Powerpoint Templates and Google slides for Security Processing
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Effective information security risk management process powerpoint presentation slides
Effective information security risk management process powerpoint presentation slidesDeliver an informational PPT on various topics by using this Effective Information Security Risk Management Process Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with fifty seven slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
-
 Improving Cyber Security Risks Management Process Powerpoint PPT Template Bundles DK MD
Improving Cyber Security Risks Management Process Powerpoint PPT Template Bundles DK MDIf you require a professional template with great design, then this Improving Cyber Security Risks Management Process Powerpoint PPT Template Bundles DK MD is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twenty one slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Data Tools Processing Model Visualization Layer Security Segment
Data Tools Processing Model Visualization Layer Security SegmentDeliver a lucid presentation by utilizing this Data Tools Processing Model Visualization Layer Security Segment. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as Processing Model, Visualization Layer, Security Segment. All the twenty nine slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
 Security Patch Management Process Powerpoint Ppt Template Bundles
Security Patch Management Process Powerpoint Ppt Template BundlesDeliver a credible and compelling presentation by deploying this Security Patch Management Process Powerpoint Ppt Template Bundles. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The saeventeen slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Security Patch Management Process Powerpoint Ppt Template Bundles PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Seven petal secure authentication cloud communications process workflow
Seven petal secure authentication cloud communications process workflowIntroduce your topic and host expert discussion sessions with this Seven Petal Secure Authentication Cloud Communications Process Workflow. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the seventeen slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 Process Governing Launch Of Security Token Offerings To Raise Venture Capital Training Ppt
Process Governing Launch Of Security Token Offerings To Raise Venture Capital Training PptPresenting Process Governing Launch of Security Token Offerings to raise Venture Capital. Our PowerPoint experts have included all the necessary templates, designs, icons, graphs, and other essential material. This deck is well crafted by extensive research. Slides consist of amazing visuals and appropriate content. These PPT slides can be instantly downloaded with just a click. Compatible with all screen types and monitors. Supports Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Technology Security Process Framework Assessment Management Awareness
Technology Security Process Framework Assessment Management AwarenessThis complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on Technology Security Process Framework Assessment Management Awareness and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of twelve slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.
-
 Cycle Input Output Business Expansion Process Security Improvement Automation
Cycle Input Output Business Expansion Process Security Improvement AutomationIf you require a professional template with great design, then this Cycle Input Output Business Expansion Process Security Improvement Automation is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twelve slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Multi factor authentication secure access process application server through
Multi factor authentication secure access process application server throughDeliver a lucid presentation by utilizing this Multi Factor Authentication Secure Access Process Application Server Through. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as Multi Factor Authentication, Secure, Access, Process, Application. All the twelve slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
 Meta Data Organizational Securing Reporting Processing Development Monitoring
Meta Data Organizational Securing Reporting Processing Development MonitoringIf you require a professional template with great design, then this Meta Data Organizational Securing Reporting Processing Development Monitoring is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twelve slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Firewall Network Security Working Process Of Firewall In Networking Domain
Firewall Network Security Working Process Of Firewall In Networking DomainThis slide represents how a firewall system works in a network. The purpose of this slide is to showcase the architecture, working, and different technologies used in a firewall mechanism to protect the network from malicious activities. The technologies include real-time monitoring, IP packet filtering, and so on. Deliver an outstanding presentation on the topic using this Firewall Network Security Working Process Of Firewall In Networking Domain Dispense information and present a thorough explanation of Working, Technologies Used, Firewall Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Devsecops Best Practices For Secure Key Processes Followed In Devsecops Model
