Powerpoint Templates and Google slides for Security Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Security Orchestration Automation Security Automation Integrates Tools Systems And Processes
Security Orchestration Automation Security Automation Integrates Tools Systems And ProcessesThis slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Deliver an outstanding presentation on the topic using this Security Orchestration Automation Security Automation Integrates Tools Systems And Processes. Dispense information and present a thorough explanation of Security Automation, Robotic Process, Security Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Orchestration Automation And Response Different Security Automation Tools With Pros And Cons
Security Orchestration Automation And Response Different Security Automation Tools With Pros And ConsThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Introducing Security Orchestration Automation And Response Different Security Automation Tools With Pros And Cons to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Security Automation, Integrates Tools, Systems And Processes, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Traditional Security In Powerpoint And Google Slides Cpb
Cloud Security Traditional Security In Powerpoint And Google Slides CpbPresenting Cloud Security Traditional Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cloud Security Traditional Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Comparative Assessment Of Security Awareness Online Preventing Data Breaches Through Cyber Security
Comparative Assessment Of Security Awareness Online Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. Present the topic in a bit more detail with this Comparative Assessment Of Security Awareness Online Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Course Description, Instructor, Rating. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparison Of Various Security Awareness Training Software Preventing Data Breaches Through Cyber Security
Comparison Of Various Security Awareness Training Software Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Deliver an outstanding presentation on the topic using this Comparison Of Various Security Awareness Training Software Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Security Reporting, Phishing Simulations, Deployment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Awareness Trends In 2023 Preventing Data Breaches Through Cyber Security
Cyber Security Awareness Trends In 2023 Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2023. increase in malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. Increase audience engagement and knowledge by dispensing information using Cyber Security Awareness Trends In 2023 Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Mobile Malware Attack, Get More Advanced, Ransomware Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Evaluating It System Security Using Swot Analysis Preventing Data Breaches Through Cyber Security
Evaluating It System Security Using Swot Analysis Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Increase audience engagement and knowledge by dispensing information using Evaluating It System Security Using Swot Analysis Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Strength, Threats, Weaknesses using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Functional Chart Of Cyber Security Team Preventing Data Breaches Through Cyber Security
Functional Chart Of Cyber Security Team Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Deliver an outstanding presentation on the topic using this Functional Chart Of Cyber Security Team Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Cyber Risk Manger, Security Training, Cyber Business Liaison using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 How Much Employees Are Aware Of Cyber Security Preventing Data Breaches Through Cyber Security
How Much Employees Are Aware Of Cyber Security Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass fail rate of employees who received the security awareness training and fail rate by age. Present the topic in a bit more detail with this How Much Employees Are Aware Of Cyber Security Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Security Training, Assessment Test, Employees. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Cyber Security Breach General Consequences Preventing Data Breaches Through Cyber Security
Impact Of Cyber Security Breach General Consequences Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Introducing Impact Of Cyber Security Breach General Consequences Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reputational Damage, Theft Events, Monetary Penalty, using this template. Grab it now to reap its full benefits.
-
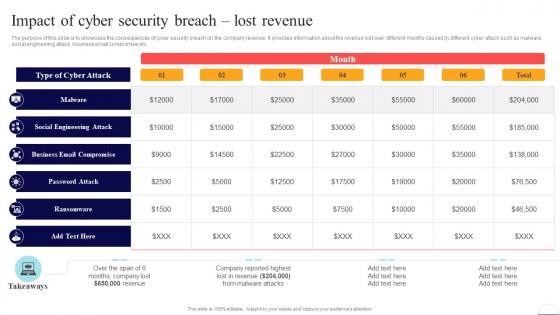 Impact Of Cyber Security Breach Lost Revenue Preventing Data Breaches Through Cyber Security
Impact Of Cyber Security Breach Lost Revenue Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. Deliver an outstanding presentation on the topic using this Impact Of Cyber Security Breach Lost Revenue Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Malware, Social Engineering Attack, Business Email Compromise using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Benefits Of Cyber Security Awareness Training Preventing Data Breaches Through Cyber Security
Key Benefits Of Cyber Security Awareness Training Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Introducing Key Benefits Of Cyber Security Awareness Training Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Drive Awareness, Prevent Downtime, Reduce Threat, using this template. Grab it now to reap its full benefits.
