Powerpoint Templates and Google slides for Security Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Measure Security Automation Metrics For Operations Efficiency Enabling Automation In Cyber Security Operations
Measure Security Automation Metrics For Operations Efficiency Enabling Automation In Cyber Security OperationsThis slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Present the topic in a bit more detail with this Measure Security Automation Metrics For Operations Efficiency Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Automation, Operations, Efficiency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Right Time To Add Automation In Security Enabling Automation In Cyber Security Operations
Right Time To Add Automation In Security Enabling Automation In Cyber Security OperationsThis slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. Present the topic in a bit more detail with this Right Time To Add Automation In Security Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Resolution, Automation, Human Insights. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations
Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security OperationsThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Present the topic in a bit more detail with this Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Automation, Integrates, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Stages With Maturity Level Enabling Automation In Cyber Security Operations
Security Automation Stages With Maturity Level Enabling Automation In Cyber Security OperationsThis slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Deliver an outstanding presentation on the topic using this Security Automation Stages With Maturity Level Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Security Automation, Services, Programmatic Workflow using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
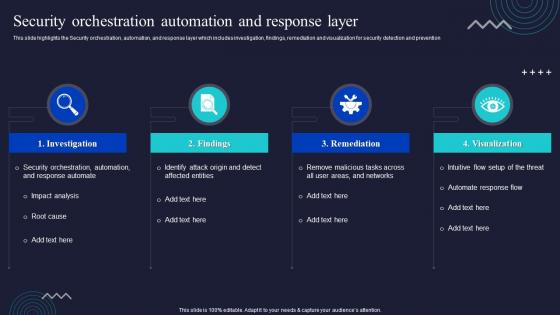 Security Orchestration Automation And Response Layer Enabling Automation In Cyber Security Operations
Security Orchestration Automation And Response Layer Enabling Automation In Cyber Security OperationsThis slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention Deliver an outstanding presentation on the topic using this Security Orchestration Automation And Response Layer Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Investigation, Remediation, Visualization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Processes That Cant Be Automated Enabling Automation In Cyber Security Operations
Security Processes That Cant Be Automated Enabling Automation In Cyber Security OperationsThe following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Increase audience engagement and knowledge by dispensing information using Security Processes That Cant Be Automated Enabling Automation In Cyber Security Operations. This template helps you present information on three stages. You can also present information on Threat Modeling, Penetration Testing, Bug Bounty using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Unified Platform Integration For Security Automation Enabling Automation In Cyber Security Operations
Unified Platform Integration For Security Automation Enabling Automation In Cyber Security OperationsThis slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. Present the topic in a bit more detail with this Unified Platform Integration For Security Automation Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Automation, Access Management, Platform Integration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Why To Automate The It Security Process Enabling Automation In Cyber Security Operations
Why To Automate The It Security Process Enabling Automation In Cyber Security OperationsThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Increase audience engagement and knowledge by dispensing information using Why To Automate The It Security Process Enabling Automation In Cyber Security Operations. This template helps you present information on five stages. You can also present information on Better Threat Detection, Faster Containment, Improve Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 F651 Security Automation In Information Technology Security Automation Architecture With Key Elements
F651 Security Automation In Information Technology Security Automation Architecture With Key ElementsThis slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Present the topic in a bit more detail with this F651 Security Automation In Information Technology Security Automation Architecture With Key Elements. Use it as a tool for discussion and navigation on Security, Automation, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F653 Security Automation In Information Technology Security Automation Stages With Maturity Level
F653 Security Automation In Information Technology Security Automation Stages With Maturity LevelThis slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Present the topic in a bit more detail with this F653 Security Automation In Information Technology Security Automation Stages With Maturity Level. Use it as a tool for discussion and navigation on Systematic Stage, Institutionalized Stage, Opportunistic Stage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Architecture With Key Elements Enabling Automation In Cyber Security Operations
Security Automation Architecture With Key Elements Enabling Automation In Cyber Security OperationsThis slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Deliver an outstanding presentation on the topic using this Security Automation Architecture With Key Elements Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Automation, Architecture, Sources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Security Awareness Online Courses Conducting Security Awareness
Comparative Assessment Of Security Awareness Online Courses Conducting Security AwarenessThe purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. Present the topic in a bit more detail with this Comparative Assessment Of Security Awareness Online Courses Conducting Security Awareness. Use it as a tool for discussion and navigation on Key Features, Course Description, Instructor. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparison Of Various Security Awareness Training Software Conducting Security Awareness
Comparison Of Various Security Awareness Training Software Conducting Security AwarenessThe purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Deliver an outstanding presentation on the topic using this Comparison Of Various Security Awareness Training Software Conducting Security Awareness. Dispense information and present a thorough explanation of Key Features, Phishing Simulations, Security Reporting using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Conducting Security Awareness Cyber Security Awareness Trends In 2022
Conducting Security Awareness Cyber Security Awareness Trends In 2022The purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2022. Increase in malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. Introducing Conducting Security Awareness Cyber Security Awareness Trends In 2022 to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Attack, Employees, Mobile Malware Attack, using this template. Grab it now to reap its full benefits.