Devsecops Best Practices For Secure Key Processes Followed In Devsecops ModelThis slide discusses the various processes followed in DevSecOps. The purpose of this slide is to highlight the processes, including code analysis, change management, compliance management, threat modelling and security training. Increase audience engagement and knowledge by dispensing information using Devsecops Best Practices For Secure Key Processes Followed In Devsecops Model. This template helps you present information on five stages. You can also present information on Code Analysis, Change Management, Compliance Managements, Threat Modelling using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Devsecops Best Practices For Secure Training Budget Of Devsecops Process For Customers
Devsecops Best Practices For Secure Training Budget Of Devsecops Process For CustomersThis slide showcases the breakdown cost for the DevSecOps installation and management training for the customers. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor cost, training cost, etc. Present the topic in a bit more detail with this Devsecops Best Practices For Secure Training Budget Of Devsecops Process For Customers. Use it as a tool for discussion and navigation on Training Budget, Devsecops Process For Customers, Instructor Cost, Training Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure World Wide Market Size Of Devsecops Process
Devsecops Best Practices For Secure World Wide Market Size Of Devsecops ProcessThis slide depicts the global market size of DevSecOps. The purpose of this slide is to highlight the holistic evolution of the market from 2022 to 2030 in terms of the estimated market value, projected market value, and compound annual growth rate. Present the topic in a bit more detail with this Devsecops Best Practices For Secure World Wide Market Size Of Devsecops Process. Use it as a tool for discussion and navigation on Global Market Size Devsecops, Holistic Evolution, Projected Market Value, Compound Annual Growth Rate. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Fintech Cyber Security Tool Investment By Process
Fintech Cyber Security Tool Investment By ProcessThis slide showcases the investment in tools to protect against cyber security. Its aim is to monitor and invest in best tools for securing fintech. This slide includes monitoring, policy, hiring, software, firewall, authentication and encryption. Introducing our Fintech Cyber Security Tool Investment By Process set of slides. The topics discussed in these slides are Fintech, Cyber Security Tool, Investment By Process. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data security it process of disaster recovery planning ppt slides download
Data security it process of disaster recovery planning ppt slides downloadThis slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Introducing Data Security IT Process Of Disaster Recovery Planning Ppt Slides Download to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Approval, Create Disaster, Recovery Team, Perform, Risk Analysis, Prioritize Procedures And Operations, Define Recovery Plans, using this template. Grab it now to reap its full benefits.
-
 Computer system security process of disaster recovery planning
Computer system security process of disaster recovery planningThis slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Introducing Computer System Security Process Of Disaster Recovery Planning to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Plan Testing, Approval, Recovery Plans, Data Collection, Forming Data Recovery Plan, using this template. Grab it now to reap its full benefits.
-
 Risk Analysis Process For Information Security
Risk Analysis Process For Information SecurityThis slide outlines the risk analysis process for information security to identify the specific action or event. It includes various aspects such as risk assessment team, scope of the project, identify assets, categorize potential losses, identify threats and vulnerabilities and identify existing controls.Presenting our set of slides with Risk Analysis Process For Information Security. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Risk Assessment Team, Identify Assets, Identify Threats.
-
 Risk Analysis Process In Cyber Security
Risk Analysis Process In Cyber SecurityThis slide outlines the risk analysis process for cyber security to effectively and efficiently protect their department assets. It includes key steps such as conduct risk assessment survey, identify risks, analyse risks, develop a risk management plan, implement risk management plan and monitor risks.Introducing our premium set of slides with Risk Analysis Process In Cyber Security. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Assessment Survey, Identify Risks, Analyze Risks. So download instantly and tailor it with your information.
-
 Data Security Processing Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Processing Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon depicts data processing. It features a laptop with a graph and a magnifying glass, representing the analysis and research involved in data processing. Use this icon to illustrate data processing in your presentations.
-
 Data Security Processing Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Processing Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is perfect for representing data processing in presentations. It features a simple, black and white design that is sure to draw attention to the data processing topic. It is ideal for illustrating data flow and other related concepts.
-
 4 Step Development Process For Big Data Analytics Security
4 Step Development Process For Big Data Analytics SecurityThis slide depicts the 4 step developmental process for big data analytics. The purpose of this slide is to help the business establish big data security analytics in an appropriate manner for safeguarding sensitive and important business information. It includes steps such as classification, encryption, etc. Presenting our set of slides with 4 Step Development Process For Big Data Analytics Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Classification, Data Encryption.
