Powerpoint Templates and Google slides for Security Controls
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Wireless LAN Security Best Practice Wireless LAN Controller
Wireless LAN Security Best Practice Wireless LAN ControllerThis slide represents the best practices for wireless LAN security such as SSID segmentation, guest wi fi, signal strength control, etc. Introducing Wireless LAN Security Best Practice Wireless LAN Controller to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Rogue AP Detection, Wireless LAN, Security Best Practice, using this template. Grab it now to reap its full benefits.
-
 Wireless LAN Security Threats And Tactics Wireless LAN Controller
Wireless LAN Security Threats And Tactics Wireless LAN ControllerThe purpose of this slide is to highlight the wireless LAN security threats and tactics such as IP and MAC spoofing, DODOS botnets and name in the middle attacks, etc. Present the topic in a bit more detail with this Wireless LAN Security Threats And Tactics Wireless LAN Controller. Use it as a tool for discussion and navigation on Deceiving Connected Clients, Distributed Denial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Wireless Local Area Network Security Overview Wireless LAN Controller
Wireless Local Area Network Security Overview Wireless LAN ControllerThis slide is to highlight the wireless local network security such as data theft concerns, prevention measures, protection scope, etc. Increase audience engagement and knowledge by dispensing information using Wireless Local Area Network Security Overview Wireless LAN Controller. This template helps you present information on three stages. You can also present information on Theft Concerns, Preventive Measures, Protection Scope using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Smart Endpoint Application Control For Reduced Building Next Generation Endpoint Security Cybersecurity SS
Smart Endpoint Application Control For Reduced Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases smart endpoint app control process. It can help developers reduce attacks through blocklist rules, risk assessment, recommendation engine, etc.Deliver an outstanding presentation on the topic using this Smart Endpoint Application Control For Reduced Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Symantec Application Control, Symantec Application Control, Recommendation Engine using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Control Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Information Security Control Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon represents a client onboarding checklist, designed to streamline the process and optimize resource utilization. With its eye-catching design and clear visual cues, this icon is perfect for presentations and documents related to client onboarding procedures and strategies.
-
 Information Security Control Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Information Security Control Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is designed to assist with client onboarding checklists, ensuring efficient resource utilization. With a sleek and minimalist design, this icon is perfect for presentations and documents related to client onboarding processes. It is a must-have for any business looking to streamline their onboarding procedures.
-
 Framework for big data control and security presentation outline
Framework for big data control and security presentation outlinePresenting framework for big data control and security presentation outline. This is a framework for big data control and security presentation outline. This is a four stage process. The stages in this process are define, data discovery, data classification, dissect, data intelligence, data analytics.
-
 Kpi for average backup time security controls risks identified powerpoint slide
Kpi for average backup time security controls risks identified powerpoint slidePresenting kpi for average backup time security controls risks identified powerpoint slide. This presentation slide shows three Key Performance Indicators or KPIs in a Dashboard style design. The first KPI that can be shown is Average Time Between Tests of Backup. The second KPI is Proportion of Information Security Risks for Which Satisfactory Controls Have Been Fully Implemented and the third is Relative Proportions of Risks Identified. These KPI Powerpoint graphics are all data driven,and the shape automatically adjusts according to your data. Just right click on the KPI graphic,enter the right value and the shape will adjust automatically. Make a visual impact with our KPI slides.
-
 Kpi for security control time flights diverted non aviation activities presentation slide
Kpi for security control time flights diverted non aviation activities presentation slidePresenting KPI For Security Control Time Flights Diverted Non Aviation Activities Presentation Slide. This presentation design has been professionally designed, is fully editable in PowerPoint and is compatible with Google slides as well. The font type, font size, colors of the diagrams, background color are customizable, and the company logo can be added too. High quality graphs, charts, tables and icons ensure that there is no deteriorating in quality on enlarging their size. Fast download at click of a button.
-
 Security controls framework ppt powerpoint presentation slides clipart cpb
Security controls framework ppt powerpoint presentation slides clipart cpbPresenting this set of slides with name - Security Controls Framework Ppt Powerpoint Presentation Slides Clipart Cpb. This is an editable six stages graphic that deals with topics like Security Controls Framework to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Controls information security ppt powerpoint presentation file design ideas cpb
Controls information security ppt powerpoint presentation file design ideas cpbPresenting this set of slides with name - Controls Information Security Ppt Powerpoint Presentation File Design Ideas Cpb. This is an editable three stages graphic that deals with topics like Controls Information Security to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Wireless remote control for system security
Wireless remote control for system securityPresenting our set of slides with Wireless Remote Control For System Security. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Wireless Remote Control For System Security.
