Powerpoint Templates and Google slides for Vulnerable Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
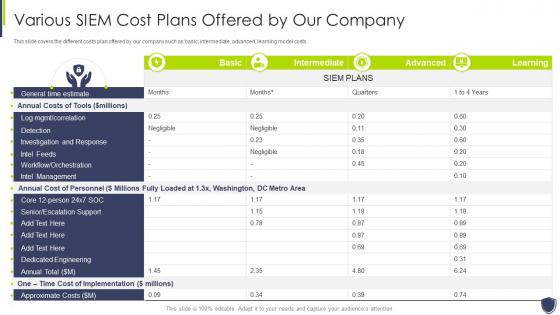 Improve it security with vulnerability management various siem cost plans offered company
Improve it security with vulnerability management various siem cost plans offered companyThis slide covers the different costs plan offered by our company such as basic, intermediate, advanced, learning model costs. Present the topic in a bit more detail with this Improve It Security With Vulnerability Management Various Siem Cost Plans Offered Company. Use it as a tool for discussion and navigation on Various SIEM Cost Plans Offered By Our Company. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Improve it security with vulnerability management what sets us apart
Improve it security with vulnerability management what sets us apartThis slide covers the reasons why our company is different from other SIEM companies since they have qualities such as attractive TCO and ROI, improved IT productivity, etc. Increase audience engagement and knowledge by dispensing information using Improve It Security With Vulnerability Management What Sets Us Apart. This template helps you present information on four stages. You can also present information on Productivity, Improvement, Business using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
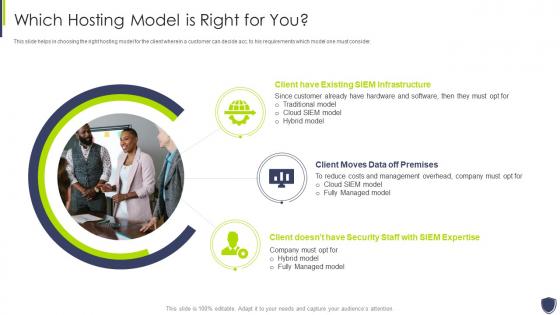 Improve it security with vulnerability management which hosting model is right for you
Improve it security with vulnerability management which hosting model is right for youThis slide helps in choosing the right hosting model for the client wherein a customer can decide acc. to his requirements which model one must consider. Introducing Improve It Security With Vulnerability Management Which Hosting Model Is Right For You to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Infrastructure, Premises, Management, using this template. Grab it now to reap its full benefits.
-
 Log management services improve it security with vulnerability management
Log management services improve it security with vulnerability managementIncrease audience engagement and knowledge by dispensing information using Log Management Services Improve It Security With Vulnerability Management. This template helps you present information on eight stages. You can also present information on Virtualization, Application, Databases using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Our management team improve it security with vulnerability management
Our management team improve it security with vulnerability managementIntroducing Our Management Team Improve It Security With Vulnerability Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Our Management Team, using this template. Grab it now to reap its full benefits.
-
 Siem competitive advantage improve it security with vulnerability management
Siem competitive advantage improve it security with vulnerability managementThis slide covers the SIEM competitive landscape based on various categories such as digital experience management, health check, application performance monitoring, event management, etc. Present the topic in a bit more detail with this Siem Competitive Advantage Improve It Security With Vulnerability Management. Use it as a tool for discussion and navigation on Experience, Management, Competitive. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table of contents improve it security with vulnerability management
Table of contents improve it security with vulnerability managementIncrease audience engagement and knowledge by dispensing information using Table Of Contents Improve It Security With Vulnerability Management. This template helps you present information on eleven stages. You can also present information on Vulnerability, Management, Architecture using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 What our clients say about us improve it security with vulnerability management
What our clients say about us improve it security with vulnerability managementThis slide covers the client testimonials and what our customers have to say about our company and its services to understand the companys market reputation. Deliver an outstanding presentation on the topic using this What Our Clients Say About Us Improve It Security With Vulnerability Management. Dispense information and present a thorough explanation of What Our Clients Say About Us using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Agenda of improve it security with vulnerability management
Agenda of improve it security with vulnerability managementIntroducing Agenda Of Improve It Security With Vulnerability Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability, Management, Agenda, using this template. Grab it now to reap its full benefits.