-
 Process For Creating Network Security Management Plan
Process For Creating Network Security Management PlanThis slide showcases the process of network security in business. The main purpose of this slide is to understand and maintain network security in the workplace. This includes understanding business models, identifying threats, developing IT security policies, etc.Introducing our premium set of slides with Process For Creating Network Security Management Plan. Ellicudate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Understanding Business, Identifying Threat, Maintain Security Future. So download instantly and tailor it with your information.
-
 Benefits Social Security Disability Appeal Process In Powerpoint And Google Slides Cpb
Benefits Social Security Disability Appeal Process In Powerpoint And Google Slides CpbPresenting Benefits Social Security Disability Appeal Process In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Benefits Social Security Disability Appeal Process. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cloud Access Security Broker CASB V2 Working Process Ppt Ideas Graphics Example
Cloud Access Security Broker CASB V2 Working Process Ppt Ideas Graphics ExampleThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Working Process Ppt Ideas Graphics Example. This template helps you present information on three stages. You can also present information on Cloud Access Security, Broker Working Process, Classification And Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secops V2 Security Operations Threat Management Process
Secops V2 Security Operations Threat Management ProcessThis slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. Deliver an outstanding presentation on the topic using this Secops V2 Security Operations Threat Management Process. Dispense information and present a thorough explanation of Extended Investigation, Preliminary Investigation, Security Operations Threat
-
 Two Factor Authentication Process Flow For Enhanced Security E Wallets As Emerging Payment Method Fin SS V
Two Factor Authentication Process Flow For Enhanced Security E Wallets As Emerging Payment Method Fin SS VThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Present the topic in a bit more detail with this Two Factor Authentication Process Flow For Enhanced Security E Wallets As Emerging Payment Method Fin SS V. Use it as a tool for discussion and navigation on Authentication, Process, Possession Verification. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Working Process Cloud Security Model
Cloud Access Security Broker Working Process Cloud Security ModelThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Working Process Cloud Security Model. This template helps you present information on three stages. You can also present information on Discovery, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Security Cloud Access Security Broker Working Process
Sase Security Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, an remediation. Deliver an outstanding presentation on the topic using this Sase Security Cloud Access Security Broker Working Process. Dispense information and present a thorough explanation of Remediation, Classification, Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Working Process Secure Access Service Edge Sase
Cloud Access Security Broker Working Process Secure Access Service Edge SaseThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Working Process Secure Access Service Edge Sase. This template helps you present information on three stages. You can also present information on Information, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Risk Audit Process Flowchart Improving Cyber Security Risks Management
Cyber Security Risk Audit Process Flowchart Improving Cyber Security Risks ManagementThe following slide depicts the cyber security review flowchart to manage risk and minimize its impact. It includes elements such as request access, grantor, authorizer, tools, auditor, follow up, alert to end user etc. Present the topic in a bit more detail with this Cyber Security Risk Audit Process Flowchart Improving Cyber Security Risks Management. Use it as a tool for discussion and navigation on Request Access, Validate User Identity, Dismiss Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents For Improving Cyber Security Risk Management Process
Table Of Contents For Improving Cyber Security Risk Management ProcessIntroducing Table Of Contents For Improving Cyber Security Risk Management Process to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Risks And Attacks, Management Solutions, Program Courses, using this template. Grab it now to reap its full benefits.
-
 Challenges In Implementing Security Patch Management Process
Challenges In Implementing Security Patch Management ProcessFollowing slide showcases constraints in establishing security patch management process. The purpose of this slide is to provide information regarding challenges faced by businesses in ensuring the security of an organizations infrastructure. It also provides solutions to overcome challenges.Introducing our Challenges In Implementing Security Patch Management Process set of slides. The topics discussed in these slides are Existing Software, Vulnerabilities Prioritize, Compatibility Issues. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Common Issues Addressed By Security Patch Management Process
Common Issues Addressed By Security Patch Management ProcessFollowing slide highlights common problems tackled by security patch management process. The purpose of this slide is to build an organizations overall security position and maintain the integrity of its IT and operational environment. It includes factors such as data breaches, loss of productivity, etc.Presenting our set of slides with Common Issues Addressed By Security Patch Management Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Reputation Damage, Unintended System, Security Incidents.
