Powerpoint Templates and Google slides for Security Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Global Cyber Security Trend Analysis Creating Cyber Security Awareness
Global Cyber Security Trend Analysis Creating Cyber Security AwarenessThe following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber-attacks etc. Introducing Global Cyber Security Trend Analysis Creating Cyber Security Awareness to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Parameters, Probability, Risk Score using this template. Grab it now to reap its full benefits.
-
 Impact Of Cyber Safety Security Measures Creating Cyber Security Awareness
Impact Of Cyber Safety Security Measures Creating Cyber Security AwarenessThe following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies. Present the topic in a bit more detail with this Impact Of Cyber Safety Security Measures Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Cyber Security, Mitigation Planning This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Cyber Security Policies And Practices Creating Cyber Security Awareness
Impact Of Cyber Security Policies And Practices Creating Cyber Security AwarenessThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, Deliver an outstanding presentation on the topic using this Impact Of Cyber Security Policies And Practices Creating Cyber Security Awareness Dispense information and present a thorough explanation of Lost Revenue, Operational Disruption, Reputational Damage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Kpis To Evaluate Cyber Security Risk Management Creating Cyber Security Awareness
Kpis To Evaluate Cyber Security Risk Management Creating Cyber Security AwarenessThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this Kpis To Evaluate Cyber Security Risk Management Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Minimizes Malware Infection, Security Requirements, Internal Risks This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organize Cyber Security Training For Employees Regularly Creating Cyber Security Awareness
Organize Cyber Security Training For Employees Regularly Creating Cyber Security AwarenessThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Present the topic in a bit more detail with this Organize Cyber Security Training For Employees Regularly Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Password Management, Due To Human Errors This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritize Cyber Security Risk With Severity Matrix Creating Cyber Security Awareness
Prioritize Cyber Security Risk With Severity Matrix Creating Cyber Security AwarenessThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Present the topic in a bit more detail with this Prioritize Cyber Security Risk With Severity Matrix Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Target Audience, Document Management This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Review Cyber Security Status With Due Diligence Checklist Creating Cyber Security Awareness
Review Cyber Security Status With Due Diligence Checklist Creating Cyber Security AwarenessThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Present the topic in a bit more detail with this Review Cyber Security Status With Due Diligence Checklist Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Risk Probability, Risk Severity This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Select Tools To Reduce Cyber Security Failure Creating Cyber Security Awareness
Select Tools To Reduce Cyber Security Failure Creating Cyber Security AwarenessThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Deliver an outstanding presentation on the topic using this Select Tools To Reduce Cyber Security Failure Creating Cyber Security Awareness Dispense information and present a thorough explanation of Duration, Mode, Start Date, End Date using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices For Securing IoT System IoT Security And Privacy Safeguarding IoT SS
Best Practices For Securing IoT System IoT Security And Privacy Safeguarding IoT SSThis slide exhibits IoT security best practices that help in addressing potential security weaknesses. It includes best practices such as network segmentation, IoT incident response plan, intrusion detection system, and patching and remediation. Increase audience engagement and knowledge by dispensing information using Best Practices For Securing IoT System IoT Security And Privacy Safeguarding IoT SS. This template helps you present information on four stages. You can also present information on Network Segmentation, Intrusion Detection System, Patching Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain Approaches To Enhance IoT Data Security IoT Security And Privacy Safeguarding IoT SS
Blockchain Approaches To Enhance IoT Data Security IoT Security And Privacy Safeguarding IoT SSThis slide encompasses blockchain technical applications to the IoT ecosystem aimed at enhancing data privacy and security. It includes decentralized system, an immutable ledger, and smart contracts. Increase audience engagement and knowledge by dispensing information using Blockchain Approaches To Enhance IoT Data Security IoT Security And Privacy Safeguarding IoT SS. This template helps you present information on three stages. You can also present information on Decentralized System, Immutable Ledger, Smart Contracts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Case Study 2 Improving Connected Home Security IoT Security And Privacy Safeguarding IoT SS
