Powerpoint Templates and Google slides for Security Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Endpoint Security Features Of Antivirus Software In Endpoint Security
Endpoint Security Features Of Antivirus Software In Endpoint SecurityThis slide outlines the functions of antivirus software in endpoint security for securing software against attacks such as malware, viruses, etc. Introducing Endpoint Security Features Of Antivirus Software In Endpoint Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Shields Computers From Threats, Protects Against Diverse Attacks, Detects And Removes Viruses, Security Software Against Malware, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Functions Of Firewall In Endpoint Security Solutions
Endpoint Security Functions Of Firewall In Endpoint Security SolutionsThis slide represents the objectives of second component of endpoint security that is firewall which is used to monitor traffic of devices. Increase audience engagement and knowledge by dispensing information using Endpoint Security Functions Of Firewall In Endpoint Security Solutions. This template helps you present information on six stages. You can also present information on Decides Traffic Allowance, Creates Network Barrier, Applies Security Rules, Monitors Traffic using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Goals Of Device Control In Endpoint Security
Endpoint Security Goals Of Device Control In Endpoint SecurityThis slide represents the objectives of one of the components of endpoint security which is device control technique to strengthens secure endpoint. Introducing Endpoint Security Goals Of Device Control In Endpoint Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Customizable Device Access Rules, Goals Of Device Control, Endpoint Security, Strengthens Secure Endpoint, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Implementation Process Of Endpoint Security Solutions
Endpoint Security Implementation Process Of Endpoint Security SolutionsThis slide highlights the process stages of endpoint security which include information gathering, choosing security solutions, etc. Increase audience engagement and knowledge by dispensing information using Endpoint Security Implementation Process Of Endpoint Security Solutions. This template helps you present information on three stages. You can also present information on Gather Information, Deploy Selected Solutions, Select Security Solutions, Endpoint Security Solutions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Introduction Of Endpoint Security Approach
Endpoint Security Introduction Of Endpoint Security ApproachThis slide discusses the overview of endpoint security solutions for the protection of entry points of devices and elevate vulnerability. Introducing Endpoint Security Introduction Of Endpoint Security Approach to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Analyze Cyberattacks, Detect And Block Attacks, Elevated Network Vulnerability, Endpoint Security Approach, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Intrusion Detection And Prevention System Idps In Endpoint Security
Endpoint Security Intrusion Detection And Prevention System Idps In Endpoint SecurityThis slide highlights the introduction of Intrusion Detection and Prevention System IDPS in endpoint security for preventing threats. Increase audience engagement and knowledge by dispensing information using Endpoint Security Intrusion Detection And Prevention System Idps In Endpoint Security. This template helps you present information on six stages. You can also present information on Alerts And Remediates Threat, Stop Detected Threats, Monitors Networks For Threats, Intrusion Detection And Prevention System using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Key Benefits Of Endpoint Security Approach
Endpoint Security Key Benefits Of Endpoint Security ApproachThis slide highlights the introduction of Intrusion Detection and Prevention System IDPS in endpoint security for preventing threats. Introducing Endpoint Security Key Benefits Of Endpoint Security Approach to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Allows For Dynamic Updating, Prevents Loss Of Data, Provides More Visibility, Offers A Cohesive Platform, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Key Elements Of Endpoint Security Approach
Endpoint Security Key Elements Of Endpoint Security ApproachThis slide highlights the major elements of endpoint security solutions which include device protection, data controls, browser protections, etc. Increase audience engagement and knowledge by dispensing information using Endpoint Security Key Elements Of Endpoint Security Approach. This template helps you present information on five stages. You can also present information on Application Controls, Data Controls, Device Protection, Browser Protections using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Key Importance Of Endpoint Security Approach
Endpoint Security Key Importance Of Endpoint Security ApproachThis slide outlines the significance of endpoint security approach which includes management of access, stop unauthorized users, etc. Introducing Endpoint Security Key Importance Of Endpoint Security Approach to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Stop Unauthorized Users, Secure All Access Points, Track Entries And Attempts, Endpoint Security Approach, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Key Types Of Endpoint Security Risks
Endpoint Security Key Types Of Endpoint Security RisksThis slide highlights the various types of endpoint security risks such as phishing, device loss, outdated patches, malware ads, etc. Increase audience engagement and knowledge by dispensing information using Endpoint Security Key Types Of Endpoint Security Risks. This template helps you present information on seven stages. You can also present information on Device Loss, Outdated Patches, Drive By Download, Ransomware using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Main Components Of Endpoint Security Approach
