Powerpoint Templates and Google slides for Security Technique
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SS
Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SSThis slide showcases decrease in cyber attacks after implementation of mobile security. Its key elements are malware, phishing attacks and ransomware Deliver an outstanding presentation on the topic using this Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Advanced Persistent Threats, Diverse Cyber Threat Landscape using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Storage Area Network San Storage Area Network Security Techniques
Storage Area Network San Storage Area Network Security TechniquesThis slide represents the different SAN security methods, including their features. The purpose of this slide is to showcase the various Storage Area Network security techniques, including LUN masking, Zoning, WWN, Virtual SAN, DHCHAP, and CHAP. Introducing Storage Area Network San Storage Area Network Security Techniques To Increase Your Presentation Threshold. Encompassed With Six Stages, This Template Is A Great Option To Educate And Entice Your Audience. Dispence Information On LUN Masking, Security Techniques, Zoning Strategies, Using This Template. Grab It Now To Reap Its Full Benefits.
-
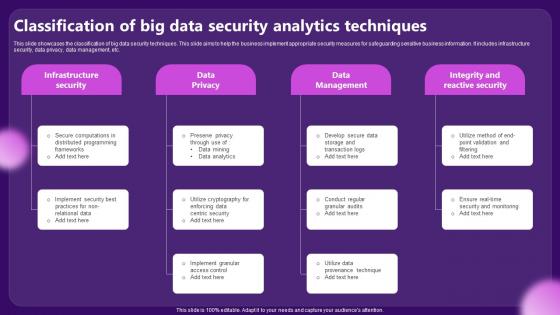 Classification Of Big Data Security Analytics Techniques
Classification Of Big Data Security Analytics TechniquesThis slide showcases the classification of big data security techniques. This slide aims to help the business implement appropriate security measures for safeguarding sensitive business information. It includes infrastructure security, data privacy, data management, etc. Presenting our set of slides with Classification Of Big Data Security Analytics Techniques. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Infrastructure Security, Data Management.
-
 Encryption Techniques Icon For Securing Big Data Analytics
Encryption Techniques Icon For Securing Big Data AnalyticsIntroducing our Encryption Techniques Icon For Securing Big Data Analytics set of slides. The topics discussed in these slides are Encryption Techniques, Securing Big Data Analytics. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
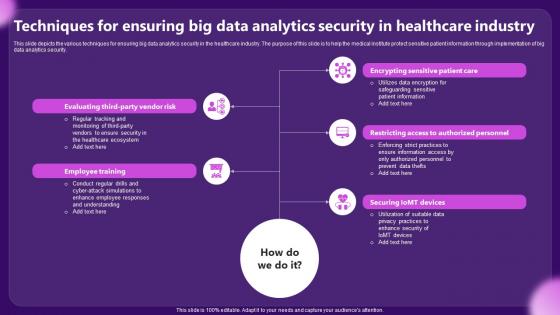 Techniques For Ensuring Big Data Analytics Security In Healthcare Industry
Techniques For Ensuring Big Data Analytics Security In Healthcare IndustryThis slide depicts the various techniques for ensuring big data analytics security in the healthcare industry. The purpose of this slide is to help the medical institute protect sensitive patient information through implementation of big data analytics security. Presenting our set of slides with Techniques For Ensuring Big Data Analytics Security In Healthcare Industry. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Employee Training, Securing Iomt Devices.
-
 Different Types Of Cryptographic Security Techniques Cloud Cryptography
Different Types Of Cryptographic Security Techniques Cloud CryptographyThis slide demonstrates the various cryptography methods. The purpose of this slide is to briefly explain the different types of cryptography techniques. These types are symmetric-key cryptography, asymmetric-key cryptography, hash functions, steganography, etc. Deliver an outstanding presentation on the topic using this Different Types Of Cryptographic Security Techniques Cloud Cryptography. Dispense information and present a thorough explanation of Cryptographic, Techniques, Quantum Cryptography using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Techniques To Prevent Eclipse Attack And Secure Funds Hands On Blockchain Security Risk BCT SS V
Techniques To Prevent Eclipse Attack And Secure Funds Hands On Blockchain Security Risk BCT SS VThe following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Introducing Techniques To Prevent Eclipse Attack And Secure Funds Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Random Node Selection, Deterministic Node Selection, New Node Restrictions, using this template. Grab it now to reap its full benefits.