-
 Effective Security Patch Management Process For Manufacturing Business
Effective Security Patch Management Process For Manufacturing BusinessThis slide showcases process of security patch management for manufacturing business. This template aims to help businesses integrate key components into a comprehensive security patch management process to maintain the stability of their operations. It includes phases such as vulnerability assessment, risk assessment, etc.Introducing our premium set of slides with Effective Security Patch Management Process For Manufacturing Business. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Vulnerability Assessment, Risk Assessment, Change Management. So download instantly and tailor it with your information.
-
 Enhancing Cyber Security With Patch Management Process
Enhancing Cyber Security With Patch Management ProcessFollowing slide showcases the process for improving cybersecurity with patch management process. The purpose of this slide is to help organizations strengthen their action plan against cyber threats to ensure a secure computing environment. It includes elements such as well trained staff, communication plan, etc.Presenting our set of slides with Enhancing Cyber Security With Patch Management Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Communication Plan, Regularly Test Patches, Production Systems.
-
 Ensuring Seamless Telecom Networks With Security Patch Management Process
Ensuring Seamless Telecom Networks With Security Patch Management ProcessFollowing slide highlights enabling of seamless telecom networks with security patch management process. The purpose of this template is to help businesses protect their networks to provide uninterrupted services and reliability of their offerings. It includes elements such as securing 5G network, etc.Introducing our premium set of slides with Ensuring Seamless Telecom Networks With Security Patch Management Process. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Vulnerability, Network Performance, Response Planning. So download instantly and tailor it with your information.
-
 Ensuring Security Compliance For Banking Systems With Patch Management Process
Ensuring Security Compliance For Banking Systems With Patch Management ProcessFollowing slide showcases process of patch management to ensure security of banking systems. The purpose of this slide is to outline a series of steps to align with industry regulations while maintaining the security and stability of financial operations. It includes steps such as regulatory framework, etc.Presenting our set of slides with Ensuring Security Compliance For Banking Systems With Patch Management Process. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Vulnerability Management, Compliance Validation, Documentation Improvement
-
 Icon For Adaption Of Security Patch Management Process For E Learning
Icon For Adaption Of Security Patch Management Process For E LearningIntroducing our Icon For Adaption Of Security Patch Management Process For E Learning set of slides. The topics discussed in these slides are Icon Adaption, Security Patch Management, Process E Learning. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Icon For Security Patch Management Process In Tech Companies
Icon For Security Patch Management Process In Tech CompaniesPresenting our well structured Icon For Security Patch Management Process In Tech Companies. The topics discussed in this slide are Icon Security, Patch Management, Process Tech Companies. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Importance Of Security Patch Management Process In Modern Business
Importance Of Security Patch Management Process In Modern BusinessFollowing slide highlights the necessity of security patch management process in business. The purpose of this template is to assist businesses in protecting their data from attacks and reduce unnecessary expenditures. It includes elements such as protection against cyberattacks, compliance with regulations, etc.Presenting our set of slides with Importance Of Security Patch Management Process In Modern Business. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Against Cyberattacks, Address Vulnerabilities, Maintain Compliance
-
 Patch Management Process For Ensuring Corporate Security
Patch Management Process For Ensuring Corporate SecurityFollowing slide showcases security patch management process for financial sector. The purpose of this slide is to summarize key steps for protecting customer data and ensuring regulatory compliance while maintaining the integrity of financial operations. It includes stages such as inventory and assessment, etc.Introducing our premium set of slides with Patch Management Process For Ensuring Corporate Security. Ellicudate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Training Improvement, Monitoring Response, Inventory Assessment. So download instantly and tailor it with your information.