Endpoint Security Main Components Of Endpoint Security ApproachThis slide outlines the five components of endpoint security solutions which include network control, application control, data control, etc. Introducing Endpoint Security Main Components Of Endpoint Security Approach to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Device Protection, Network Control, Application Control, Endpoint Security Approach, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Major Types Of Endpoint Security Solutions
Endpoint Security Major Types Of Endpoint Security SolutionsThis slide showcases the different techniques of endpoint security which include email gateway, network access control, browser isolation, etc. Increase audience engagement and knowledge by dispensing information using Endpoint Security Major Types Of Endpoint Security Solutions. This template helps you present information on eight stages. You can also present information on Endpoint Detection And Response, Network Access Control, Email Gateway, Endpoint Security Solutions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Micro Endpoint Security Application Control
Endpoint Security Micro Endpoint Security Application ControlThis slide discusses about one of the components of endpoint security which is application control for data protection in devices. Introducing Endpoint Security Micro Endpoint Security Application Control to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Increase In Malware Defense, Data Protection, Prevent Unauthorized Applications, Optimal Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Objectives Of Endpoint Security Encryption Technique
Endpoint Security Objectives Of Endpoint Security Encryption TechniqueThis slide outlines the functions of encryption technique in endpoint security for safeguarding data on devices such as laptops, computers, etc. Increase audience engagement and knowledge by dispensing information using Endpoint Security Objectives Of Endpoint Security Encryption Technique. This template helps you present information on six stages. You can also present information on Restricts Unauthorized Access, Protects Valuable Corporate Data, Makes Data Unreadable, Safeguards Data On Devices using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Patch Management Technique For Endpoint Security
Endpoint Security Patch Management Technique For Endpoint SecurityThis slide outlines the overview of patch management technique in endpoint security to scan, identify, download, and deploy patches. Introducing Endpoint Security Patch Management Technique For Endpoint Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Fresh Network Security Approach, Works For Windows And Mac, Quick Threat Response, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Roadmap To Implement Effective Endpoint Security
Endpoint Security Roadmap To Implement Effective Endpoint SecurityThis slide outlines the steps to deploy endpoint security which include recognizing known malware, reduce end user access, utilizing application control, etc. Increase audience engagement and knowledge by dispensing information using Endpoint Security Roadmap To Implement Effective Endpoint Security. This template helps you present information on six stages. You can also present information on Utilize Sensible Application Control, Recognize And Avoid Known Malware, Block Dangerous Activity, Effective Endpoint Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Timeline For Implementing Efficient Endpoint Security
Endpoint Security Timeline For Implementing Efficient Endpoint SecurityThis slide outlines the different steps performed while deploying endpoint security, including planning phase, solution selection, etc. Introducing Endpoint Security Timeline For Implementing Efficient Endpoint Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Testing And Optimization, Solution Selection, Deployment, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Top Endpoint Security Tools And Cost
Endpoint Security Top Endpoint Security Tools And CostThis slide highlights the tools used for endpoint security such as Sophos, Vipre, and CrowdStrike along with their cost and features. Deliver an outstanding presentation on the topic using this Endpoint Security Top Endpoint Security Tools And Cost. Dispense information and present a thorough explanation of Prevents Ransomware, Security Tools And Cost, Crowdstrike using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Selection Of Optimal Application Security Technique
Application Security Implementation Plan Selection Of Optimal Application Security TechniqueThis slide outlines the comparison of different application testing techniques on the basis of parameters such as security provided and cost. Present the topic in a bit more detail with this Application Security Implementation Plan Selection Of Optimal Application Security Technique. Use it as a tool for discussion and navigation on Authorization, Encryption, Security Testing, Access Control. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective Software Of Visualization Security To Secure Access
Effective Software Of Visualization Security To Secure AccessThis slide showcases various software for visualization security. The main purpose of this template is to secure data transmission . this includes tableau, microsoft power BI, google data studio, etc. Presenting our well structured Effective Software Of Visualization Security To Secure Access. The topics discussed in this slide are Microsoft Power, Google Data Studio, Secure Access. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Different Modes Of IP Security For Securing Data
