Powerpoint Templates and Google slides for Secure Digital
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Encryption Adaptability To Tackle Recent Security Challenges Encryption For Data Privacy In Digital Age It
Encryption Adaptability To Tackle Recent Security Challenges Encryption For Data Privacy In Digital Age ItThis slide discusses about the increasing adoption of encryption to solve current cyber security issues. The key points discussed are more use of cloud encryption in banking sector, introduction of homomorphic encryption, increase in BYOE adoption, etc. Increase audience engagement and knowledge by dispensing information using Encryption Adaptability To Tackle Recent Security Challenges Encryption For Data Privacy In Digital Age It. This template helps you present information on five stages. You can also present information on Homomorphic, Encryption, Introduction using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 End To End Encryption To Secure Digital Ecosystems Encryption For Data Privacy In Digital Age It
End To End Encryption To Secure Digital Ecosystems Encryption For Data Privacy In Digital Age ItThis slide discusses about the end to end encryption methodology. It secures the communication between sender and receiver. The purpose of this slide is to show the data flow between two users using end to end encryption technique. Present the topic in a bit more detail with this End To End Encryption To Secure Digital Ecosystems Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Encryption, Digital Ecosystems, Communication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Factors Responsible For Cloud Security Failures Encryption For Data Privacy In Digital Age It
Factors Responsible For Cloud Security Failures Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc. Introducing Factors Responsible For Cloud Security Failures Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Data Protection, Poor Key Management, Software Engineers, using this template. Grab it now to reap its full benefits.
-
 Internet Protocol Security Architecture And Working Encryption For Data Privacy In Digital Age It
Internet Protocol Security Architecture And Working Encryption For Data Privacy In Digital Age ItThis slide demonstrates the working of Internet Protocol Security. The main components of IPsec architecture are ESP protocol, AH protocol, encryption algorithm, authentication algorithm, key management, etc. Present the topic in a bit more detail with this Internet Protocol Security Architecture And Working Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Protocol Security, Architecture, Encryption Algorithm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Introduction To Hypertext Transfer Protocol Secure Encryption For Data Privacy In Digital Age It
Introduction To Hypertext Transfer Protocol Secure Encryption For Data Privacy In Digital Age ItThis slide talks about the Hypertext Transfer Protocol Secure HTTPS, which is an advance version of HTTP. The purpose of this slide is to discuss the importance of using HTTPS to encrypt communication between browser and server. Present the topic in a bit more detail with this Introduction To Hypertext Transfer Protocol Secure Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Introduction, Overview, Protocol Secure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Components Of Internet Protocol Security Encryption For Data Privacy In Digital Age It
Key Components Of Internet Protocol Security Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to discuss the main components of Internet Protocol Security IPsec architecture. These three components are Encapsulating Security Payload ESP, Authentication Header AH, and Internet Key Exchange IKE. Deliver an outstanding presentation on the topic using this Key Components Of Internet Protocol Security Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Authentication Header, Internet Key Exchange, Encapsulating Security Payload using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Limitations Transfer Protocol Secure And Solutions Encryption For Data Privacy In Digital Age It
Limitations Transfer Protocol Secure And Solutions Encryption For Data Privacy In Digital Age ItThis slide talks about the challenges of Hypertext Transfer Protocol Secure HTTPS and their possible solutions. These challenges are lack of end-to-end encryption, certificate authority vulnerabilities, difficulty in detecting malicious content, and complexity and cost of certificate management. Present the topic in a bit more detail with this Limitations Transfer Protocol Secure And Solutions Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Limitations, Solutions, Description. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Relationship Between Byoe And Hardware Security Module Encryption For Data Privacy In Digital Age It
Relationship Between Byoe And Hardware Security Module Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to highlight the benefits and capabilities of Hardware Security Modules HSMs. The key components included are cloud server, private key, encrypted request, encrypted data, HSM isolated environment, etc. Deliver an outstanding presentation on the topic using this Relationship Between Byoe And Hardware Security Module Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Relationship, Hardware, Cryptographic using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Socket Layer Ssl Security Technology Encryption For Data Privacy In Digital Age It