-
 Architecture flowchart improve it security with vulnerability management
Architecture flowchart improve it security with vulnerability managementThis slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Present the topic in a bit more detail with this Architecture Flowchart Improve It Security With Vulnerability Management. Use it as a tool for discussion and navigation on Security Device, Network Devices, Servers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Estimating total cost of ownership improve it security vulnerability management
Estimating total cost of ownership improve it security vulnerability managementThis slide covers the total cost of ownership incurred by SIEM services which focuses on the costs of hardware, software, infrastructure, and support. Deliver an outstanding presentation on the topic using this Estimating Total Cost Of Ownership Improve It Security Vulnerability Management. Dispense information and present a thorough explanation of Estimating Total Cost Of Ownership Of SIEM using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Icons slide for improve it security with vulnerability management
Icons slide for improve it security with vulnerability managementIntroducing our well researched set of slides titled Icons Slide For Improve It Security With Vulnerability Management. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Improve it security vulnerability management calculating network device velocity sizing
Improve it security vulnerability management calculating network device velocity sizingThis slide covers the SIEM sizing wherein velocity is calculated for various selected network devices and conduct an inventory of the devices from where logs can be collected. Present the topic in a bit more detail with this Improve It Security Vulnerability Management Calculating Network Device Velocity Sizing. Use it as a tool for discussion and navigation on Calculating Network Device Velocity Sizing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Improve it security vulnerability management companys enhanced features capabilities
Improve it security vulnerability management companys enhanced features capabilitiesThis slide provides the details about the companys main features and additional features such as threat detection, investigation, security monitoring, normalization, etc. Deliver an outstanding presentation on the topic using this Improve It Security Vulnerability Management Companys Enhanced Features Capabilities. Dispense information and present a thorough explanation of Threat Detection, Investigation, Time To Respond using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Improve it security vulnerability management estimating total cost ownership siem
Improve it security vulnerability management estimating total cost ownership siemThis slide covers the cost breakdown of SIEM solution based on initial expenses, recurring expenses and amount saved by the client if they choose our company. Present the topic in a bit more detail with this Improve It Security Vulnerability Management Estimating Total Cost Ownership Siem. Use it as a tool for discussion and navigation on Management, Engineering, Ownership. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Improve it security with vulnerability benchmarking security operations maturity model
Improve it security with vulnerability benchmarking security operations maturity modelThis slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Introducing Improve It Security With Vulnerability Benchmarking Security Operations Maturity Model to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Improve Visibility, Quickly Identify Threats, Decrease Response Time, using this template. Grab it now to reap its full benefits.
-
 Improve it security with vulnerability benefits of choosing our company siem services
Improve it security with vulnerability benefits of choosing our company siem servicesThis slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. Increase audience engagement and knowledge by dispensing information using Improve It Security With Vulnerability Benefits Of Choosing Our Company Siem Services. This template helps you present information on four stages. You can also present information on Cost Saving, Reduction In The Impact Of Security Events, Compliance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Improve it security with vulnerability information and event management logging process
Improve it security with vulnerability information and event management logging processThis slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Introducing Improve It Security With Vulnerability Information And Event Management Logging Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Information, Management, Process, using this template. Grab it now to reap its full benefits.