Different Modes Of IP Security For Securing DataThis slide showcases various modes of IP security. The main purpose of this template is to secure communication between two endpoints. This includes Point-to-point security, tunnel mode, remote access, etc. Introducing our Different Modes Of IP Security For Securing Data set of slides. The topics discussed in these slides are IP Security, Secure Communication, Point To Point Security, Tunnel Mode. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Analysis Of Security And Utility Token Tokenization For Improved Data Security
Comparative Analysis Of Security And Utility Token Tokenization For Improved Data SecurityThis slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc. Present the topic in a bit more detail with this Comparative Analysis Of Security And Utility Token Tokenization For Improved Data Security. Use it as a tool for discussion and navigation on Comparative Analysis, Security And Utility Token, Expectations, Scam Potential. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Before Vs After Implementing Tokenization In Data Security
Tokenization For Improved Data Security Before Vs After Implementing Tokenization In Data SecurityThis slide showcases the comparative analysis of the before versus after tokenization. The purpose of this slide is to showcase the different performance metrics and how tokenization has improved these metrics. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Before Vs After Implementing Tokenization In Data Security. Dispense information and present a thorough explanation of Compliance With Regulations, Reduced Insider Threats, Exposure Of Sensitive Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Best Practices For Tokenization In Data Security
Tokenization For Improved Data Security Best Practices For Tokenization In Data SecurityThe purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Best Practices For Tokenization In Data Security. This template helps you present information on four stages. You can also present information on Effective Cybersecurity And Compliance, Broaden Data Tokenization Scope, Regularly Revise Tokenization Policies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Characteristics Of Utility Tokenization In Data Security
Tokenization For Improved Data Security Characteristics Of Utility Tokenization In Data SecurityThis slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Characteristics Of Utility Tokenization In Data Security. This template helps you present information on seven stages. You can also present information on Utility Tokenization, Data Security, Platforms Economic Activity, Blockchain Powered Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Checklist To Conduct Tokenization In Data Security
Tokenization For Improved Data Security Checklist To Conduct Tokenization In Data SecurityThis slide showcases the checklist for performing tokenization. The purpose of this slide is to highlight the actions performed while conducting regression testing, person responsible, status and comments for the same. Present the topic in a bit more detail with this Tokenization For Improved Data Security Checklist To Conduct Tokenization In Data Security. Use it as a tool for discussion and navigation on Data Classification, Tokenization Algorithm Selection, Key Management, Access Control. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Common Use Cases Of Tokenization In Data Security
Tokenization For Improved Data Security Common Use Cases Of Tokenization In Data SecurityThis slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc. Introducing Tokenization For Improved Data Security Common Use Cases Of Tokenization In Data Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Restricting Access To Sensitive Data, Reducing Compliance Scope, Tokenization In Data Security, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Data Security Benefits Of Adopting Tokenization
Tokenization For Improved Data Security Data Security Benefits Of Adopting TokenizationThis slide discusses the cons of tokenization. The purpose of this slide is to showcase the advantages of tokenization such as utilizing less resources, decreases risk, stimulates innovation, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Data Security Benefits Of Adopting Tokenization. Dispense information and present a thorough explanation of Builds Customer Trust, Data Security Benefits, Adopting Tokenization, Fostering Technologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Introduction Of Utility Token In Data Security
Tokenization For Improved Data Security Introduction Of Utility Token In Data SecurityThis slide showcases the overview of utility tokens in data security. The purpose of this slide is to discuss the introduction of utility tokens required for data security and preventing thefts. Introducing Tokenization For Improved Data Security Introduction Of Utility Token In Data Security to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Data Security, Utility Tokens, Preventing Thefts, Unique To Each Platform, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Main Data Security Tokenization Techniques
Tokenization For Improved Data Security Main Data Security Tokenization TechniquesThis slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc. Introducing Tokenization For Improved Data Security Main Data Security Tokenization Techniques to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Transactional, Governance Tokenization, Utility Tokenization, Platform Tokenization, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Overview And Benefits Of Encryption For Data Security
Tokenization For Improved Data Security Overview And Benefits Of Encryption For Data SecurityThis slide outlines the introduction and cons of encryption. The purpose of this slide is to highlight the overview and advantages of encryption which include broad application, provides protection, security, etc. Present the topic in a bit more detail with this Tokenization For Improved Data Security Overview And Benefits Of Encryption For Data Security. Use it as a tool for discussion and navigation on Employing Mathematical Algorithms, Transform Sensitive Data, Unstructured Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Overview And Process Of Tokenization In Data Security