Secure Socket Layer Ssl Security Technology Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the role of HTTPS in encrypting web communication and use of the Secure Sockets Layer SSL protocol for secure connections. This slide also discusses the incorporation of symmetric and asymmetric encryption during the SSL handshake. Deliver an outstanding presentation on the topic using this Secure Socket Layer Ssl Security Technology Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Technology, Asymmetric, Symmetric using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps Followed By Internet Protocol Security Connections Encryption For Data Privacy In Digital Age It
Steps Followed By Internet Protocol Security Connections Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to outline the working steps of Internet Protocol Security connections. These are key exchange, packet headers and trailers, packet authentication, encryption, data transmission and decryption of data packets. Deliver an outstanding presentation on the topic using this Steps Followed By Internet Protocol Security Connections Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Connections, Protocol Security, Data Transmission using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tunnel And Transport Modes Of Internet Protocol Security Encryption For Data Privacy In Digital Age It
Tunnel And Transport Modes Of Internet Protocol Security Encryption For Data Privacy In Digital Age ItThis slide talks about the distinction between the two methods of protecting information transmission. The purpose of this slide is to explain the concepts of transport mode and tunnel mode in the context of securing data during communication. Present the topic in a bit more detail with this Tunnel And Transport Modes Of Internet Protocol Security Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Transport Mode, Protocol Security, Transmission. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Types Of Secure Sockets Layer Certificates Encryption For Data Privacy In Digital Age It
Types Of Secure Sockets Layer Certificates Encryption For Data Privacy In Digital Age ItThis slide demonstrates the different forms of Secure Sockets Layer certificates such as single domain, wildcard and multi-domain. This slide also discusses the types of SSL certificates based on validation such as domain, organization and extended validation. Deliver an outstanding presentation on the topic using this Types Of Secure Sockets Layer Certificates Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Domain Validation, Organization Validation, Extended Validation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Working Of Hypertext Transfer Protocol Secure Encryption For Data Privacy In Digital Age It
Working Of Hypertext Transfer Protocol Secure Encryption For Data Privacy In Digital Age ItThis slide illustrates the flow of several components in the working of Hypertext Transfer Protocol Secure HTTPS. The purpose of this slide is to showcase how data is encrypted in transit and transferred to the user using public and private keys. Present the topic in a bit more detail with this Working Of Hypertext Transfer Protocol Secure Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Asymmetric Encryption, Symmetric Encryption, Transmission. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Ensure Secure Mobile Banking Digital Wallets For Making Hassle Fin SS V
Checklist To Ensure Secure Mobile Banking Digital Wallets For Making Hassle Fin SS VThis slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Present the topic in a bit more detail with this Checklist To Ensure Secure Mobile Banking Digital Wallets For Making Hassle Fin SS V. Use it as a tool for discussion and navigation on Secure, Banking, Mobile. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mobile Banking Application Security Testing Digital Wallets For Making Hassle Fin SS V
Mobile Banking Application Security Testing Digital Wallets For Making Hassle Fin SS VThis slide shows various tools which can be used to evaluate or analyze the security level of mobile banking apps. It includes features and ratings of applications. It also contains various tools such as ImmuniWeb MobileSuite, CodifiedSecurity, QARK, etc. Deliver an outstanding presentation on the topic using this Mobile Banking Application Security Testing Digital Wallets For Making Hassle Fin SS V. Dispense information and present a thorough explanation of Banking, Mobile, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Agenda IoT Security And Privacy Safeguarding The Digital Ecosystem IoT SS
Agenda IoT Security And Privacy Safeguarding The Digital Ecosystem IoT SSIntroducing Agenda IoT Security And Privacy Safeguarding The Digital Ecosystem IoT SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Agenda, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For IoT Security And Privacy Safeguarding The Digital Ecosystem IoT SS
