communications' intentions to purchase Yahoo! for $4.8 billion in July 2016. The breach led to a $350 million reduction in the final price of the merger finalized in June 2017.
Slide 29
This slide gives an overview of the cyber attack on Sony’s PlayStation Network. In 2011, Sony disclosed that approximately 77 million customers' names, addresses, and other personal information on its PlayStation Network (PSN) had been stolen.
Slide 30
This slide highlights some interesting facts about Sony’s Playstation Network Attack. Sony wrote to the US House of Representatives to make many announcements, including the provision of an identity theft insurance policy of $1 million per PlayStation Network subscriber
Instructor’s Notes: Another complaint from Canada sought up to C$1 billion in damages against Sony USA, Sony Canada, and Sony Japan
Slide 51 to 66
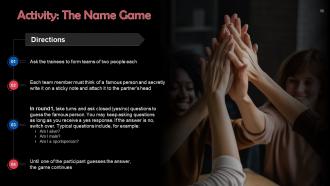
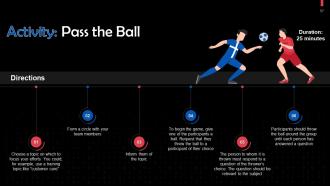
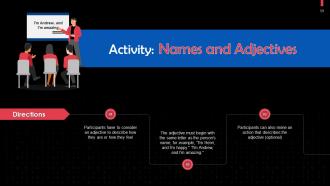
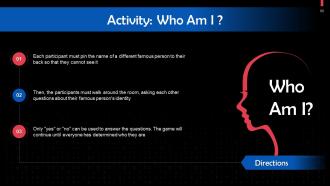
These slides contain energizer activities that a trainer can employ to make the training session interactive and engage the audience.
Slide 67 to 94
These slides contain a training proposal covering what the company providing corporate training can accomplish for prospective clients.
Slide 95 to 97
These slides include a training evaluation form for the instructor, content, and course assessment to assess the effectiveness of the coaching program.
Business Impact of Cyber Attacks Training Ppt with all 106 slides:
Use our Business Impact of Cyber Attacks Training Ppt to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
I was really impressed with the presentation I created with their templates. I’ll be using their services moving forward.
-
Excellent Designs.