-
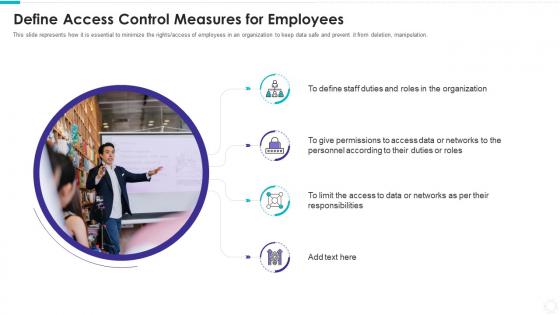 Electronic information security define access control measures employees
Electronic information security define access control measures employeesThis slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Introducing Electronic Information Security Define Access Control Measures Employees to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Organization, Data Or Networks, Personnel According, Responsibilities, using this template. Grab it now to reap its full benefits.
-
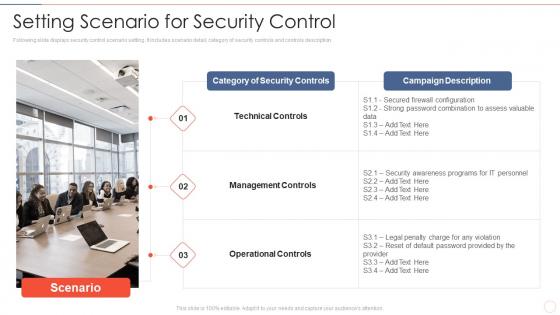 Setting scenario security control effective information security risk management process
Setting scenario security control effective information security risk management processFollowing slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description.Introducing Setting Scenario Security Control Effective Information Security Risk Management Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Controls, Operational Controls, Technical Controls, using this template. Grab it now to reap its full benefits.
-
 How financial risk can be controlled managing critical threat vulnerabilities and security threats
How financial risk can be controlled managing critical threat vulnerabilities and security threatsThis slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Increase audience engagement and knowledge by dispensing information using How Financial Risk Can Be Controlled Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on three stages. You can also present information on Liquidity Risk, Exchange Risk, Credit Exchange Risk using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How financial risk can be controlled corporate security management
How financial risk can be controlled corporate security managementThis slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Increase audience engagement and knowledge by dispensing information using How Financial Risk Can Be Controlled Corporate Security Management. This template helps you present information on three stages. You can also present information on Handling Liquidity Risk, Foreign Exchange Risk, Credit Exchange Risk using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key security controls to be addressed in the program managing cyber risk in a digital age
Key security controls to be addressed in the program managing cyber risk in a digital agePurpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Increase audience engagement and knowledge by dispensing information using Key Security Controls To Be Addressed In The Program Managing Cyber Risk In A Digital Age. This template helps you present information on three stages. You can also present information on Framework, Elaborates, Security, Controls, Recovery using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ai based automation of cyber threat security controls
Ai based automation of cyber threat security controlsThe following slide highlights the threat security controls which are integrated with artificial intelligence which includes RPA and ML. Introducing our AI Based Automation Of Cyber Threat Security Controls set of slides. The topics discussed in these slides are Cyber Threat Security, Automated Control Management, Control And Vulnerability Reporting. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Types Security Controls Ppt Powerpoint Presentation Model Samples Cpb
Types Security Controls Ppt Powerpoint Presentation Model Samples CpbPresenting our Types Security Controls Ppt Powerpoint Presentation Model Samples Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Types Security Controls. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Endpoint security controls checklist ppt powerpoint presentation infographic template cpb
Endpoint security controls checklist ppt powerpoint presentation infographic template cpbPresenting our Endpoint Security Controls Checklist Ppt Powerpoint Presentation Infographic Template Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Endpoint Security Controls Checklist This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Information Security Define Access Control Measures For Employees
Information Security Define Access Control Measures For EmployeesThis slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Introducing Information Security Define Access Control Measures For Employees to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Control, Measures, Employees, using this template. Grab it now to reap its full benefits.
