Powerpoint Templates and Google slides for Vulnerability Cybersecurity
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity CD
Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity CDStep up your game with our enchanting Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity CD deck, guaranteed to leave a lasting impression on your audience. Crafted with a perfect balance of simplicity, and innovation, our deck empowers you to alter it to your specific needs. You can also change the color theme of the slide to mold it to your companys specific needs. Save time with our ready-made design, compatible with Microsoft versions and Google Slides. Additionally, it is available for download in various formats including JPG, JPEG, and PNG. Outshine your competitors with our fully editable and customized deck.
-
 Cybersecurity Incident And Vulnerability Response Playbook Powerpoint Presentation Slides
Cybersecurity Incident And Vulnerability Response Playbook Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Cybersecurity Incident And Vulnerability Response Playbook Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fifty slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Identifying Vulnerabilities As A Step For Cybersecurity Risk Identification Training Ppt
Identifying Vulnerabilities As A Step For Cybersecurity Risk Identification Training PptPresenting Identifying Vulnerabilities as a Step for Cybersecurity Risk Identification. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Network Vulnerabilities Logged Off In Previous Years Implementing Strategies For Mitigating Cybersecurity SS
Network Vulnerabilities Logged Off In Previous Years Implementing Strategies For Mitigating Cybersecurity SSThis slide represents network vulnerabilities faced by the organization, which led to the theft of confidential and sensitive information due to opening of infected email attachments etc.Deliver an outstanding presentation on the topic using this Network Vulnerabilities Logged Off In Previous Years Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Phishing Attacks, Malware Attacks, Reasons, Key Insights using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Vulnerabilities Assessment KPI Dashboard Implementing Strategies For Mitigating Cybersecurity SS
Network Vulnerabilities Assessment KPI Dashboard Implementing Strategies For Mitigating Cybersecurity SSThis dashboard tracks and assesses the network vulnerabilities faced by the organization. It includes KPIs such as critical vulnerabilities, new vulnerabilities, and unresolved vulnerabilities etc.Present the topic in a bit more detail with this Network Vulnerabilities Assessment KPI Dashboard Implementing Strategies For Mitigating Cybersecurity SS. Use it as a tool for discussion and navigation on New Vulnerabilities, Unresolved Vulnerabilities, Activity, Insecure Libraries. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Potential Impact Of Mitigating Network Vulnerabilities On Cyber Attacks Cybersecurity SS
Potential Impact Of Mitigating Network Vulnerabilities On Cyber Attacks Cybersecurity SSThis slide shows the impact of strategies implemented by IT and security professionals to prevent and mitigate network vulnerabilities, including phishing attacks, malware attacks, insider attacks and software vulnerabilities.Deliver an outstanding presentation on the topic using this Potential Impact Of Mitigating Network Vulnerabilities On Cyber Attacks Cybersecurity SS. Dispense information and present a thorough explanation of Cyber Attacks, Secure Passwords, Compliant Monitoring And Auditing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Potential Roi After Implementing Tools And Technologies To Reduce Network Vulnerabilities Cybersecurity SS
Potential Roi After Implementing Tools And Technologies To Reduce Network Vulnerabilities Cybersecurity SSThis slide demonstrates the positive impact of implementing network vulnerability management solutions on returns on investments. The graph depicts an increase in ROI and savings over time..Deliver an outstanding presentation on the topic using this Potential Roi After Implementing Tools And Technologies To Reduce Network Vulnerabilities Cybersecurity SS. Dispense information and present a thorough explanation of Key Insights, Improved Compliance, Password Hacking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Challenges Faced By ChatGPT In Vulnerability How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS
Challenges Faced By ChatGPT In Vulnerability How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SSThis slide showcases various challenges faced by ChatGPT for effective vulnerability assessment and tackling cyber attacks. Key challenges faced are requirement of training data, difficulty in identifying assets and ethical implications. Increase audience engagement and knowledge by dispensing information using Challenges Faced By ChatGPT In Vulnerability How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS. This template helps you present information on three stages. You can also present information on Amount, Legal, Sensitive using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 ChatGPT Opportunities For Vulnerability How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS
ChatGPT Opportunities For Vulnerability How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SSThis slide showcases various ChatGPT opportunities for vulnerability assessment which can help to tackle cyber attack. Its key elements are automation of security tasks, improved efficiency and identification of new vulnerabilities. Increase audience engagement and knowledge by dispensing information using ChatGPT Opportunities For Vulnerability How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS. This template helps you present information on three stages. You can also present information on Security, Improved, Identify using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview And Importance Of Vulnerability How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS
Overview And Importance Of Vulnerability How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SSThis slide showcases vulnerability assessment overview which can help organization to prevent cyber attacks. It also highlights various importance of vulnerability assessment such as identifying security flaws, optimize security investments, reduced likelihood of security breach etc. Increase audience engagement and knowledge by dispensing information using Overview And Importance Of Vulnerability How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS. This template helps you present information on three stages. You can also present information on Reduce, Security, Organization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
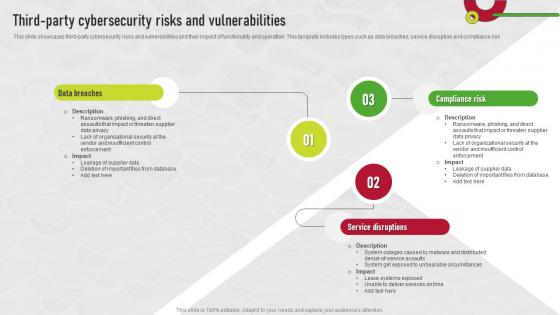 Third Party Cybersecurity Risks And Vulnerabilities Supplier Risk Management
Third Party Cybersecurity Risks And Vulnerabilities Supplier Risk ManagementThis slide showcases third party cybersecurity risks and vulnerabilities and their impact of functionality and operation. This template includes types such as data breaches, service disruption and compliance risk. Increase audience engagement and knowledge by dispensing information using Third Party Cybersecurity Risks And Vulnerabilities Supplier Risk Management. This template helps you present information on three stages. You can also present information on Data Breaches, Service Disruptions, Compliance Risk using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Threats Vulnerabilities In Powerpoint And Google Slides Cpb
Cybersecurity Threats Vulnerabilities In Powerpoint And Google Slides CpbPresenting Cybersecurity Threats Vulnerabilities In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cybersecurity Threats Vulnerabilities. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Blockchain And Cybersecurity Conducting Vulnerability Assessment To Respond And Recover BCT SS V
Blockchain And Cybersecurity Conducting Vulnerability Assessment To Respond And Recover BCT SS VThe following slide showcases blockchain cybersecurity vulnerability assessment framework to optimize resilience and transparency. It includes key elements such as identify, protect, respond, recover, etc. Deliver an outstanding presentation on the topic using this Blockchain And Cybersecurity Conducting Vulnerability Assessment To Respond And Recover BCT SS V Dispense information and present a thorough explanation of Identity, Protect, Detect using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Blockchain And Cybersecurity Discovery Identifying Potential Vulnerabilities In System BCT SS V
Blockchain And Cybersecurity Discovery Identifying Potential Vulnerabilities In System BCT SS VThe following slide showcases key phases of penetration testing to identify potential flaws and malware. It includes elements of discovery phase such as architecture, compliance readiness, readiness analysis, etc. Introducing Blockchain And Cybersecurity Discovery Identifying Potential Vulnerabilities In System BCT SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Architecture Of Blockchain, Compliance Readiness, Readiness Analysis using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Reporting Analyzing Vulnerabilities Through Penetration Testing Summary BCT SS V
Blockchain And Cybersecurity Reporting Analyzing Vulnerabilities Through Penetration Testing Summary BCT SS VThe following slide depicts brief summary of penetration testing report. It includes elements such as vulnerabilities, status, severity, risk score, unpatched operating system, cross site scripting, SQL injection, weak private key policies, misconfigured firewall rules, etc. Deliver an outstanding presentation on the topic using this Vulnerabilities, Description, Assigned Dispense information and present a thorough explanation of Vulnerabilities, Description, Assigned using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Tips While Using Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V
Cybersecurity Tips While Using Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS VThis slide showcases various cybersecurity tips that can be used while using ChatGPT for generating responses. Its key elements are avoid inserting sensitive data, awareness of potential bias and beware of fake applications Increase audience engagement and knowledge by dispensing information using Cybersecurity Tips While Using Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V. This template helps you present information on three stages. You can also present information on Avoid Inserting Sensitive Data, Awareness Of Potential Bias, Beware Of Fake Applications using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How In Cybersecurity Penetration Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V
How In Cybersecurity Penetration Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS VThis slide showcases various ChatGPT use cases for penetration testing which can help to prevent cyber attacks in organization. Its key elements are establish penetration testing environment, gain knowledge about testing tools, writing code for testing etc. Introducing How In Cybersecurity Penetration Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Penetration, Testing Environment, Penetration, using this template. Grab it now to reap its full benefits.
