Powerpoint Templates and Google slides for Attacker
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Social Engineering Attacks Overview And Types Social Engineering Attacks Prevention
Social Engineering Attacks Overview And Types Social Engineering Attacks PreventionThis slide discusses about social engineering process of manipulating victims to provide access to their confidential information. This slide also outlines the types of social engineering attacks, such as phishing, pretexting, baiting, tailgating, impersonation, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Attacks Overview And Types Social Engineering Attacks Prevention. This template helps you present information on five stages. You can also present information on Quid Pro Quo Attack, Watering Hole Attack, Tailgating, Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Attacks Prevention 30 60 90 Days Plan To Implement Social Engineering
Social Engineering Attacks Prevention 30 60 90 Days Plan To Implement Social EngineeringThis slide represents 30-60-90 plan to protect companies and their employees from social engineering attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Introducing Social Engineering Attacks Prevention 30 60 90 Days Plan To Implement Social Engineering to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Simulation Test, Implement Continuous Monitoring, Third Party Risk Assessment, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Attacks Prevention About Anti Phishing Solutions Types And Benefits
Social Engineering Attacks Prevention About Anti Phishing Solutions Types And BenefitsThis slide highlights the services available for social engineering prevention, such as browser-based, email-based and API-based. This slide also outlines the benefits of these services. These include risk identification, damage control, zero-trust security, etc. Present the topic in a bit more detail with this Social Engineering Attacks Prevention About Anti Phishing Solutions Types And Benefits. Use it as a tool for discussion and navigation on Reduce Cybersecurity Attacks, Zero Trust Security, Deliver Operational Efficiency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attacks Prevention Best Practices For Social Engineering Awareness Campaign
Social Engineering Attacks Prevention Best Practices For Social Engineering Awareness CampaignThis slide talks about the measures for successful social engineering awareness campaign. These include recognize phish, train staff while keeping their individual needs in mind, action-oriented employee engagement, plan constant training sessions, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Attacks Prevention Best Practices For Social Engineering Awareness Campaign. This template helps you present information on six stages. You can also present information on Plan Constant Training Sessions, Evaluate Training Outcomes, Consumable Tidbits Of Knowledge, Action Oriented Employee Engagement using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Attacks Prevention Business Benefits Of Comprehensive Training Programs
Social Engineering Attacks Prevention Business Benefits Of Comprehensive Training ProgramsThis slide outlines the benefits of comprehensive training programs in organizations. These include align with company database, instructional library, auto-enrolment service, inform about real risks, track and evaluate and plan a year ahead. Introducing Social Engineering Attacks Prevention Business Benefits Of Comprehensive Training Programs to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Track And Evaluate, Instructional Library, Comprehensive Training Programs, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Attacks Prevention Checklist To Secure Organizations From Social Engineering
Social Engineering Attacks Prevention Checklist To Secure Organizations From Social EngineeringThis slide outlines the steps to be taken to protect the organization and its employees from social engineering attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan. Present the topic in a bit more detail with this Social Engineering Attacks Prevention Checklist To Secure Organizations From Social Engineering. Use it as a tool for discussion and navigation on Provide Staff Training, Multi Factor Authentication, Develop An Incident Response Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attacks Prevention Common Attack Vectors For Social Engineering
Social Engineering Attacks Prevention Common Attack Vectors For Social EngineeringThis slide outlines the different components which result in successful social engineering attacks. These are software vulnerabilities, compromised credentials, weak passwords, malicious employees, poor encryption, ransomware, phishing, etc. Introducing Social Engineering Attacks Prevention Common Attack Vectors For Social Engineering to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Software Vulnerabilities, Compromised Credentials, Malicious Employees, Weak Passwords, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Attacks Prevention Comparison Of Different Anti-Phishing Solutions Providers