-
 Information Security Program Cybersecurity Setting Scenario For Cybersecurity Control
Information Security Program Cybersecurity Setting Scenario For Cybersecurity ControlFollowing slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Setting Scenario For Cybersecurity Control. Dispense information and present a thorough explanation of Technical Controls, Management Controls, Operational Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Key Security Controls To Be Addressed In The Program
Information Security Program Key Security Controls To Be Addressed In The ProgramPurpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Deliver an outstanding presentation on the topic using this Information Security Program Key Security Controls To Be Addressed In The Program. Dispense information and present a thorough explanation of Prevents Attacks, Limits Extent Of Attacks, Data Recovery using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Framework For Information Security Setting Scenario For Security Control
Risk Management Framework For Information Security Setting Scenario For Security ControlFollowing slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. Present the topic in a bit more detail with this Risk Management Framework For Information Security Setting Scenario For Security Control. Use it as a tool for discussion and navigation on Category Security Controls, Controls Description, Operational Controls, Management Controls, Technical Controls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Management Framework Setting Scenario For Security Control
Cybersecurity Risk Management Framework Setting Scenario For Security ControlFollowing slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. Increase audience engagement and knowledge by dispensing information using Cybersecurity Risk Management Framework Setting Scenario For Security Control. This template helps you present information on three stages. You can also present information on Technical Controls, Management Controls, Operational Controls using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Security Controls To Be Addressed In The Program Risk Based Methodology To Cyber
Key Security Controls To Be Addressed In The Program Risk Based Methodology To CyberPurpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications.Present the topic in a bit more detail with this Key Security Controls To Be Addressed In The Program Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Prevents Attacks, Limits Extent Of Attacks, Data Recovery This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Security Controls To Be Addressed In The Program Introducing A Risk Based Approach
Key Security Controls To Be Addressed In The Program Introducing A Risk Based ApproachPurpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications.Deliver an outstanding presentation on the topic using this Key Security Controls To Be Addressed In The Program Introducing A Risk Based Approach Dispense information and present a thorough explanation of Restrict Admin Privileges, Factor Authentication, Limits Extent Of Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Setting Scenario For Cybersecurity Control Introducing A Risk Based Approach To Cyber Security
Setting Scenario For Cybersecurity Control Introducing A Risk Based Approach To Cyber SecurityFollowing slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description.Present the topic in a bit more detail with this Setting Scenario For Cybersecurity Control Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Technical Controls, Management Controls, Operational Controls This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management how financial risk can be controlled
Cyber security risk management how financial risk can be controlledThis slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Introducing Cyber Security Risk Management How Financial Risk Can Be Controlled to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Handling Liquidity Risk, Handling Foreign Exchange Risk, Handling Credit Exchange Risk, using this template. Grab it now to reap its full benefits.
-
 Iso 27001 performance indicators to measure information security controls ppt slides
Iso 27001 performance indicators to measure information security controls ppt slidesFollowing slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver an outstanding presentation on the topic using this ISO 27001 Performance Indicators To Measure Information Security Controls Ppt Slides. Dispense information and present a thorough explanation of Information Security Policy, Information Security Training, Asset Inventory using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Incorporation Isms Framework Into Corporate Control Processes
Information Security And Iso 27001 Incorporation Isms Framework Into Corporate Control ProcessesMentioned slide displays the incorporation of information security management system framework within the corporate control process. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Incorporation Isms Framework Into Corporate Control Processes. Dispense information and present a thorough explanation of Framework, Corporate, Processes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Performance Indicators To Measure Information Security Controls
Information Security And Iso 27001 Performance Indicators To Measure Information Security ControlsFollowing slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Present the topic in a bit more detail with this Information Security And Iso 27001 Performance Indicators To Measure Information Security Controls. Use it as a tool for discussion and navigation on Performance, Indicators, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Define Access Control Measures For Employees
Network Security Define Access Control Measures For EmployeesThis slide represents how it is essential to minimize the rights access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Increase audience engagement and knowledge by dispensing information using Network Security Define Access Control Measures For Employees. This template helps you present information on four stages. You can also present information on Organization, Duties, Roles, Permissions, Personnel using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 5 Operational Technology Security Controls To Improve It Security
5 Operational Technology Security Controls To Improve It SecurityFollowing slide depict operational technology OT security controls ways that can be used by an organization. Organization can enhance the security of IT infrastructure by using security controls such as update asset inventory, training, managing portable media, backup and restore and implementing secure configuration. Present the topic in a bit more detail with this 5 Operational Technology Security Controls To Improve IT Security. Use it as a tool for discussion and navigation on Update Asset Inventory, Training Manage, Portable Media, Backup And Restore, Secure Configuration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Define Access Control Measures For Employees
Information Technology Security Define Access Control Measures For EmployeesThis slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Increase audience engagement and knowledge by dispensing information using Information Technology Security Define Access Control Measures For Employees. This template helps you present information on four stages. You can also present information on Organization, Permissions, Responsibilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Access Control Methods Information Security Ppt Powerpoint Presentation Pictures Visual Aids Cpb
Access Control Methods Information Security Ppt Powerpoint Presentation Pictures Visual Aids CpbPresenting our Access Control Methods Information Security Ppt Powerpoint Presentation Pictures Visual Aids Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Access Control Methods Information Security. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Building organizational security strategy plan determine user access controls levels
Building organizational security strategy plan determine user access controls levelsThis slide provides information about information user access controls levels for access critical assets and information associated to firm and levels of access for administrator, maintainer, guest or disabled. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Determine User Access Controls Levels. Use it as a tool for discussion and navigation on Information, Administrator, Associated. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Generation internet security controls ppt powerpoint presentation outline grid cpb
Generation internet security controls ppt powerpoint presentation outline grid cpbPresenting our Generation Internet Security Controls Ppt Powerpoint Presentation Outline Grid Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Generation Internet Security Controls. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cybersecurity and digital business risk management key security controls to be addressed
Cybersecurity and digital business risk management key security controls to be addressedPurpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Increase audience engagement and knowledge by dispensing information using Cybersecurity And Digital Business Risk Management Key Security Controls To Be Addressed. This template helps you present information on three stages. You can also present information on Framework, Authentification, Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware
Incident Response Playbook Security Controls To Reduce The Risk Of RansomwareMentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Present the topic in a bit more detail with this Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware. Use it as a tool for discussion and navigation on Impact Category, Functional Impact, Informational Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Security Checklist Access Control Cloud Information Security
Cloud Security Checklist Access Control Cloud Information SecurityThis slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management.Introducing Cloud Security Checklist Access Control Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Service Provider, Physical Access, Natural Disasters using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats End User Control Cloud Information Security
Cloud Security Threats End User Control Cloud Information SecurityThis slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats.Introducing Cloud Security Threats End User Control Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Wisely Considering, Storage Location, Procedures Strategies using this template. Grab it now to reap its full benefits.
-
 Measures And Controls In Cloud Security Cloud Information Security
Measures And Controls In Cloud Security Cloud Information SecurityThis slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls.Increase audience engagement and knowledge by dispensing information using Measures And Controls In Cloud Security Cloud Information Security This template helps you present information on four stages. You can also present information on Implement Information, Restrict Data, Implement Advanced using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Computing Security Measures And Controls In Cloud Security
Cloud Computing Security Measures And Controls In Cloud SecurityThis slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls. Introducing Cloud Computing Security Measures And Controls In Cloud Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Preventive Control, Corrective Control, Detective Control, Deterrent Control, Cloud Security, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Access Control Cloud Computing Security
Cloud Security Checklist Access Control Cloud Computing SecurityThis slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Introducing Cloud Security Checklist Access Control Cloud Computing Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Multi Factor Authorization, Cloud Services, Networks, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats End User Control Cloud Computing Security
Cloud Security Threats End User Control Cloud Computing SecurityThis slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats. Introducing Cloud Security Threats End User Control Cloud Computing Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Centralized Data, Cloud Security Threats, End User Control, using this template. Grab it now to reap its full benefits.
-
 Information Security Controls Ppt Powerpoint Presentation Model Professional Cpb
Information Security Controls Ppt Powerpoint Presentation Model Professional CpbPresenting Information Security Controls Ppt Powerpoint Presentation Model Professional Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Information Security Controls. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Network Security Control Devices In Powerpoint And Google Slides Cpb
Network Security Control Devices In Powerpoint And Google Slides CpbPresenting our Network Security Control Devices In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Network Security Control Devices. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Performance Indicators To Measure Information Security Controls Iso 27001certification Process
Performance Indicators To Measure Information Security Controls Iso 27001certification ProcessFollowing slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver an outstanding presentation on the topic using this Performance Indicators To Measure Information Security Controls Iso 27001certification Process. Dispense information and present a thorough explanation of Performance, Measure, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Security Checklist Access Control Cloud Data Protection
Cloud Security Checklist Access Control Cloud Data ProtectionThis slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Introducing Cloud Security Checklist Access Control Cloud Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Cloud Services, Information, Data Servers, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats End User Control Cloud Data Protection
Cloud Security Threats End User Control Cloud Data ProtectionThis slide represents the end-user threat in cloud security and how an organization needs to control user access and be aware of potential threats. Introducing Cloud Security Threats End User Control Cloud Data Protection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Business Data, Customers, Centralized Data, using this template. Grab it now to reap its full benefits.