-
 Reducing Downtime With Security Patch Management Process
Reducing Downtime With Security Patch Management ProcessFollowing slide showcases security patch management process for minimizing downtime. The purpose of this slide is to aid businesses in striking a balance between secure environment and smooth business operations for minimizing downtime. It includes steps such as patch testing, automated deployment, etc.Presenting our set of slides with Reducing Downtime With Security Patch Management Process. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Regular Maintenance, Performance Testing, Monitoring Alerting.
-
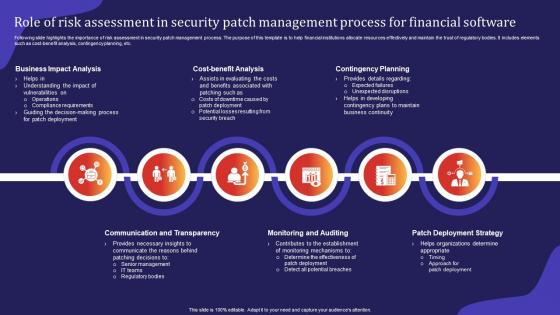 Role Of Risk Assessment In Security Patch Management Process For Financial Software
Role Of Risk Assessment In Security Patch Management Process For Financial SoftwareFollowing slide highlights the importance of risk assessment in security patch management process. The purpose of this template is to help financial institutions allocate resources effectively and maintain the trust of regulatory bodies. It includes elements such as cost benefit analysis, contingency planning, etc.Introducing our premium set of slides with Role Of Risk Assessment In Security Patch Management Process For Financial Software. Ellicudate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Contingency Planning, Communication Transparency, Monitoring Auditing. So download instantly and tailor it with your information.
-
 Security Patch Management Process For Healthcare IT Systems
Security Patch Management Process For Healthcare IT SystemsFollowing slide showcases the healthcare industry security patch management process. The purpose of this slide is to help healthcare organizations in ensuring that their IT systems are patched safely and effectively. It includes steps such as define, identify and prioritize, etc.Presenting our set of slides with Security Patch Management Process For Healthcare IT Systems. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Roles Responsibilities, Ensure Introduced, Deployment Depends.
-
 Security Patch Management Process Ppt Powerpoint Presentation File Gallery
Security Patch Management Process Ppt Powerpoint Presentation File GalleryPresenting our well structured Security Patch Management Process Ppt Powerpoint Presentation File Gallery. The topics discussed in this slide are Security Patch, Management Process. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Strengthening Logistics Security With Patch Management Process
Strengthening Logistics Security With Patch Management ProcessFollowing slide showcases patch management process for enhancing logistics security. The purpose of this template is to help businesses foster secure operations, maintain continuity for activities and uphold customer trust. It includes elements such as long term protection, securing data integrity, etc.Presenting our set of slides with Strengthening Logistics Security With Patch Management Process. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Vendor Security Collaboration, Response Preparation, Securing Data Integrity.
-
 Unique Security Patch Management Process For Online Retailers
Unique Security Patch Management Process For Online RetailersThis slide highlights the e commerce business security patch management process. The purpose of this slide is to help businesses in ensuring a smooth e commerce experience while maintaining industry standards. It includes steps such as regulatory focus, risk assessment, etc.Introducing our premium set of slides with Unique Security Patch Management Process For Online Retailers. Ellicudate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Automated Deployment, Effective Communication, Thorough Testing. So download instantly and tailor it with your information.