Social Engineering Attacks Prevention Comparison Of Different Anti-Phishing Solutions ProvidersThis slide compares the different anti-phishing solutions available in the market. It highlights the type of support provided, price and rating of various solutions. This slide also outlines the final service selection and the reasons supporting it. Deliver an outstanding presentation on the topic using this Social Engineering Attacks Prevention Comparison Of Different Anti-Phishing Solutions Providers. Dispense information and present a thorough explanation of Anti Phishing Solutions, Final Service Selection, Reasons Supporting, Abnormal Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Attacks Prevention Components Of Social Engineering Life Cycle
Social Engineering Attacks Prevention Components Of Social Engineering Life CycleThis slide represents the life cycle of the social engineering process. The main steps included are ground preparation for the attack, deceiving the victim to achieve a foothold, collecting the data over time, and closing the interaction without any suspicion. Increase audience engagement and knowledge by dispensing information using Social Engineering Attacks Prevention Components Of Social Engineering Life Cycle. This template helps you present information on four stages. You can also present information on Ground Preparation For Attack, Collecting The Information, Social Engineering Life Cycle, Taking Control Of The Conversation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Attacks Prevention Different Types Of Social Engineering Attacks
Social Engineering Attacks Prevention Different Types Of Social Engineering AttacksThis slide represents the different types of social engineering attacks based on technology and human interaction. These two types are further divided into components such as mobile-based, computer-based, voice-based, physical mode, etc. Introducing Social Engineering Attacks Prevention Different Types Of Social Engineering Attacks to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering Attacks, Physical Mode, Technology And Human Interaction, Email Phishing, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Attacks Prevention For Businesses For Table Of Contents
Social Engineering Attacks Prevention For Businesses For Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Social Engineering Attacks Prevention For Businesses For Table Of Contents. This template helps you present information on one stages. You can also present information on Resources And Training, Awareness Training Program, Training Budget using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Attacks Prevention Human Based Social Engineering Attacks
Social Engineering Attacks Prevention Human Based Social Engineering AttacksThis slide discusses the different human-based techniques used by social engineering scammers. These attacks include impersonation, tailgating, baiting, pretexting, quid pro quo attacks, reverse social engineering and dumpster diving. Present the topic in a bit more detail with this Social Engineering Attacks Prevention Human Based Social Engineering Attacks. Use it as a tool for discussion and navigation on Reverse Social Engineering, Dumpster Diving, Social Engineering Attacks, Fraudulent Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attacks Prevention Important Traits Of Social Engineering Attacks
Social Engineering Attacks Prevention Important Traits Of Social Engineering AttacksThe purpose of this slide is to outline the significant traits of a social engineering scam. The main points discussed in this slide are urgency, believability, trust, and heightened emotions such as fear, excitement, curiosity, sadness, guilt, etc. Introducing Social Engineering Attacks Prevention Important Traits Of Social Engineering Attacks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Time Sensitive Opportunities, Believability, Heightened Emotions, Manipulated Emotions, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Attacks Prevention Main Goals Of Social Engineering Attackers
Social Engineering Attacks Prevention Main Goals Of Social Engineering AttackersThis slide highlights the motive of the scammers behind the social engineering attacks. The two primary goals discussed in this slide are disruption and theft. This slide also outlines several examples, such as ransomware, phishing attacks, impersonation, etc. Deliver an outstanding presentation on the topic using this Social Engineering Attacks Prevention Main Goals Of Social Engineering Attackers. Dispense information and present a thorough explanation of Social Engineering Attackers, Phishing Attacks, Distributed Denial Of Service, Aims To Corrupt Data Or Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Attacks Prevention Ontological Model Of Social Engineering Attack
Social Engineering Attacks Prevention Ontological Model Of Social Engineering AttackThe purpose of this slide is to represent the model of a social engineering attack which consists of several components. The major points depicted in this slide are social engineer, medium, goal, target, compliance principles, techniques, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Attacks Prevention Ontological Model Of Social Engineering Attack. This template helps you present information on six stages. You can also present information on Direct Communication, Bidirectional Communication, Unidirectional Communication using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Attacks Prevention Red Flags Of A Social Engineering Attack