Icons Slide For IoT Security And Privacy Safeguarding The Digital Ecosystem IoT SSPresenting our well crafted Icons Slide For IoT Security And Privacy Safeguarding The Digital Ecosystem IoT SS set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly
-
 Digital Systems Engineering Creation Of Secure Networks Using Mbse Principles
Digital Systems Engineering Creation Of Secure Networks Using Mbse PrinciplesThe purpose of this slide is to explain how MBSE principles can be applied to create secure networks and align with the criteria and models of information security management systems. This slide also highlights the steps involved, such as plan, do, check, and act. Present the topic in a bit more detail with this Digital Systems Engineering Creation Of Secure Networks Using Mbse Principles. Use it as a tool for discussion and navigation on Techniques, Information, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Various Types Of Blockchain Virtual Assets Security Tokens Managing Digital Wealth BCT SS
Various Types Of Blockchain Virtual Assets Security Tokens Managing Digital Wealth BCT SSThe following slide depicts details about security tokens to offer benefits to investors. It includes elements such as stocks, bonds, real world assets, improved liquidity, foster innovation, transparency, automated payments, etc. Increase audience engagement and knowledge by dispensing information using Various Types Of Blockchain Virtual Assets Security Tokens Managing Digital Wealth BCT SS This template helps you present information on Four stages. You can also present information on Improved Liquidity, Foster Innovation, Offers Transparency using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enhancing E Commerce Security With Unlocking Digital Wallets All You Need Fin SS
Enhancing E Commerce Security With Unlocking Digital Wallets All You Need Fin SSThis slide highlights the application of digital wallets to enhance the security of e-commerce platforms. Key technologies are tokenization, biometric authentication, and two-factor authentication. Increase audience engagement and knowledge by dispensing information using Enhancing E Commerce Security With Unlocking Digital Wallets All You Need Fin SS. This template helps you present information on three stages. You can also present information on Biometric Authentication, Two-Factor Authentication, Tokenization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Future Of Digital Wallet Security And Safety Unlocking Digital Wallets All You Need Fin SS
Future Of Digital Wallet Security And Safety Unlocking Digital Wallets All You Need Fin SSThis slide exhibits the future of digital wallet security using various technologies and regulations that help to promote the seamless working of online transactions. The major components are biometric authorization, government regulations, artificial intelligence, etc. Introducing Future Of Digital Wallet Security And Safety Unlocking Digital Wallets All You Need Fin SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Government Regulations, Biometric Authorization, Decentralized Wallets, using this template. Grab it now to reap its full benefits.
-
 Security In IoT Payment For Digital Wallet Unlocking Digital Wallets All You Need Fin SS
Security In IoT Payment For Digital Wallet Unlocking Digital Wallets All You Need Fin SSThe following slide highlights the security measures for IoT and digital wallet that ensure secure data transfer from one device to another. Key components are security credentials, device authentication, and consumer authentication. Introducing Security In IoT Payment For Digital Wallet Unlocking Digital Wallets All You Need Fin SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Security Credentials, Device Authentication, Consumer Authentication, using this template. Grab it now to reap its full benefits.
-
 Digital Facility Security Assessment Checklist
Digital Facility Security Assessment ChecklistThe purpose of this slide is to systematically evaluate and enhance security measures of digital facility by identifying potential vulnerabilities and implementing necessary safeguards. Introducing our Digital Facility Security Assessment Checklist set of slides. The topics discussed in these slides are Access Control Systems, Check Fencing Condition, Monitor Entry Point Systems, Intrusion Detection. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Best Practices To Maintain Digital Wallet Security Implementation Of Cashless Payment
Best Practices To Maintain Digital Wallet Security Implementation Of Cashless PaymentMentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private.Increase audience engagement and knowledge by dispensing information using Best Practices To Maintain Digital Wallet Security Implementation Of Cashless Payment This template helps you present information on five stages. You can also present information on Responsible Managers, Segregate Duties, Bank Statements using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Adopting Homomorphic Encryption To Secure Cloud Ai Driven Digital Transformation Planning DT SS