Case Study 2 Improving Connected Home Security IoT Security And Privacy Safeguarding IoT SSThis slide exhibits case study showcasing how AWS solutions helps consumer product company in enhancing connected home products security. It includes elements such as business goals, challenges, IoT solutions, and results. Increase audience engagement and knowledge by dispensing information using Case Study 2 Improving Connected Home Security IoT Security And Privacy Safeguarding IoT SS. This template helps you present information on three stages. You can also present information on Security Solutions, Improved Customer Satisfaction, Provide Innovative using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Categorization Of IoT Architecture Security Concerns IoT Security And Privacy Safeguarding IoT SS
Categorization Of IoT Architecture Security Concerns IoT Security And Privacy Safeguarding IoT SSThis slide consists of security concerns in each IoT architecture layer that helps to deploy a more secure security framework. It includes various security concerns such as insecure web interface, insufficient data authentication, insecure network services, etc. Present the topic in a bit more detail with this Categorization Of IoT Architecture Security Concerns IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Insecure Cloud Interface, Insecure Mobile Interface, Insecure Security Configuration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Processing And Storage System Security Measures IoT Security And Privacy Safeguarding IoT SS
Data Processing And Storage System Security Measures IoT Security And Privacy Safeguarding IoT SSThis slide includes security measures to address security and data privacy concerns of IoT architecture processing layer. It includes three elements such as cloud storage, data center, and web services. Deliver an outstanding presentation on the topic using this Data Processing And Storage System Security Measures IoT Security And Privacy Safeguarding IoT SS. Dispense information and present a thorough explanation of Data Tampering, Strong Authentications, Regular Hardware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Edge Computing Role In Securing IoT Data IoT Security And Privacy Safeguarding IoT SS
Edge Computing Role In Securing IoT Data IoT Security And Privacy Safeguarding IoT SSThis slide showcases the significant role of edge computing in enhancing IoT data security and privacy. It include role such as data filtering and processing, localised threat identification, and reduce attack surface. Introducing Edge Computing Role In Securing IoT Data IoT Security And Privacy Safeguarding IoT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Data Filtering Processing, Reduce Attack Surface, Trusted Entities Interacting, using this template. Grab it now to reap its full benefits.
-
 Emerging Technologies Enhancing IoT Security And IoT Security And Privacy Safeguarding IoT SS
Emerging Technologies Enhancing IoT Security And IoT Security And Privacy Safeguarding IoT SSThis slide includes key technologies integrated with IoT ecosystem that helps to tackle cyberattacks and resolve any other issues. It includes technologies such as blockchain technology, artificial intelligence and machine learning and quantum computing.Present the topic in a bit more detail with this Emerging Technologies Enhancing IoT Security And IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Transactions Securely, Identity Management, Predictive Maintenance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Communication Protocol Security Concerns IoT Security And Privacy Safeguarding IoT SS
IoT Communication Protocol Security Concerns IoT Security And Privacy Safeguarding IoT SSThis slide outlines key communication protocols that facilitate data exchange within IoT devices. It covers communication protocols such as wireless frequencies, Bluetooth, Zigbee, and LPWAN. Present the topic in a bit more detail with this IoT Communication Protocol Security Concerns IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Wearables Devices, Personal Devices, Jamming Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Data Security Vulnerabilities And Privacy Concerns IoT Security And Privacy Safeguarding IoT SS
IoT Data Security Vulnerabilities And Privacy Concerns IoT Security And Privacy Safeguarding IoT SSThis slide includes common IoT security vulnerabilities and risk that helps organization implement security measures. It includes vulnerabilities such as lack of privacy protection, improper device management approach, default settings, weak credentials, etc. Increase audience engagement and knowledge by dispensing information using IoT Data Security Vulnerabilities And Privacy Concerns IoT Security And Privacy Safeguarding IoT SS. This template helps you present information on six stages. You can also present information on Insecure Data Transfer, Weak Credentials, Insecure Default Settings using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IoT Device Management Process To Enhance Security IoT Security And Privacy Safeguarding IoT SS
IoT Device Management Process To Enhance Security IoT Security And Privacy Safeguarding IoT SSThis slide exhibits Internet of things device management process that helps to monitor and manage a large number of devices remotely. It includes the following steps such as registering devices, provisioning, authentication, configuration, maintenance, diagnostics, and retire. Introducing IoT Device Management Process To Enhance Security IoT Security And Privacy Safeguarding IoT SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Robust Authentication, Registering Devices, Device Management, using this template. Grab it now to reap its full benefits.