Social Engineering Attacks Prevention Red Flags Of A Social Engineering AttackThis slide highlights the signs of a social engineering attack. The purpose of this slide is to outline the various symptoms of cyber attack, such as strange messages from a friend, arouse emotions, create a sense of urgency, tempting offers, etc. Introducing Social Engineering Attacks Prevention Red Flags Of A Social Engineering Attack to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering Attack, Arouse Emotions, Arouse Emotions Like Fear, Arouse Emotions, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Attacks Prevention Resources And Training Provided To Employees In Organization
Social Engineering Attacks Prevention Resources And Training Provided To Employees In OrganizationThis slide demonstrates the resources and training that can be provided by companies to their staff. These include employee training, check to see if you have already been breached, be aware of the various phishing attacks, invest in security education, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Attacks Prevention Resources And Training Provided To Employees In Organization. This template helps you present information on five stages. You can also present information on Invest In Security Education, Invest In Password, Employee Training, Phishing Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Attacks Prevention Roadmap To Implement Social Engineering Prevention Strategies
Social Engineering Attacks Prevention Roadmap To Implement Social Engineering Prevention StrategiesThis slide represents the roadmap to prevent social engineering attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. Introducing Social Engineering Attacks Prevention Roadmap To Implement Social Engineering Prevention Strategies to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Establish Policies And Procedures, Implement Technical Controls, Social Engineering Prevention Strategies, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Attacks Prevention Sciences Involved In Targeting Humans In Modern Social
Social Engineering Attacks Prevention Sciences Involved In Targeting Humans In Modern SocialThis slide highlights the key sciences involved in the process of modern social engineering. These are psychology, pedagogy, cognitive sciences, psychiatry, marketing, communication sciences, philosophy, normative processes, organizational sociology, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Attacks Prevention Sciences Involved In Targeting Humans In Modern Social. This template helps you present information on thirteen stages. You can also present information on Modern Social Engineering, Psychology, Pedagogy, Cognitive Sciences, Psychiatry, Marketing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Attacks Prevention Social Engineering Awareness Training Program For Employees
Social Engineering Attacks Prevention Social Engineering Awareness Training Program For EmployeesThis slide represents the training program for employees which will help them to prevent various cyber security scams in business. The purpose of this slide is to outline the mode, venue and schedule for the different training programs. Deliver an outstanding presentation on the topic using this Social Engineering Attacks Prevention Social Engineering Awareness Training Program For Employees. Dispense information and present a thorough explanation of Social Engineering Awareness, Training Program For Employees, Training Programs, Cyber Security Scams using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Attacks Prevention Social Engineering Classification Chart Overview
Social Engineering Attacks Prevention Social Engineering Classification Chart OverviewIntroducing Social Engineering Attacks Prevention Social Engineering Classification Chart Overview to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering, Ingratiation, Instant Messaging, Waste Threats Management, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Attacks Prevention Social Engineering Methods Used By Attackers
Social Engineering Attacks Prevention Social Engineering Methods Used By AttackersThis slide demonstrates the popular procedures for conducting social engineering scams. These methods of performing social engineering attacks are phone calls, in-person interactions, tailgating, persuasion through third-party applications, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Attacks Prevention Social Engineering Methods Used By Attackers. This template helps you present information on four stages. You can also present information on Guide Them To Phishing Websites, Attackers Call Targets, Scammers Act As Employees, Fictitious Positions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Attacks Prevention Social Engineering Prevention Strategies For Safe Network Use
Social Engineering Attacks Prevention Social Engineering Prevention Strategies For Safe Network UseThis slide represents the protective measures for users to practice safe networking. The best practices mentioned in this slide are restrict others from connecting to primary wi-fi network, use a VPN, security of network-connected devices, etc. Introducing Social Engineering Attacks Prevention Social Engineering Prevention Strategies For Safe Network Use to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Practice Safe Networking, Primary Wifi Network, Security Of Network Connected Devices, Social Engineering Prevention Strategies, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Attacks Prevention Step By Step Process Of Social Engineering Awareness Program