Tokenization For Improved Data Security Overview And Process Of Tokenization In Data SecurityThis slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc. Introducing Tokenization For Improved Data Security Overview And Process Of Tokenization In Data Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Tokenization In Data Security, While Ensuring Security, Small And Midsize Enterprises, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Overview Of Platform Tokenization In Data Security
Tokenization For Improved Data Security Overview Of Platform Tokenization In Data SecurityThis slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc. Introducing Tokenization For Improved Data Security Overview Of Platform Tokenization In Data Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Ethereum Token Exchange, Platform Tokenization, Data Security, Security And Transactional Capacity, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Overview Of Security Tokenization In Data Security
Tokenization For Improved Data Security Overview Of Security Tokenization In Data SecurityThis slide outlines the introduction of security tokenization in data security. The purpose of this slide is to highlight the overview of security tokenization which include the definition, purpose, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Overview Of Security Tokenization In Data Security. This template helps you present information on eight stages. You can also present information on Security Tokenization, Data Security, Considering Security Tokens, Conventional Financial Securities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Reasons For Conducting Tokenization In Data Security
Tokenization For Improved Data Security Reasons For Conducting Tokenization In Data SecurityThis slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Reasons For Conducting Tokenization In Data Security. This template helps you present information on five stages. You can also present information on Card Accepting Businesses, Regulatory Compliance, Bureaucratic Processes For Businesses using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Regulations Of Security Tokens In Blockchain Technology
Tokenization For Improved Data Security Regulations Of Security Tokens In Blockchain TechnologyThis slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A plus, S regulations, etc. Introducing Tokenization For Improved Data Security Regulations Of Security Tokens In Blockchain Technology to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Regulations Of Security Tokens, Blockchain Technology, Data Security, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Roadmap To Implement Tokenization For Data Security
Tokenization For Improved Data Security Roadmap To Implement Tokenization For Data SecurityThis slide outlines the deployment for tokenization. The purpose of this slide is to highlight the steps that an organization should take while implementing tokenization including, generating tokens, identifying sensitive data, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Roadmap To Implement Tokenization For Data Security. This template helps you present information on five stages. You can also present information on Identify Sensitive Data, Implement Access Controls, Configure The Tokenization System, Data Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Salient Features Of Tokenization In Data Security
Tokenization For Improved Data Security Salient Features Of Tokenization In Data SecurityThis slide outlines the key characteristics of tokenization in data security. The purpose of this slide is to highlight the properties of tokenization that include underlying representation, transferability, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Salient Features Of Tokenization In Data Security. This template helps you present information on five stages. You can also present information on Underlying Representation, Transferability, Fungibility, Data Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Timeline To Implementation Tokenization In Data Security
Tokenization For Improved Data Security Timeline To Implementation Tokenization In Data SecurityThis slide outlines the timeline for executing tokenization. The purpose of this slide is to showcase the different steps performed while implementing tokenization, including key management, monitoring, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Timeline To Implementation Tokenization In Data Security. This template helps you present information on six stages. You can also present information on Tokenization Key Management, Monitoring And Auditing, Tokenization Methods, Data Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Tokenization In Payment Card Industry For Data Security
Tokenization For Improved Data Security Tokenization In Payment Card Industry For Data SecurityThis slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Tokenization In Payment Card Industry For Data Security. Dispense information and present a thorough explanation of Tokenization In Payment Card, Data Security, Converts Credit Card, Point Of Sale Terminals using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Tokenization Working Process For Data Security
Tokenization For Improved Data Security Tokenization Working Process For Data SecurityThis slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Tokenization Working Process For Data Security. Dispense information and present a thorough explanation of Tokenization Working Process, Data Security, Mobile Payment Application, Generating Tokens using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Working Of Security Tokenization In Financial Assets