-
 IoT Ecosystem Gateway Security Challenges IoT Security And Privacy Safeguarding IoT SS
IoT Ecosystem Gateway Security Challenges IoT Security And Privacy Safeguarding IoT SSThis slide exhibits emerging trends in IoT gateway security challenges along with best practices to mitigate such risks effectively. It includes best practices such as utilize hardware tools, regular review and updates, security audits, and authentication implementation,. Introducing IoT Ecosystem Gateway Security Challenges IoT Security And Privacy Safeguarding IoT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Trusted Execution, Platform Module, Vulnerability Assessment, using this template. Grab it now to reap its full benefits.
-
 IoT Security Framework To Safeguard Connected IoT Security And Privacy Safeguarding IoT SS
IoT Security Framework To Safeguard Connected IoT Security And Privacy Safeguarding IoT SSThis slide showcases the IoT security framework that helps play an important role in examining the identities of users and devices. It includes key components such as operator, device edge, device agent, authentication service, device management, etc. Deliver an outstanding presentation on the topic using this IoT Security Framework To Safeguard Connected IoT Security And Privacy Safeguarding IoT SS. Dispense information and present a thorough explanation of Device Provisioning, Operational Resources, Authentication Service using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Principles Of IoT Security Solutions IoT Security And Privacy Safeguarding IoT SS
Key Principles Of IoT Security Solutions IoT Security And Privacy Safeguarding IoT SSThis slide presents an overview of IoT security requirements to protect devices and vulnerable networks from unauthorised access or breaches. It includes data confidentially, availability, integrity, privacy, and authenticity. Increase audience engagement and knowledge by dispensing information using Key Principles Of IoT Security Solutions IoT Security And Privacy Safeguarding IoT SS. This template helps you present information on six stages. You can also present information on Data Confidentiality, Authenticity, Nonrepudiation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overall Impact Of IoT Security Breaches Incidents IoT Security And Privacy Safeguarding IoT SS
Overall Impact Of IoT Security Breaches Incidents IoT Security And Privacy Safeguarding IoT SSThis slide includes IoT security breaches impact on an organisations operational capabilities, hindering the ability to function properly. It includes impacts such as financial burden, operations disruptions, and reputational damage. Deliver an outstanding presentation on the topic using this Overall Impact Of IoT Security Breaches Incidents IoT Security And Privacy Safeguarding IoT SS. Dispense information and present a thorough explanation of Operations Disruptions, Reputational Damage, Financial Burden using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Of Encryption Security Attacks In IoT Security And Privacy Safeguarding IoT SS
Overview Of Encryption Security Attacks In IoT Security And Privacy Safeguarding IoT SSThis slide presents an overview and types of encryption security threats, helpful in protecting data during transmission and storage. It includes various threats such as side channel, cryptanalysis, and man in middle attack. Introducing Overview Of Encryption Security Attacks In IoT Security And Privacy Safeguarding IoT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Attackers Deploy, Possess Either, Sensitive Information, using this template. Grab it now to reap its full benefits.
-
 Overview Of IoT Security And Privacy With Key Benefits IoT Security And Privacy Safeguarding IoT SS
Overview Of IoT Security And Privacy With Key Benefits IoT Security And Privacy Safeguarding IoT SSThis slide presents the benefits of Internet of things devices security and data privacy. It includes benefits such as reduce risk of information leaks, ensures authenticity, reduce financial liabilities, minimise negative impact on business operations. Increase audience engagement and knowledge by dispensing information using Overview Of IoT Security And Privacy With Key Benefits IoT Security And Privacy Safeguarding IoT SS. This template helps you present information on five stages. You can also present information on Confidential Data, Business Operations, Reduce Financial Liabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview Of Network Security Attacks In IoT Environment IoT Security And Privacy Safeguarding IoT SS
Overview Of Network Security Attacks In IoT Environment IoT Security And Privacy Safeguarding IoT SSThis slide presents an overview and types of network security threats, helpful in identifying potential risks in IoT networked environments. It includes attacks such as man in middle attacks, RFIS spoofing, sinkhole attacks, and traffic analysis attacks. Introducing Overview Of Network Security Attacks In IoT Environment IoT Security And Privacy Safeguarding IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Communication Nodes, Mimics Legitimate, Malicious Destination, using this template. Grab it now to reap its full benefits.