-
 Conducting Security Awareness How To Overcome The Security Awareness Training Program
Conducting Security Awareness How To Overcome The Security Awareness Training ProgramThe purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. Present the topic in a bit more detail with this Conducting Security Awareness How To Overcome The Security Awareness Training Program. Use it as a tool for discussion and navigation on Outdated Content, Low Employee, Participation Rate. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Conducting Security Awareness Impact Of Cyber Security Breach General Consequences
Conducting Security Awareness Impact Of Cyber Security Breach General ConsequencesThe purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetxary penalty and operational disruption. Introducing Conducting Security Awareness Impact Of Cyber Security Breach General Consequences to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reputational Damage, Operational Disruption, Monetary Penalty, Theft Events, using this template. Grab it now to reap its full benefits.
-
 Conducting Security Awareness Key Stakeholders Of Cyber Security Awareness
Conducting Security Awareness Key Stakeholders Of Cyber Security AwarenessIncrease audience engagement and knowledge by dispensing information using Conducting Security Awareness Key Stakeholders Of Cyber Security Awareness. This template helps you present information on three stages. You can also present information on Senior Mangers, Line Managers, Employees using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Conducting Security Awareness Overview Of Cyber Security Awareness Course
Conducting Security Awareness Overview Of Cyber Security Awareness CourseThe purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. Introducing Conducting Security Awareness Overview Of Cyber Security Awareness Course to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Course Content, Attendees, Learning Outcome, Employees, using this template. Grab it now to reap its full benefits.
-
 Conducting Security Awareness Strategies We Will Implement To Make Security Awareness
Conducting Security Awareness Strategies We Will Implement To Make Security AwarenessThe purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Introducing Conducting Security Awareness Strategies We Will Implement To Make Security Awareness to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Gamification, Personalization, High Quality Content, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Awareness Checklist To Ensure IT Asset Protection Conducting Security Awareness
Cyber Security Awareness Checklist To Ensure IT Asset Protection Conducting Security AwarenessThe purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Present the topic in a bit more detail with this Cyber Security Awareness Checklist To Ensure IT Asset Protection Conducting Security Awareness. Use it as a tool for discussion and navigation on Checklist, Operating System, Employees Encouraged. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Evaluating IT System Security Using Swot Analysis Conducting Security Awareness
Evaluating IT System Security Using Swot Analysis Conducting Security AwarenessThe purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Introducing Evaluating IT System Security Using Swot Analysis Conducting Security Awareness to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strengths, Weaknesses, Opportunities, Threats, using this template. Grab it now to reap its full benefits.