Tokenization For Improved Data Security Working Of Security Tokenization In Financial AssetsThis slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc. Introducing Tokenization For Improved Data Security Working Of Security Tokenization In Financial Assets to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Working Of Security Tokenization, Financial Assets, Dividend Distribution, Security Token Classification, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Application Security Training Program For IT Team
Application Security Implementation Plan Application Security Training Program For IT TeamThis slide highlights the comprehensive training program for software testers which aims to train beginners about application security. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Application Security Training Program For IT Team. Dispense information and present a thorough explanation of Understanding Functionalities, Application Security, Training Program using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Authorization Deployment Steps For Application Security
Application Security Implementation Plan Authorization Deployment Steps For Application SecurityThis slide discusses the process phases for implementing effective authorization which include assessment, planning, defining access control policies, etc. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Authorization Deployment Steps For Application Security. This template helps you present information on seven stages. You can also present information on Technology Selection, Assessment And Planning, Training And Awareness using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Before Vs After Implementation Of Application Security
Application Security Implementation Plan Before Vs After Implementation Of Application SecurityThis slide showcases the comparative analysis of the before versus after implementation of application security situation of an organization. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Before Vs After Implementation Of Application Security. Dispense information and present a thorough explanation of Lack Of Encryption, Vulnerable Authentication, Absence Of Regular Security Updates using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Elements Security Response Plan Business Recovery Plan To Overcome Cyber Security Threat
Key Elements Security Response Plan Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the key components of cyber security threat response plan. It includes key elements such as identify attack source, limit damage, damage scope assessment, consulting, clean up system, and future action plan. Increase audience engagement and knowledge by dispensing information using Key Elements Security Response Plan Business Recovery Plan To Overcome Cyber Security Threat. This template helps you present information on six stages. You can also present information on Identify The Attack Source, Limit Additional Damage, Damage Scope Assessment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Potential Consistent Cyber Security Attacks Business Recovery Plan To Overcome Cyber Security Threat
Potential Consistent Cyber Security Attacks Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various solutions that can be adopted for business cyber-attack management. It includes key solutions such as staff training, collaboration with experts, and develop business recovery plan. Deliver an outstanding presentation on the topic using this Potential Consistent Cyber Security Attacks Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Solution Scope, Solution Duration, Requisites using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Software Updation To Avoid Security Breach Business Recovery Plan To Overcome Cyber Security Threat
Software Updation To Avoid Security Breach Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information software updation best practices to follow. It includes key practices such as updation operating system, uninstall unnecessary software, and leverage patch systems. Increase audience engagement and knowledge by dispensing information using Software Updation To Avoid Security Breach Business Recovery Plan To Overcome Cyber Security Threat. This template helps you present information on three stages. You can also present information on Leverage Patching System, Uninstall Unnecessary Software, Update Operating System using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
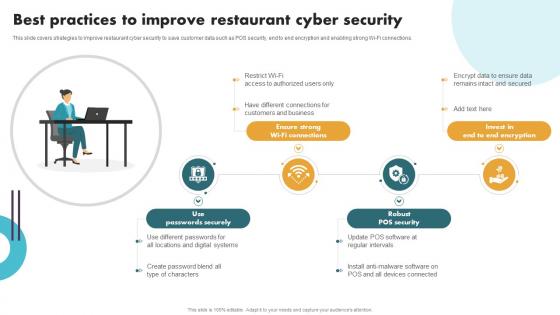 Securing Food Safety In Online Best Practices To Improve Restaurant Cyber Security
Securing Food Safety In Online Best Practices To Improve Restaurant Cyber SecurityThis slide covers strategies to improve restaurant cyber security to save customer data such as POS security, end to end encryption and enabling strong Wi-Fi connections. Introducing Securing Food Safety In Online Best Practices To Improve Restaurant Cyber Security to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Use Passwords Securely, Ensure Strong Wi-Fi Connections, Robust POS Security, using this template. Grab it now to reap its full benefits.
-
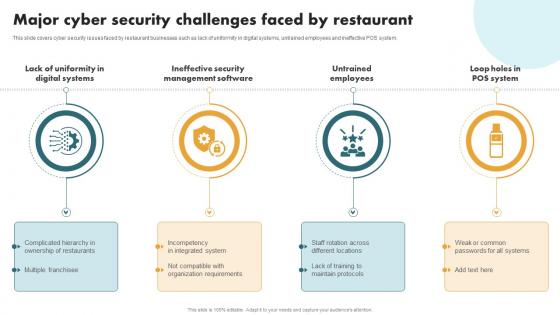 Securing Food Safety In Online Major Cyber Security Challenges Faced By Restaurant
Securing Food Safety In Online Major Cyber Security Challenges Faced By RestaurantThis slide covers cyber security issues faced by restaurant businesses such as lack of uniformity in digital systems, untrained employees and ineffective POS system. Introducing Securing Food Safety In Online Major Cyber Security Challenges Faced By Restaurant to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Lack Of Uniformity In Digital Systems, Ineffective Security Management Software, Untrained Employees, Loop Holes In POS System, using this template. Grab it now to reap its full benefits.