-
 Potential Security Vulnerabilities In IoT Ecosystem IoT Security And Privacy Safeguarding IoT SS
Potential Security Vulnerabilities In IoT Ecosystem IoT Security And Privacy Safeguarding IoT SSThis slide highlights security concerns in various areas of internet of things system in order to effectively address and mitigate such risks. It includes various components Of IoT ecosystem such as web and mobile application, cloud, communications, gateways, IoT sensors, etc. Increase audience engagement and knowledge by dispensing information using Potential Security Vulnerabilities In IoT Ecosystem IoT Security And Privacy Safeguarding IoT SS. This template helps you present information on six stages. You can also present information on Insecure Communication, Closed Platforms, Communications using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Real Life Examples Of IoT Security Breaches Incident IoT Security And Privacy Safeguarding IoT SS
Real Life Examples Of IoT Security Breaches Incident IoT Security And Privacy Safeguarding IoT SSThis slide exhibits real life examples of IoT security breaches and their potential consequences including Mirai botnet, Stuxnet, and Jeep Cherokee hack. It includes elements such as security attack, year of occurrence, targeted device, attack method, and impact. Deliver an outstanding presentation on the topic using this Real Life Examples Of IoT Security Breaches Incident IoT Security And Privacy Safeguarding IoT SS. Dispense information and present a thorough explanation of Exploited Default, Extensive Internet, Disrupted Industrial Operations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Attacks At Various Stages Of IoT Process IoT Security And Privacy Safeguarding IoT SS
Security Attacks At Various Stages Of IoT Process IoT Security And Privacy Safeguarding IoT SSThis slide showcases various types of attacks categorised for IoT data processes. It includes phases such as data perception, data storage, intelligent processing, data transmission, and end to end delivery. Present the topic in a bit more detail with this Security Attacks At Various Stages Of IoT Process IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Intelligent Processing, Data Transmission, Transmission Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Concerns And Solutions For Interconnected IoT Security And Privacy Safeguarding IoT SS
Security Concerns And Solutions For Interconnected IoT Security And Privacy Safeguarding IoT SSThis slide exhibits security solution to safeguard interconnected devices against security attacks in order to enhance overall productivity. It includes devices such as smart cameras, RFID tags, Smart GPS systems, and smart home devices, smart meters. Deliver an outstanding presentation on the topic using this Security Concerns And Solutions For Interconnected IoT Security And Privacy Safeguarding IoT SS. Dispense information and present a thorough explanation of Manipulating Video Streams, Creating Unauthorized, Network Segmentation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Standards And Framework For IoT Risk Mitigation IoT Security And Privacy Safeguarding IoT SS
Security Standards And Framework For IoT Risk Mitigation IoT Security And Privacy Safeguarding IoT SSThis side presents IoT security standards and framework that help organisation for risk mitigation. It incudes security standards such as ISO 27000 series, NIST SP 800 53, and NIST CSF controls. Introducing Security Standards And Framework For IoT Risk Mitigation IoT Security And Privacy Safeguarding IoT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on International Organization, Information Security Issues, Management System, using this template. Grab it now to reap its full benefits.