Adopting Homomorphic Encryption To Secure Cloud Ai Driven Digital Transformation Planning DT SSThis slide provides glimpse about utilizing homomorphic encryption approach that can help businesses in privacy preservation. It includes stages such as encryption, computation, decryption, etc. Deliver an outstanding presentation on the topic using this Adopting Homomorphic Encryption To Secure Cloud Ai Driven Digital Transformation Planning DT SS. Dispense information and present a thorough explanation of Architecture, Return Results, Benefits using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Incorporating Secure Multi-Party Computation To Boost Data Ai Driven Digital Transformation Planning DT SS
Incorporating Secure Multi-Party Computation To Boost Data Ai Driven Digital Transformation Planning DT SSThis slide provides glimpse about utilizing secure multi-party computation SMPC approach that can help businesses in boosting data confidentiality. It includes stages such as input sharing, secure computation, output reconstruction, etc. Present the topic in a bit more detail with this Incorporating Secure Multi-Party Computation To Boost Data Ai Driven Digital Transformation Planning DT SS. Use it as a tool for discussion and navigation on Secure Computation, Output Reconstruction, Input Sharing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Adopting Homomorphic Encryption To Secure Cloud Complete Guide Of Digital Transformation DT SS V
Adopting Homomorphic Encryption To Secure Cloud Complete Guide Of Digital Transformation DT SS VThis slide provides glimpse about utilizing homomorphic encryption approach that can help businesses in privacy preservation. It includes stages such as encryption, computation, decryption, etc. Deliver an outstanding presentation on the topic using this Adopting Homomorphic Encryption To Secure Cloud Complete Guide Of Digital Transformation DT SS V. Dispense information and present a thorough explanation of Privacy Preservation, Secure Cloud Computing, Computation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Incorporating Secure Multi Party Computation To Boost Complete Guide Of Digital Transformation DT SS V
Incorporating Secure Multi Party Computation To Boost Complete Guide Of Digital Transformation DT SS VThis slide provides glimpse about utilizing secure multi-party computation SMPC approach that can help businesses in boosting data confidentiality. It includes stages such as input sharing, secure computation, output reconstruction, etc. Present the topic in a bit more detail with this Incorporating Secure Multi Party Computation To Boost Complete Guide Of Digital Transformation DT SS V. Use it as a tool for discussion and navigation on Benefits, Secure Computation, Output Reconstruction, Input Sharing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices To Maintain Digital Wallet Security Improve Transaction Speed By Leveraging
Best Practices To Maintain Digital Wallet Security Improve Transaction Speed By LeveragingMentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Introducing Best Practices To Maintain Digital Wallet Security Improve Transaction Speed By Leveraging to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Secure Network Connection, Secure Login Credentials, Keep Personal Data Private using this template. Grab it now to reap its full benefits.
-
 Cyber Security Policy Icon For Securing Digital Assets
Cyber Security Policy Icon For Securing Digital AssetsPresenting our set of slides with Cyber Security Policy Icon For Securing Digital Assets This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Policy Icon, Securing Digital Assets
-
 Applications Of Digital Solution For Ensuring Data Security
Applications Of Digital Solution For Ensuring Data SecurityThis slide showcases use cases of digital solution. The main purpose of this template is to showcase methods for optimizing resources in business. This includes streamlining operations, improving decision making, enabling remote work, etc. Presenting our set of slides with Applications Of Digital Solution For Ensuring Data Security This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Streamlining Operations, Enhancing Customer Experience, Improve Decision Making
-
 Networking Security Icon For Futuristic Digital Transformation
Networking Security Icon For Futuristic Digital TransformationPresenting our set of slides with name Networking Security Icon For Futuristic Digital Transformation. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Networking Security, Icon For Futuristic, Digital Transformation.
-
 Blockchains Impact On Education Secured Digital Credential Categories For Accreditation BCT SS V
Blockchains Impact On Education Secured Digital Credential Categories For Accreditation BCT SS VThis slide covers types of online credentials within the context of accreditation in education sector. It includes credentials such as digital certificates, Micro credentials, stacked and blockchain credentials facilitating blockchain transactions. Introducing Blockchains Impact On Education Secured Digital Credential Categories For Accreditation BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Digital Certificates, Micro Credentials, Stacked Credentials using this template. Grab it now to reap its full benefits.