-
 Functional Chart Of Cyber Security Team Conducting Security Awareness
Functional Chart Of Cyber Security Team Conducting Security AwarenessThe purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Deliver an outstanding presentation on the topic using this Functional Chart Of Cyber Security Team Conducting Security Awareness. Dispense information and present a thorough explanation of Cyber Risk Manger, Security Training, Cyber Business Liaison using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 How Much Employees Are Aware Of Cyber Security Conducting Security Awareness
How Much Employees Are Aware Of Cyber Security Conducting Security AwarenessThe purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass or fail rate of employees who received the security awareness training and fail rate by age. Increase audience engagement and knowledge by dispensing information using How Much Employees Are Aware Of Cyber Security Conducting Security Awareness. This template helps you present information on one stages. You can also present information on Age Group, Key Takeaways, Assessment Test using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
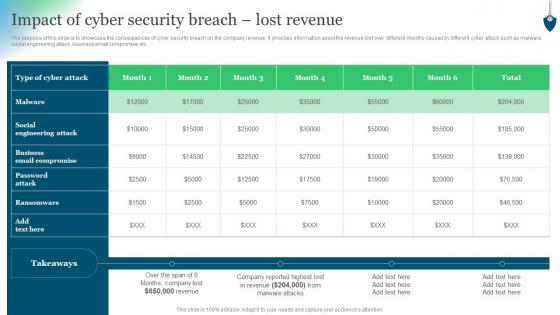 Impact Of Cyber Security Breach Lost Revenue Conducting Security Awareness
Impact Of Cyber Security Breach Lost Revenue Conducting Security AwarenessThe purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. Present the topic in a bit more detail with this Impact Of Cyber Security Breach Lost Revenue Conducting Security Awareness. Use it as a tool for discussion and navigation on Type Cyber Attack, Social Engineering Attack, Business Email Compromise. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Benefits Of Cyber Security Awareness Training Conducting Security Awareness
Key Benefits Of Cyber Security Awareness Training Conducting Security AwarenessThe purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Increase audience engagement and knowledge by dispensing information using Key Benefits Of Cyber Security Awareness Training Conducting Security Awareness. This template helps you present information on one stages. You can also present information on Drive Awareness, Prevent Downtime, Reduce Threat using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Major Statistics Of Cyber Security Awareness Conducting Security Awareness
Major Statistics Of Cyber Security Awareness Conducting Security AwarenessThis graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Present the topic in a bit more detail with this Major Statistics Of Cyber Security Awareness Conducting Security Awareness. Use it as a tool for discussion and navigation on Employees Keep, Keep Password Secure, IT Experts. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Measuring Security Awareness Campaign Results With KPIS Conducting Security Awareness
Measuring Security Awareness Campaign Results With KPIS Conducting Security AwarenessThe purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. Increase audience engagement and knowledge by dispensing information using Measuring Security Awareness Campaign Results With KPIS Conducting Security Awareness. This template helps you present information on one stages. You can also present information on Phishing Rate, Security Breaches, Cost Security Breach using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Need For Cyber Security Awareness Training Conducting Security Awareness
Need For Cyber Security Awareness Training Conducting Security AwarenessThe purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Increase audience engagement and knowledge by dispensing information using Need For Cyber Security Awareness Training Conducting Security Awareness. This template helps you present information on five stages. You can also present information on Organization, Cyber Attack, Cyber Security Awareness using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
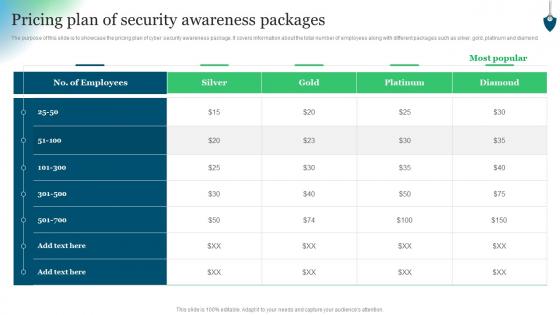 Pricing Plan Of Security Awareness Packages Conducting Security Awareness
Pricing Plan Of Security Awareness Packages Conducting Security AwarenessThe purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Present the topic in a bit more detail with this Pricing Plan Of Security Awareness Packages Conducting Security Awareness. Use it as a tool for discussion and navigation on Employees, Platinum, Silver. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Recognizing The Cyber Security Gaps Faced By Key Stakeholders Conducting Security Awareness
Recognizing The Cyber Security Gaps Faced By Key Stakeholders Conducting Security AwarenessThe purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, iot-based attack, malware etc. Present the topic in a bit more detail with this Recognizing The Cyber Security Gaps Faced By Key Stakeholders Conducting Security Awareness. Use it as a tool for discussion and navigation on Types Cyber Attack, Employees, Line Managers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective Mobile Device Security Management Enterprise Mobile Security For On Device