-
 Improve it security with vulnerability management about our siem company
Improve it security with vulnerability management about our siem companyThis slide provides the glimpse about the SIEM company which covers the companys background, firms operations and offerings. Present the topic in a bit more detail with this Improve It Security With Vulnerability Management About Our Siem Company. Use it as a tool for discussion and navigation on Automatized, Solutions, Innovative. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Improve it security with vulnerability management cloud siem model
Improve it security with vulnerability management cloud siem modelThis slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver an outstanding presentation on the topic using this Improve It Security With Vulnerability Management Cloud Siem Model. Dispense information and present a thorough explanation of Vulnerability, Management, Processes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Improve it security with vulnerability management competitive advantage
Improve it security with vulnerability management competitive advantageThis slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Present the topic in a bit more detail with this Improve It Security With Vulnerability Management Competitive Advantage. Use it as a tool for discussion and navigation on Siem Competitive Advantage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Improve it security with vulnerability management event management services
Improve it security with vulnerability management event management servicesThis slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Increase audience engagement and knowledge by dispensing information using Improve It Security With Vulnerability Management Event Management Services. This template helps you present information on eight stages. You can also present information on Data Aggregation, Data Correlation, Security Alert using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Improve it security with vulnerability management fully managed service model
Improve it security with vulnerability management fully managed service modelThis slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Deliver an outstanding presentation on the topic using this Improve It Security With Vulnerability Management Fully Managed Service Model. Dispense information and present a thorough explanation of Vulnerability, Management, Processes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Improve it security with vulnerability management hybrid managed siem model
Improve it security with vulnerability management hybrid managed siem modelThis slide covers the hybrid managed model wherein most of the services will be taken care by our company except event sources which focuses on handling software and hardware infrastructure. Deliver an outstanding presentation on the topic using this Improve It Security With Vulnerability Management Hybrid Managed Siem Model. Dispense information and present a thorough explanation of Vulnerability, Management, Processes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Improve it security with vulnerability management integrations
Improve it security with vulnerability management integrationsPresent the topic in a bit more detail with this Improve It Security With Vulnerability Management Integrations. Use it as a tool for discussion and navigation on Applications And Devices, Network Logs, Security Events. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Improve it security with vulnerability management key features of siem software
Improve it security with vulnerability management key features of siem softwareThis slide provides the details about our companys SIEM key features such as automated reports, log collection and classification, high scalability, security automation, etc. Increase audience engagement and knowledge by dispensing information using Improve It Security With Vulnerability Management Key Features Of Siem Software. This template helps you present information on seven stages. You can also present information on Comprehensive, Compliance, Classification using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Improve it security with vulnerability management log management services
Improve it security with vulnerability management log management servicesThis slide covers the log management services offered by our company such as collection and normalization, search speed, real time analysis, decision making process etc. Introducing Improve It Security With Vulnerability Management Log Management Services to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Collection And Normalization, Search Speed, Real Time Analysis, using this template. Grab it now to reap its full benefits.
-
 Improve it security with vulnerability management logging sources
Improve it security with vulnerability management logging sourcesThis slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. Increase audience engagement and knowledge by dispensing information using Improve It Security With Vulnerability Management Logging Sources. This template helps you present information on four stages. You can also present information on Security Devices, Network Devices, Servers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Improve it security with vulnerability management need for siem software company
Improve it security with vulnerability management need for siem software companyThis slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management Introducing Improve It Security With Vulnerability Management Need For Siem Software Company to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Detecting Incidents, Compliance With Regulations, Efficient Incident Management, using this template. Grab it now to reap its full benefits.
-
 Improve it security with vulnerability management next evolution of siem software
Improve it security with vulnerability management next evolution of siem softwareThis slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Increase audience engagement and knowledge by dispensing information using Improve It Security With Vulnerability Management Next Evolution Of Siem Software. This template helps you present information on six stages. You can also present information on Foundation, Threat Intelligence, Analytics using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Improve it security with vulnerability management organization siem log flow
Improve it security with vulnerability management organization siem log flowThis slide covers the companys log flow and understand how the data is gathered, security alerts are notified to the clients. Introducing Improve It Security With Vulnerability Management Organization Siem Log Flow to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Our Organization Siem Log Flow, using this template. Grab it now to reap its full benefits.