-
 Techniques For Cyber Security Audit
Techniques For Cyber Security AuditThis slide covers approaches in cyber security audit and provides details about various techniques to protect systems from risk in a organization. It includes elements such as manual analysis , manual documentation, etc. Introducing our premium set of slides with Techniques For Cyber Security Audit. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Manual Specification Analysis, Automate Testing, Automate Static Analysis. So download instantly and tailor it with your information.
-
 Blockchain And Cybersecurity Techniques To Prevent Eclipse Attack And Secure Funds BCT SS V
Blockchain And Cybersecurity Techniques To Prevent Eclipse Attack And Secure Funds BCT SS VThe following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Techniques To Prevent Eclipse Attack And Secure Funds BCT SS V This template helps you present information on Four stages. You can also present information on Increased Node Connections, Deterministic Node Selection, New Node Restrictions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Your Digital Assets Techniques To Generate Money With Cryptocurrency
Secure Your Digital Assets Techniques To Generate Money With CryptocurrencyThe purpose of this slide is to outline the top ways of making money with cryptocurrency. This slide highlights the methods such as lending the cryptocurrency, mining, investing, trading, staking, etc. Increase audience engagement and knowledge by dispensing information using Secure Your Digital Assets Techniques To Generate Money With Cryptocurrency. This template helps you present information on seven stages. You can also present information on Techniques To Generate Money, Mining, Investing, Trading, Staking using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Threats In Blockchain Techniques To Prevent Eclipse Attack And Secure Funds BCT SS V
Cyber Threats In Blockchain Techniques To Prevent Eclipse Attack And Secure Funds BCT SS VThe following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Introducing Cyber Threats In Blockchain Techniques To Prevent Eclipse Attack And Secure Funds BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Mining Capability, Mining Capabilities, Much Faster Rate using this template. Grab it now to reap its full benefits.
-
 Techniques Employed Under SAP Cyber Security To Safeguard Company Networks
Techniques Employed Under SAP Cyber Security To Safeguard Company NetworksThis slide showcases the strategies employed under SAP cybersecurity to secure company networks. The purpose of this template is to help the business implement SAP cybersecurity measures through the use of techniques such as roles and authorizations, patch management, etc. Introducing our premium set of slides with Techniques Employed Under SAP Cyber Security To Safeguard Company Networks. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Roles And Authorizations, Patch Management, Transaction Monitoring. So download instantly and tailor it with your information.
-
 Firewall Network Security Types Of Network Address Translation Firewall Techniques
Firewall Network Security Types Of Network Address Translation Firewall TechniquesThis slide describes the different types of cloud-based firewall systems. The purpose of this slide is to give an overview of different kinds of cloud-based firewall systems, such as Next Generation firewalls, Security as a Service, and Firewall as a Service. Present the topic in a bit more detail with this Firewall Network Security Types Of Network Address Translation Firewall Techniques Use it as a tool for discussion and navigation on Robust Threat Prevention, Services To The Customers This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Firewall Techniques To Restrict Access And Ensure Web Client Security
Firewall Network Security Firewall Techniques To Restrict Access And Ensure Web Client SecurityThis slide outlines the many ways to control access and guarantee web client security policy. The purpose of this slide is to highlight the firewall techniques to limit user access and confirm web user security, such as service control, direction control, user control and behavior control. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Firewall Techniques To Restrict Access And Ensure Web Client Security This template helps you present information on Four stages. You can also present information on Market By Deployment, Market By Solution using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Sql Injection Sqli Technique Of Hacking
Ethical Hacking And Network Security Sql Injection Sqli Technique Of HackingThis slide depicts the SQL injection technique of hacking and how hackers can attack organizations critical information stored in databases through SQL queries. Present the topic in a bit more detail with this Ethical Hacking And Network Security Sql Injection Sqli Technique Of Hacking. Use it as a tool for discussion and navigation on Injection Technique Of Hacking, Attack Organizations, Sql Injection, Credit Card Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ethical Hacking And Network Security Techniques Used In Ethical Hacking
Ethical Hacking And Network Security Techniques Used In Ethical HackingThis slide represents the techniques of ethical hacking such as port scanning, analyzing and sniffing network traffic, detection of SQL injections, an inspection of patch installation. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Techniques Used In Ethical Hacking. This template helps you present information on six stages. You can also present information on Techniques Of Ethical Hacking, Port Scanning, Sniffing Network Traffic, Patch Installation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Techniques To Establish It Infrastructure And Cyber Security