Effective Mobile Device Security Management Enterprise Mobile Security For On DeviceThis slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events associated to mobile device. Present the topic in a bit more detail with this Effective Mobile Device Security Management Enterprise Mobile Security For On Device. Use it as a tool for discussion and navigation on Incidents Damaging, Access Violations, Security Incidents. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Mobile Device Security Roadmap Enterprise Mobile Security For On Device
Implementing Mobile Device Security Roadmap Enterprise Mobile Security For On DeviceThis slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Present the topic in a bit more detail with this Implementing Mobile Device Security Roadmap Enterprise Mobile Security For On Device. Use it as a tool for discussion and navigation on Risk Management, Implement Security, Control Environment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Reverse Proxy Server Secure Client Connection To Proxy And Secure Proxy Connection To Content Server
Reverse Proxy Server Secure Client Connection To Proxy And Secure Proxy Connection To Content ServerThis slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely. Present the topic in a bit more detail with this Reverse Proxy Server Secure Client Connection To Proxy And Secure Proxy Connection To Content Server. Use it as a tool for discussion and navigation on Server Outside Firewall, Encrypted Secure, Proxy. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation In Information Technology Domain Security Controls That Can Be Automated
Security Automation In Information Technology Domain Security Controls That Can Be AutomatedThis slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Present the topic in a bit more detail with this Security Automation In Information Technology Domain Security Controls That Can Be Automated. Use it as a tool for discussion and navigation on Information Security, Organization, Operations Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
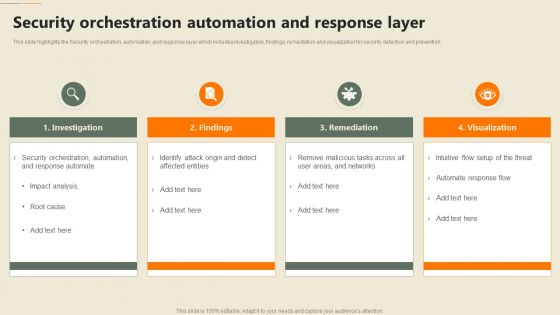 Security Automation In Information Technology Security Orchestration Automation And Response Layer
Security Automation In Information Technology Security Orchestration Automation And Response LayerThis slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention Increase audience engagement and knowledge by dispensing information using Security Automation In Information Technology Security Orchestration Automation And Response Layer. This template helps you present information on four stages. You can also present information on Investigation, Remediation, Visualization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Different Security Automation Tools With Pros Security Automation To Investigate And Remediate Cyberthreats
Different Security Automation Tools With Pros Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Present the topic in a bit more detail with this Different Security Automation Tools With Pros Security Automation To Investigate And Remediate Cyberthreats. Use it as a tool for discussion and navigation on Automation, Security Orchestration, Response. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Integrates Tools Systems And Security Automation To Investigate And Remediate Cyberthreats
Security Automation Integrates Tools Systems And Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Increase audience engagement and knowledge by dispensing information using Security Automation Integrates Tools Systems And Security Automation To Investigate And Remediate Cyberthreats. This template helps you present information on eight stages. You can also present information on Automation, Processes, System Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
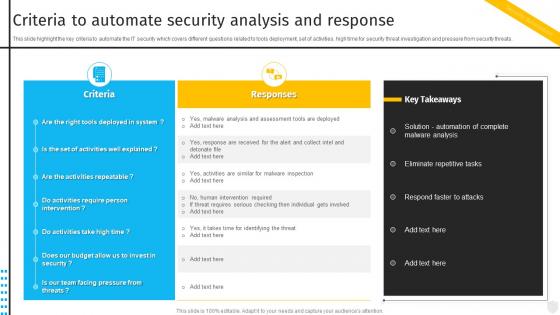 Criteria To Automate Security Analysis And Response Security Automation To Investigate And Remediate Cyberthreats
Criteria To Automate Security Analysis And Response Security Automation To Investigate And Remediate CyberthreatsThis slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Present the topic in a bit more detail with this Criteria To Automate Security Analysis And Response Security Automation To Investigate And Remediate Cyberthreats. Use it as a tool for discussion and navigation on Analysis, Deployment, Investigation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Domain Security Controls That Can Be Automated Security Automation To Investigate And Remediate Cyberthreats
Domain Security Controls That Can Be Automated Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Deliver an outstanding presentation on the topic using this Domain Security Controls That Can Be Automated Security Automation To Investigate And Remediate Cyberthreats. Dispense information and present a thorough explanation of Resources Security, Asset Management, Communications using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Network It Security Automation Security Automation To Investigate And Remediate Cyberthreats
Enterprise Network It Security Automation Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Increase audience engagement and knowledge by dispensing information using Enterprise Network It Security Automation Security Automation To Investigate And Remediate Cyberthreats. This template helps you present information on six stages. You can also present information on Automation, Security Infrastructure, Troubleshooting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Measure Security Automation Metrics For Operations Security Automation To Investigate And Remediate Cyberthreats