-
 Key Importance Of Cybersecurity Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V
Key Importance Of Cybersecurity Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS VThis slide showcases various statistics that highlights the importance of cybersecurity in organization. It highlights stats related to malware attacks, DDos attacks, cybersecurity spending, ransomware attacks, malicious mining software etc. Present the topic in a bit more detail with this Key Importance Of Cybersecurity Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V. Use it as a tool for discussion and navigation on Cybersecurity, Statistics, Importance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview And Cybersecurity Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V
Overview And Cybersecurity Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS VThis slide showcases cybersecurity overview that can help organization to safeguard data from different types of cyber attacks. It also highlights various benefits of cybersecurity such as safeguard data, timely incident response, reduce monetary damage etc. Deliver an outstanding presentation on the topic using this Overview And Cybersecurity Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V. Dispense information and present a thorough explanation of Organization, Cybersecurity, Overview using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Cybersecurity Incident Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V
Overview Cybersecurity Incident Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS VThis slide showcases overview of incident management that can help organization in tackling cyber attacks. It also highlights various importance of incident management that are reduction in cyber attacks, decrease in system downtime, improved incident response etc. Present the topic in a bit more detail with this Overview Cybersecurity Incident Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V. Use it as a tool for discussion and navigation on Management, Overview, Cybersecurity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Monitor Vulnerability Disclosure And Threat Intelligence Internet Of Things IoT Security Cybersecurity SS
Monitor Vulnerability Disclosure And Threat Intelligence Internet Of Things IoT Security Cybersecurity SSThis slide showcases vulnerability assessment disclosure and threat intelligence on internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about continuous monitoring, correlation, disclosure, etc. Introducing Monitor Vulnerability Disclosure And Threat Intelligence Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Continuous Monitoring, Correlation With Metadata, Disclosure Implementation, using this template. Grab it now to reap its full benefits.
-
 Agenda Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS
Agenda Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SSIntroducing Agenda Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Network Security Loopholes, Security Vulnerabilities, Vulnerabilities Mitigation Strategies, using this template. Grab it now to reap its full benefits.
-
 Gap Analysis Of Network Vulnerabilities Experienced By Organization Cybersecurity SS
Gap Analysis Of Network Vulnerabilities Experienced By Organization Cybersecurity SSThis slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results.Present the topic in a bit more detail with this Gap Analysis Of Network Vulnerabilities Experienced By Organization Cybersecurity SS. Use it as a tool for discussion and navigation on Current State, Gap, Desired State, Strategies To Fill Gap. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons Slide Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS
Icons Slide Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SSPresenting our well crafted Icons Slide Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly.
-
 Impact Of Mitigating Network Vulnerabilities On Organizational Operations Cybersecurity SS
Impact Of Mitigating Network Vulnerabilities On Organizational Operations Cybersecurity SSThis slide highlights the impact of implementing effective strategies to mitigate network vulnerabilities on organizational operations, such as potential revenue loss, customer churn, and other factors.Introducing Impact Of Mitigating Network Vulnerabilities On Organizational Operations Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Potential Annual Revenue, Customer Attrition Rate, Employee Productivity Rates, using this template. Grab it now to reap its full benefits.