-
 Key Stakeholders Of Cyber Security Awareness Training Preventing Data Breaches Through Cyber Security
Key Stakeholders Of Cyber Security Awareness Training Preventing Data Breaches Through Cyber SecurityIncrease audience engagement and knowledge by dispensing information using Key Stakeholders Of Cyber Security Awareness Training Preventing Data Breaches Through Cyber Security. This template helps you present information on three stages. You can also present information on Drive Awareness, Prevent Downtime, Reduce Threat using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Major Statistics Of Cyber Security Awareness Preventing Data Breaches Through Cyber Security
Major Statistics Of Cyber Security Awareness Preventing Data Breaches Through Cyber SecurityIntroducing Major Statistics Of Cyber Security Awareness Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Browser, Employees, Password Manager, using this template. Grab it now to reap its full benefits.
-
 Measuring Security Awareness Campaign Results With KPIS Preventing Data Breaches Through Cyber Security
Measuring Security Awareness Campaign Results With KPIS Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self reported incidents, security breaches, cost of security breach and campaign participation rate. Deliver an outstanding presentation on the topic using this Measuring Security Awareness Campaign Results With KPIS Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Phishing Rate, Security Breaches, Campaign Participation Rate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Need For Cyber Security Awareness Training Preventing Data Breaches Through Cyber Security
Need For Cyber Security Awareness Training Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Increase audience engagement and knowledge by dispensing information using Need For Cyber Security Awareness Training Preventing Data Breaches Through Cyber Security. This template helps you present information on five stages. You can also present information on Data Breach, Technological, Customers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview Of Cyber Security Awareness Course Preventing Data Breaches Through Cyber Security
Overview Of Cyber Security Awareness Course Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. Introducing Overview Of Cyber Security Awareness Course Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Course Content, Attendees, Learning Outcome, using this template. Grab it now to reap its full benefits.
-
 Pricing Plan Of Security Awareness Packages Preventing Data Breaches Through Cyber Security
Pricing Plan Of Security Awareness Packages Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Deliver an outstanding presentation on the topic using this Pricing Plan Of Security Awareness Packages Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Employees, Security, Awareness Packages using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Recognizing The Cyber Security Gaps Faced By Key Preventing Data Breaches Through Cyber Security
Recognizing The Cyber Security Gaps Faced By Key Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto jacking, IoT based attack, malware etc. Present the topic in a bit more detail with this Recognizing The Cyber Security Gaps Faced By Key Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Social Engineering Attack, Business Email Comprise, Iot Based Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Roles And Responsibilities Of Cyber Security Team Preventing Data Breaches Through Cyber Security
Roles And Responsibilities Of Cyber Security Team Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Introducing Roles And Responsibilities Of Cyber Security Team Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Risk Committee, Cyber Risk Manager, Security Operations Manager, using this template. Grab it now to reap its full benefits.
-
 Running Cyber Security Awareness Campaign For Employees Preventing Data Breaches Through Cyber Security
Running Cyber Security Awareness Campaign For Employees Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered. Increase audience engagement and knowledge by dispensing information using Running Cyber Security Awareness Campaign For Employees Preventing Data Breaches Through Cyber Security. This template helps you present information on two stages. You can also present information on Data, Employees, Security Awareness using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Statistics Highlighting Lack Of Cyber Security Awareness Preventing Data Breaches Through Cyber Security
Statistics Highlighting Lack Of Cyber Security Awareness Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc. Introducing Statistics Highlighting Lack Of Cyber Security Awareness Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Employees, Confidential Data, Email, using this template. Grab it now to reap its full benefits.