-
 Firewall Migration Proposal Our Process For Migrating Firewall Network Security
Firewall Migration Proposal Our Process For Migrating Firewall Network SecurityThis slide outlines the process of a firewall service provider company to replace a legacy firewall solution with a new one in an organization. The process steps include assessment and requirements gathering, solution design and planning, pre-migration preparation, etc. Present the topic in a bit more detail with this Firewall Migration Proposal Our Process For Migrating Firewall Network Security. Use it as a tool for discussion and navigation on Assessment And Requirements Gathering, Solution Design And Planning, Migration Execution. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE Network Security Cloud Access Security Broker Working Process
SASE Network Security Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using SASE Network Security Cloud Access Security Broker Working Process. This template helps you present information on three stages. You can also present information on Discovery, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Adopt Security Auditing Checklist To Verify Processes Hands On Blockchain Security Risk BCT SS V
Adopt Security Auditing Checklist To Verify Processes Hands On Blockchain Security Risk BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Adopt Security Auditing Checklist To Verify Processes Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Parameters, Description, Comments. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview And Workflow Process Of Eclipse Attack Hands On Blockchain Security Risk BCT SS V
Overview And Workflow Process Of Eclipse Attack Hands On Blockchain Security Risk BCT SS VThe following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer-to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. Introducing Overview And Workflow Process Of Eclipse Attack Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Enabled Attack, Achieve Control, Incoming And Outgoing, using this template. Grab it now to reap its full benefits.
-
 Overview And Working Process Of Ddos Attack Hands On Blockchain Security Risk BCT SS V
Overview And Working Process Of Ddos Attack Hands On Blockchain Security Risk BCT SS VThe following slide illustrates brief introduction of distributed denial of service DDOS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc. Increase audience engagement and knowledge by dispensing information using Overview And Working Process Of Ddos Attack Hands On Blockchain Security Risk BCT SS V. This template helps you present information on four stages. You can also present information on Website Hostage, Close The Attack, Inability To Resolve using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Audit Process For Digital Ecosystem
Cyber Security Audit Process For Digital EcosystemThis slide elaborates on cybersecurity audit process and provides details about how to implement protection in a digital ecosystem. It includes elements such as build blueprint, audit frequently, etc. Presenting our set of slides with Cyber Security Audit Process For Digital Ecosystem. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Define Audit Purpose, Build Blueprint, Identify Evaluate Risk Management.
-
 NEO Banks For Digital Funds Two Factor Authentication Process Flow For Enhanced Security Fin SS V
NEO Banks For Digital Funds Two Factor Authentication Process Flow For Enhanced Security Fin SS VThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Deliver an outstanding presentation on the topic using this NEO Banks For Digital Funds Two Factor Authentication Process Flow For Enhanced Security Fin SS V. Dispense information and present a thorough explanation of Authentication Process Flow, Enhanced Security, Verify Biometrics, Authentication Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Incident Management Process Icon
Security Incident Management Process IconPresenting our well structured Security Incident Management Process Icon. The topics discussed in this slide are Incident, Management, Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Blockchain And Cybersecurity Adopt Security Auditing Checklist To Verify Processes BCT SS V
Blockchain And Cybersecurity Adopt Security Auditing Checklist To Verify Processes BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Blockchain And Cybersecurity Adopt Security Auditing Checklist To Verify Processes BCT SS V Use it as a tool for discussion and navigation on Parameters, Description, Verify Processes This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS V
Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS V Dispense information and present a thorough explanation of Consensus Mechanism, Smart Contract Security, Data Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 HR Offboarding Process Mapping To Mitigate Security Risks
HR Offboarding Process Mapping To Mitigate Security RisksThis slide represents HR offboarding process mapping to mitigate security risks. It further includes manager request, replacement, job vacancy, preparation of resignation letter and health check, etc. Presenting our well structured HR Offboarding Process Mapping To Mitigate Security Risks. The topics discussed in this slide are Resignation, Documentation, Termination. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Build Cyber Security Team Structure Implementing Cyber Risk Management Process
Build Cyber Security Team Structure Implementing Cyber Risk Management ProcessThe following slide showcases the organizational cyber security team hierarchy to prevent sensitive data loss and damage. It mainly includes elements such as security manager, engineer, analyst, chief information security officer etc. Deliver an outstanding presentation on the topic using this Build Cyber Security Team Structure Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Security Analyst, Security Manager, Chief Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.