-
 Impact Of Network Vulnerabilities On Organizational Operations Cybersecurity SS
Impact Of Network Vulnerabilities On Organizational Operations Cybersecurity SSThis slide illustrates the impact of network vulnerabilities experienced by enterprises on organizational operations, such as data corruption, reputational damage, and data theft etc. Increase audience engagement and knowledge by dispensing information using Impact Of Network Vulnerabilities On Organizational Operations Cybersecurity SS. This template helps you present information on four stages. You can also present information on Data Corruptions, Reputational Damage, Operational Disruption, Data Stealing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementing Strategies For Mitigating Network Vulnerabilities Table Of Contents Cybersecurity SS
Implementing Strategies For Mitigating Network Vulnerabilities Table Of Contents Cybersecurity SSIntroducing Implementing Strategies For Mitigating Network Vulnerabilities Table Of Contents Cybersecurity SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Best Practices, Training Plan For Identification, using this template. Grab it now to reap its full benefits.
-
 Implementing Tools For Immediate Response To Network Vulnerabilities Cybersecurity SS
Implementing Tools For Immediate Response To Network Vulnerabilities Cybersecurity SSThis slide compares tools and technologies necessary to mitigate network vulnerabilities based on different aspects such as the scope of protection, granularity, user experience, and use cases.Present the topic in a bit more detail with this Implementing Tools For Immediate Response To Network Vulnerabilities Cybersecurity SS. Use it as a tool for discussion and navigation on Network Segmentation, End Point Protection, Zero Trust Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Issues Faced By Organization Due To Network Vulnerabilities Cybersecurity SS
Key Issues Faced By Organization Due To Network Vulnerabilities Cybersecurity SSThis slide represents challenges faced by enterprise as a result of network vulnerabilities leading to issues such as lack of privacy, compliance and security and data leakage etc.Introducing Key Issues Faced By Organization Due To Network Vulnerabilities Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Compliance, Security, Personal Devices, Software Encryption, using this template. Grab it now to reap its full benefits.
-
 Network Vulnerabilities Management Key Metrics Dashboard Cybersecurity SS
Network Vulnerabilities Management Key Metrics Dashboard Cybersecurity SSThis dashboard tracks and manages the organizations network vulnerabilities. It includes KPIs such as data access vulnerabilities and exploitable vulnerabilities and a summary of vulnerabilities by severity.Deliver an outstanding presentation on the topic using this Network Vulnerabilities Management Key Metrics Dashboard Cybersecurity SS. Dispense information and present a thorough explanation of Unmitigated, Mitigated, Exploitable, Exploitable Hosts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Strategies For Mitigating Network Vulnerabilities Cybersecurity SS
Overview Strategies For Mitigating Network Vulnerabilities Cybersecurity SSThis slide presents effective techniques for mitigating network vulnerabilities, including anti-phishing training, end-to-end encryption, patch management, strong password policies and authentication protocols.Introducing Overview Strategies For Mitigating Network Vulnerabilities Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Provide Anti Phishing Training, Authentication Protocols, Patch Management, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS
Table Of Contents Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SSIncrease audience engagement and knowledge by dispensing information using Table Of Contents Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS. This template helps you present information on eight stages. You can also present information on Gap Analysis, Patch Management, Dashboard Tracking, Additional Slides using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
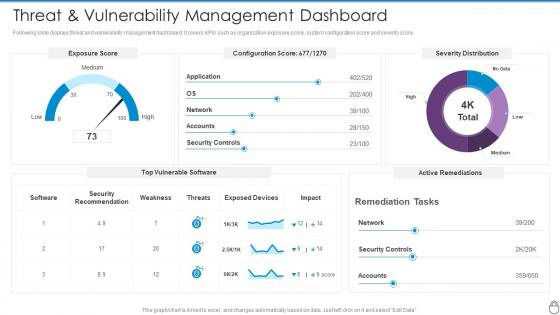 Cybersecurity Risk Management Framework Threat And Vulnerability Management Dashboard
Cybersecurity Risk Management Framework Threat And Vulnerability Management DashboardFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Cybersecurity Risk Management Framework Threat And Vulnerability Management Dashboard. Use it as a tool for discussion and navigation on Exposure Score, Configuration Score, Severity Distribution, Weakness, Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Clustered Column Cybersecurity Incident And Vulnerability Response Playbook