-
 Best Practices To Maintain Digital Wallet Security Enhancing Transaction Security With E Payment
Best Practices To Maintain Digital Wallet Security Enhancing Transaction Security With E PaymentMentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Increase audience engagement and knowledge by dispensing information using Best Practices To Maintain Digital Wallet Security Enhancing Transaction Security With E Payment This template helps you present information on five stages. You can also present information on Enable Password, Secure Network Connection, Secure Login Credentials using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cryptocurrency Payment Overview For Enhancing Digital Transaction Enhancing Transaction Security With E Payment
Cryptocurrency Payment Overview For Enhancing Digital Transaction Enhancing Transaction Security With E PaymentMentioned slide provides overview of cryptocurrency as a cashless payment solution which can be implemented by businesses to reach global customers. It includes key components such as description, types, and popular cryptocurrencies. Increase audience engagement and knowledge by dispensing information using Cryptocurrency Payment Overview For Enhancing Digital Transaction Enhancing Transaction Security With E Payment This template helps you present information on four stages. You can also present information on Security, Exchange, Payment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secured Digital Credential Categories For Accreditation Blockchain Role In Education BCT SS
Secured Digital Credential Categories For Accreditation Blockchain Role In Education BCT SSThis slide covers types of online credentials within the context of accreditation in education sector. It includes credentials such as digital certificates, Micro-credentials, stacked and blockchain credentials facilitating blockchain transactions. Introducing Secured Digital Credential Categories For Accreditation Blockchain Role In Education BCT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Digital Certificates, Micro Credentials, Stacked Credentials using this template. Grab it now to reap its full benefits.
-
 Security Digital Hub Transformation In Workplace
Security Digital Hub Transformation In WorkplaceThis slide showcases the digital hub transformation workplace. Its aim is to integrate the workplace with digital platforms with easy user experience. This slide includes document, intranet, voice, video, enterprise, productivity apps, etc. Presenting our well structured Security Digital Hub Transformation In Workplace. The topics discussed in this slide are Document, Intranet, Social Network Enterprise. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Architecture Of Security Testing In Digital Landscape
Architecture Of Security Testing In Digital LandscapeThis slide highlights the architecture of security testing components such as user interface, controller, tester, test report, test case, etc. Present the topic in a bit more detail with this Architecture Of Security Testing In Digital Landscape. Use it as a tool for discussion and navigation on Source Code Analyzer, Web Application Scanner, Host Vulnerability, Scanner. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
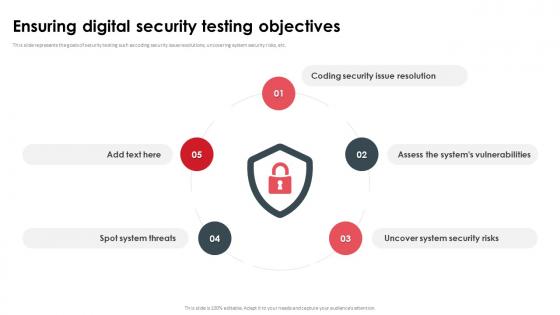 Ensuring Digital Security Testing Objectives
Ensuring Digital Security Testing ObjectivesThis slide represents the goals of security testing such as coding security issue resolutions, uncovering system security risks, etc. Introducing Ensuring Digital Security Testing Objectives to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Spot System Threats, Coding Security Issue Resolution, Uncover System Security Risks, using this template. Grab it now to reap its full benefits.
-
 Introduction Of Security Testing In Digital Landscape
Introduction Of Security Testing In Digital LandscapeThis slide highlights the overview of security testing such as discovering and securing vulnerabilities, ensuring a threat-free software environment, etc. Introducing Introduction Of Security Testing In Digital Landscape to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Discover And Secure Vulnerabilities, Identify System Weaknesses, Digital Landscape, using this template. Grab it now to reap its full benefits.
-
 Icon For Digital Forensics In Information Security
Icon For Digital Forensics In Information SecurityIntroducing our premium set of slides with Icon For Digital Forensics In Information Security. Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon For Digital, Forensics In Information Security. So download instantly and tailor it with your information.
-
 Endpoint Cyber Security Framework For Digital Transformation
Endpoint Cyber Security Framework For Digital TransformationThis slide lays out unified endpoint cyber security framework to prevent digital data threats. The purpose of this slide is to support business in digital transformation through endpoint management system It covers actions such as identification, protection, detection, response, recovery, etc. Presenting our set of slides with Endpoint Cyber Security Framework For Digital Transformation This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Protect, Detect
-
 Endpoint Cyber Security Icon For Digital Transformation
Endpoint Cyber Security Icon For Digital TransformationIntroducing our premium set of slides with Endpoint Cyber Security Icon For Digital Transformation Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Endpoint Cyber Security Icon, Digital Transformation So download instantly and tailor it with your information.