-
 Strategies We Will Implement To Make Security Awareness Preventing Data Breaches Through Cyber Security
Strategies We Will Implement To Make Security Awareness Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high quality content and variety. Increase audience engagement and knowledge by dispensing information using Strategies We Will Implement To Make Security Awareness Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Gamification, Personalization, High Quality Content using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Schedule Matrix To Increase Data Security
Cyber Security Schedule Matrix To Increase Data SecurityThis slide signifies the IT schedule table to enhance data protection. It covers information about weekly schedule of activities to be conducted like configure technical security, conduct penetration test, install firewalls, conduct formal training.Presenting our well structured Cyber Security Schedule Matrix To Increase Data Security. The topics discussed in this slide are Conduct Stimulated, Configuring Technical, Unnatural Activities. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Secure Type Firewall Network Security In Powerpoint And Google Slides Cpb
Secure Type Firewall Network Security In Powerpoint And Google Slides CpbPresenting our Secure Type Firewall Network Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Secure Type Firewall Network Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber Security Policy Overview Of Network Security Policy For Workers
Cyber Security Policy Overview Of Network Security Policy For WorkersThis slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Policy Overview Of Network Security Policy For Workers. This template helps you present information on six stages. You can also present information on Overview, Information, Confidentiality using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Policy Security Awareness And Training Policy Overview
Cyber Security Policy Security Awareness And Training Policy OverviewThis slide represents the security awareness and training policy. It covers that the training program should be designed by management, and employees will sign a confidentiality agreement after getting the training. Increase audience engagement and knowledge by dispensing information using Cyber Security Policy Security Awareness And Training Policy Overview. This template helps you present information on six stages. You can also present information on Awareness, Overview, Business using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 F982 Cyber Security Policy Information Security Policy For Employees
F982 Cyber Security Policy Information Security Policy For EmployeesThis slide depicts the information security policy that critical topics covered in this policy. It also covers the reasons for frequent changes in the policy. Present the topic in a bit more detail with this F982 Cyber Security Policy Information Security Policy For Employees. Use it as a tool for discussion and navigation on Information, Infrastructure, Responsibility. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing Role Of Chief Security Officer At Workplace Strategic Organizational Security Plan
Addressing Role Of Chief Security Officer At Workplace Strategic Organizational Security PlanThis slide provides information regarding role of chief security officer at workplace and determine their key priorities in terms of day to day operations, security, compliance, innovation, etc. Present the topic in a bit more detail with this Addressing Role Of Chief Security Officer At Workplace Strategic Organizational Security Plan. Use it as a tool for discussion and navigation on Compliance, Innovation, Security . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Overview Of Established Security Centre Strategic Organizational Security Plan
Determine Overview Of Established Security Centre Strategic Organizational Security PlanThis slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver an outstanding presentation on the topic using this Determine Overview Of Established Security Centre Strategic Organizational Security Plan. Dispense information and present a thorough explanation of Functional Business Units, Management Staff, Steering Committee using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Role Of Security Centre In Firm Strategic Organizational Security Plan
Determine Role Of Security Centre In Firm Strategic Organizational Security PlanThis slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security center implementation. Present the topic in a bit more detail with this Determine Role Of Security Centre In Firm Strategic Organizational Security Plan. Use it as a tool for discussion and navigation on Before Security, After Security, Towards Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Security Policy Framework At Workplace Strategic Organizational Security Plan
Determine Security Policy Framework At Workplace Strategic Organizational Security PlanThis slide provides information about security policy framework at workplace in terms of management, operational procedures, information, personnel, training, crisis management, etc. Deliver an outstanding presentation on the topic using this Determine Security Policy Framework At Workplace Strategic Organizational Security Plan. Dispense information and present a thorough explanation of Company Policies, Management, Operational Procedures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Facilities Offered By Implementation Of Security Centre Strategic Organizational Security Plan
Facilities Offered By Implementation Of Security Centre Strategic Organizational Security PlanThis slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Introducing Facilities Offered By Implementation Of Security Centre Strategic Organizational Security Plan to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Investigations By Hr, Employees, Phishing Detection, using this template. Grab it now to reap its full benefits.