Clustered Column Cybersecurity Incident And Vulnerability Response PlaybookDeliver an outstanding presentation on the topic using this Clustered Column Cybersecurity Incident And Vulnerability Response Playbook. Dispense information and present a thorough explanation of Product, Clustered Column, Sales using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determining The Ransom Payment Paid By Organizations Over Cybersecurity Incident And Vulnerability
Determining The Ransom Payment Paid By Organizations Over Cybersecurity Incident And VulnerabilityDeliver an outstanding presentation on the topic using this Determining The Ransom Payment Paid By Organizations Over Cybersecurity Incident And Vulnerability. Dispense information and present a thorough explanation of Payments, Response Approaches using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPI Dashboard To Track Department Wise Security Incidents Cybersecurity Incident And Vulnerability
KPI Dashboard To Track Department Wise Security Incidents Cybersecurity Incident And VulnerabilityMentioned slide portrays KPI dashboard that can be used to monitor department wise security incidents. KPIs covered are new cases, total cases, resolved and pending cases. Present the topic in a bit more detail with this KPI Dashboard To Track Department Wise Security Incidents Cybersecurity Incident And Vulnerability. Use it as a tool for discussion and navigation on New Cases, In Progress, IT Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Line Chart Cybersecurity Incident And Vulnerability Response Playbook
Line Chart Cybersecurity Incident And Vulnerability Response PlaybookDeliver an outstanding presentation on the topic using this Line Chart Cybersecurity Incident And Vulnerability Response Playbook. Dispense information and present a thorough explanation of Line Chart using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Real Time Incident Management Dashboard Cybersecurity Incident And Vulnerability
Real Time Incident Management Dashboard Cybersecurity Incident And VulnerabilityFollowing slide illustrate KPI dashboard that can be used by organizations to track real time incident data. KPIs covered are number of tickets, average resolution time per customer, incidents registered per month. Present the topic in a bit more detail with this Real Time Incident Management Dashboard Cybersecurity Incident And Vulnerability. Use it as a tool for discussion and navigation on Average Resolution, Customer, Incidents Registered. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Cybersecurity Management Threat Vulnerability Asset Matrix
Information Security Program Cybersecurity Management Threat Vulnerability Asset MatrixMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Management Threat Vulnerability Asset Matrix. Dispense information and present a thorough explanation of Threat Vulnerability Asset Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Management Framework Defining Vulnerability Rating
Cybersecurity Risk Management Framework Defining Vulnerability RatingFollowing slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Management Framework Defining Vulnerability Rating. Dispense information and present a thorough explanation of Occurrence Attack, Asset Moderately Susceptible, Asset Highly Susceptible using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
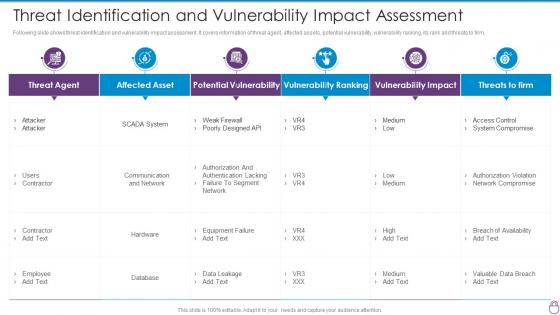 Cybersecurity Risk Management Framework Threat Identification And Vulnerability Impact
Cybersecurity Risk Management Framework Threat Identification And Vulnerability ImpactFollowing slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Management Framework Threat Identification And Vulnerability Impact. Dispense information and present a thorough explanation of Threat Agent, Affected Asset, Potential Vulnerability, Vulnerability Ranking, Vulnerability Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
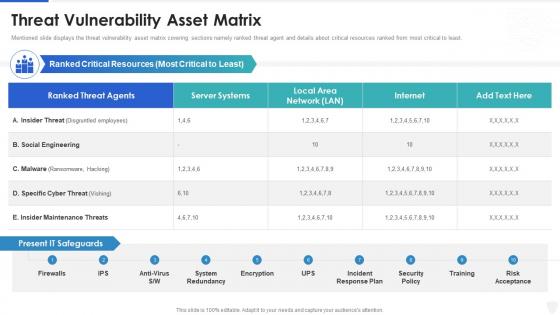 Cybersecurity and digital business risk management threat vulnerability asset matrix
Cybersecurity and digital business risk management threat vulnerability asset matrixMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an outstanding presentation on the topic using this Cybersecurity And Digital Business Risk Management Threat Vulnerability Asset Matrix. Dispense information and present a thorough explanation of Threat Vulnerability Asset Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Vulnerability Assessment Process Roadmap
Cybersecurity Vulnerability Assessment Process RoadmapThis slide depicts cybersecurity roadmap for vulnerability assessment illustrating steps such as vulnerability identification, analysis, risk assessment and remediation. Introducing our premium set of slides with Cybersecurity Vulnerability Assessment Process Roadmap. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Vulnerability Identification, Analysis, Risk Assessment, Remediation. So download instantly and tailor it with your information.