Measure Security Automation Metrics For Operations Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Present the topic in a bit more detail with this Measure Security Automation Metrics For Operations Security Automation To Investigate And Remediate Cyberthreats. Use it as a tool for discussion and navigation on Measure, Automation, Operations Efficiency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Right Time To Add Automation In Security Security Automation To Investigate And Remediate Cyberthreats
Right Time To Add Automation In Security Security Automation To Investigate And Remediate CyberthreatsThis slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. Present the topic in a bit more detail with this Right Time To Add Automation In Security Security Automation To Investigate And Remediate Cyberthreats. Use it as a tool for discussion and navigation on Individual Insights, Automation, Security Personnels. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Architecture With Key Elements Security Automation To Investigate And Remediate Cyberthreats
Security Automation Architecture With Key Elements Security Automation To Investigate And Remediate CyberthreatsThis slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Deliver an outstanding presentation on the topic using this Security Automation Architecture With Key Elements Security Automation To Investigate And Remediate Cyberthreats. Dispense information and present a thorough explanation of Automation, Architecture, Sources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Automation Stages With Maturity Level Security Automation To Investigate And Remediate Cyberthreats
Security Automation Stages With Maturity Level Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Present the topic in a bit more detail with this Security Automation Stages With Maturity Level Security Automation To Investigate And Remediate Cyberthreats. Use it as a tool for discussion and navigation on Opportunistic Stage, Systematic Stage, Institutionalized Stage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation To Investigate And Remediate Cyberthreats Determine Ideal Tasks For Security Automation
Security Automation To Investigate And Remediate Cyberthreats Determine Ideal Tasks For Security AutomationThis slide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Deliver an outstanding presentation on the topic using this Security Automation To Investigate And Remediate Cyberthreats Determine Ideal Tasks For Security Automation. Dispense information and present a thorough explanation of Security Automation, Sensitive Tasks, Individual Insight using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
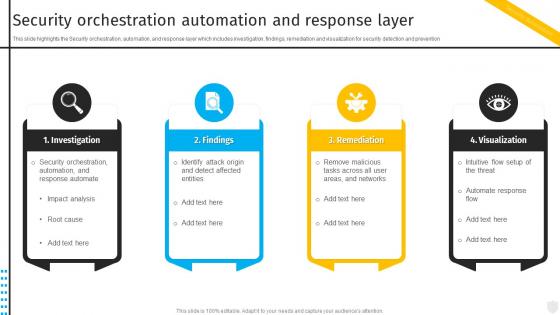 Security Orchestration Automation And Response Layer Security Automation To Investigate And Remediate Cyberthreats
Security Orchestration Automation And Response Layer Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention Increase audience engagement and knowledge by dispensing information using Security Orchestration Automation And Response Layer Security Automation To Investigate And Remediate Cyberthreats. This template helps you present information on four stages. You can also present information on Orchestration, Automation, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Processes That Cant Be Automated Security Automation To Investigate And Remediate Cyberthreats
Security Processes That Cant Be Automated Security Automation To Investigate And Remediate CyberthreatsThe following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Introducing Security Processes That Cant Be Automated Security Automation To Investigate And Remediate Cyberthreats to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Threat Modeling, Penetration Testing, Bug Bounty , using this template. Grab it now to reap its full benefits.
-
 Unified Platform Integration Security Automation Security Automation To Investigate And Remediate Cyberthreats
Unified Platform Integration Security Automation Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. Increase audience engagement and knowledge by dispensing information using Unified Platform Integration Security Automation Security Automation To Investigate And Remediate Cyberthreats. This template helps you present information on four stages. You can also present information on Security Automation, Prevention, Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Why To Automate The It Security Process Security Automation To Investigate And Remediate Cyberthreats
Why To Automate The It Security Process Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Introducing Why To Automate The It Security Process Security Automation To Investigate And Remediate Cyberthreats to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Better Threat Detection, Faster Containment, Improve Productivity, using this template. Grab it now to reap its full benefits.