-
 Strategies To Secure Digital Banking Channels
Strategies To Secure Digital Banking ChannelsThe purpose of this slide is to help banking professionals secure digital channels for prevention of potential threats. It covers security solutions for various threats such as phishing, ransomware, advanced persistent threats, etc. Introducing our premium set of slides with Strategies To Secure Digital Banking Channels. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Threats,Phishing,Ransomware.So download instantly and tailor it with your information.
-
 Steps To Implement Digital Authentication With IAM Securing Systems With Identity
Steps To Implement Digital Authentication With IAM Securing Systems With IdentityThis slide discusses the IAM implementing digital authentication. The purpose of this slide is to highlight the various types of digital authentication done by IAM, which are unique passwords, pre-shared keys, Behavioral authentication, and biometrics. Increase audience engagement and knowledge by dispensing information using Steps To Implement Digital Authentication With IAM Securing Systems With Identity This template helps you present information on Five stages. You can also present information on Unique Passwords, Biometrics using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 ERP Digital Transformation Icon For Improving Data Security
ERP Digital Transformation Icon For Improving Data SecurityIntroducing our premium set of slides with ERP Digital Transformation Icon For Improving Data Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like ERP Digital Transformation, Icon, Improving Data Security. So download instantly and tailor it with your information.
-
 Challenges Related To Cyber Security In Digital Banking
Challenges Related To Cyber Security In Digital BankingThis slide represents concerns with safety in digital banking. It aims to invest in robust cyber security measures, stay informed about emerging threats, collaborate with industry peers, and prioritize security education and awareness for both customers and employees. It includes various approaches such as lack of awareness, inadequate budgeting and lack of management, etc. Introducing our premium set of slides with Challenges Related To Cyber Security In Digital Banking. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Inadequate Awareness, Apps And Mobile Devices, Increase Ransomware. So download instantly and tailor it with your information.
-
 Icon For Cyber Security In Banking To Ensure Digitization Of Services
Icon For Cyber Security In Banking To Ensure Digitization Of ServicesIntroducing our premium set of slides with Icon For Cyber Security In Banking To Ensure Digitization Of Services. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon, Cyber Security, Banking To Ensure, Digitization Services. So download instantly and tailor it with your information.
-
 Solutions For Threat Of Cyber Security In Digital Banking
Solutions For Threat Of Cyber Security In Digital BankingThis slide represents remedies to cyber security problem in internet banking. It aims to adopt holistic and proactive approach to cyber security that encompasses technology, processes, and people. It includes various solutions such as integrated security, protecting information, etc. Introducing our premium set of slides with Solutions For Threat Of Cyber Security In Digital Banking. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Integrated Security, Security Integration, Spent Money. So download instantly and tailor it with your information.
-
 Email Security Best Practices Features Of Email Security In Digital Age
Email Security Best Practices Features Of Email Security In Digital AgeThis slide highlights the different attributes which emphasize on the need of email security in current times. These are protecting sensitive information, preventing identity theft, data breach mitigation, maintaining business reputation, etc. Introducing Email Security Best Practices Features Of Email Security In Digital Age to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Protects Sensitive Information, Prevents Identity Theft, Data Breach Mitigation, using this template. Grab it now to reap its full benefits.
-
 Securing Digital Asset Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Securing Digital Asset Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your presentation with our Network Security Technology Stack PowerPoint icon. This vibrant and eye-catching icon represents the layers of security technology used to protect networks from cyber threats. Perfect for presentations on cybersecurity, IT infrastructure, and network management. Grab your audiences attention and showcase your knowledge with this dynamic icon.
-
 Securing Digital Asset Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Securing Digital Asset Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon represents the advanced network security technology stack. It features a sleek and modern design, making it the perfect addition to any presentation on network security. Use it to showcase the latest advancements in protecting your network and data from cyber threats.
-
 Cyber Crisis Management Icon For Digital Security
Cyber Crisis Management Icon For Digital SecurityIntroducing our premium set of slides with name Cyber Crisis Management Icon For Digital Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Crisis Management, Digital Security. So download instantly and tailor it with your information.
-
 Digital Certificate Data Security Illustration
Digital Certificate Data Security IllustrationThis coloured PowerPoint icon features a lock symbol on a blue background, representing the Secure Socket Layer SSL protocol for secure online communication. Use it to enhance your presentations on internet security, encryption, and data protection. Perfect for technology and cybersecurity related presentations.