-
 Vulnerability Cybersecurity In Powerpoint And Google Slides Cpb
Vulnerability Cybersecurity In Powerpoint And Google Slides CpbPresenting our Vulnerability Cybersecurity In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases eight stages. It is useful to share insightful information on Vulnerability Cybersecurity This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management Plan
Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management PlanThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating Deliver an outstanding presentation on the topic using this Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Identification, Assessment, Vulnerability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Vulnerability Rating For Risk Identification Cybersecurity Risk Analysis And Management Plan
Vulnerability Rating For Risk Identification Cybersecurity Risk Analysis And Management PlanThis slide showcases table for allocating vulnerability rating to different class of information assets. Its shows information about severity, vulnerability score and description Deliver an outstanding presentation on the topic using this Vulnerability Rating For Risk Identification Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Vulnerability, Identification, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Assessment Matrix With Vulnerability And Threat Level Formulating Cybersecurity Plan
Risk Assessment Matrix With Vulnerability And Threat Level Formulating Cybersecurity PlanThis slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level. Present the topic in a bit more detail with this Risk Assessment Matrix With Vulnerability And Threat Level Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Risk Assessment Matrix, Vulnerability Level. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat Identification And Vulnerability Assessment Formulating Cybersecurity Plan
Threat Identification And Vulnerability Assessment Formulating Cybersecurity PlanThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Present the topic in a bit more detail with this Threat Identification And Vulnerability Assessment Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Vulnerability Severity, Threat Source, Likelihood. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Vulnerability Rating For Risk Identification Formulating Cybersecurity Plan
Vulnerability Rating For Risk Identification Formulating Cybersecurity PlanThis slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description. Introducing Vulnerability Rating For Risk Identification Formulating Cybersecurity Plan to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability Score, Risk Identification, using this template. Grab it now to reap its full benefits.
-
 Addressing The Cyber Incident Logging Process Cybersecurity Incident And Vulnerability
Addressing The Cyber Incident Logging Process Cybersecurity Incident And VulnerabilityThis slide displays logging process for a cyber incident logging. It covers information about process ID, procedure, its description and owner details. Present the topic in a bit more detail with this Addressing The Cyber Incident Logging Process Cybersecurity Incident And Vulnerability. Use it as a tool for discussion and navigation on Create New Incident, Complete Incident Details, Category And Priority. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing The Roles And Responsibilities Of Incident Response Cybersecurity Incident And Vulnerability
Addressing The Roles And Responsibilities Of Incident Response Cybersecurity Incident And VulnerabilityThis slide provides information about various roles and responsibilities of incident response team to effectively identify, report and take accurate measures against any cyber incident. Introducing Addressing The Roles And Responsibilities Of Incident Response Cybersecurity Incident And Vulnerability to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Incident First Response Team, Steering Committee, Cyber Incident Response Team, using this template. Grab it now to reap its full benefits.