Social Engineering Attacks Prevention Step By Step Process Of Social Engineering Awareness ProgramThis slide demonstrates the working of cyber security awareness training programs for organizations. These include start with employee training, make fictitious cyber attack campaigns, reinforce the awareness training and track progress and upgrade. Increase audience engagement and knowledge by dispensing information using Social Engineering Attacks Prevention Step By Step Process Of Social Engineering Awareness Program. This template helps you present information on four stages. You can also present information on Awareness Training Program, Cyber Attack Campaigns, Start With Employee Training using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Attacks Prevention Technology Based Social Engineering Attacks
Social Engineering Attacks Prevention Technology Based Social Engineering AttacksThis slide discusses the different technology-based techniques used by social engineering scammers. These attacks include phishing, vishing, smishing, watering hole attacks, man-in-the-middle attacks, scareware and angler phishing. Deliver an outstanding presentation on the topic using this Social Engineering Attacks Prevention Technology Based Social Engineering Attacks. Dispense information and present a thorough explanation of Watering Hole Attacks, Social Engineering Attacks, Angler Phishing, Fraudsters Fake Trusted Phone using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
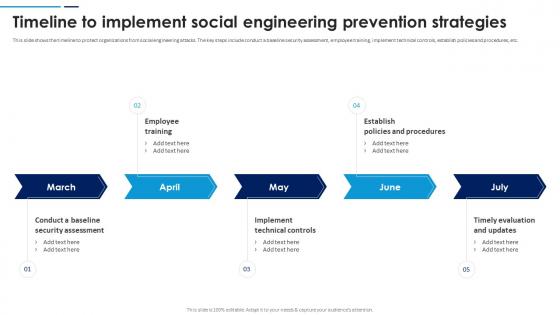 Social Engineering Attacks Prevention Timeline To Implement Social Engineering Prevention Strategies
Social Engineering Attacks Prevention Timeline To Implement Social Engineering Prevention StrategiesThis slide shows the timeline to protect organizations from social engineering attacks. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. Introducing Social Engineering Attacks Prevention Timeline To Implement Social Engineering Prevention Strategies to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Establish Policies And Procedures, Timely Evaluation And Updates, Implement Technical Controls, Employee Training, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Attacks Prevention Understanding Social Engineering Threat Landscape
Social Engineering Attacks Prevention Understanding Social Engineering Threat LandscapeThis slide shows the threat landscape for social engineering. The key components included are email, social media and the internet, trends, criminal groups, malicious insiders, and attack vectors such as physical on-site attacks, mobile, network, cloud, etc. Deliver an outstanding presentation on the topic using this Social Engineering Attacks Prevention Understanding Social Engineering Threat Landscape. Dispense information and present a thorough explanation of Social Media And Internet, Social Engineering Threat Landscape, Search Result Poisoning using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Prevention Strategies For Safe Communication Social Engineering Attacks Prevention
Social Engineering Prevention Strategies For Safe Communication Social Engineering Attacks PreventionThis slide discusses several social engineering mitigation techniques. These include avoid clicking on links in emails and texts, use multi-factor authentication, select strong passwords, avoid sharing personal information, beware of internet friendships, etc. Introducing Social Engineering Prevention Strategies For Safe Communication Social Engineering Attacks Prevention to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering Prevention, Strategies For Safe Communication, Multi Factor Authentication, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Prevention Strategies For Safe Device Usage Social Engineering Attacks Prevention
Social Engineering Prevention Strategies For Safe Device Usage Social Engineering Attacks PreventionThe purpose of this slide is to represent the best practices for safe device usage. These safety measures include internet security software, never leave devices unsecured in public places, keep software updated and inspect all internet accounts. Increase audience engagement and knowledge by dispensing information using Social Engineering Prevention Strategies For Safe Device Usage Social Engineering Attacks Prevention. This template helps you present information on four stages. You can also present information on Internet Security Software, Keep Software Updated, Inspect All Internet Accounts, Devices Unsecured In Public using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents For Social Engineering Attacks Prevention For Businesses
Table Of Contents For Social Engineering Attacks Prevention For BusinessesIntroducing Table Of Contents For Social Engineering Attacks Prevention For Businesses to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Lifecycle And Process, Social Engineering Introduction, Attack Targets And Vectors, Statistics Of Social Engineering Scams, using this template. Grab it now to reap its full benefits.
-
 Classification Of Attacks Based On 5g Iot Architecture Layers
Classification Of Attacks Based On 5g Iot Architecture LayersThis Slide Shows Classifying Attacks Based On 5G Iot Architecture Layers To Improve Network Security. It Further Includes Physical Device Layer, Communication Layer, Edge Computing Layer Etc. Presenting Our Set Of Slides With Classification Of Attacks Based On 5g Iot Architecture Layers. This Exhibits Information On Seven Stages Of The Process. This Is An Easy To Edit And Innovatively Designed Powerpoint Template. So Download Immediately And Highlight Information On Data Storage Layer, Management Service Layer, Collaboration And Processes Layer.
-
 Valerian Root Heart Attack In Powerpoint And Google Slides Cpb
Valerian Root Heart Attack In Powerpoint And Google Slides CpbPresenting our Valerian Root Heart Attack In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Valerian Root Heart Attack This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Current Trending Technologies Various Types Of Cyber Attacks On System
Current Trending Technologies Various Types Of Cyber Attacks On SystemThis slide explains Various types of cyber attacks on system on a system such as malware, phishing, man in the middle, distributed denial of service, brute force, SQL injection, and domain name system. Introducing Current Trending Technologies Various Types Of Cyber Attacks On System to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Attacks On System, Distributed Denial Of Service, Cryptographic Trick, Cybercriminals Disable Targeted Servers, using this template. Grab it now to reap its full benefits.
-
 Banking Solutions For Improving Customer Man In The Middle Mobile Banking Attacking Methods Fin SS V
Banking Solutions For Improving Customer Man In The Middle Mobile Banking Attacking Methods Fin SS VThis slide shows overview of popular cyberattack related to mobile banking which is man in the middle MiTM. It also includes popular types of this attack which are WIFI network interception, DNS spoofing, email interception and malware. Deliver an outstanding presentation on the topic using this Banking Solutions For Improving Customer Man In The Middle Mobile Banking Attacking Methods Fin SS V. Dispense information and present a thorough explanation of Popular Cyberattack, Network Interception, Email Interception And Malware, Mobile Banking Attacking Methods using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 New Technologies Various Types Of Cyber Attacks On System
New Technologies Various Types Of Cyber Attacks On SystemThis slide explains Various types of cyber attacks on system on a system such as malware, phishing, man in the middle, distributed denial of service, brute force, SQL injection, and domain name system. Introducing New Technologies Various Types Of Cyber Attacks On System to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Malware, Phishing, Distributed, using this template. Grab it now to reap its full benefits.
-
 How Does Phishing Attack Works On Blockchain Network Guide For Blockchain BCT SS V
How Does Phishing Attack Works On Blockchain Network Guide For Blockchain BCT SS VThe following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Introducing How Does Phishing Attack Works On Blockchain Network Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Attacker, Phishing Email, Internet Network using this template. Grab it now to reap its full benefits.
-
 How Hackers Attack Blockchain Technology Guide For Blockchain BCT SS V
How Hackers Attack Blockchain Technology Guide For Blockchain BCT SS VThe following slide showcases how hackers attacks blockchain technology to protect key information and mange threats. It includes elements such as false transactions, private keys, hampering network nodes, fake cryptocurrencies, personal information, etc. Increase audience engagement and knowledge by dispensing information using How Hackers Attack Blockchain Technology Guide For Blockchain BCT SS V This template helps you present information on six stages. You can also present information on Through Which Hackers, Attack Blockchain Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Impact Of 51 Percent Attack On Bitcoin And Blockchain Transactions Guide For Blockchain BCT SS V
Impact Of 51 Percent Attack On Bitcoin And Blockchain Transactions Guide For Blockchain BCT SS VThe following slide depicts the key effect of 51 percent attack on bitcoin and blockchain technology to plan actions and minimize its impact. It includes element such as delayed transactions, network disruption, low miner rewards, market volatility, reputation, credibility, etc. Introducing Impact Of 51 Percent Attack On Bitcoin And Blockchain Transactions Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Delayed Transactions, Network Disruption, Market Volatility using this template. Grab it now to reap its full benefits.
-
 Impact Of Ddos Attack On Targeted Servers Guide For Blockchain BCT SS V
Impact Of Ddos Attack On Targeted Servers Guide For Blockchain BCT SS VThe following slide depicts the adverse impact of denial of service DDoS attack to determine malicious attempt to hamper targeted server. It includes elements such as software crashes, node failure, network congestion, bloated ledger, etc. Increase audience engagement and knowledge by dispensing information using Impact Of Ddos Attack On Targeted Servers Guide For Blockchain BCT SS V This template helps you present information on four stages. You can also present information on Software Crashes, Node Failures, Network Congestion using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Impact Of Eclipse Attack On Peer To Peer Network Guide For Blockchain BCT SS V
Impact Of Eclipse Attack On Peer To Peer Network Guide For Blockchain BCT SS VThe following slide illustrates the impact of eclipse attack on functioning of blockchain network to plan strategies and action steps. It includes elements such as leading to double spending, centralization, disrupting mining power, network instability, monetary loss, etc. Introducing Impact Of Eclipse Attack On Peer To Peer Network Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Double Spending, Network Instability, Centralization using this template. Grab it now to reap its full benefits.
-
 Key Scenarios Of Sybil Attack On Blockchain Network Guide For Blockchain BCT SS V
Key Scenarios Of Sybil Attack On Blockchain Network Guide For Blockchain BCT SS VThe following slide showcases major scenarios of Sybil attack to minimize the impact and manage operations. It includes elements such as attack on bitcoin network, tor network, peer-to-peer model, etc. Introducing Key Scenarios Of Sybil Attack On Blockchain Network Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Attack On Bitcoin Network, Attack On Tor Network using this template. Grab it now to reap its full benefits.
-
 Methods To Avoid Sybil Attack For Protecting Tokens Guide For Blockchain BCT SS V
Methods To Avoid Sybil Attack For Protecting Tokens Guide For Blockchain BCT SS VThe following slide illustrates various ways to minimize and prevent Sybil attacks and ensure safe blockchain transactions. It includes elements such as identity validation, hierarchical, defense system, cost of new nodes, social trust graphs Introducing Methods To Avoid Sybil Attack For Protecting Tokens Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Identity Validation, Hierarchical System, Defense System using this template. Grab it now to reap its full benefits.
-
 Overview And Categories Of Sybil Attack On Blockchain Network Guide For Blockchain BCT SS V
Overview And Categories Of Sybil Attack On Blockchain Network Guide For Blockchain BCT SS VThe following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc. Increase audience engagement and knowledge by dispensing information using Overview And Categories Of Sybil Attack On Blockchain Network Guide For Blockchain BCT SS V This template helps you present information on two stages. You can also present information on Direct Sybil Attack, Categories Of Sybil Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview And Impact Of Blockchain Routing Attacks Guide For Blockchain BCT SS V
Overview And Impact Of Blockchain Routing Attacks Guide For Blockchain BCT SS VThe following slide illustrates the brief introduction of routing attacks to reduce leakage of information. It includes elements such as interrupting communication between nodes, delaying blockchain delivery, breaking network into two or more parts, etc. Introducing Overview And Impact Of Blockchain Routing Attacks Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Communication Between, Routing Attack, Blockchain Delivery using this template. Grab it now to reap its full benefits.
-
 Overview And Workflow Process Of Eclipse Attack Guide For Blockchain BCT SS V
Overview And Workflow Process Of Eclipse Attack Guide For Blockchain BCT SS VThe following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer-to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. Present the topic in a bit more detail with this Overview And Workflow Process Of Eclipse Attack Guide For Blockchain BCT SS V Use it as a tool for discussion and navigation on Overview, Eclipse Attack Works, Malicious Nodes This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview And Working Process Of Ddos Attack Guide For Blockchain BCT SS V
Overview And Working Process Of Ddos Attack Guide For Blockchain BCT SS VThe following slide illustrates brief introduction of distributed denial of service DDoS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc. Introducing Overview And Working Process Of Ddos Attack Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Overview, Perform Operations, Excessive Internet Traffic using this template. Grab it now to reap its full benefits.
-
 Overview Of Blockchain 51 Percent Attack With Workflow Guide For Blockchain BCT SS V
Overview Of Blockchain 51 Percent Attack With Workflow Guide For Blockchain BCT SS VThe following slide showcases brief introduction of 51 percent attack to analyze hashing power of cryptocurrency users. It includes elements such at mining faster rate, malicious user, along with its workflow, etc. Present the topic in a bit more detail with this Overview Of Blockchain 51 Percent Attack With Workflow Guide For Blockchain BCT SS V Use it as a tool for discussion and navigation on Overview, Blockchain Network, Public Network This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Phishing Attack In Blockchain Technology Guide For Blockchain BCT SS V
Overview Of Phishing Attack In Blockchain Technology Guide For Blockchain BCT SS VThe following slide illustrates brief introduction of phishing attacks impacting blockchian to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc. Introducing Overview Of Phishing Attack In Blockchain Technology Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Overview, Phishing Attacks Carried, Investment Opportunities using this template. Grab it now to reap its full benefits.
-
 Techniques To Prevent Eclipse Attack And Secure Funds Guide For Blockchain BCT SS V
Techniques To Prevent Eclipse Attack And Secure Funds Guide For Blockchain BCT SS VThe following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Introducing Techniques To Prevent Eclipse Attack And Secure Funds Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Random Node Selection, Deterministic Node Selection using this template. Grab it now to reap its full benefits.
-
 Threats Imposed By Sybil Attack On Blockchain Network Guide For Blockchain BCT SS V
Threats Imposed By Sybil Attack On Blockchain Network Guide For Blockchain BCT SS VThe following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51 percent attack, etc. Increase audience engagement and knowledge by dispensing information using Threats Imposed By Sybil Attack On Blockchain Network Guide For Blockchain BCT SS V This template helps you present information on three stages. You can also present information on Block Users From Network, Breach Of Privacy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various Types Of Ddos Attacks Impacting Internet Traffic Guide For Blockchain BCT SS V
Various Types Of Ddos Attacks Impacting Internet Traffic Guide For Blockchain BCT SS VThe following slide showcases various types of denial of service DDoS attack to reduce abnormal traffic and lessen the impact. It includes elements such as volumetric, applications, protocol, fragmentation attacks, etc. Increase audience engagement and knowledge by dispensing information using Various Types Of Ddos Attacks Impacting Internet Traffic Guide For Blockchain BCT SS V This template helps you present information on four stages. You can also present information on Volumetric Attacks, Application Attacks, Fragmentation Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ways To Minimize 51 Percent Attacks And Optimize Hash Rate Guide For Blockchain BCT SS V
Ways To Minimize 51 Percent Attacks And Optimize Hash Rate Guide For Blockchain BCT SS VThe following slide illustrates various methods to reduce the impact of 51 percent attacks and optimize hash rate. It includes elements such as restriction on single user, constant updates, establishing strong network system, leveraging proof of stake, performing security audits, etc. Introducing Ways To Minimize 51 Percent Attacks And Optimize Hash Rate Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Constant Updates, Network System, Security Audits using this template. Grab it now to reap its full benefits.