Techniques To Establish It Infrastructure And Cyber SecurityThis slide depicts the multiple strategies to establish safeguard IT infrastructure and cybersecurity. The purpose of this slide is to help ensure robust safety measures are in place through the use of firewalls, authentication software, etc. Presenting our set of slides with Techniques To Establish It Infrastructure And Cyber Security This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Firewall, Antivirus And Antimalware Systems
-
 Implement Authentication Techniques For Wireless Lan Security
Implement Authentication Techniques For Wireless Lan SecurityThis slide highlights wireless security LAN checklist for preventing security threats and compile standard authentication and encryption techniques. It includes elements such as wireless lan security recommendations, applicable, not applicable and notes. Introducing our Implement Authentication Techniques For Wireless Lan Security set of slides. The topics discussed in these slides are Authentication, Techniques, Applicable. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Ethical Hacking And Network Security Cookie Theft Technique Of Hacking
Ethical Hacking And Network Security Cookie Theft Technique Of HackingThis slide depicts the cookie theft technique of hacking and how cookies are used to steal user sessions and use their information to perform malicious activities. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Cookie Theft Technique Of Hacking. This template helps you present information on four stages. You can also present information on Technique Of Hacking, Perform Malicious Activities, Customized Website, Session Hijacking using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Crosssite Scripting Technique Of Hacking Xss
Ethical Hacking And Network Security Crosssite Scripting Technique Of Hacking XssThis slide represents the cross-site scripting technique of hacking, its architecture, and how it works by modifying weak websites through malicious code. Deliver an outstanding presentation on the topic using this Ethical Hacking And Network Security Crosssite Scripting Technique Of Hacking Xss. Dispense information and present a thorough explanation of Cross Site Scripting, Technique Of Hacking, Modifying Weak Websites, Susceptible Program using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Techniques To Prevent Eclipse Attack And Secure Funds Guide For Blockchain BCT SS V
Techniques To Prevent Eclipse Attack And Secure Funds Guide For Blockchain BCT SS VThe following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Introducing Techniques To Prevent Eclipse Attack And Secure Funds Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Random Node Selection, Deterministic Node Selection using this template. Grab it now to reap its full benefits.
-
 Techniques To Prevent Eclipse Securing Blockchain Transactions A Beginners Guide BCT SS V
Techniques To Prevent Eclipse Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Increase audience engagement and knowledge by dispensing information using Techniques To Prevent Eclipse Securing Blockchain Transactions A Beginners Guide BCT SS V. This template helps you present information on four stages. You can also present information on Random Node Selection, New Node Restrictions, Increased Node Connections using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Network Security Threats And Optimization Techniques
Network Security Threats And Optimization TechniquesThis slide presents optimization strategies to prevent network security attacks. The purpose of this slide is to help businesses in securing their digital infrastructure against security threats through these optimization techniques. It covers solutions to prevent threats such as malware, phishing, DDoS and social engineering attacks. Introducing our premium set of slides with Network Security Threats And Optimization Techniques. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Secure, Software, Employees. So download instantly and tailor it with your information.
-
 Types And Techniques Of Cloning Risks In Cyber Security
Types And Techniques Of Cloning Risks In Cyber SecurityThis slide covers different types of cloning and techniques that provides attackers an unauthorized access to confidential data. It covers three types of cloning such as device, software and identity cloning. Introducing our Types And Techniques Of Cloning Risks In Cyber Security set of slides. The topics discussed in these slides are Device Cloning, Software Cloning, Identity Cloning. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Characteristics Of Internet Protocol Security Technique Encryption For Data Privacy In Digital Age It
Characteristics Of Internet Protocol Security Technique Encryption For Data Privacy In Digital Age ItThis slide demonstrates the various features of Internet Protocol Security IPsec mechanism. The properties of IPsec include authentication, privacy, integrity, key management, tunnelling, flexibility and interoperability. Introducing Characteristics Of Internet Protocol Security Technique Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Key Management, Interoperability, using this template. Grab it now to reap its full benefits.
-
 Major Techniques Of Cryptography In Cyber Security
Major Techniques Of Cryptography In Cyber SecurityThis slide elaborates on various approaches in cyber security and provides details about cryptography techniques to optimize security. It includes elements such as hashing, simple codes, etc. Introducing our premium set of slides with Major Techniques Of Cryptography In Cyber Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Steganography, Simple Codes, Symmetric Encryption. So download instantly and tailor it with your information.
-
 Techniques To Enhance Security Of Web Servers
Techniques To Enhance Security Of Web ServersFollowing slide highlights enhancing web server security through different techniques, also including elements such as segmented environment, track server logs, automate backup, etc. Introducing our Techniques To Enhance Security Of Web Servers set of slides. The topics discussed in these slides are Segmented Environment, Based Permissions, Automate Backup. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Security Audit Techniques For Operational Efficiency
Cloud Security Audit Techniques For Operational EfficiencyThis slide showcases cloud security audit techniques to analyze data retention such as configuration review, access controls assessments, etc. Introducing our premium set of slides with name Cloud Security Audit Techniques For Operational Efficiency. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Configuration Review, Access Controls Assessment, Patch Management Review, Vendor Security Evaluation. So download instantly and tailor it with your information.
-
 Data Security Best Practices To Protect Customer Information Database Marketing Techniques MKT SS V
Data Security Best Practices To Protect Customer Information Database Marketing Techniques MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Deliver an outstanding presentation on the topic using this Data Security Best Practices To Protect Customer Information Database Marketing Techniques MKT SS V. Dispense information and present a thorough explanation of Data Usage Policy, Data Encryption, Endpoint Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
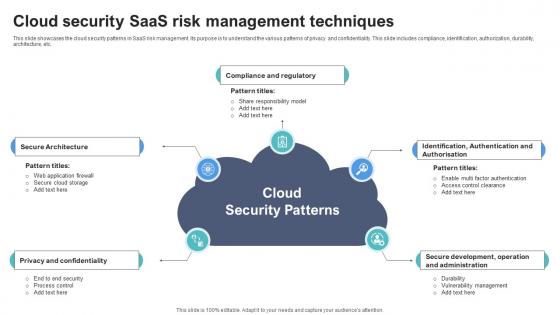 Cloud Security SaaS Risk Management Techniques
Cloud Security SaaS Risk Management TechniquesThis slide showcases the cloud security patterns in SaaS risk management. Its purpose is to understand the various patterns of privacy and confidentiality. This slide includes compliance, identification, authorization, durability, architecture, etc. Introducing Cloud Security SaaS Risk Management Techniques to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Secure Architecture, Privacy And Confidentiality, Cloud Security Patterns, Compliance And Regulatory, using this template. Grab it now to reap its full benefits.
-
 Prevention Techniques For Cyber Security Data Attacks
Prevention Techniques For Cyber Security Data AttacksThe highlighted slide identifies critical types of cybersecurity attacks on data, including malware, phishing, password attacks, man in the middle attacks, and SQL injection. This information is essential for understanding and preparing against various threats, contributing to a more robust defense strategy for safeguarding data. Introducing our Prevention Techniques For Cyber Security Data Attacks set of slides. The topics discussed in these slides are Malware Attack, Phishing Attack, Password Attack. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Different Types Of Security Gap Mitigation Techniques
Different Types Of Security Gap Mitigation TechniquesThis slide showcases various types of security gaps for data protection to showcase data encryption for shared data. This includes role-based access control, encrypted file sharing, regular security audits, etc. Presenting our set of slides with name Different Types Of Security Gap Mitigation Techniques. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Role Based Access Control, Data Encryption Techniques, Secure Data Access Methods.
-
 Techniques To Counter Mobile Security Threats
Techniques To Counter Mobile Security ThreatsThis slide highlights the techniques to counter mobile security threats which include remote wipe for lost devices, segment storage to prevent malware, etc. Presenting our set of slides with name Techniques To Counter Mobile Security Threats. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implement Network Security, Techniques To Counter, Mobile Security Threats.
-
 Additional Privacy And Security Techniques Comprehensive Approach To Privacy BCT SS
Additional Privacy And Security Techniques Comprehensive Approach To Privacy BCT SSThis slide covers methodologies to safeguard confidential information within blockchain system through techniques such as mixing, group signature, attribute based encryption, secure multi-party computation, etc with applications. Present the topic in a bit more detail with this Additional Privacy And Security Techniques Comprehensive Approach To Privacy BCT SS. Use it as a tool for discussion and navigation on Group Signature, Mixing, Attribute-Based Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Techniques To Achieve Web Application Security
Techniques To Achieve Web Application SecurityThis slide showcases approaches to ensure web application security. The purpose of this slide is to help businesses in protecting their data against cyber attacks. It covers techniques such as utilizing heuristic detection, implementing cybersecurity framework, adopting secure software development practices, etc. Introducing our premium set of slides with Techniques To Achieve Web Application Security Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Utilize Heuristic Detection, Implement Cybersecurity Framework, Security Measures So download instantly and tailor it with your information.
-
 Benefits Of Filtering Techniques In Email Security
Benefits Of Filtering Techniques In Email SecurityThis slide provides an outline of key benefits of filtering techniques in email security which include reputation-based email filters, safe listing and blocklisting. Introducing our Benefits Of Filtering Techniques In Email Security set of slides. The topics discussed in these slides are Benefits, Filtering Techniques, Email Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Objectives Of Email Security Filter Techniques
Objectives Of Email Security Filter TechniquesThis slide provides an outline of objectives of email security filter techniques which include stop spam by filtering out spammers, allow legitimate emails, etc. Presenting our set of slides with Objectives Of Email Security Filter Techniques. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Stop Spam, Control, Emails.
-
 Types Of Filtering Techniques In Email Security
Types Of Filtering Techniques In Email SecurityThis slide provides an outline of types of filtering techniques used in email security such as reputation-based email filters, safe listing and grey listing. Presenting our set of slides with Types Of Filtering Techniques In Email Security. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Types, Filtering Techniques, Email Security.
-
 Website Penetration Testing Techniques For Cyber Security
Website Penetration Testing Techniques For Cyber SecurityThis slide covers two major techniques of website penetration testing. It provides overview of both techniques on the basis of their functionality, testing approach and tools. Introducing our premium set of slides with Website Penetration Testing Techniques For Cyber Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Functionality, Testing Approach, Tools. So download instantly and tailor it with your information.
-
 Endpoint Security Objectives Of Endpoint Security Encryption Technique
Endpoint Security Objectives Of Endpoint Security Encryption TechniqueThis slide outlines the functions of encryption technique in endpoint security for safeguarding data on devices such as laptops, computers, etc. Increase audience engagement and knowledge by dispensing information using Endpoint Security Objectives Of Endpoint Security Encryption Technique. This template helps you present information on six stages. You can also present information on Restricts Unauthorized Access, Protects Valuable Corporate Data, Makes Data Unreadable, Safeguards Data On Devices using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Patch Management Technique For Endpoint Security
Endpoint Security Patch Management Technique For Endpoint SecurityThis slide outlines the overview of patch management technique in endpoint security to scan, identify, download, and deploy patches. Introducing Endpoint Security Patch Management Technique For Endpoint Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Fresh Network Security Approach, Works For Windows And Mac, Quick Threat Response, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Selection Of Optimal Application Security Technique
Application Security Implementation Plan Selection Of Optimal Application Security TechniqueThis slide outlines the comparison of different application testing techniques on the basis of parameters such as security provided and cost. Present the topic in a bit more detail with this Application Security Implementation Plan Selection Of Optimal Application Security Technique. Use it as a tool for discussion and navigation on Authorization, Encryption, Security Testing, Access Control. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Main Data Security Tokenization Techniques
Tokenization For Improved Data Security Main Data Security Tokenization TechniquesThis slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc. Introducing Tokenization For Improved Data Security Main Data Security Tokenization Techniques to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Transactional, Governance Tokenization, Utility Tokenization, Platform Tokenization, using this template. Grab it now to reap its full benefits.