-
 Addressing The Various Security Incidents And Attacks Cybersecurity Incident And Vulnerability
Addressing The Various Security Incidents And Attacks Cybersecurity Incident And VulnerabilityPurpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques. Increase audience engagement and knowledge by dispensing information using Addressing The Various Security Incidents And Attacks Cybersecurity Incident And Vulnerability. This template helps you present information on three stages. You can also present information on Traditional IT Security Incidents, Cyber Security Attacks, Common Techniques using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Asset Criticality Of Identified System Components Cybersecurity Incident And Vulnerability
Asset Criticality Of Identified System Components Cybersecurity Incident And VulnerabilityMentioned slide demonstrates the asset criticality of identified system components. It includes information of system name, component used, impact rating, criticality rating and failure cost. Deliver an outstanding presentation on the topic using this Asset Criticality Of Identified System Components Cybersecurity Incident And Vulnerability. Dispense information and present a thorough explanation of Host Computers, SCADA Software, Field Devices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Asset Maintenance Cost Assessment Sheet Cybersecurity Incident And Vulnerability
Asset Maintenance Cost Assessment Sheet Cybersecurity Incident And VulnerabilityFollowing slide displays assessment sheet that can be used by members to record overall asset maintenance cost for further analysis. Sections covered in the sheet are onsite solution, initial, monthly and annual cost. Introducing Asset Maintenance Cost Assessment Sheet Cybersecurity Incident And Vulnerability to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Data Storage, Application Servers, Email Servers, using this template. Grab it now to reap its full benefits.
-
 Backup Methods For Cyber Defense Planning Cybersecurity Incident And Vulnerability
Backup Methods For Cyber Defense Planning Cybersecurity Incident And VulnerabilityFollowing slide shows various backup methods as well as backup options that can be chosen for cyber defense planning. Methods covered are full, differential and incremental. Increase audience engagement and knowledge by dispensing information using Backup Methods For Cyber Defense Planning Cybersecurity Incident And Vulnerability. This template helps you present information on three stages. You can also present information on Backup Methods, Backup Options, Incremental using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Work From Home Data Security Practices Cybersecurity Incident And Vulnerability
Best Work From Home Data Security Practices Cybersecurity Incident And VulnerabilityPurpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc. Introducing Best Work From Home Data Security Practices Cybersecurity Incident And Vulnerability to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Configure WIFI Encryption, Avoid Using External Devices, System Update, using this template. Grab it now to reap its full benefits.
-
 Categorization Worksheet For System Components Cybersecurity Incident And Vulnerability
Categorization Worksheet For System Components Cybersecurity Incident And VulnerabilityThis slide illustrates categorization worksheet that can be used to categorize system components. It includes information about security system such as system name, its version, system location and other general information. Present the topic in a bit more detail with this Categorization Worksheet For System Components Cybersecurity Incident And Vulnerability. Use it as a tool for discussion and navigation on System Location, System Accessibility, IT Server Room. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist For Work From Home Data Security Cybersecurity Incident And Vulnerability
Checklist For Work From Home Data Security Cybersecurity Incident And VulnerabilityDeliver an outstanding presentation on the topic using this Checklist For Work From Home Data Security Cybersecurity Incident And Vulnerability. Dispense information and present a thorough explanation of Data Security, Reporting Process, Employees using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Ensure Asset Protection From Internal Threats Cybersecurity Incident And Vulnerability
Checklist To Ensure Asset Protection From Internal Threats Cybersecurity Incident And VulnerabilityFollowing slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Introducing Checklist To Ensure Asset Protection From Internal Threats Cybersecurity Incident And Vulnerability to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Employees, Email, Mobile Devices, using this template. Grab it now to reap its full benefits.
-
 Classifying Various Security Issues And Attacks Cybersecurity Incident And Vulnerability
Classifying Various Security Issues And Attacks Cybersecurity Incident And VulnerabilityPurpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks. Present the topic in a bit more detail with this Classifying Various Security Issues And Attacks Cybersecurity Incident And Vulnerability. Use it as a tool for discussion and navigation on Data Breaches, Data Loss, Risk Profiling. This template is free to edit as deemed fit for your organization. Therefore download it now.