-
 Types Of Security Attacks In IoT Ecosystem IoT Security And Privacy Safeguarding IoT SS
Types Of Security Attacks In IoT Ecosystem IoT Security And Privacy Safeguarding IoT SSThis slide presents various types of security attacks that can impact IoT systems and devices, which might cause disruption in operations. It includes security attacks such as physical attacks, software attacks, network attacks, and encryption attacks. Deliver an outstanding presentation on the topic using this Types Of Security Attacks In IoT Ecosystem IoT Security And Privacy Safeguarding IoT SS. Dispense information and present a thorough explanation of Software Attacks, Network Attacks, Encryption Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Understanding Physical Security Attacks In IoT Landscape IoT Security And Privacy Safeguarding IoT SS
Understanding Physical Security Attacks In IoT Landscape IoT Security And Privacy Safeguarding IoT SSThis slide presents an overview and types of physical security threats, helpful in identifying areas for strict regulation. It includes malicious code injection, malicious node injection, node tampering, and RF interference on radio frequency identification. Introducing Understanding Physical Security Attacks In IoT Landscape IoT Security And Privacy Safeguarding IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Malicious Code Injection, Device Tampering, Physical Damage , using this template. Grab it now to reap its full benefits.
-
 Understanding Software Security Attacks In IoT Landscape IoT Security And Privacy Safeguarding IoT SS
Understanding Software Security Attacks In IoT Landscape IoT Security And Privacy Safeguarding IoT SSThis slide presents an overview and types of software security threats, helpful in identifying potential areas of vulnerabilities. It includes types such as denial of service attacks, phishing attacks, malicious scripts, and worms and spyware.Increase audience engagement and knowledge by dispensing information using Understanding Software Security Attacks In IoT Landscape IoT Security And Privacy Safeguarding IoT SS. This template helps you present information on four stages. You can also present information on Phishing Attacks, Malicious Scripts, Injecting Malicious using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comparison Between Secure Web Internet Gateway Security IT
Comparison Between Secure Web Internet Gateway Security ITThis slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. Present the topic in a bit more detail with this Comparison Between Secure Web Internet Gateway Security IT. Use it as a tool for discussion and navigation on Parameter, Scope, Deployment, Architecture, Features, Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
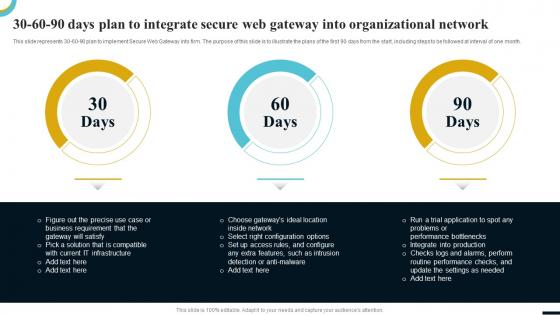 Internet Gateway Security IT 30 60 90 Days Plan To Integrate Secure Web
Internet Gateway Security IT 30 60 90 Days Plan To Integrate Secure WebThis slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Introducing Internet Gateway Security IT 30 60 90 Days Plan To Integrate Secure Web to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on 30 60 90 Days Plan, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Applications Of Secure Web Gateway In Various
Internet Gateway Security IT Applications Of Secure Web Gateway In VariousThis slide talks about how Secure Web Gateway is used in several industrial domains. The purpose of this slide is to explain how SWG is used in different sectors. The industries covered are financial services, healthcare, education, manufacturing, etc. Introducing Internet Gateway Security IT Applications Of Secure Web Gateway In Various to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Financial Services, Healthcare, Education, Manufacturing, Government, Retail, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Architecture Of Citrix Secure Web Gateway
Internet Gateway Security IT Architecture Of Citrix Secure Web GatewayThis slide represents the Secure Web Gateway solution provided by Citrix. The purpose of this slide is to demonstrate the architecture of Citrixs SWG solution. The key components included are users, firewall, internet, logstream, SWG appliance, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Architecture Of Citrix Secure Web Gateway. Use it as a tool for discussion and navigation on Citrix ADC Appliance, URL Filtering, Policies, Citrix Application Delivery Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Before Vs After Implementing Secure Web
Internet Gateway Security IT Before Vs After Implementing Secure WebThis slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Before Vs After Implementing Secure Web. Use it as a tool for discussion and navigation on Security, Visibility, Compliance, Productivity, Costs. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Best Practices For Secure Web Gateway
Internet Gateway Security IT Best Practices For Secure Web GatewayThis slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc. Introducing Internet Gateway Security IT Best Practices For Secure Web Gateway to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Perform A Risk Assessment, Deploy Safe Setups, Monitor And Analyse Traffic, Keep Software Up To Date, Provide User Awareness Training, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Checklist To Implement Secure Web Gateway