-
 Introducing Security At Workplace To Ensure Assets Safety Strategic Organizational Security Plan
Introducing Security At Workplace To Ensure Assets Safety Strategic Organizational Security PlanThis slide provides information about introducing security at workplace in order to ensure assets safety and details regarding security mission statement and objectives. Increase audience engagement and knowledge by dispensing information using Introducing Security At Workplace To Ensure Assets Safety Strategic Organizational Security Plan. This template helps you present information on four stages. You can also present information on Security Mission Statement, Strategic Security Objectives, Organizational Strategy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents For Strategic Organizational Security Plan Strategic Organizational Security Plan
Table Of Contents For Strategic Organizational Security Plan Strategic Organizational Security PlanIntroducing Table Of Contents For Strategic Organizational Security Plan Strategic Organizational Security Plan to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Dashboard Assessment, Impact Assessment, Budget Assessment , using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Guid Cyber Security Incident Management Checklist During An Incident
Cyber Security Attacks Response Guid Cyber Security Incident Management Checklist During An IncidentThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management during the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using Cyber Security Attacks Response Guid Cyber Security Incident Management Checklist During An Incident. This template helps you present information on one stages. You can also present information on Cyber Security, Incident Management, Checklist During An Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comparative Analysis Of Cyber Security Incident Mitigation Development And Implementation Of Security
Comparative Analysis Of Cyber Security Incident Mitigation Development And Implementation Of SecurityThis slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Deliver an outstanding presentation on the topic using this Comparative Analysis Of Cyber Security Incident Mitigation Development And Implementation Of Security. Dispense information and present a thorough explanation of Incident Tool, User Rating, Price using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Crisis Management Action Plan Timeline Development And Implementation Of Security
Cyber Security Crisis Management Action Plan Timeline Development And Implementation Of SecurityThis slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Deliver an outstanding presentation on the topic using this Cyber Security Crisis Management Action Plan Timeline Development And Implementation Of Security. Dispense information and present a thorough explanation of Incident Response, Business Continuity, Review Recovery using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Event And Incident Flow Diagram Development And Implementation Of Security
Cyber Security Event And Incident Flow Diagram Development And Implementation Of SecurityThis slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Present the topic in a bit more detail with this Cyber Security Event And Incident Flow Diagram Development And Implementation Of Security. Use it as a tool for discussion and navigation on Information Collection, Assessment, Alarm Or Anomaly. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Communication Strategy Development And Implementation Of Security
Cyber Security Incident Communication Strategy Development And Implementation Of SecurityThis slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. Deliver an outstanding presentation on the topic using this Cyber Security Incident Communication Strategy Development And Implementation Of Security. Dispense information and present a thorough explanation of Senior Management, Impacted Business Managers, Employees using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incident Handler Contact Information Development And Implementation Of Security
Cyber Security Incident Handler Contact Information Development And Implementation Of SecurityThis slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. Introducing Cyber Security Incident Handler Contact Information Development And Implementation Of Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Incident, Response Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Handling Checklist Development And Implementation Of Security
Cyber Security Incident Handling Checklist Development And Implementation Of SecurityThis slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post incident activity. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Handling Checklist Development And Implementation Of Security. This template helps you present information on three stages. You can also present information on Detection And Analysis, Prioritize Incident Handling, Incident Containment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Management Checklist After Development And Implementation Of Security
Cyber Security Incident Management Checklist After Development And Implementation Of SecurityThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Introducing Cyber Security Incident Management Checklist After Development And Implementation Of Security to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Review Performance, Incident Response Team, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Management Checklist Before Development And Implementation Of Security
Cyber Security Incident Management Checklist Before Development And Implementation Of SecurityThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management before the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Checklist Before Development And Implementation Of Security. This template helps you present information on one stages. You can also present information on Develop Effective And Efficient, Incident Response Team using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Management Checklist During Development And Implementation Of Security
Cyber Security Incident Management Checklist During Development And Implementation Of SecurityThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management during the occurrence of the incident. Introducing Cyber Security Incident Management Checklist During Development And Implementation Of Security to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Triage Current Problems, Communicate, Executive Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Management Team Roles Development And Implementation Of Security
Cyber Security Incident Management Team Roles Development And Implementation Of SecurityThis slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. Present the topic in a bit more detail with this Cyber Security Incident Management Team Roles Development And Implementation Of Security. Use it as a tool for discussion and navigation on Incident Management, Business Decision Capability, Network Management Capabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Management Team Structure Development And Implementation Of Security