-
 Improve it security with vulnerability management our siem companys milestones
Improve it security with vulnerability management our siem companys milestonesThis slide provides the milestones of our company such as foundation year, revenue generation, profitability, etc. Increase audience engagement and knowledge by dispensing information using Improve It Security With Vulnerability Management Our Siem Companys Milestones. This template helps you present information on six stages. You can also present information on Our Siem Companys Milestones using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Improve it security with vulnerability management security intelligence services
Improve it security with vulnerability management security intelligence servicesThis slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Deliver an outstanding presentation on the topic using this Improve It Security With Vulnerability Management Security Intelligence Services. Dispense information and present a thorough explanation of Management, Analytics, Infrastructure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Improve it security with vulnerability management siem architecture
Improve it security with vulnerability management siem architecturePresent the topic in a bit more detail with this Improve It Security With Vulnerability Management Siem Architecture. Use it as a tool for discussion and navigation on Vulnerability Scans, Operating Systems, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing Asset Security Categorization Vulnerability Administration At Workplace
Addressing Asset Security Categorization Vulnerability Administration At WorkplaceThis slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Present the topic in a bit more detail with this Addressing Asset Security Categorization Vulnerability Administration At Workplace. Use it as a tool for discussion and navigation on Location, Availability, Categorization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Vulnerability Administration At Workplace Selecting Secured Threat Management Software
Vulnerability Administration At Workplace Selecting Secured Threat Management SoftwareThis slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Present the topic in a bit more detail with this Vulnerability Administration At Workplace Selecting Secured Threat Management Software. Use it as a tool for discussion and navigation on Management, Software, Workflows. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Vulnerability Cyber Security Ppt Powerpoint Presentation Icon Clipart Images Cpb
Vulnerability Cyber Security Ppt Powerpoint Presentation Icon Clipart Images CpbPresenting Vulnerability Cyber Security Ppt Powerpoint Presentation Icon Clipart Images Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Vulnerability Cyber Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cloud Security Threats Shared Vulnerabilities Cloud Information Security
Cloud Security Threats Shared Vulnerabilities Cloud Information SecurityThis slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data.Introducing Cloud Security Threats Shared Vulnerabilities Cloud Information Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Information Centers, Reduced Upfront, Diminished Opportunity using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Shared Vulnerabilities Cloud Computing Security
Cloud Security Threats Shared Vulnerabilities Cloud Computing SecurityThis slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. Introducing Cloud Security Threats Shared Vulnerabilities Cloud Computing Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Secure Cloud Data, Organizations, Clients Responsibility, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Vulnerability Analysis Checklist
Cyber Security Vulnerability Analysis ChecklistThis slide contains the checklist of multiple human threats human error, dishonesty, social engineering attacks and general threats with their impact and probability to occur in the business. Introducing our premium set of slides with Cyber Security Vulnerability Analysis Checklist. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Human Threats, General Threats, Unsecure Devices. So download instantly and tailor it with your information.
-
 Risk Assessment Matrix With Vulnerability Risk Assessment And Management Plan For Information Security
Risk Assessment Matrix With Vulnerability Risk Assessment And Management Plan For Information SecurityThis slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level Present the topic in a bit more detail with this Risk Assessment Matrix With Vulnerability Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Assessment, Vulnerability, Associated. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Vulnerability And Data Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Vulnerability And Data Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Vulnerability and data security colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Vulnerability And Data Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Vulnerability And Data Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Vulnerability and data security monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Vulnerability And Security Magnification Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Vulnerability And Security Magnification Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Vulnerability and security magnification colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Vulnerability And Security Magnification Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Vulnerability And Security Magnification Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Vulnerability and security magnification monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Cloud Security Threats Shared Vulnerabilities Cloud Data Protection
Cloud Security Threats Shared Vulnerabilities Cloud Data ProtectionThis slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. Introducing Cloud Security Threats Shared Vulnerabilities Cloud Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Secure Cloud Data, Organizations, Data Security, using this template. Grab it now to reap its full benefits.
-
 Vulnerability Management Cyber Security In Powerpoint And Google Slides Cpb
Vulnerability Management Cyber Security In Powerpoint And Google Slides CpbPresenting Vulnerability Management Cyber Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Vulnerability Management Cyber Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 IT Risk Management Strategies Security Criteria And Control Measures For IT System Vulnerabilities
IT Risk Management Strategies Security Criteria And Control Measures For IT System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Introducing IT Risk Management Strategies Security Criteria And Control Measures For It System Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Security, Operational Security, Technical Security, using this template. Grab it now to reap its full benefits.
-
 Enterprise Risk Management Security Criteria And Control Measures For IT System Vulnerabilities
Enterprise Risk Management Security Criteria And Control Measures For IT System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Introducing Enterprise Risk Management Security Criteria And Control Measures For IT System Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Security, Operational Security, Technical Security, using this template. Grab it now to reap its full benefits.
-
 Security Criteria And Control Measures For IT System Vulnerabilities
Security Criteria And Control Measures For IT System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Introducing Security Criteria And Control Measures For IT System Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Security, Operational Security, Technical Security, using this template. Grab it now to reap its full benefits.
-
 Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Management
Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk ManagementThis slide showcases assessment matrix to identify risk associate with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Deliver an outstanding presentation on the topic using this Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Management. Dispense information and present a thorough explanation of Risk Assessment Matrix, Vulnerability Level, Threat Level using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat Identification And Vulnerability Assessment Information Security Risk Management
Threat Identification And Vulnerability Assessment Information Security Risk ManagementThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Present the topic in a bit more detail with this Threat Identification And Vulnerability Assessment Information Security Risk Management. Use it as a tool for discussion and navigation on Threat Identification, Vulnerability Assessment, Risk Identification. This template is free to edit as deemed fit for your organization. Therefore download it now
-
 Vulnerability Rating For Risk Identification Information Security Risk Management
Vulnerability Rating For Risk Identification Information Security Risk ManagementThis slide showcases table for allocating vulnerability rating to different class of information assets. Its shows information about severity, vulnerability score and description. Present the topic in a bit more detail with this Vulnerability Rating For Risk Identification Information Security Risk Management. Use it as a tool for discussion and navigation on Vulnerability Score, Risk Identification, Severity. This template is free to edit as deemed fit for your organization. Therefore download it now
-
 Risk Assessment Of It Systems Security Criteria And Control Measures For It System Vulnerabilities
Risk Assessment Of It Systems Security Criteria And Control Measures For It System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Deliver an outstanding presentation on the topic using this Risk Assessment Of It Systems Security Criteria And Control Measures For It System Vulnerabilities. Dispense information and present a thorough explanation of Management Security, Operational Security, Technical Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information System Security And Risk Administration Risk Assessment Matrix With Vulnerability And Threat Level
Information System Security And Risk Administration Risk Assessment Matrix With Vulnerability And Threat LevelThis slide showcases assessment matrix to identify risk associated with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Present the topic in a bit more detail with this Information System Security And Risk Administration Risk Assessment Matrix With Vulnerability And Threat Level. Use it as a tool for discussion and navigation on Treat Level, Vulnerability Level, Risk Assessment Matrix. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat Identification And Vulnerability Assessment For Information System Security And Risk Administration Plan
Threat Identification And Vulnerability Assessment For Information System Security And Risk Administration PlanThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Deliver an outstanding presentation on the topic using this Threat Identification And Vulnerability Assessment For Information System Security And Risk Administration Plan. Dispense information and present a thorough explanation of Vulnerability Severity, Threat Source, Risk Rating using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Vulnerability Rating For Risk Identification Information System Security And Risk Administration Plan
Vulnerability Rating For Risk Identification Information System Security And Risk Administration PlanThis slide showcases table for allocating vulnerability rating to different class of information assets. Its shows information about severity, vulnerability score and description. Increase audience engagement and knowledge by dispensing information using Vulnerability Rating For Risk Identification Information System Security And Risk Administration Plan. This template helps you present information on one stages. You can also present information on Severity, Vulnerability Score, Vulnerability Rating using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Vulnerability Management Program And Security Services
Vulnerability Management Program And Security ServicesThis slide defines the vulnerability management program and security services based on risk. It includes information related to integrating, assessment planning, analysis and sustainability. Presenting our set of slides with Vulnerability Management Program And Security Services. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Assessment Planning, Analysis And Reporting, Sustainability.
-
 Cyber Security Environment Vulnerability Assessment In Powerpoint And Google Slides Cpb
Cyber Security Environment Vulnerability Assessment In Powerpoint And Google Slides CpbPresenting our Cyber Security Environment Vulnerability Assessment In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases eight stages. It is useful to share insightful information on Cyber Security Environment Vulnerability Assessment. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Web security vulnerabilities click image
Web security vulnerabilities click imagePresenting this set of slides with name Web Security Vulnerabilities Click Image. The topics discussed in these slides are Web Security, Computer, Networking. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.