Internet Gateway Security IT Checklist To Implement Secure Web GatewayThis slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Present the topic in a bit more detail with this Internet Gateway Security IT Checklist To Implement Secure Web Gateway. Use it as a tool for discussion and navigation on Determine Use Case, Select Best Solution, Plan Deployment, Configure Solution, Test And Improve, Roll Out And Monitor. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Comparison Between Secure Web Gateway
Internet Gateway Security IT Comparison Between Secure Web GatewayThis slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment. Present the topic in a bit more detail with this Internet Gateway Security IT Comparison Between Secure Web Gateway. Use it as a tool for discussion and navigation on Function, Scope, Granularity, Features, Deployment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Different Types Of Secure Web Gateway
Internet Gateway Security IT Different Types Of Secure Web GatewayThis slide demonstrates the various kinds of SWG deployments. The purpose of this slide is to explain the different types of Secure Web Gateway deployment methods such as on-premises deployment, cloud-based deployment and hybrid deployment. Introducing Internet Gateway Security IT Different Types Of Secure Web Gateway to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on On Premises Deployment, CLOUD Based Deployment, Hybrid Deployment, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Estimated Budget Of Secure Web Gateway
Internet Gateway Security IT Estimated Budget Of Secure Web GatewayThis slide represents the budget of integrating Secure Web Gateway in organization. The purpose of this slide is to showcase the estimated and actual cost for installing SWG. These include hardware and software, maintenance and support, training, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Estimated Budget Of Secure Web Gateway. Use it as a tool for discussion and navigation on Hardware And Software, Maintenance And Support, Training, Third Party Services, Deployment Team. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Features Of Next Generation Secure Web
Internet Gateway Security IT Features Of Next Generation Secure WebThis slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc. Introducing Internet Gateway Security IT Features Of Next Generation Secure Web to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Based Architecture, More Visibility And Control, Advanced Threat Intelligence, Multi-Factor Authentication, Integrated Data Loss Prevention, Zero Trust Security, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Future Of Secure Web Gateway Technology
Internet Gateway Security IT Future Of Secure Web Gateway TechnologyThis slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. Introducing Internet Gateway Security IT Future Of Secure Web Gateway Technology to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Sales Are Predicted, SWG Market Anticipated, Security Solution, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Impact Of Secure Web Gateway On Application
Internet Gateway Security IT Impact Of Secure Web Gateway On ApplicationThis slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Impact Of Secure Web Gateway On Application. Use it as a tool for discussion and navigation on Parameters, Content Filtering, Policy Enforcement, Data Loss Prevention. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Importance Of Secure Web Gateway For Businesses
Internet Gateway Security IT Importance Of Secure Web Gateway For BusinessesThis slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc. Introducing Internet Gateway Security IT Importance Of Secure Web Gateway For Businesses to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Client Connector, Data Center, Iot Headquarters, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Introduction To Next Generation Secure Web
Internet Gateway Security IT Introduction To Next Generation Secure WebThis slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications. Introducing Internet Gateway Security IT Introduction To Next Generation Secure Web to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Applications, Services, Risks Enabled, Vulnerability, Public Resources, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Introduction To Secure Web Gateway Technology
Internet Gateway Security IT Introduction To Secure Web Gateway TechnologyThis slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Introducing Internet Gateway Security IT Introduction To Secure Web Gateway Technology to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Traffic Inspection, Application Control, Website Content Inspection, Data Loss Prevention, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Key Benefits Of Using Secure Web Gateway
Internet Gateway Security IT Key Benefits Of Using Secure Web GatewayThis slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc. Introducing Internet Gateway Security IT Key Benefits Of Using Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Improved Security, Increased Productivity, Reduced Risk Of Data Loss, Compliance, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Key Secure Web Gateway Solution Providers
Internet Gateway Security IT Key Secure Web Gateway Solution ProvidersThis slide outlines the popular service providers of Secure Wen Gateway. The purpose of this slide is to demonstrate the services provided by various SWG solutions such as Cisco, Symantec, McAfee, Zscaler, Barracuda Networks, Fortinet, etc. Introducing Internet Gateway Security IT Key Secure Web Gateway Solution Providers to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Cisco, Symantec, Forcepoint, Fortinet, Barracuda Networks, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Methods To Implement Security Policies
Internet Gateway Security IT Methods To Implement Security PoliciesThis slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Methods To Implement Security Policies. Use it as a tool for discussion and navigation on Data Loss Prevention, Encrypted Traffic Examination, Protocol Support, Constant Security Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Prominent Users Of Secure Web Gateway
Internet Gateway Security IT Prominent Users Of Secure Web GatewayThis slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc. Introducing Internet Gateway Security IT Prominent Users Of Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on IT Security Experts, Network Administrators, Compliance Officers, HR Managers, Business Executives, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Reasons Behind Need For Secure Web Gateway
Internet Gateway Security IT Reasons Behind Need For Secure Web GatewayThis slide discusses the requirement of Secure Web Gateway in protecting organizations from various cyber crimes. The reasons behind need of Secure Web Gateway are protection against web-based threats, enforce security policies, controlled access, etc. Introducing Internet Gateway Security IT Reasons Behind Need For Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Rise In Web-Based Threats, Non-Compliance To Security Policies, Need Of Access Control, Web Traffic Monitoring, Remote Worker Protection, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Relationship Between Secure Access Service
Internet Gateway Security IT Relationship Between Secure Access ServiceThis slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc. Introducing Internet Gateway Security IT Relationship Between Secure Access Service to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Administration Of Microservices, Distributed Environment, Visibility Control Over Traffic Passing, Cloud-Native Application, using this template. Grab it now to reap its full benefits.
-
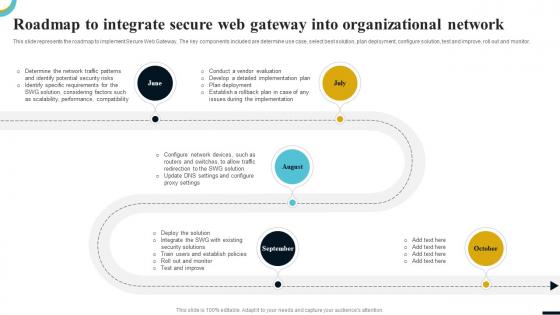 Internet Gateway Security IT Roadmap To Integrate Secure Web Gateway
Internet Gateway Security IT Roadmap To Integrate Secure Web GatewayThis slide represents the roadmap to implement Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Introducing Internet Gateway Security IT Roadmap To Integrate Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Scalability, Performance, Compatibility, Implementation, Plan Deployment, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Architecture And Working
Internet Gateway Security IT Secure Web Gateway Architecture And WorkingThis slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. Introducing Internet Gateway Security IT Secure Web Gateway Architecture And Working to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Policy Enforcement, Malware Detection, Web Proxy, Public Internet, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Challenges And Solutions
Internet Gateway Security IT Secure Web Gateway Challenges And SolutionsThis slide outlines the limitations of Secure Web Gateway such as increasingly sophisticated threats, encrypted traffic, cloud-based applications and mobile devices. This purpose of this slide is to explain the possible solutions to these challenges. Present the topic in a bit more detail with this Internet Gateway Security IT Secure Web Gateway Challenges And Solutions. Use it as a tool for discussion and navigation on Increasingly, Sophisticated Threats, Encrypted Traffic, Cloud-Based Applications, Mobile Devices. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Secure Web Gateway For Remote And On Site
Internet Gateway Security IT Secure Web Gateway For Remote And On SiteThis slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees. Introducing Internet Gateway Security IT Secure Web Gateway For Remote And On Site to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Remote Users, Internet, Cloud Based Secure Web Gateway, Secure Web Gateway, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Implementation
Internet Gateway Security IT Secure Web Gateway ImplementationThis slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Introducing Internet Gateway Security IT Secure Web Gateway Implementation to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Internet Gateway, Internet Connected Network Site, Administrative Costs, using this template. Grab it now to reap its full benefits.