-
 Adopting Homomorphic Encryption To Secure Cloud Computing Implementing Digital Transformation And Ai DT SS
Adopting Homomorphic Encryption To Secure Cloud Computing Implementing Digital Transformation And Ai DT SSThis slide provides glimpse about utilizing homomorphic encryption approach that can help businesses in privacy preservation. It includes stages such as encryption, computation, decryption, etc. Increase audience engagement and knowledge by dispensing information using Adopting Homomorphic Encryption To Secure Cloud Computing Implementing Digital Transformation And Ai DT SS. This template helps you present information on three stages. You can also present information on Privacy Preservation, Secure Cloud Computing, Model Owner using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Incorporating Secure Multi Party Computation To Boost Data Implementing Digital Transformation And Ai DT SS
Incorporating Secure Multi Party Computation To Boost Data Implementing Digital Transformation And Ai DT SSThis slide provides glimpse about utilizing secure multi party computation SMPC approach that can help businesses in boosting data confidentiality. It includes stages such as input sharing, secure computation, output reconstruction, etc. Increase audience engagement and knowledge by dispensing information using Incorporating Secure Multi Party Computation To Boost Data Implementing Digital Transformation And Ai DT SS. This template helps you present information on three stages. You can also present information on Increase Security Against Attacks, Boost Data Confidentiality, Input Sharing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
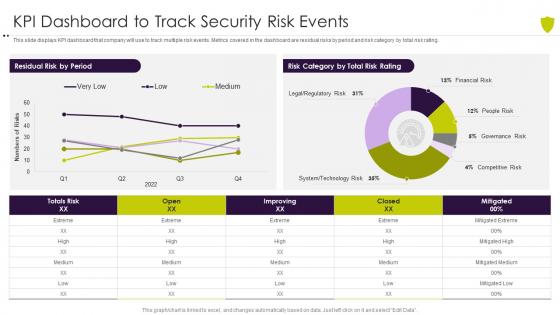 Kpi dashboard to track security risk events managing cyber risk in a digital age
Kpi dashboard to track security risk events managing cyber risk in a digital ageThis slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver an outstanding presentation on the topic using this Kpi Dashboard To Track Security Risk Events Managing Cyber Risk In A Digital Age. Dispense information and present a thorough explanation of KPI Dashboard To Track Security Risk Events using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Growing cyber security issues digital infrastructure to resolve organization issues
Growing cyber security issues digital infrastructure to resolve organization issuesThe slide provides the major cyber security issues Unprecedented Attacks, Cyber Espionage, and Data Theft along with the split of total information security incidents by the type of incident. Deliver an outstanding presentation on the topic using this Growing Cyber Security Issues Digital Infrastructure To Resolve Organization Issues. Dispense information and present a thorough explanation of Unprecedented Attacks, Cyber Espionage, Data Theft using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
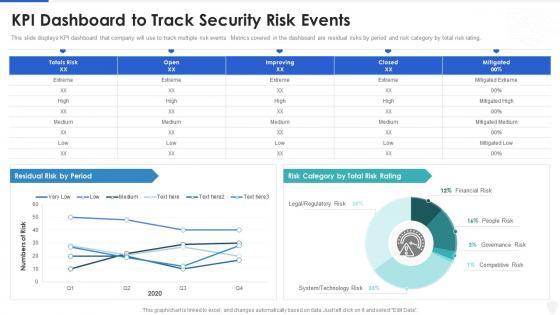 Cybersecurity and digital business risk management kpi dashboard to track security risk events
Cybersecurity and digital business risk management kpi dashboard to track security risk eventsPresent the topic in a bit more detail with this Cybersecurity And Digital Business Risk Management Kpi Dashboard To Track Security Risk Events. Use it as a tool for discussion and navigation on KPI Dashboard To Track Security Risk Events. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Online Data Security Limitation Analysis For Digital Organizations
Online Data Security Limitation Analysis For Digital OrganizationsThis slide depicts the challenges faced while storing digital data. The purpose of this template is to analyze the security limitations faced in the technology industries. It also includes elements such as cyberattack, loss of devices, etc. Introducing our Online Data Security Limitation Analysis For Digital Organizations set of slides. The topics discussed in these slides are Data Limitations, Impact, Technology Industry. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.