-
 Securing Food Safety In Online Secure Payment Gateways To Enhance Restaurant
Securing Food Safety In Online Secure Payment Gateways To Enhance RestaurantThis slide covers secure payment gateways to improve cyber security. It involves components such as encryption, tokenization, authentication and reliability. Present the topic in a bit more detail with this Securing Food Safety In Online Secure Payment Gateways To Enhance Restaurant. Use it as a tool for discussion and navigation on Customer, Merchant, Payment Gateway, Confirm Payment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ai Network Security Icon With Secure Database
Ai Network Security Icon With Secure DatabasePresenting our well structured Ai Network Security Icon With Secure Database. The topics discussed in this slide are AI Network Security, Secure Database. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Role Of Identity And Access Management In Data Security Securing Systems With Identity
Role Of Identity And Access Management In Data Security Securing Systems With IdentityThis slide discusses the Identity and Access Management importance in data security. The purpose of this slide is to highlight the importance, including protecting business data, addressing new challenges, beyond perimeter security, combatting compromised credentials, and so on. Deliver an outstanding presentation on the topic using this Role Of Identity And Access Management In Data Security Securing Systems With Identity Dispense information and present a thorough explanation of Protecting Business Data, Combatting Compromised Credentials using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Traditional Vs Modern IAM Security Landscape Securing Systems With Identity
Traditional Vs Modern IAM Security Landscape Securing Systems With IdentityThis slide compares traditional vs. modern Identity and Access Management security landscape. The purpose of this slide is to highlight the difference between conventional and contemporary Identity and Access Management systems. Increase audience engagement and knowledge by dispensing information using Traditional Vs Modern IAM Security Landscape Securing Systems With Identity This template helps you present information on Two stages. You can also present information on Authorization, Central User Repository, User Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 30 60 90 Days Plan For Mobile Security Implementation Mobile Security
30 60 90 Days Plan For Mobile Security Implementation Mobile SecurityThis slide discusses the 30-60-90 day plan for the implementation of mobile security which include assessment and planning, security awareness, review and update. Introducing 30 60 90 Days Plan For Mobile Security Implementation Mobile Security to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Assessment And Planning, Security Awareness, Review And Update using this template. Grab it now to reap its full benefits.
-
 Application Based Mobile Security Threats Mobile Security
Application Based Mobile Security Threats Mobile SecurityThis slide represents the different types of application based mobile security threats which include malicious apps, fake or clone apps and app spoofing. Increase audience engagement and knowledge by dispensing information using Application Based Mobile Security Threats Mobile Security This template helps you present information on Five stages. You can also present information on Simplicity, Ubiquitousness, Cost Effective using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Strategies For Creating Security Awareness Mobile Security
Best Strategies For Creating Security Awareness Mobile SecurityThis slide represents the best strategies for creating culture of mobile security awareness which includes educate workforce on mobile security, etc. Increase audience engagement and knowledge by dispensing information using Best Strategies For Creating Security Awareness Mobile Security This template helps you present information on Five stages. You can also present information on Enable Authentication In App, Device Settings using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Biometric Authentication In Mobile Device Security Mobile Security
Biometric Authentication In Mobile Device Security Mobile SecurityThis slide gives an overview of biometric authentication in mobile device security which includes enable authentication in app and support unlocking, etc. Introducing Biometric Authentication In Mobile Device Security Mobile Security to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Budget Category, Estimated Cost, Actual Cost using this template. Grab it now to reap its full benefits.
-
 Budget Allocation For Mobile Security Implementation Mobile Security
Budget Allocation For Mobile Security Implementation Mobile SecurityThis slide represents the estimated and actual cost of implementing mobile security in an organization based on categories like training and security update. Increase audience engagement and knowledge by dispensing information using Budget Allocation For Mobile Security Implementation Mobile Security This template helps you present information on Three stages. You can also present information on Data Exposure Risks, Encryption Vulnerabilities, Authorization Weaknesses using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Common Issues Affecting Mobile App Security Mobile Security
Common Issues Affecting Mobile App Security Mobile SecurityThis slide represents the common issues affecting mobile app security which includes data exposure risks, unencrypted data transmissions, etc. Introducing Common Issues Affecting Mobile App Security Mobile Security to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Stolen Passwords, Phishing Attempts, Social Engineering using this template. Grab it now to reap its full benefits.