Cyber Security Incident Management Team Structure Development And Implementation Of SecurityThis slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Team Structure Development And Implementation Of Security. This template helps you present information on one stages. You can also present information on Human Resources, Outside Counsel, Forensics using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Response Lifecycle Development And Implementation Of Security Incident Management
Cyber Security Incident Response Lifecycle Development And Implementation Of Security Incident ManagementThis slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Introducing Cyber Security Incident Response Lifecycle Development And Implementation Of Security Incident Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Preparation, Detection Analysis, Containment Eradication Recovery, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Response Plan Timeline Development And Implementation Of Security Incident
Cyber Security Incident Response Plan Timeline Development And Implementation Of Security IncidentThis slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Present the topic in a bit more detail with this Cyber Security Incident Response Plan Timeline Development And Implementation Of Security Incident. Use it as a tool for discussion and navigation on Verification Of Incident, Cyber Incident Report, Response Arrives. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Response Process Flow Chart Development And Implementation Of Security
Cyber Security Incident Response Process Flow Chart Development And Implementation Of SecurityThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Deliver an outstanding presentation on the topic using this Cyber Security Incident Response Process Flow Chart Development And Implementation Of Security. Dispense information and present a thorough explanation of Data Collection And Preservation, Perform Technical Analysis, Incident Declaration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incidents Follow Up Report Development And Implementation Of Security Incident Management
Cyber Security Incidents Follow Up Report Development And Implementation Of Security Incident ManagementThis slide represents the follow up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. Present the topic in a bit more detail with this Cyber Security Incidents Follow Up Report Development And Implementation Of Security Incident Management. Use it as a tool for discussion and navigation on Confidential Information Customers, Theft Confidential Information, Organizational Projects. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security Incident
Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security IncidentThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security Incident. Use it as a tool for discussion and navigation on Consequences, Vulnerability, Risk. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Threats Detection Techniques Development And Implementation Of Security Incident Management
Cyber Security Threats Detection Techniques Development And Implementation Of Security Incident ManagementThis slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Present the topic in a bit more detail with this Cyber Security Threats Detection Techniques Development And Implementation Of Security Incident Management. Use it as a tool for discussion and navigation on Intruder Traps, Attacker And User Behavior Analytics, Threat Intelligence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Implementing Cyber Security Incident Management Development And Implementation Of Security
Impact Of Implementing Cyber Security Incident Management Development And Implementation Of SecurityThis slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Present the topic in a bit more detail with this Impact Of Implementing Cyber Security Incident Management Development And Implementation Of Security. Use it as a tool for discussion and navigation on Results, Post Implementation, Pre Implementation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Parameters To Select Cyber Security Containment Strategy Development And Implementation Of Security
Key Parameters To Select Cyber Security Containment Strategy Development And Implementation Of SecurityThis slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Introducing Key Parameters To Select Cyber Security Containment Strategy Development And Implementation Of Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Organizational Resources, Potential Damages, Strategy, using this template. Grab it now to reap its full benefits.
-
 Strategies To Analyze Cyber Security Incidents Development And Implementation Of Security Incident Management
Strategies To Analyze Cyber Security Incidents Development And Implementation Of Security Incident ManagementThis slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Increase audience engagement and knowledge by dispensing information using Strategies To Analyze Cyber Security Incidents Development And Implementation Of Security Incident Management. This template helps you present information on two stages. You can also present information on Profile Network And Systems, Understand Normal Behaviors, Perform Event Correlation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various Cyber Security Incidents Detected By It Department Development And Implementation Of Security
Various Cyber Security Incidents Detected By It Department Development And Implementation Of SecurityThis slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Increase audience engagement and knowledge by dispensing information using Various Cyber Security Incidents Detected By It Department Development And Implementation Of Security. This template helps you present information on five stages. You can also present information on Insider Threat, Phishing Attack, Malware Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ways To Detect Cyber Security Incidents Development And Implementation Of Security Incident Management
Ways To Detect Cyber Security Incidents Development And Implementation Of Security Incident ManagementThis slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Introducing Ways To Detect Cyber Security Incidents Development And Implementation Of Security Incident Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Privileged User Accounts, Unusual Behavior, Network Traffic, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Comparative Analysis Of Cyber Security Incident Mitigation Software
Cyber Security Attacks Response Comparative Analysis Of Cyber Security Incident Mitigation SoftwareThis slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Comparative Analysis Of Cyber Security Incident Mitigation Software. Use it as a tool for discussion and navigation on Comparative Analysis, Cyber Security Incident, Mitigation Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Cyber Security Incident Management Team Roles And Responsibilities
Cyber Security Attacks Response Cyber Security Incident Management Team Roles And ResponsibilitiesPresent the topic in a bit more detail with this Cyber Security Attacks Response Cyber Security Incident Management Team Roles And Responsibilities. Use it as a tool for discussion and navigation on Cyber Security Incident, Management Team, Roles And Responsibilities. This template is free to edit as deemed fit for your organization. Therefore download it now.