-
 Determine Ideal Tasks For Security Automation Security Automation In Information Technology
Determine Ideal Tasks For Security Automation Security Automation In Information Technologyslide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Present the topic in a bit more detail with this Determine Ideal Tasks For Security Automation Security Automation In Information Technology. Use it as a tool for discussion and navigation on Security Automation, Determine, Sensitive Tasks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Security Automation Tools With Pros And Cons Security Automation In Information Technology
Different Security Automation Tools With Pros And Cons Security Automation In Information TechnologyThis slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM Deliver an outstanding presentation on the topic using this Different Security Automation Tools With Pros And Cons Security Automation In Information Technology. Dispense information and present a thorough explanation of Automation, Security Orchestration, Process Automation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Network It Security Automation Security Automation In Information Technology
Enterprise Network It Security Automation Security Automation In Information TechnologyThis slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Increase audience engagement and knowledge by dispensing information using Enterprise Network It Security Automation Security Automation In Information Technology. This template helps you present information on six stages. You can also present information on Orchestrating Network Security, Security Policy Automation, Infrastructure using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
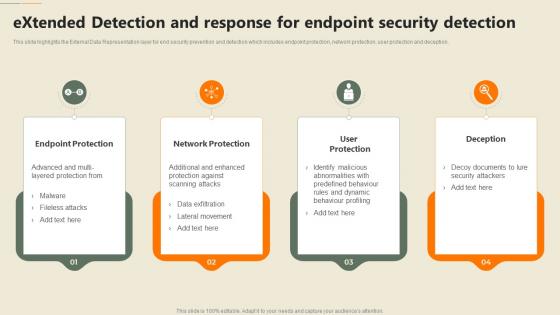 Extended Detection And Response For Endpoint Security Detection Security Automation In Information Technology
Extended Detection And Response For Endpoint Security Detection Security Automation In Information TechnologyThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Increase audience engagement and knowledge by dispensing information using Extended Detection And Response For Endpoint Security Detection Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Endpoint Protection, Network Protection, Deception using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Measure Security Automation Metrics For Operations Efficiency Security Automation In Information Technology
Measure Security Automation Metrics For Operations Efficiency Security Automation In Information TechnologyThis slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Present the topic in a bit more detail with this Measure Security Automation Metrics For Operations Efficiency Security Automation In Information Technology. Use it as a tool for discussion and navigation on Automation, Operations Efficiency, Performance Improvements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Right Time To Add Automation In Security Security Automation In Information Technology
Right Time To Add Automation In Security Security Automation In Information TechnologyThis slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. Deliver an outstanding presentation on the topic using this Right Time To Add Automation In Security Security Automation In Information Technology. Dispense information and present a thorough explanation of Individual, Insights, Automation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
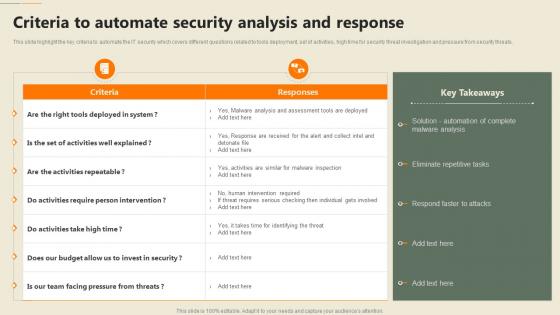 Security Automation In Information Technology Criteria To Automate Security Analysis And Response
Security Automation In Information Technology Criteria To Automate Security Analysis And ResponseThis slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Present the topic in a bit more detail with this Security Automation In Information Technology Criteria To Automate Security Analysis And Response. Use it as a tool for discussion and navigation on Analysis, Eliminate Repetitive Tasks, Respond Faster To Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation In Information Technology Impacts Of Ineffective Information Technology Security
Security Automation In Information Technology Impacts Of Ineffective Information Technology SecurityThis slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Increase audience engagement and knowledge by dispensing information using Security Automation In Information Technology Impacts Of Ineffective Information Technology Security. This template helps you present information on five stages. You can also present information on Information, Technology, Automation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Security Automation Integrates Tools Systems And Processes Security Automation In Information Technology
Security Automation Integrates Tools Systems And Processes Security Automation In Information TechnologyThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Increase audience engagement and knowledge by dispensing information using Security Automation Integrates Tools Systems And Processes Security Automation In Information Technology. This template helps you present information on eight stages. You can also present information on Automation, Integrates, Processes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Security Processes That Cant Be Automated Security Automation In Information Technology
Security Processes That Cant Be Automated Security Automation In Information TechnologyThe following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Increase audience engagement and knowledge by dispensing information using Security Processes That Cant Be Automated Security Automation In Information Technology. This template helps you present information on three stages. You can also present information on Threat Modeling, Penetration Testing, Bug Bounty using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Unified Platform Integration For Security Automation Security Automation In Information Technology
Unified Platform Integration For Security Automation Security Automation In Information TechnologyThis slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. Increase audience engagement and knowledge by dispensing information using Unified Platform Integration For Security Automation Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Access Management, Security Automation, Firewalls using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations





