Powerpoint Templates and Google slides for Security Controls
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Controls Powerpoint PPT Template Bundles
Cyber Security Controls Powerpoint PPT Template BundlesDeliver a credible and compelling presentation by deploying this Cyber Security Controls Powerpoint PPT Template Bundles Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The fourteen slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Cyber Security Controls Powerpoint PPT Template Bundles PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Physical Security And Environmental Controls In Cybersecurity Training Ppt
Physical Security And Environmental Controls In Cybersecurity Training PptPresenting Physical Security and Environmental Controls in Cybersecurity. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Objectives Of Physical Security And Environmental Controls Training Ppt
Objectives Of Physical Security And Environmental Controls Training PptPresenting Objectives of Physical Security and Environmental Controls. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Application Security Controls In Cybersecurity Training Ppt
Application Security Controls In Cybersecurity Training PptPresenting Application Security Controls in Cybersecurity. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Preventative Controls In Application Security Training Ppt
Preventative Controls In Application Security Training PptPresenting Preventative Controls in Application Security. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Corrective Controls In Application Security Training Ppt
Corrective Controls In Application Security Training PptPresenting Corrective Controls in Application Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Detective Controls In Application Security Training Ppt
Detective Controls In Application Security Training PptPresenting Detective Controls in Application Security. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Network Access Control As An Element Of Network Security Training Ppt
Network Access Control As An Element Of Network Security Training PptPresenting Network Access Control as an Element of Network Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Security Controls Management Cyberattacks Organization Infrastructure Investments
Security Controls Management Cyberattacks Organization Infrastructure InvestmentsIf you require a professional template with great design, then this Security Controls Management Cyberattacks Organization Infrastructure Investments is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twelve slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Blockchain security data protection risk control incident management
Blockchain security data protection risk control incident managementEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Blockchain Security Data Protection Risk Control Incident Management is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With twelve slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
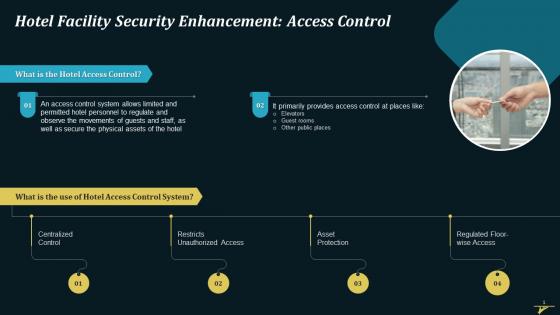 Enhanced Hotel Facility Security With Access Control Training Ppt
Enhanced Hotel Facility Security With Access Control Training PptPresenting Enhanced Hotel Facility Security with Access Control. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizablealter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Cyber Security Attack Control Dashboard
Cyber Security Attack Control DashboardThis slide highlights the data to track cyber attack attempted on the company to analyze and make strategies to prevent from these attacks and protect sensitive data. It includes various KPIs such as malicious emails, malicious files, malicious websites, etc. Introducing our Cyber Security Attack Control Dashboard set of slides. The topics discussed in these slides are Malicious Emails, Malicious Files, Malicious Websites This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Building Access Control Security Market Snapshot
Building Access Control Security Market SnapshotThis slide showcases the building access control security market size referable for users,investors and business owners for making relevant decisions. It include details such as increase in the demand for advanced technologies and rise of 5g networks. Introducing our Building Access Control Security Market Snapshot set of slides. The topics discussed in these slides are Market Size,Projections USD Bn,Top Companies. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data security it define access control measures for employees
Data security it define access control measures for employeesThis slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Increase audience engagement and knowledge by dispensing information using Data Security IT Define Access Control Measures For Employees. This template helps you present information on four stages. You can also present information on Data, Networks, Roles, Organization, Data Or Networks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer system security define access control measures for employees
Computer system security define access control measures for employeesThis slide represents how it is essential to minimize the rights oraccess of employees in an organization to keep data safe and prevent it from deletion, manipulation. Introducing Computer System Security Define Access Control Measures For Employees to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Organization, Responsibilities, Access, using this template. Grab it now to reap its full benefits.
-
 Key Access Security Control Models Delivering ICT Services For Enhanced Business Strategy SS V
Key Access Security Control Models Delivering ICT Services For Enhanced Business Strategy SS VThis slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control, Deliver an outstanding presentation on the topic using this Key Access Security Control Models Delivering ICT Services For Enhanced Business Strategy SS V. Dispense information and present a thorough explanation of Access Control Method, Description using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementation Of Information Key Access Security Control Models Strategy SS V
Implementation Of Information Key Access Security Control Models Strategy SS VThis slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role based access control and attributes based access control, Present the topic in a bit more detail with this Implementation Of Information Key Access Security Control Models Strategy SS V. Use it as a tool for discussion and navigation on Discretionary Access, Mandatory Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Operational Technology Security Controls To Enhance Safety Guide For Integrating Technology Strategy SS V
Operational Technology Security Controls To Enhance Safety Guide For Integrating Technology Strategy SS VThis slide covers operational technology security controls to improve IT safety. It involves five kinds of security controls such as update asset inventory, training, ,manage portable media and secure configuration. Introducing Operational Technology Security Controls To Enhance Safety Guide For Integrating Technology Strategy SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Update Asset Inventory, Portable Media, Backup And Restore, using this template. Grab it now to reap its full benefits.
-
 Information Security Plan Control Measures
Information Security Plan Control MeasuresThis slide covers types of information security plan control parameters which provides safeguard and countermeasures for protecting information of organization. It involves preventive control, detective control and corrective control. Presenting our set of slides with Information Security Plan Control Measures. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Preventive Controls, Detective Controls, Corrective Controls.
-
 Steps To Place Information Security Control Plan
Steps To Place Information Security Control PlanThis slide highlights stages to place information security control measures for protecting defences and risks of business effectively. It involves deter, deny, detect, delay, correct and recover. Introducing our premium set of slides with Steps To Place Information Security Control Plan. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Deter, Correct, Recover. So download instantly and tailor it with your information.
-
 Cloud Access Security Broker CASB V2 Cloud Security Standards And Control Frameworks
Cloud Access Security Broker CASB V2 Cloud Security Standards And Control FrameworksThis slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Cloud Security Standards And Control Frameworks. Use it as a tool for discussion and navigation on Payment Card Industry, Data Security Standard, System And Organization Controls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Access Control Security ID Card Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Access Control Security ID Card Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful icon is perfect for use in PowerPoint presentations. It features a modern ID card design with a bright background and a unique, eye catching shape. Its sure to help make your slides stand out and draw attention to your message.
-
 Access Control Security ID Card Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Access Control Security ID Card Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon on ID Card is perfect for any presentation. It is a simple, professional design that is sure to make a statement. It is easy to use and customize, so you can create the perfect look for your project.
-
 Strategic Plan To Implement Key Access Security Control Models Strategy SS V
Strategic Plan To Implement Key Access Security Control Models Strategy SS VThis slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control. Deliver an outstanding presentation on the topic using this Strategic Plan To Implement Key Access Security Control Models Strategy SS V Dispense information and present a thorough explanation of This slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control, using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Access Control Database Security In Powerpoint And Google Slides Cpb
Access Control Database Security In Powerpoint And Google Slides CpbPresenting our Access Control Database Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Access Control Database Security. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Security Breach Access Control In Powerpoint And Google Slides Cpb
Security Breach Access Control In Powerpoint And Google Slides CpbPresenting our Security Breach Access Control In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Security Breach Access Control This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Layered Defence Security Control Measures
Layered Defence Security Control MeasuresThis slide covers types of layered defence control parameters which provides safeguard and countermeasures for protecting crucial information. It involves preventive control, detective control and corrective control. Introducing our premium set of slides with Layered Defence Security Control Measures. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Preventive Controls, Detective Controls, Corrective Controls. So download instantly and tailor it with your information.
-
 Biometric Security Control Icon For Digital Forensics
Biometric Security Control Icon For Digital ForensicsIntroducing our premium set of slides with Biometric Security Control Icon For Digital Forensics. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Biometric Security, Control Icon, Digital Forensics. So download instantly and tailor it with your information.
-
 Key Access Security Control Models Comprehensive Guide For Deployment Strategy SS V
Key Access Security Control Models Comprehensive Guide For Deployment Strategy SS VThis slide represents key access security control models for organizations It includes discretionary access control, mandatory access control, role based access control and attributes based access control,Present the topic in a bit more detail with this Key Access Security Control Models Comprehensive Guide For Deployment Strategy SS V Use it as a tool for discussion and navigation on Mandatory Access, Discretionary Access, Administrator Protected This template is free to edit as deemed fit for your organization Therefore download it now
-
 Information Security Management Controls To Enhance Data Integrity
Information Security Management Controls To Enhance Data IntegrityThis slide represents controls that help businesses to manage information security effectively from data breaches. It includes controls such as physical control, access control, procedural control, etc, Presenting our well structured Information Security Management Controls To Enhance Data Integrity. The topics discussed in this slide are Physical Control, Access Control, Procedural Control. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cloud Security Standards And Control Frameworks Next Generation CASB
Cloud Security Standards And Control Frameworks Next Generation CASBThis slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA. Present the topic in a bit more detail with this Cloud Security Standards And Control Frameworks Next Generation CASB Use it as a tool for discussion and navigation on Security Standard, Accountability, Protection Regulation This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Security Standards And Control Frameworks CASB Cloud Security
Cloud Security Standards And Control Frameworks CASB Cloud SecurityThis slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA. Deliver an outstanding presentation on the topic using this Cloud Security Standards And Control Frameworks CASB Cloud Security. Dispense information and present a thorough explanation of General Data Protection Regulation, System And Organization Controls, Payment Card Industry Data Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Document Control Security Measures Icon
Document Control Security Measures IconIntroducing our premium set of slides with Document Control Security Measures Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Measures, Security, Control. So download instantly and tailor it with your information.
-
 Access Control Safeguards In Application Security Ppt Diagram Templates
Access Control Safeguards In Application Security Ppt Diagram TemplatesThis slide highlights the introduction of access control safeguards in application security for preventing malicious attacks in applications. Introducing Access Control Safeguards In Application Security Ppt Diagram Templates to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Identity Confirmation, Regulating Resource Interaction, Application Security, using this template. Grab it now to reap its full benefits.
-
 Application Security Setting Up Access Control System In Organization
Application Security Setting Up Access Control System In OrganizationThis slide represents the installation process of access control system for application security in an organization. Increase audience engagement and knowledge by dispensing information using Application Security Setting Up Access Control System In Organization. This template helps you present information on ten stages. You can also present information on Combine Tools With Infrastructure, Implement And Utilize Tools, Select Access Control Models using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Types Of Access Control In Application Security
Types Of Access Control In Application SecurityThis slide outlines the different types of access control safeguards in application security which include Role-based Access Control RBAC, Access Control Lists, etc. Introducing Types Of Access Control In Application Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Mandatory Access Control, Discretionary Access Control, Application Security, using this template. Grab it now to reap its full benefits.
-
 Comparison Between Preventive And Detective Controls In Cyber Security
Comparison Between Preventive And Detective Controls In Cyber SecurityThis slide represents the comparison between preventative controls and detective controls in cyber security to prevent potential threats and secure data. It includes preventative controls and detective controls Presenting our set of slides with Comparison Between Preventive And Detective Controls In Cyber Security This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Preventative Control, Detective Control
-
 Cyber Security Attack Control Icon
Cyber Security Attack Control IconIntroducing our premium set of slides with Cyber Security Attack Control Icon Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security Attack Control Icon So download instantly and tailor it with your information.
-
 Cyber Security Controls Checklist For Business
Cyber Security Controls Checklist For BusinessThis slide highlights the checklist for cyber security controls to prevent business from cyber attacks and protect company confidential data. It includes various KPIs such as password management, privacy and security of sensitive data. Presenting our well structured Cyber Security Controls Checklist For Business The topics discussed in this slide are Password Management, Security Awareness This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Controls Software Comparative Analysis
Cyber Security Controls Software Comparative AnalysisThis slide highlights the comparative analysis of cyber security control software to protect confidential data and protection from data breach. It includes various factors such as features, ratings, etc Introducing our Cyber Security Controls Software Comparative Analysis set of slides. The topics discussed in these slides are Secpod Sanernow, Intruder, Solar Winds Security Event Manager This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Online Threat Control Icon
Cyber Security Online Threat Control IconPresenting our set of slides with Cyber Security Online Threat Control Icon This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Online Threat Control Icon
-
 NIST Cyber Security Control Framework For Business
NIST Cyber Security Control Framework For BusinessThis slide represents cyber security control NIST framework to help business in identifying potential threats of attacks or data breach. It includes various steps such as identify, protect, detect, respond and recover. Introducing our premium set of slides with NIST Cyber Security Control Framework For Business Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify, Protect, Detect So download instantly and tailor it with your information.
-
 Process To Determine Adequate Cyber Security Control
Process To Determine Adequate Cyber Security ControlThis slide represents the process to identifying adequate cyber security control for business to prevent online threats and implement necessary steps. It includes various steps such as evaluate size of the company, identify scope of IT infrastructure, etc. Presenting our set of slides with Process To Determine Adequate Cyber Security Control This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify Scope Of It Infrastructure, Evaluate Size Of Company, Investment In Cyber Security
-
 Types Of Detective Controls Cyber Security
Types Of Detective Controls Cyber SecurityThis slide represents the types of detective controls used in cyber security to prevent data breach by unauthorized access or online attack. It includes various steps such as log monitoring, SIEM, trend analysis, etc. Introducing our premium set of slides with Types Of Detective Controls Cyber Security Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Trend Analysis, Security Audits, Log Monitoring So download instantly and tailor it with your information.
-
 Types Of Preventative Controls In Cyber Security
Types Of Preventative Controls In Cyber SecurityThis slide represents the different type of preventative controls in cyber security to prevent leakage of confidential data by unauthorized access. It includes various steps such as hardening, security awareness training, change management, etc. Presenting our set of slides with Types Of Preventative Controls In Cyber Security This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Awareness Training, Hardening, Change Management
-
 Types Of Technical Controls In Cyber Security
Types Of Technical Controls In Cyber SecurityThis slide represents the various types of technical control in cyber security to monitor and track potential threats and prevent data breach. It includes various types such as encryptions, firewalls, antivirus software, etc. Introducing our premium set of slides with Types Of Technical Controls In Cyber Security Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Encryptions, Firewalls, Antivirus Software So download instantly and tailor it with your information.
-
 Various Types Of Cyber Security Controls
Various Types Of Cyber Security ControlsThis slide represents different types of cyber security controls to prevent from online threats and protect sensitive data. It includes various cyber security controls such as technical controls, preventative controls, detective controls, corrective controls, etc. Presenting our set of slides with Various Types Of Cyber Security Controls This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Technical Controls, Preventative Controls, Detective Controls
-
 Web Security Audit Controls To Reduce Threats
Web Security Audit Controls To Reduce ThreatsThis slide represents various security control methods to minimize threats to web security. The purpose of this slide is to help businesses in developing strategy for data protection. It provides techniques to minimize web security threats such as SQL injection, ransomware, denial of service attacks and phishing. Introducing our Web Security Audit Controls To Reduce Threats set of slides. The topics discussed in these slides are Ransomware, Service Attacks, Phishing This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Apply Authentication And Access Control Mechanisms Internet Of Things IoT Security Cybersecurity SS
Apply Authentication And Access Control Mechanisms Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of authentication and access control for internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about trust boundaries, identity authentication, etc. Increase audience engagement and knowledge by dispensing information using Apply Authentication And Access Control Mechanisms Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on three stages. You can also present information on Trust Boundaries, Identity Authentication, Access Protection Measures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Center For Internet Security Control Framework
Center For Internet Security Control FrameworkThis slide overviews the CIS Control framework which includes three major categories that are basic controls, foundational controls and organizational controls. Introducing Center For Internet Security Control Framework to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Foundational Controls, Organizational Controls, Internet Security, Control Framework , using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Steps To Deploy Efficient Access Control
Application Security Implementation Plan Steps To Deploy Efficient Access ControlThis slide discusses the process phases of implementing access control which include taking inventory of systems, examining staffs, etc. Introducing Application Security Implementation Plan Steps To Deploy Efficient Access Control to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Establish Roles, Resist Sporadic Adjustments, Examine The Staff, Take Inventory Of Systems, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Goals Of Device Control In Endpoint Security
Endpoint Security Goals Of Device Control In Endpoint SecurityThis slide represents the objectives of one of the components of endpoint security which is device control technique to strengthens secure endpoint. Introducing Endpoint Security Goals Of Device Control In Endpoint Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Customizable Device Access Rules, Goals Of Device Control, Endpoint Security, Strengthens Secure Endpoint, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Micro Endpoint Security Application Control
Endpoint Security Micro Endpoint Security Application ControlThis slide discusses about one of the components of endpoint security which is application control for data protection in devices. Introducing Endpoint Security Micro Endpoint Security Application Control to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Increase In Malware Defense, Data Protection, Prevent Unauthorized Applications, Optimal Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Cyber Threat Intelligence Security Control Solutions
Cyber Threat Intelligence Security Control SolutionsThis slide showcases cyber threat intelligence security control which helps managers improve threat detection and organizational defence capabilities. It includes elements such as strategic, tactical, operational, technical, high level, low level, short term use and long term use. Introducing our premium set of slides with name Cyber Threat Intelligence Security Control Solutions. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Strategic, Tactical, Operational, Technical. So download instantly and tailor it with your information.
-
 Physical Security Control Methods And Its Functions
Physical Security Control Methods And Its FunctionsThis slide showcases security control system types that are physical, technical and administrative controls. These help to prevent unauthorized access, maintain confidentiality, etc. Introducing our premium set of slides with Physical Security Control Methods And Its Functions. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Physical Controls, Technical Controls, Administrative Controls. So download instantly and tailor it with your information.
-
 Securing Food Safety In Online Key Aspects Of Quality Control In Food Deliver Process
Securing Food Safety In Online Key Aspects Of Quality Control In Food Deliver ProcessThis slide covers major aspects of maintaining food quality during delivery such as ingredient sourcing, packaging and waste control. Introducing Securing Food Safety In Online Key Aspects Of Quality Control In Food Deliver Process to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Ingredient Sourcing, Packaging, Waste Control, using this template. Grab it now to reap its full benefits.
-
 Enterprise Blockchain Solutions For Security Controls
Enterprise Blockchain Solutions For Security ControlsIntroducing our premium set of slides with Enterprise Blockchain Solutions For Security Controls. Ellicudate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Key Administration, Data Privacy, Ensured Communication. So download instantly and tailor it with your information.
-
 Near Field Communication NFC For Access Control Mobile Security
Near Field Communication NFC For Access Control Mobile SecurityThis slide represents the introduction of near field communication for access control which is based on radio frequency identification technology. Introducing Near Field Communication NFC For Access Control Mobile Security to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Relay Attack, Data Interception, Data Tampering using this template. Grab it now to reap its full benefits.
-
 Wireless LAN Controller Security Checklist Wireless LAN Controller
Wireless LAN Controller Security Checklist Wireless LAN ControllerThe purpose of this slide is to highlight the wireless LAN controller security checklist such as research device encryption, segmentation for less secure devices, etc. Present the topic in a bit more detail with this Wireless LAN Controller Security Checklist Wireless LAN Controller. Use it as a tool for discussion and navigation on Research Device Encryption, Restricted Guest Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Wireless LAN Cryptographic Security Algorithms Wireless LAN Controller
Wireless LAN Cryptographic Security Algorithms Wireless LAN ControllerThe purpose of this slide is to highlight the various wireless LAN cryptographic algorithm such as wired equivalent privacy, temporal key integrity proposal, etc. Increase audience engagement and knowledge by dispensing information using Wireless LAN Cryptographic Security Algorithms Wireless LAN Controller. This template helps you present information on two stages. You can also present information on Equivalent Privacy, Security Methods, Security Algorithms using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.