-
 Data Destruction Techniques For Securely Disposing Data Lifecycle Management To Enhance Flow
Data Destruction Techniques For Securely Disposing Data Lifecycle Management To Enhance FlowThis slide presents various data destruction techniques for securely disposing of data. It provides details about techniques such as, overwriting, degussing, physical destruction, cryptographic erasure and secure erase. Present the topic in a bit more detail with this Data Destruction Techniques For Securely Disposing Data Lifecycle Management To Enhance Flow. Use it as a tool for discussion and navigation on Physical Destruction, Cryptographic Erasure, Secure Erase, Data Destruction Technique. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Gamification Techniques To Enhance Cyber Security Awareness
Gamification Techniques To Enhance Cyber Security AwarenessThe purpose of this slide is to incorporate various gamification techniques, providing a hands-on and enjoyable approach to cybersecurity training to solve practical challenges including techniques such as points and badges, leaderboards, etc. Presenting our well structured Gamification Techniques To Enhance Cyber Security Awareness. The topics discussed in this slide are Points And Badges, Leaderboards, Interactive Quizzes, Cyber Security Awareness. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 DOS Attack Techniques To Overcome Security Systems
DOS Attack Techniques To Overcome Security SystemsFollowing slide represents overcoming security systems by DOS attack techniques for enhanced risk to system. It further covers techniques such as spoofing, amplification, reflection, etc. Presenting our set of slides with name DOS Attack Techniques To Overcome Security Systems. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Amplification, Reflection, Spoofing.
-
 Regular Backup Techniques Application Business Recovery Plan To Overcome Cyber Security Threat
Regular Backup Techniques Application Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information on various methods of data backups that should be implemented by a company to avoid data loss. It includes data backup types such as full, incremental, differential, and mirror. Present the topic in a bit more detail with this Regular Backup Techniques Application Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Techniques, Application, Incremental. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 E Commerce Subscription Data Security Management Techniques
E Commerce Subscription Data Security Management TechniquesThis slide highlights the techniques to secure e-commerce subscription data to ensure data protection and management for trust building. Key strategies are encryption strategy, hand-on monitoring, and contingency planning. Introducing our premium set of slides with E Commerce Subscription Data Security Management Techniques Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Encryption Strategy, Hands-On Monitoring, Contingency Planning So download instantly and tailor it with your information.
-
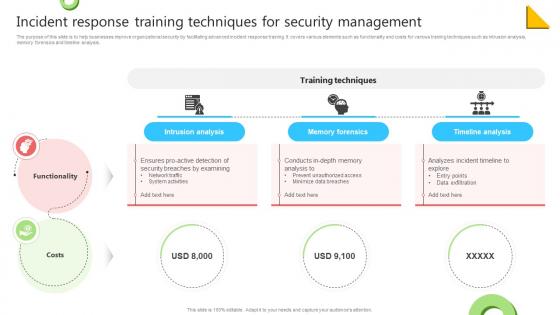 Incident Response Training Techniques For Security Management
Incident Response Training Techniques For Security ManagementThe purpose of this slide is to help businesses improve organizational security by facilitating advanced incident response training. It covers various elements such as functionality and costs for various training techniques such as intrusion analysis, memory forensics and timeline analysis. Introducing our premium set of slides with Incident Response Training Techniques For Security Management Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Intrusion Analysis, Memory Forensics, Timeline Analysis So download instantly and tailor it with your information.
-
 Secure Retirement Planning With Key Activities Wealth Management Techniques Fin SS V
Secure Retirement Planning With Key Activities Wealth Management Techniques Fin SS VThis slide shows information which can be utilized to know basics of retirement planning. It also includes details about key activities included in retirement planning which are lifestyle assessment, income projection, etc. Introducing Secure Retirement Planning With Key Activities Wealth Management Techniques Fin SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Income Projection, Savings Strategies using this template. Grab it now to reap its full benefits.