-
 Ways To Prevent Blockchain Routing Attacks Guide For Blockchain BCT SS V
Ways To Prevent Blockchain Routing Attacks Guide For Blockchain BCT SS VThe following slide illustrates some methods to minimize blockchain routing attacks to safeguard network from wrong routing table. It includes elements such as strong passwords, updating firmware, managing access control lists, monitoring logs, etc. Increase audience engagement and knowledge by dispensing information using Ways To Prevent Blockchain Routing Attacks Guide For Blockchain BCT SS V This template helps you present information on four stages. You can also present information on Strong Passwords, Update Firmware, Monitor using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Gallbladder Attacks Symptoms In Powerpoint And Google Slides Cpb
Gallbladder Attacks Symptoms In Powerpoint And Google Slides CpbPresenting Gallbladder Attacks Symptoms In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Gallbladder Attacks Symptoms This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Ways To Protect Digital Twins From Cyber Attacks IoT Digital Twin Technology IOT SS
Ways To Protect Digital Twins From Cyber Attacks IoT Digital Twin Technology IOT SSThis slide provides an overview of the techniques followed to prevent attacks and safeguard data. Major ways covered are controlling network access, verification of data integrity and prevention of flooding attacks. Present the topic in a bit more detail with this Ways To Protect Digital Twins From Cyber Attacks IoT Digital Twin Technology IOT SS. Use it as a tool for discussion and navigation on Control Network Access, Prevent Flooding Attacks, Verify Data Integrity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Relax Anxiety Attack In Powerpoint And Google Slides Cpb
Relax Anxiety Attack In Powerpoint And Google Slides CpbPresenting our Relax Anxiety Attack In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Relax Anxiety Attack This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Data Breach Response Plan Checklist For Responding To A Data Breach Attack
Data Breach Response Plan Checklist For Responding To A Data Breach AttackThis slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc. Deliver an outstanding presentation on the topic using this Data Breach Response Plan Checklist For Responding To A Data Breach Attack. Dispense information and present a thorough explanation of Data Breach Response Plan, Fundamental Approaches, Formal Risk Assessment, Restore Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Response Plan Possible Causes Of Data Breach Attack
Data Breach Response Plan Possible Causes Of Data Breach AttackThis slide highlights the reasons behind the success of data breach attack. These include phishing attacks, unpatched software, malware, insider threats, third-party vulnerabilities, SQL Structured Query Language injections, unsecured APIs, etc. Deliver an outstanding presentation on the topic using this Data Breach Response Plan Possible Causes Of Data Breach Attack. Dispense information and present a thorough explanation of Phishing Attacks, Unpatched Software, Third Party Vulnerabilities, Structured Query Language using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impact Of DDoS Attack On Targeted Servers Hands On Blockchain Security Risk BCT SS V
Impact Of DDoS Attack On Targeted Servers Hands On Blockchain Security Risk BCT SS VThe following slide depicts the adverse impact of denial of service DDOS attack to determine malicious attempt to hamper targeted server. It includes elements such as software crashes, node failure, network congestion, bloated ledger, etc. Increase audience engagement and knowledge by dispensing information using Impact Of Impact Of DDoS Attack On Targeted Servers Hands On Blockchain Security Risk BCT SS V. This template helps you present information on four stages. You can also present information on Software Crashes, Node Failures, Network Congestion using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various Types Of DDoS Attacks Impacting Internet Traffic Hands On Blockchain Security Risk BCT SS V
Various Types Of DDoS Attacks Impacting Internet Traffic Hands On Blockchain Security Risk BCT SS VThe following slide showcases various types of denial of service DDOS attack to reduce abnormal traffic and lessen the impact. It includes elements such as volumetric, applications, protocol, fragmentation attacks, etc. Introducing Various Types Of DDoS Attacks Impacting Internet Traffic Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Volumetric Attacks, Protocol Attacks, Application Attacks, using this template. Grab it now to reap its full benefits.