-
 Measures And Controls In Cloud Security Cloud Data Protection
Measures And Controls In Cloud Security Cloud Data ProtectionThis slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls. Introducing Measures And Controls In Cloud Security Cloud Data Protection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Corrective Control, Detective Control, Preventive Control, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Risk Management Approach With Risk Priority And Control
Cyber Security Risk Management Approach With Risk Priority And ControlThe following slide highlights the cyber security risk management approach with risk priority and control it illustrates risk priority, mitigation, controls, automation, governance and risk culture, which helps organisation to train workforce for cyber awareness and define company policy for cyber security. Presenting our set of slides with name Cyber Security Risk Management Approach With Risk Priority And Control. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Governance, Risk Priority, Mitigation.
-
 Business Security And Automation Control System
Business Security And Automation Control SystemThe purpose of this slide is to highlight the incorporation between business security and automation system which enables faster threat detection along with prominent control measures. The automated security system includes alarm systems, fire emergency buttons, control systems, and surveillance systems. Introducing our Business Security And Automation Control System set of slides. The topics discussed in these slides are Siren Alarm Systems, Fire Emergency Buttons, Control System. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Obtaining ISO 27001 Certificate Performance Indicators To Measure Information Security Controls
Obtaining ISO 27001 Certificate Performance Indicators To Measure Information Security ControlsFollowing slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver an outstanding presentation on the topic using this Obtaining ISO 27001 Certificate Performance Indicators To Measure Information Security Controls. Dispense information and present a thorough explanation of Control, Performance Indicator Formula, Target, Periodicity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Review And Control Matrix
Cyber Security Risk Review And Control MatrixThe purpose of this slide is to define the level of hazards and their severity in cybersecurity management along with priority levels 1-5 to manage risks. This is categorized as certain, likely, possible, unlikely, and rare. Introducing our Cyber Security Risk Review And Control Matrix set of slides. The topics discussed in these slides are Risk Matrix, Minor, Priority Levels. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 IT Risk Management Strategies Detection And Prevention Of Management Security Controls
IT Risk Management Strategies Detection And Prevention Of Management Security ControlsThe following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Introducing IT Risk Management Strategies Detection And Prevention Of Management Security Controls to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Preventive Management, Security Controls, Detection Management, using this template. Grab it now to reap its full benefits.
-
 IT Risk Management Strategies Security Criteria And Control Measures For IT System Vulnerabilities
IT Risk Management Strategies Security Criteria And Control Measures For IT System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Introducing IT Risk Management Strategies Security Criteria And Control Measures For It System Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Security, Operational Security, Technical Security, using this template. Grab it now to reap its full benefits.
-
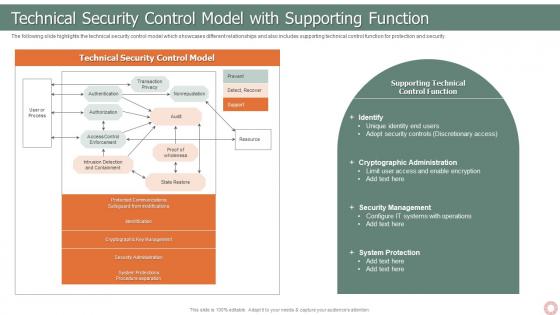 IT Risk Management Strategies Technical Security Control Model With Supporting Function
IT Risk Management Strategies Technical Security Control Model With Supporting FunctionThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Introducing IT Risk Management Strategies Technical Security Control Model With Supporting Function to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Technical Security, Control Model, Transaction Privacy, State Restore, using this template. Grab it now to reap its full benefits.
-
 Enterprise Risk Management Detection And Prevention Of Management Security Controls
Enterprise Risk Management Detection And Prevention Of Management Security ControlsThe following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Increase audience engagement and knowledge by dispensing information using Enterprise Risk Management Detection And Prevention Of Management Security Controls. This template helps you present information on two stages. You can also present information on Preventive Management, Security Controls, Detection Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