-
 Web Security Upgradation Selection Of Optimal Web Security Technique
Web Security Upgradation Selection Of Optimal Web Security TechniqueThis slide highlights the comparison of different web security techniques which include Web Application Firewall, vulnerability scanners, etc. Present the topic in a bit more detail with this Web Security Upgradation Selection Of Optimal Web Security Technique. Use it as a tool for discussion and navigation on Techniques, Cost, Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Techniques To Boost Security And Privacy Of Chatbots
Techniques To Boost Security And Privacy Of ChatbotsThis slide shows information regarding various methods that are used by organizations to increase or improve their chatbot security. These techniques are threat modeling, vulnerability assessment, and penetration testing. Introducing our premium set of slides with Techniques To Boost Security And Privacy Of Chatbots. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Threat Modelling, Vulnerability Assessment, Penetration Testing. So download instantly and tailor it with your information.
-
 Organizational Physical Security Development Techniques
Organizational Physical Security Development TechniquesThis slide highlights various techniques to enhance physical security environment by providing real-time tracking and monitoring of activities. The different measures are access control systems, surveillance cameras, detection systems, etc. Introducing our premium set of slides with Organizational Physical Security Development Techniques. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Control Systems, Surveillance Cameras, Detection Systems, Security Personnel. So download instantly and tailor it with your information.
-
 User Authentication Techniques To Enhance Organizational Security
User Authentication Techniques To Enhance Organizational SecurityThis slide shows the different user authentication and authorization techniques that help to protect sensitive data. The various techniques explained are password-based, multi-factor, biometric, token-based, etc. Introducing our premium set of slides with User Authentication Techniques To Enhance Organizational Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Password Based, Multi Factor, Biometric, Token Based. So download instantly and tailor it with your information.
-
 Recent Trends In Web Security Techniques
Recent Trends In Web Security TechniquesThis slide highlights the key trends of web security which include rise in IoT devices, zero trust cyber security, multi-factor authentication, etc. Introducing Recent Trends In Web Security Techniques to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Integration Of Artificial Intelligence Ml, Multi-Factor Authentication, Growing It Skills Gap, using this template. Grab it now to reap its full benefits.
-
 Techniques Of Including Security Configuration Management
Techniques Of Including Security Configuration ManagementThis slide depicts the techniques to handle security configuration management in an enterprise. Its aim is to reduce security vulnerabilities. This slide includes monitoring, endpoint, configuration, avoid jams, etc. Introducing our premium set of slides with name Techniques Of Including Security Configuration Management. Ellicudate the Seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Configure Remote Endpoints, Monitor Results, Operating System Endpoint. So download instantly and tailor it with your information.
-
 Statistical Analysis Applications In Cyber Security Statistical Analysis Techniques
Statistical Analysis Applications In Cyber Security Statistical Analysis TechniquesThe purpose of this slide is to represent the uses of statistical analysis in cyber security. These include anomaly detection, intrusion detection, risk assessment, incident response, phishing detection and vulnerability assessment. Introducing Statistical Analysis Applications In Cyber Security Statistical Analysis Techniques to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Anomaly Detection, Intrusion Detection, Risk Assessment, Incident Response, using this template. Grab it now to reap its full benefits.
-
 How Different Biometric Technique Can Enhance Mobile Device Security Cybersecurity SS
How Different Biometric Technique Can Enhance Mobile Device Security Cybersecurity SSThis slide showcases use cases of different biometric techniques for enhancing mobile security. Biometric techniques used are fingerprint scanner, facial recognition, voice recognition etc. Introducing How Different Biometric Technique Can Enhance Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Company Financial Loss, Operational Disruption using this template. Grab it now to reap its full benefits.
-
 Mobile Application Security Techniques Mobile Device Security Cybersecurity SS
Mobile Application Security Techniques Mobile Device Security Cybersecurity SSThis slide showcases plan that can help to implement mobile device application techniques. Its key elements are risk assessment, security policies, Wi-Fi configurations etc. Introducing Mobile Application Security Techniques Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Global Mobile Cyber Attacks, Telegram And Twitter using this template. Grab it now to reap its full benefits.
-
 Plan To Implement Different Mobile Biometric Techniques Mobile Device Security Cybersecurity SS
Plan To Implement Different Mobile Biometric Techniques Mobile Device Security Cybersecurity SSThis slide showcases plan that can help company to implement mobile biometric solutions. Its key components are biometric technique, team responsible, expected benefits, progress and budget allocated. Deliver an outstanding presentation on the topic using this Plan To Implement Different Mobile Biometric Techniques Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Policy Development, Choose Solution, Train Users using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.




